HSCCTF WP
强行写了个wp,那就简单发一下吧
Web
CLICK
似乎是f12就能看到flag
Web-sign in
robots.txt看到fiag_ls_h3re.php,禁用下js f12就能看到
EXEC
?cmd=ca\t$IFS/ctf_is_fun_fla\g2021>2
然后访问2
CMS SYSTEM
yccms的rce,百度第一篇就可以参考
https://www.cnblogs.com/0daybug/p/12932677.html
先一模一样的方法改掉admin的密码
然后唯一不一样的地方就是任意文件上传的logo的那个地方改了下判断后缀名,但是只判断第二个,所以直接1.png.php就行了
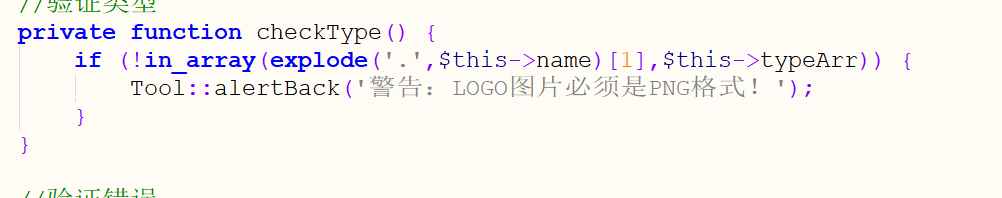
另外传完会变成logo.php,也要注意
Language
原题,先注入得到token,然后url编码绕过比较
https://fmyyy.gitee.io/2021/10/13/%E9%95%BF%E5%9F%8E%E6%9D%AF%E7%BA%BF%E4%B8%8B%E8%B5%9B%E8%B5%9B%E5%90%8E%E5%A4%8D%E7%8E%B0/
这篇wp可能有点问题,url编码哪里需要编码的是?,及/flag%3Faction=readFlag
Avatar detection system
文件上传测试了一下发现是白名单,但是传上去会触发getimagesize,getimagesize里可以用伪协议,而题目用的又是tp6,所以就可以用phar触发tp6的链子,具体的链子就不贴了,也是自己收藏的
MISC
Sign-in
公众号直接拿flag
DORAEMON
图片高度被改了,crc32爆破一下得到正确高度,然后ps里补两个定位符,扫一下就有flag
汝闻,人言否
压缩包的注释是键盘密码,画出来得到WVALOU,解压是个wave,直接看下频谱图就是flag

WIRESHARK
看名字还以为流量包,结果没半毛钱关系害
zip后面有张png,手动分一下,然后lsb发现r0g0b0发现还有张png,拿出来是个二维码,扫一下得到一串字符,栅栏栏数2解一下,得到压缩包密码,解压是个pdf,头被改了还原一下,010发现明显特征块whitespace,最后wbstego无密码直接出
PCXP
换了n多次附件才搞对的题目,一开始做的怀疑人生
最后给了两个镜像,vol常规流程走一走,发现一个里面有有个ffflllaaaggg.rar,另外一个有一个mirror.rar,都提取出来
把mirror.png拿出来后发现文件尾还有一张倒过来的png,手动分一下,cyberchef或者脚本倒一下,拿到另外一个图片上面有个密码,试了下发现是另一个rar的解压密码
另一个rar解压出来是个usb流量包,一开始还以为又是键盘鼠标,后来仔细一看发现这不有两张图片嘛,lsb先看一下发现明显盲水印特征,直接上bwmforpy3,得到flag

RE
hiahia o(▽)┛
ida打开分析一下发现是个简单的加密,前九位后九位的奇偶加加减减,写个脚本就行
s = 'igdb~Mumu@p&>%;%<$<p'
res = ''
for i in range(len(s)):
if i>9:
if i%2==0:
res += chr(ord(s[i])-11)
else:
res += chr(ord(s[i]) + 13)
else:
if i%2==0:
res += chr(ord(s[i])-3)
else:
res += chr(ord(s[i]) + 5)
print(res)
ANDROID
jadx反编译看一下,又是奇偶位异或,再写个辣鸡脚本
iArr = [102, 13, 99, 28, 127, 55, 99, 19, 109, 1, 121, 58, 83, 30, 79, 0, 64, 42]
iArr2 = [42, 42, 42, 42, 42, 42, 42, 42, 42, 42, 42, 42, 42, 42, 42, 42, 42, 42]
res = ''
for i in range(17):
if i%2==0:
res += chr(iArr[i]^i)
# else:
# res += chr(iArr[i]^iArr[i+1])
print(res)
res1 = ''
for i in range(9):
res1 += chr(iArr[i*2-1] ^ ord(res[i]))
print(res1)
for i in range(8):
print(res[i],end='')
print(res1[i+1],end='')
WAY
文件名就可看出来是个upx加密的迷宫,脱壳后ida看一下,找到了5*5的迷宫,手动走一下
OIIII
OOIO#
IOOOI
IOIOI
IIIII
sdsddwd
Crypto
Easy SignIn
hex -> base64 -> base32 -> base64
没记错的话是这样
AFFINE
稍微变了下的仿射,要爆破下ab,直接贴脚本
letter=string.ascii_letters+string.digits
s = 'xGJ13kkRK9QDfORQomFOf9NZs9LKVZvGqVIsVO9NOkorv'
for a in range(1,128):
for b in range(1,128):
res = ''
#求a关于26的乘法逆元
x, y = get(a, 62)
a1 = x % 62
l= len(s)
for i in range(l):
cipher = a1 * (letter.index(s[i]) - b) % 62
# res+=chr(cipher + 65)
# print(cipher)
res += letter[cipher]
if 'flag' in res:
print(res)
RSA
去年newsctf上strving出的原题,直接拿过来用可还行
import gmpy2
# import sympy
from Crypto.Util.number import *
# flag = b'????'
#
# z=getPrime(1024)
# p=sympy.nextprime(z)
# q=sympy.prevprime(10*z)
# n=p*q
#
# m=bytes_to_long(flag)
e=0xe18e
# c=pow(m,e,n)
#
# print("n=",n)
# print("c=",c)
n= 124689085077258164778068312042204623310499608479147230303784397390856552161216990480107601962337145795119702418941037207945225700624828698479201514402813520803268719496873756273737647275368178642547598433774089054609501123610487077356730853761096023439196090013976096800895454898815912067003882684415072791099101814292771752156182321690149765427100411447372302757213912836177392734921107826800451961356476403676537015635891993914259330805894806434804806828557650766890307484102711899388691574351557274537187289663586196658616258334182287445283333526057708831147791957688395960485045995002948607600604406559062549703501
c= 57089349656454488535971268237112640808678921972499308620061475860564979797594115551952530069277022452969364212192304983697546604832633827546853055947447207342333989645243311993521374600648715233552522771885346402556591382705491510591127114201773297304492218255645659953740107015305266722841039559992219190665868501327315897172069355950699626976019934375536881746570219967192821765127789432830133383612341872295059056728626931869442945556678768428472037944494803103784312535269518166034046358978206653136483059224165128902173951760232760915861623138593103016278906012134142386906130217967052002870735327582045390117565
t = 10
import gmpy2
for k in range(-1000000, 1000000):
x = gmpy2.iroot(k ** 2 + 4 * t * n, 2)
if x[1]:
p = (-k + x[0]) // (2 * t)
q = t * p + k
break
import gmpy2
from Crypto.Util.number import long_to_bytes, bytes_to_long
phi = (p - 1) * (q - 1)
t = gmpy2.gcd(e, phi)
d = gmpy2.invert(e // t, phi)
m = pow(c, d, n)
msg = gmpy2.iroot(m, t)
if msg[1]:
print(long_to_bytes(msg[0]))
# b'flag{6d22773623d3d5c871692e9985de5f16}'