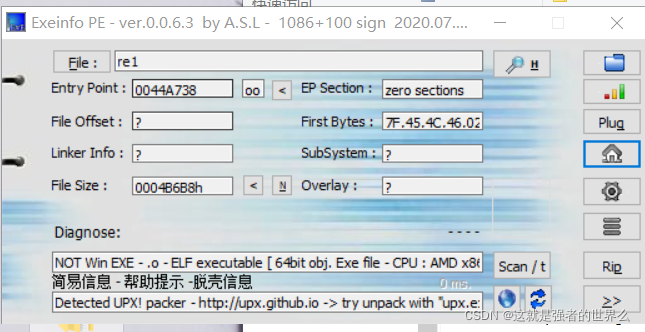
普通的upx壳,放kali里面脱下壳就行
运行

进入主函数
__int64 sub_401165()
{
int v0; // edx
int v1; // ecx
int v2; // er8
int v3; // er9
__int64 result; // rax
__int64 v5; // [rsp+8h] [rbp-1018h]
char v6[112]; // [rsp+10h] [rbp-1010h] BYREF
int v7; // [rsp+80h] [rbp-FA0h]
int v8; // [rsp+A0Ch] [rbp-614h]
unsigned __int64 v9; // [rsp+1018h] [rbp-8h]
v9 = __readfsqword(0x28u);
sub_400488(v6, 12LL, 4096LL);
if ( (int)sub_400B7D() < (v7 ^ v8) )
sub_400B6D();
sub_410990("welcome to ctfshow file system");
sub_410990("plz input your authcode");
v5 = sub_400B97(); //输入函数
sub_400D9A(v5); //加密函数
sub_40FD10((unsigned int)"your authcode is %s\n", v5, v0, v1, v2, v3);
result = 0LL;
if ( __readfsqword(0x28u) != v9 )
sub_44BCE0();
return
进入加密函数
unsigned __int64 __fastcall sub_400D9A(__int64 a1)
{
int v1; // ebx
void *v2; // rsp
unsigned __int64 result; // rax
__int64 v4; // [rsp+0h] [rbp-130h] BYREF
__int64 v5; // [rsp+8h] [rbp-128h]
char v6; // [rsp+13h] [rbp-11Dh]
unsigned int j; // [rsp+14h] [rbp-11Ch]
unsigned int i; // [rsp+18h] [rbp-118h]
int v9; // [rsp+1Ch] [rbp-114h]
__int64 v10; // [rsp+20h] [rbp-110h]
__int64 v11; // [rsp+28h] [rbp-108h]
__int64 *v12; // [rsp+30h] [rbp-100h]
__int64 v13; // [rsp+38h] [rbp-F8h] BYREF
__int64 v14[27]; // [rsp+40h] [rbp-F0h]
unsigned __int64 v15; // [rsp+118h] [rbp-18h]
v5 = a1;
v15 = __readfsqword(0x28u);
v9 = 0;
v10 = 0LL;
while ( *(_BYTE *)(v9 + v5) )
v10 += *(char *)(v9++ + v5);
v1 = v9;
v11 = v9 - 1LL;
v2 = alloca(16 * ((4LL * v9 + 18) / 0x10uLL));
v12 = &v4;
v13 = 0LL;
for ( i = 0; (int)i < v9; i += 2 )
{
*((_DWORD *)v12 + (int)i) = *(char *)((int)i + v5);
*((_DWORD *)v12 + (int)(i + 1)) = *(char *)((int)i + 1LL + v5);
LODWORD(v13) = *((_DWORD *)v12 + (int)i);
HIDWORD(v13) = *((_DWORD *)v12 + (int)(i + 1));
sub_400C9D((unsigned int *)&v13); //加密函数
*((_DWORD *)v12 + (int)i) = v13;
*((_DWORD *)v12 + (int)(i + 1)) = HIDWORD(v13);
}
v14[0] = 0x507BC5BCLL; //加密后的密文
v14[1] = 0x2B989A22LL;
v14[2] = 0x63A48F40LL;
v14[3] = 2831241988LL;
v14[4] = 0x7451189ALL;
v14[5] = 0x8A3E7CCFLL;
v14[6] = 0x62CA9921LL;
v14[7] = 0xE1B5C82LL;
v14[8] = 0xC3965CA9LL;
v14[9] = 0xD6268AA1LL;
v14[10] = 0x22AC5103LL;
v14[11] = 0x9ACC9D7ELL;
v14[12] = 0x224A7DC3LL;
v14[13] = 0xD588C510LL;
v14[14] = 0xCB432BE4LL;
v14[15] = 0xB6A13511LL;
v14[16] = 0x4C3513DCLL;
v14[17] = 0x6FCEEBC1LL;
v14[18] = 0xA3614D20LL;
v14[19] = 0x87C441CCLL;
v14[20] = 0xA1F95799LL;
v14[21] = 0x3E6DD14ALL;
v14[22] = 0x6F28852FLL;
v14[23] = 0x52AC745FLL;
v14[24] = 0x9190AC59LL;
v14[25] = 0x16DE2CFBLL;
if ( (unsigned __int64)(4LL * v1 - 100) > 3 )
{
sub_410990(&unk_492968);
sub_40F0F0(0LL);
}
v6 = 0;
for ( j = 0; j <= 25; ++j ) //比较
{
if ( *((_DWORD *)v12 + (int)j) != v14[j] )
{
sub_410990(&unk_492990);
v6 = 1;
break;
}
}
if ( v6 == 1 )
sub_40F0F0(0LL);
sub_410990(&unk_4929B3);
result = __readfsqword(0x28u) ^ v15;
if ( result )
sub_44BCE0();
return result;
}
加密函数,TEA加密
unsigned __int64 __fastcall sub_400C9D(unsigned int *a1)
{
unsigned __int64 result; // rax
int v2; // [rsp+18h] [rbp-38h]
unsigned int v3; // [rsp+1Ch] [rbp-34h]
unsigned int v4; // [rsp+20h] [rbp-30h]
int i; // [rsp+24h] [rbp-2Ch]
unsigned __int64 v6; // [rsp+48h] [rbp-8h]
v6 = __readfsqword(0x28u);
v2 = 0;
v3 = *a1;
v4 = a1[1];
for ( i = 0; i <= 31; ++i )
{
v2 += 0x6F361F7C;
v3 += (v4 + v2) ^ (16 * v4 + 0x6F) ^ ((v4 >> 5) + 0x36);
v4 += (v3 + v2) ^ (16 * v3 + 0x1F) ^ ((v3 >> 5) + 0x7C);
}
*a1 = v3;
a1[1] = v4;
result = __readfsqword(0x28u) ^ v6;
if ( result )
sub_44BCE0();
return result;
}
写个脚本
#include <stdlib.h>
#include <stdio.h>
#include <string.h>
int main()
{
long long int v14[27] = {0};
v14[0] = 0x507BC5BC;
v14[1] = 0x2B989A22;
v14[2] = 0x63A48F40;
v14[3] = 2831241988;
v14[4] = 0x7451189A;
v14[5] = 0x8A3E7CCF;
v14[6] = 0x62CA9921;
v14[7] = 0xE1B5C82;
v14[8] = 0xC3965CA9;
v14[9] = 0xD6268AA1;
v14[10] = 0x22AC5103;
v14[11] = 0x9ACC9D7E;
v14[12] = 0x224A7DC3;
v14[13] = 0xD588C510;
v14[14] = 0xCB432BE4;
v14[15] = 0xB6A13511;
v14[16] = 0x4C3513DC;
v14[17] = 0x6FCEEBC1;
v14[18] = 0xA3614D20;
v14[19] = 0x87C441CC;
v14[20] = 0xA1F95799;
v14[21] = 0x3E6DD14A;
v14[22] = 0x6F28852F;
v14[23] = 0x52AC745F;
v14[24] = 0x9190AC59;
v14[25] = 0x16DE2CFB;
int v2 = 0;
int i,j,k;
for(i = 0; i <= 31 ; ++i)
{
v2 += 0x6F361F7C;
}
unsigned int v3,v4;
for(j = 0; j < 26 ; j += 2)
{
int sum = v2;
v3 = v14[j];
v4 = v14[j + 1];
for( k = 0 ; k <= 31 ; k ++)
{
v4 -= (v3 + sum) ^ (v3 * 16 + 31) ^ ((v3 >> 5) + 124);
v3 -= (v4 + sum) ^ (v4 * 16 + 111) ^ ((v4 >> 5) + 54);
sum -= 0x6F361F7C;
}
v14[j] = v3;
v14[j + 1] = v4;
}
for(i = 0 ; i < 26; i++)
{
printf("%c",v14[i]);
}
return 0;
}
得到最终flag:ctfshow{just_a_simple_re}