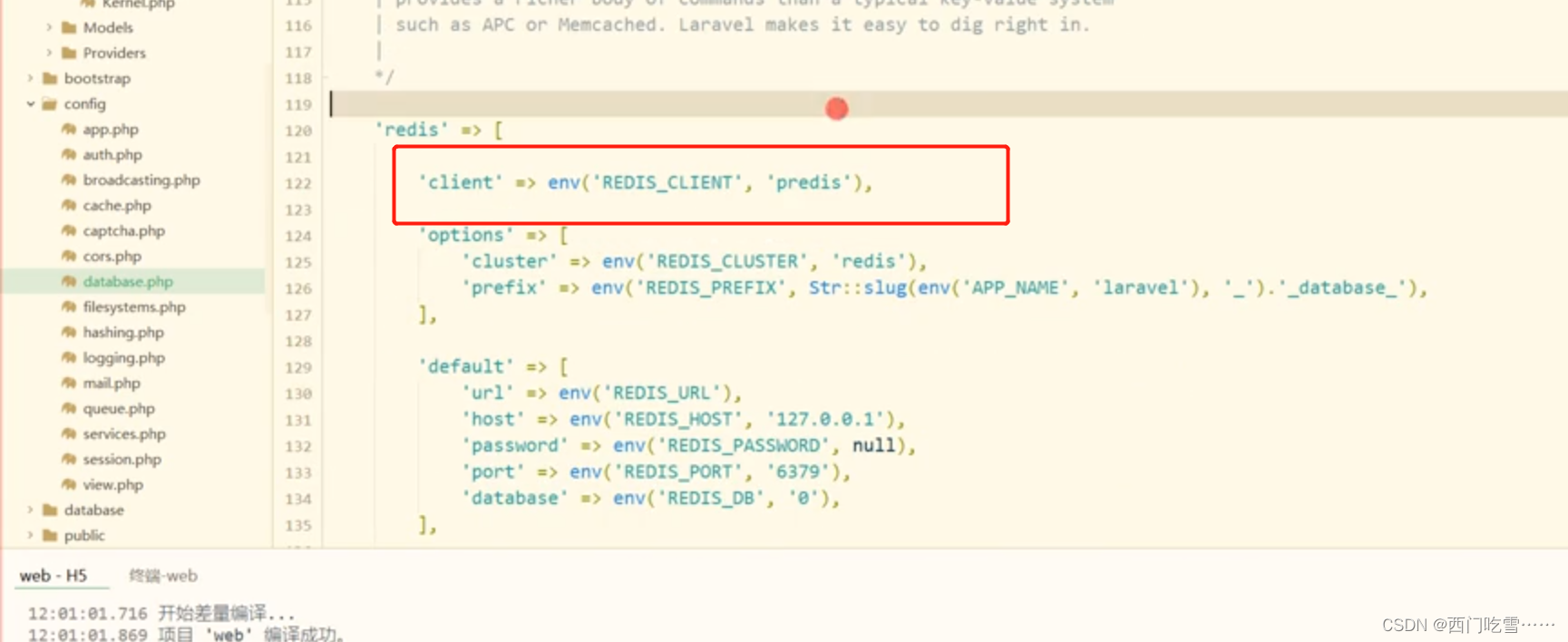
1.0 对请求参数进行ascii排序
2 转成a=111&b =2222&key=''
3进行md5加密 生产sign
4客户端请求携带参数以及sign
5后端同样算法 生成新sign
6然后两个sign进行对比即可
这里是前端sign 不用太在意
var sign = this.common.sign(params);
params['sign']=sign
uni.request({
url:'http://www.study.com/api/sendCode',
data:params,
method:'POST',
header:{
'content-type':'application/x-www-form-urlencoded'
}
})
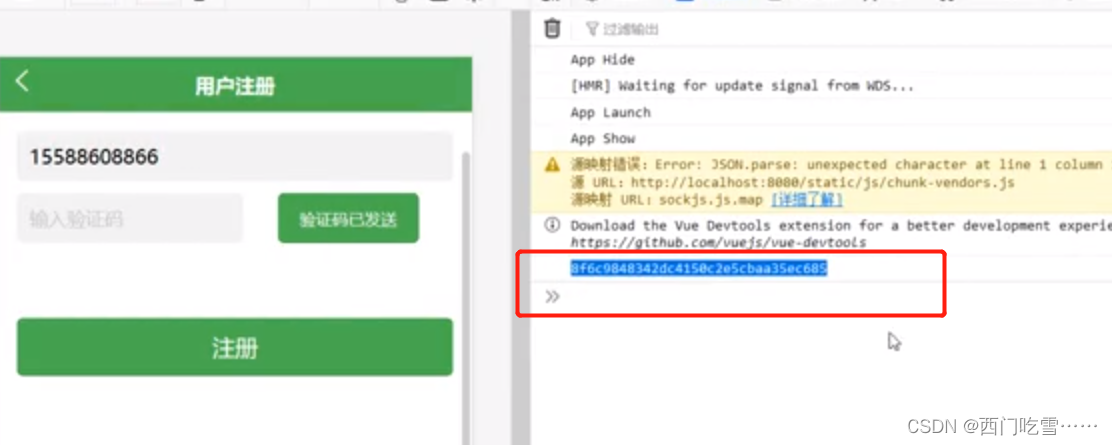
this.msg='验证码已发送'
this.status=true
sign:function(data){
var arr = [];
for(var index in data){
arr.push(index+'='+data[index])
}
var str = arr.join('&')
return this.paramSort(str);
},
上面的对于后端来说不重要 重点看下面签名
public function handle(Request $request, Closure $next)
{
$apiKey = env('API_KEY');
$data = $request->all();
if(!isset($data['sign'])){
return \response()->json(['code'=>803,'msg'=>'非法请求参数']);
}
$sign = $data['sign'];
unset($data['sign']);
$data['key']=$apiKey;
ksort($data);
$data = http_build_query($data);
$newSign = md5($data);
if($newSign!=$sign){
return response()->json(['code'=>801,'msg'=>'非法的接口请求']);
}
if(Redis::get($sign)){
return response()->json(['code'=>802,'msg'=>'请勿重复请求接口']);
}
Redis::setex($sign,60,1);
return $next($request);
}

接口防刷思路