64位elf文件

64位ida查看字符串跟进main函数
__int64 __fastcall main(__int64 a1, char **a2, char **a3)
{
char v3; // al
__int64 result; // rax
char v5; // [rsp+7h] [rbp-B9h]
signed int i; // [rsp+8h] [rbp-B8h]
signed int j; // [rsp+Ch] [rbp-B4h]
int v8[14]; // [rsp+10h] [rbp-B0h]
int v9; // [rsp+4Ah] [rbp-76h]
__int16 v10; // [rsp+4Eh] [rbp-72h]
char v11[17]; // [rsp+50h] [rbp-70h]
char v12; // [rsp+61h] [rbp-5Fh]
unsigned __int64 v13; // [rsp+B8h] [rbp-8h]
v13 = __readfsqword(0x28u);
printf("input flag:", a2, a3);
scanf("%s", v11);
v9 = 'ftca';
v10 = '{';
v5 = 1;
for ( i = 0; i <= 4; ++i )
{
if ( *((_BYTE *)&v9 + i) != v11[i] )
{
v5 = 0;
goto LABEL_6;
}
}
if ( !v5 )
goto LABEL_19;
LABEL_6:
for ( j = 0; j <= 11; ++j )
v8[j] = v11[j + 5];
v3 = (unsigned __int8)sub_83A(v8) && v12 == '}' ? 1 : 0;
if ( v3 )
{
printf("That's true! flag is %s", v11);
result = 0LL;
}
else
{
LABEL_19:
printf("Try another time...");
result = 0LL;
}
return result;
}
上下是判定头字符串的actf{}
主要看sub_83A
ida提示too big function
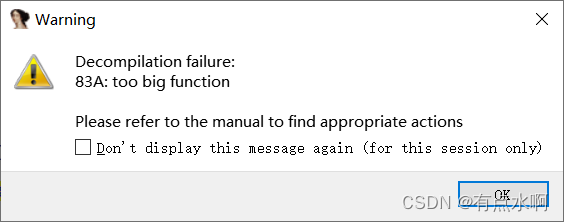
百度得到只需要修改配置文件IDA\cfg\hexrays.cfg
找到:
MAX_FUNCSIZE = 64 // Functions over 64K are not decompiled
修改为:
MAX_FUNCSIZE = 1024 // Functions over 64K are not decompiled
重启ida,让函数再跑一会儿
卡完是一个三千多行的函数
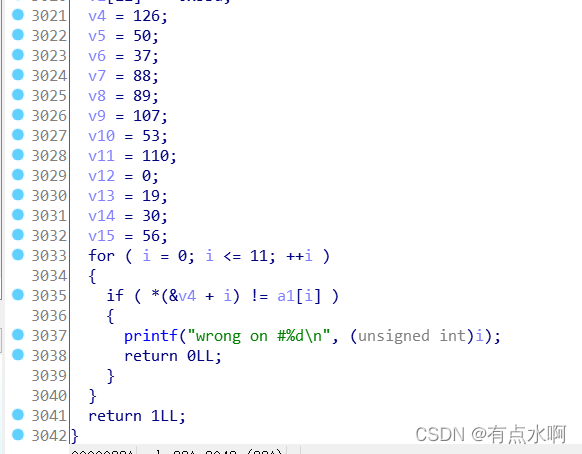
总结:
输入的值经历三千行的变换后等于数组v4的值
逆向是不可能逆向的,直接开始爆破
#include <stdlib.h>
#include <stdio.h>
#include <string.h>
int v4[]={126,50,37,88,89,107,53,110,0,19,30,56};
int sub_83A(char *v1,int i)
{
*v1 ^= 43u;
v1[1] ^= 108u;
v1[2] ^= 126u;
v1[3] ^= 86u;
//略 直接复制源代码就行
v1[8] ^= 0x6Bu;
v1[9] ^= 0x70u;
v1[10] ^= 0x29u;
v1[11] ^= 0x3Bu;
if(v1[i] == v4[i])
return 1;
else
return 0;
}
int main()
{
int i,j;
char flag[13] = "";
char tmp[13] = "";
for(i = 0; i < 12 ; i++)
{
for(j = 33; j <= 126 ; j++)
{
strcpy(flag,tmp);
flag[i] = j;
if(sub_83A(flag,i))
{
tmp[i] = j;
break;
}
}
}
printf("actf{%s}\n",tmp);
return 0;
}
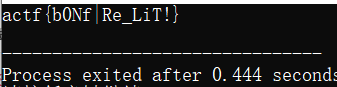
flag{b0Nf|Re_LiT!}