进入程序,刚刚做出来,先按照我做出的顺序来把
发现无法f5直接看汇编
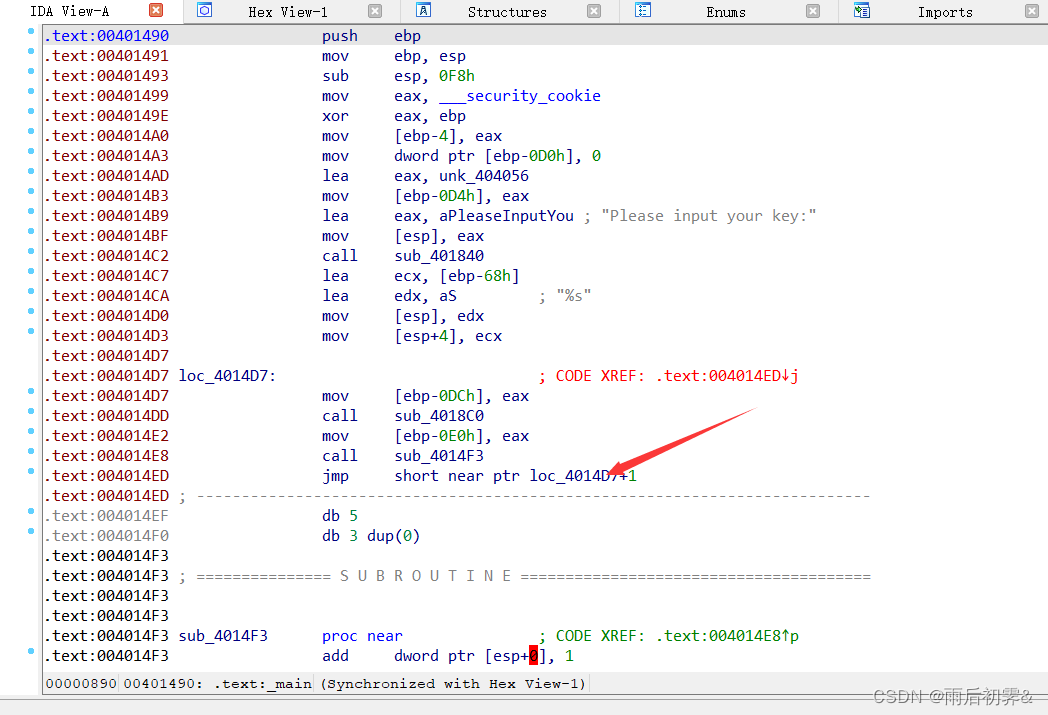
花指令,我们直接nop掉。为了平衡栈

?箭头指向的地方全部nop
同样,还有另外2处,全部nop掉,然后创建函数可以f5看逻辑了
int __cdecl main(int argc, const char **argv, const char **envp)
{
const char *Str1; // eax
const char *Str2; // [esp+14h] [ebp-E4h]
int i; // [esp+20h] [ebp-D8h]
const char *v7; // [esp+24h] [ebp-D4h]
char flag[100]; // [esp+2Ch] [ebp-CCh] BYREF
char key[100]; // [esp+90h] [ebp-68h] BYREF
sub_401840("Please input your key:");
sub_4018C0("%s", key);
Str2 = off_405004;
Str1 = (const char *)sub_401000(key);
if ( !strcmp(Str1, Str2) )
{
sub_401840("Please input your flag:");
sub_4018C0("%s", flag);
if ( strlen(flag) == 25 )
{
v7 = sub_4011D0(flag, key);
for ( i = 0; i < 25; ++i )
{
if ( v7[i] != byte_405008[i] )
{
sub_401840("Ohh no~~\n");
return 0;
}
}
sub_401840("Congratulation! The answer is flag{md5(your flag)}\n");
}
}
else
{
sub_401840("Wrong Key!\n");
}
return 0;很明显,先输入key,然后输入flag。key可以从
Str2 = off_405004;
?Str1 = (const char *)sub_401000(key);
获取,我们知道
我们通过观察发现是key进过变种的base64加密成的key。所以我们解得key为i_am_a_ctF3rr
我们进一步观察key与flag之间进行的操作
const char *__cdecl sub_4011D0(const char *flag, const char *key)
{
int v3; // [esp+18h] [ebp-134h]
char v4; // [esp+1Ch] [ebp-130h]
int j; // [esp+20h] [ebp-12Ch]
char v6; // [esp+24h] [ebp-128h]
int v7; // [esp+28h] [ebp-124h]
int v8; // [esp+28h] [ebp-124h]
int v9; // [esp+2Ch] [ebp-120h]
int i; // [esp+30h] [ebp-11Ch]
size_t k; // [esp+30h] [ebp-11Ch]
char v12[257]; // [esp+3Bh] [ebp-111h]
v7 = 0;
for ( i = 0; i < 256; ++i )
v12[i] = i;
for ( j = 0; j < 256; ++j )
{
v3 = v7 + (unsigned __int8)v12[j];
v7 = ((unsigned __int8)key[j % strlen(key)] + v3) % 256;
v4 = v12[j];
v12[j] = v12[v7];
v12[v7] = v4;
}
v9 = 0;
v8 = 0;
for ( k = 0; k < strlen(flag); ++k )
{
v9 = (v9 + 1) % 256;
v8 = (v8 + (unsigned __int8)v12[v9]) % 256;
v6 = v12[v9];
v12[v9] = v12[v8];
v12[v8] = v6;
flag[k] ^= v12[((unsigned __int8)v12[v8] + (unsigned __int8)v12[v9]) % 256];
}
return flag;
}就是变种RC4加密
直接写好了,代码直接贴,都不需要逆向
EXP
#include<stdio.h>
#include<windows.h>
#include<string.h>
int main()
{int v3; // [esp+18h] [ebp-134h]
int v4; // [esp+1Ch] [ebp-130h]
int j; // [esp+20h] [ebp-12Ch]
int v6; // [esp+24h] [ebp-128h]
int v7; // [esp+28h] [ebp-124h]
int v8; // [esp+28h] [ebp-124h]
int v9; // [esp+2Ch] [ebp-120h]
int i; // [esp+30h] [ebp-11Ch]
int k; // [esp+30h] [ebp-11Ch]
int v12[257]; // [esp+3Bh] [ebp-111
char flag[]={ 12, 170, 161, 170, 167, 226, 31, 229, 204, 85,
173, 198, 102, 193, 164, 30, 24, 238, 25, 12,
237, 221, 13, 73, 153};
char key[]="i_am_a_ctF3rr";
v7 = 0;
v9 = 0;
v8 = 0;
for ( i = 0; i < 256; ++i )
{
v12[i] = i;
}
for ( j = 0; j < 256; ++j )
{
v3 = v7 + v12[j];
v7 = (key[j % strlen(key)] + v3) % 256;
v4 = v12[j];
v12[j] = v12[v7];
v12[v7] = v4;
}
for ( k = 0; k < strlen(flag); ++k )
{
v9 = (v9 + 1) % 256;
v8 = (v8 + v12[v9]) % 256;
v6 = v12[v9];
v12[v9] = v12[v8];
v12[v8] = v6;
flag[k] ^= v12[(v12[v8] + v12[v9]) % 256];
}
puts(flag);
}把flagmd5掉就是题目要求的flag
Please input your key:i_am_a_ctF3rr
Please input your flag:HAve-FVn-wiTh-base&Rcfour
Congratulation! The answer is flag{md5(your flag)}
