前言
实验目的
1)初步了解对称密码
2)掌握数据加密标准DES的实现
实验方法
根据PPT中关于DES加解密算法的描述,用所熟悉的语言,完成实验内容、描述实验操作步骤、实验结果与实验心得。
实验环境
计算机语言:C语言
开发环境:Dev-C++
实验内容
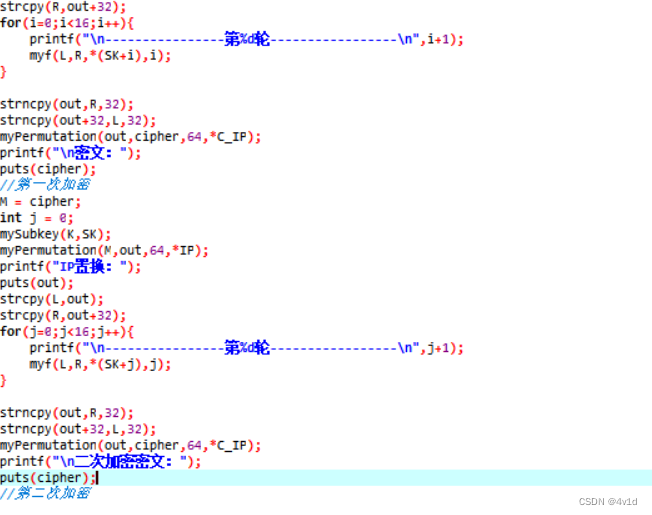
1.编程实现DES算法,要求有加密步骤和解密步骤。
2. DES算法作为密码体制中的对称密码体制,明文按64位进行分组,密钥长64位,密钥实际是56位参与DES运算,另外的8位被用于奇偶验证。
3. 56位分成两个28位密匙,每半个密匙都被分别处理。在接下来的循环中,两个半密钥都被左移一位或2位,然后通过置换2产生48位子密匙,每个半密匙24位,
4. 解密过程中,除了子密匙的输出顺序相反外,密匙的调度过程完全一样。
实验操作步骤
暂略
实验结果
对课件上的两种密钥分别测试
正常密钥:
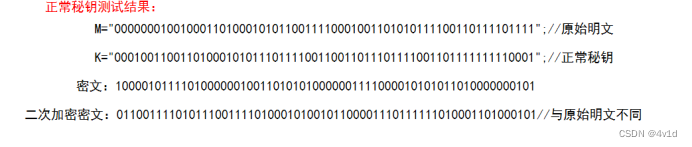
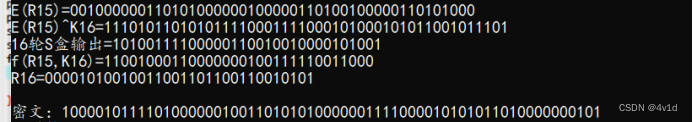
运行结果截图
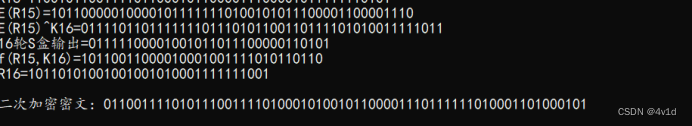
弱密钥:
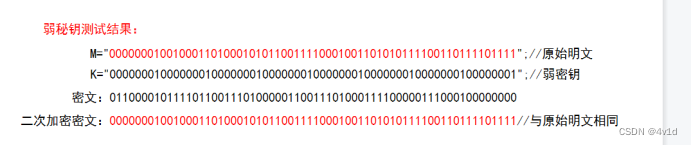
设定密钥改变
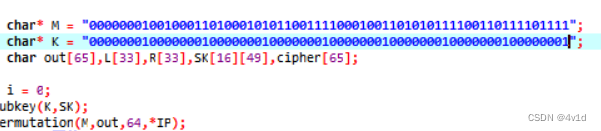
运行结果截图,二次加密后与明文相同
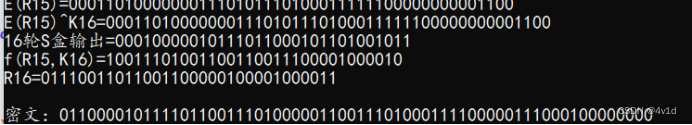
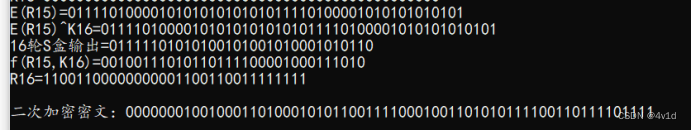
实验心得
这次学习了des的加解密算法,整个算法的机制其实不难,就是由定义好的置换表和s盒进行操作,完成加解密的运算。虽然过程不像一些密码那样繁琐,但是在不知道密钥的情况下进行暴力破解却是十分麻烦的,让我领略到与RSA不同的魅力。
实验代码
des.cpp
#include<stdio.h>
#include<string.h>
//数据表
//选择置换PC-1
char PC_1[8][7] =
{
{57, 49, 41, 33, 25, 17, 9},
{1, 58, 50, 42, 34, 26, 18},
{10, 2, 59, 51, 43, 35, 27},
{19, 11, 3, 60, 52, 44, 36},
{63, 55, 47, 39, 31, 23, 15},
{7, 62, 54, 46, 38, 30, 22},
{14, 6, 61, 53, 45, 37, 29},
{21, 13, 5, 28, 20, 12, 4}
};
//左移位数
int move_time[16] = {1, 1, 2, 2, 2, 2, 2, 2, 1, 2, 2, 2, 2, 2, 2, 1};
//选择置换PC-2
char PC_2[8][6] =
{
{14, 17, 11, 24, 1, 5},
{3, 28, 15, 6, 21, 10},
{23, 19, 12, 4, 26, 8},
{16, 7, 27, 20, 13, 2},
{41, 52, 31, 37, 47, 55},
{30, 40, 51, 45, 33, 48},
{44, 49, 39, 56, 34, 53},
{46, 42, 50, 36, 29, 32}
};
char IP[8][8] =
{
{ 58, 50, 42, 34, 26, 18, 10, 2},
{60, 52, 44, 36, 28, 20, 12, 4},
{62, 54, 46, 38, 30, 22, 14, 6},
{64, 56, 48, 40, 32, 24, 16, 8},
{57, 49, 41, 33, 25, 17, 9, 1},
{59, 51, 43, 35, 27, 19, 11, 3},
{61, 53, 45, 37, 29, 21, 13, 5},
{63, 55, 47, 39, 31, 23, 15, 7 }
};
char C_IP[8][8] =
{
{40, 8, 48, 16, 56, 24, 64, 32},
{39, 7, 47, 15, 55, 23, 63, 31},
{38, 6, 46, 14, 54, 22, 62, 30},
{37, 5, 45, 13, 53, 21, 61, 29},
{36, 4, 44, 12, 52, 20, 60, 28},
{35, 3, 43, 11, 51, 19, 59, 27},
{34, 2, 42, 10, 50, 18, 58, 26},
{33, 1, 41, 9, 49, 17, 57, 25}
};
char E[8][6] =
{
{32, 1, 2, 3, 4, 5},
{4, 5, 6, 7, 8, 9},
{8, 9, 10, 11, 12, 13},
{12, 13, 14, 15, 16, 17},
{16, 17, 18, 19, 20, 21},
{20, 21, 22, 23, 24, 25},
{24, 25, 26, 27, 28, 29},
{28, 29, 30, 31, 32, 1}
};
char P[4][8] =
{
{16, 7, 20, 21,29, 12, 28, 17},
{1, 15, 23, 26,5, 18, 31, 10},
{2, 8, 24, 14,32, 27, 3, 9},
{19, 13, 30, 6,22, 11, 4, 25 }
};
char S_Box[8][65] =
{
{
14,4,13,1,2,15,11,8,3,10,6,12,5,9,0,7,
0,15,7,4,14,2,13,1,10,6,12,11,9,5,3,8,
4,1,14,8,13,6,2,11,15,12,9,7,3,10,5,0,
15,12,8,2,4,9,1,7,5,11,3,14,10,0,6,13
},
{
15,1,8,14,6,11,3,4,9,7,2,13,12,0,5,10,
3,13,4,7,15,2,8,14,12,0,1,10,6,9,11,5,
0,14,7,11,10,4,13,1,5,8,12,6,9,3,2,15,
13,8,10,1,3,15,4,2,11,6,7,12,0,5,14,9
},
{
10,0,9,14,6,3,15,5,1,13,12,7,11,4,2,8,
13,7,0,9,3,4,6,10,2,8,5,14,12,11,15,1,
13,6,4,9,8,15,3,0,11,1,2,12,5,10,14,7,
1,10,13,0,6,9,8,7,4,15,14,3,11,5,2,12
},
{
7,13,14,3,0,6,9,10,1,2,8,5,11,12,4,15,
13,8,11,5,6,15,0,3,4,7,2,12,1,10,14,9,
10,6,9,0,12,11,7,13,15,1,3,14,5,2,8,4,
3,15,0,6,10,1,13,8,9,4,5,11,12,7,2,14
},
{
2,12,4,1,7,10,11,6,8,5,3,15,13,0,14,9,
14,11,2,12,4,7,13,1,5,0,15,10,3,9,8,6,
4,2,1,11,10,13,7,8,15,9,12,5,6,3,0,14,
11,8,12,7,1,14,2,13,6,15,0,9,10,4,5,3
},
{
12,1,10,15,9,2,6,8,0,13,3,4,14,7,5,11,
10,15,4,2,7,12,9,5,6,1,13,14,0,11,3,8,
9,14,15,5,2,8,12,3,7,0,4,10,1,13,11,6,
4,3,2,12,9,5,15,10,11,14,1,7,6,0,8,13
},
{
4,11,2,14,15,0,8,13,3,12,9,7,5,10,6,1,
13,0,11,7,4,9,1,10,14,3,5,12,2,15,8,6,
1,4,11,13,12,3,7,14,10,15,6,8,0,5,9,2,
6,11,13,8,1,4,10,7,9,5,0,15,14,2,3,12
},
{
13,2,8,4,6,15,11,1,10,9,3,14,5,0,12,7,
1,15,13,8,10,3,7,4,12,5,6,11,0,14,9,2,
7,11,4,1,9,12,14,2,0,6,10,13,15,3,5,8,
2,1,14,7,4,10,8,13,15,12,9,0,3,5,6,11
}
};
void myXOR(char* In1,char* In2,int n,char* Out)
{
int i=0;
for(i=0;i<n;i++)
*(In1+i)!=*(In2+i) ? *(Out+i)='1' : *(Out+i)='0';
}
void myPermutation(char *In,char *Out,int n,char *P)
{
int i = 0;
for(i=0;i<n;i++)
*(Out+i)=*(In+*(P+i)-1);
*(Out+i) = '\0';
}
void myShift(char *In,char *Out,int n,int s)
{
int i = 0;
for(i=0;i<n;i++)
*(Out+i)=*(In+(s+i)%n);
*(Out+i)= '\0';
}
void myf(char* L,char* R,char* SK,int t)
{
int i=0,j=0;
int row,col;
char out1[49]={0},out2[49]={0},out3[33]={0},out4[33]={0},temp[33]={0};
printf("K%d=",t+1);
puts(SK);
myPermutation(R,out1,48,*E);
printf("E(R%d)=",t);
puts(out1);
myXOR(out1,SK,48,out2);
printf("E(R%d)^K%d=",t,t+1);
puts(out2);
for(i=0;i<8;i++)
{
row = ((out2[i*6]-'0')<<1)+(out2[i*6+5]-'0');
col = ((out2[i*6+1]-'0')<<3)+((out2[i*6+2]-'0')<<2)+((out2[i*6+3]-'0')<<1)
+(out2[i*6+4]-'0');
for(j=3;j>=0;j--)
*(out3+(i*4+3-j))=((S_Box[i][row*16+col]>>j)&1)+'0';
}
*(out3+32)='\0';
printf("%d轮S盒输出=",t+1);
puts(out3);
myPermutation(out3,out4,32,*P);
printf("f(R%d,K%d)=",t,t+1);
puts(out4);
strcpy(temp,R);
myXOR(L,out4,32,R);
printf("R%d=",t+1);
puts(R);
strcpy(L,temp);
}
void mySubkey(char* K,char (*SK)[49])
{
char out[57],C[57],D[29],e[29],t[57];
int i=0,j=0;
myPermutation(K,out,56,*PC_1);
strcpy(C,out);
strcpy(D,out+28);
for(j=0;j<16;j++)
{
myShift(C,e,28,move_time[j]);
strcpy(C,e);
myShift(D,e,28,move_time[j]);
strcpy(D,e);
strncpy(t,C,28);
strncpy(t+28,D,28);
myPermutation(t,*(SK+j),48,*PC_2);
}
}
int main()
{
char* M = "0000000100100011010001010110011110001001101010111100110111101111";
char* K = "0000000100000001000000010000000100000001000000010000000100000001";
char out[65],L[33],R[33],SK[16][49],cipher[65];
int i = 0;
mySubkey(K,SK);
myPermutation(M,out,64,*IP);
printf("IP置换:");
puts(out);
strcpy(L,out);
strcpy(R,out+32);
for(i=0;i<16;i++){
printf("\n----------------第%d轮-----------------\n",i+1);
myf(L,R,*(SK+i),i);
}
strncpy(out,R,32);
strncpy(out+32,L,32);
myPermutation(out,cipher,64,*C_IP);
printf("\n密文:");
puts(cipher);
//第一次加密
M = cipher;
int j = 0;
mySubkey(K,SK);
myPermutation(M,out,64,*IP);
printf("IP置换:");
puts(out);
strcpy(L,out);
strcpy(R,out+32);
for(j=0;j<16;j++){
printf("\n----------------第%d轮-----------------\n",j+1);
myf(L,R,*(SK+j),j);
}
strncpy(out,R,32);
strncpy(out+32,L,32);
myPermutation(out,cipher,64,*C_IP);
printf("\n二次加密密文:");
puts(cipher);
//第二次加密
printf("\n---------------解密----------------\n");
int J =0;
mySubkey(K,SK);
myPermutation(cipher,out,64,*IP);
printf("IP置换:");
puts(out);
strcpy(L,out);
strcpy(R,out+32);
for(J=15;J>=0;J--){
printf("\n-----------第%d轮--------",J+1);
myf(L,R,*(SK+J),J);
}
strncpy(out,R,32);
strncpy(out+32,L,32);
myPermutation(out,cipher,64,*C_IP);
printf("\n明文:");
puts(cipher);
}
