早上打MR去了,然后一上午怀疑人生,又花了两个小时调整心态,之后来DAS做了个re,顺便记录一下。
Crackme
一个32位的MFC:

随便输了点东西,确定,然后 MessageBox 弹了个 Wrong !!! 。

之后就顺着这个 wrong 在IDA里面摸到了对应的函数:

下面就是要把key先找出来,可以看到下面有用 memcmp 进行密文比较,将对应的hash值提取到在线网站(https://www.somd5.com/)进行还原。
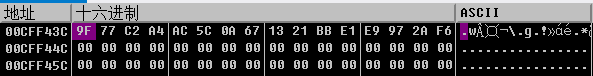
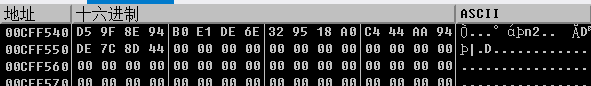
解的key为:NocTuRne。
然后再把key扔回去,以同样的方式获取flag的密文:
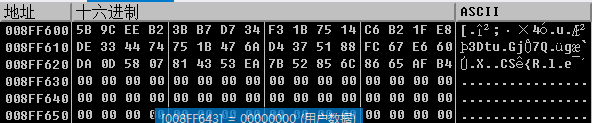

最后就是参照 flag 的加密方式写一个解密就好了:
#include<Windows.h>
#include<iostream>
#include<wincrypt.h>
int main() {
BOOL v6; // [esp+4h] [ebp-18h]
HCRYPTKEY phKey; // [esp+Ch] [ebp-10h] BYREF
HCRYPTPROV phProv; // [esp+10h] [ebp-Ch] BYREF
HCRYPTHASH phHash; // [esp+14h] [ebp-8h] BYREF
BYTE key[] = "\x5c\x53\xa4\xa4\x1d\x52\x43\x7a\x9f\xa1\xe9\xc2\x6c\xa5\x90\x90";
BYTE flag[100] = { 0x5B,0x9C,0xEE,0xB2,0x3B,0xB7,0xD7,0x34,0xF3,0x1B,0x75,0x14,0xC6,0xB2,0x1F,0xE8,0xDE,0x33,0x44,0x74,0x75,0x1B,0x47,0x6A,0xD4,0x37,0x51,0x88,0xFC,0x67,0xE6,0x60,0xDA,0x0D,0x58,0x07,0x81,0x43,0x53,0xEA,0x7B,0x52,0x85,0x6C,0x86,0x65,0xAF,0xB4
};
DWORD var_16 = 16;
DWORD flag_len = 0x30;
DWORD var_260 = 260;
phProv = 0;
phHash = 0;
phKey = 0;
v6 = CryptAcquireContextA(&phProv, 0, 0, 0x18u, 0xF0000000);
if (v6)
{
v6 = CryptCreateHash(phProv, 0x8003u, 0, 0, &phHash);
if (v6)
{
v6 = CryptHashData(phHash, key, var_16, 0);
if (v6)
{
v6 = CryptDeriveKey(phProv, 0x660Eu, phHash, 1u, &phKey);
if (v6)
v6 = CryptDecrypt(phKey, 0, 1, 0, flag, &flag_len);
}
}
}
if (phKey)
CryptDestroyKey(phKey);
if (phHash)
CryptDestroyHash(phHash);
if (phProv)
CryptReleaseContext(phProv, 0);
flag[32] = 0;
cout << "flag : " << flag << endl;
char xx = getchar();
return EXIT_SUCCESS;
}
