单点登录微服务阿里下
调用服务,通关认证服务之后,feign调用其他服务
Oauth2规范
oauth2定义了一种认证授权协议,一种规范,此规范中定义了四种类型的角色:
1)资源有者(User)
2)认证授权服务器(jt-auth)
3)资源服务器(jt-resource)
4)客户端应用(jt-ui)
同时,在这种协议中规定了认证授权时的几种模式:
1)密码模式 (基于用户名和密码进行认证)
2)授权码模式(就是我们说的三方认证:QQ,微信,微博,。。。。)…
<dependency>
<groupId>org.springframework.cloud</groupId>
<artifactId>spring-cloud-starter-oauth2</artifactId>
</dependency>
加上依赖以后,项目启动时会显示一串登录密码,如图
默认登录地址localhost:8071
配置一下
server:
port: 8071
spring:
application:
name: spa-auth
cloud:
nacos:
discovery:
server-addr: localhost:8848
config:
server-addr: localhost:8848
登陆逻辑
有两种:
1.基于cookies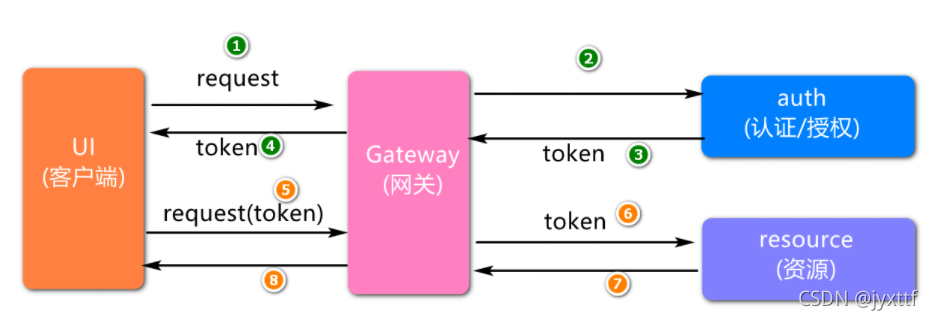
2.基于redis
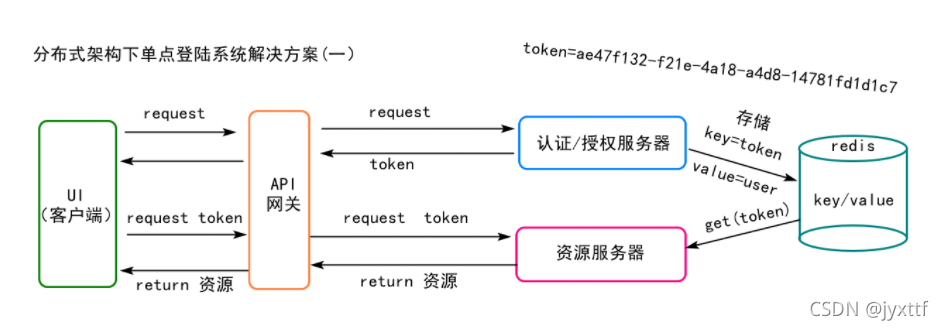
流程:
令牌生成对象配置 TokenStore
借助JWT(Json Web Token-是一种json格式
这是暗号,auth服务和所调用的资源服务都需要
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.security.authentication.AuthenticationManager;
import org.springframework.security.oauth2.provider.token.TokenStore;
import org.springframework.security.oauth2.provider.token.store.JwtAccessTokenConverter;
import org.springframework.security.oauth2.provider.token.store.JwtTokenStore;
@Configuration
public class TokenConfig {
//定义令牌签发口令(暗号),这个口令自己定义即可
//在对header和PAYLOAD部分进行签名时,需要的一个口令
private String SIGNING_KEY= "auth";
//初始化令牌生成策略(默认生成策略 UUID)
//这里采用JWT方式生成令牌
//构建令牌生成器对象
@Bean
public TokenStore tokenStore() {
return new JwtTokenStore(jwtAccessTokenConverter()); //JwtAccessTokenConverter
}
//Jwt转换器,将任何数据转换为jwt字符串
@Bean
public JwtAccessTokenConverter jwtAccessTokenConverter(){
JwtAccessTokenConverter converter=new JwtAccessTokenConverter();
//设置加密/解密口令
converter.setSigningKey(SIGNING_KEY);
return converter;
}
}
配置一下
server:
port: 8071
spring:
application:
name: sca-auth
cloud:
nacos:
discovery:
server-addr: localhost:8848
config:
server-addr: localhost:8848
auth服务
第一 认证授权服务器的核心配 AuthorizationServerConfigurerAdapter
package com.jt.auth.config;
import lombok.AllArgsConstructor;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.http.HttpMethod;
import org.springframework.security.authentication.AuthenticationManager;
import org.springframework.security.core.userdetails.UserDetailsService;
import org.springframework.security.crypto.password.PasswordEncoder;
import org.springframework.security.oauth2.config.annotation.configurers.ClientDetailsServiceConfigurer;
import org.springframework.security.oauth2.config.annotation.web.configuration.AuthorizationServerConfigurerAdapter;
import org.springframework.security.oauth2.config.annotation.web.configuration.EnableAuthorizationServer;
import org.springframework.security.oauth2.config.annotation.web.configurers.AuthorizationServerEndpointsConfigurer;
import org.springframework.security.oauth2.config.annotation.web.configurers.AuthorizationServerSecurityConfigurer;
import org.springframework.security.oauth2.provider.token.AuthorizationServerTokenServices;
import org.springframework.security.oauth2.provider.token.DefaultTokenServices;
import org.springframework.security.oauth2.provider.token.TokenEnhancerChain;
import org.springframework.security.oauth2.provider.token.TokenStore;
import org.springframework.security.oauth2.provider.token.store.JwtAccessTokenConverter;
import java.util.Arrays;
/**
* 完成所有配置的组装,在这个配置类中完成认证授权,JWT令牌签发等配置操作
* 1)SpringSecurity (安全认证和授权)
* 2)TokenConfig
* 3)Oauth2(暂时说)
*/
@AllArgsConstructor
@Configuration
@EnableAuthorizationServer //开启认证和授权服务
public class Oauth2Config extends AuthorizationServerConfigurerAdapter {
//此对象负责完成认证管理,自己创建的
private AuthenticationManager authenticationManager;
//TokenStore负责完成令牌创建,信息读取,自己创建的
private TokenStore tokenStore;
//负责获取用户详情信息(username,password,client_id,grant_type,client_secret)
//private ClientDetailsService clientDetailsService;
//JWT令牌转换器(基于用户信息构建令牌,解析令牌),自己创建的
private JwtAccessTokenConverter jwtAccessTokenConverter;
//密码加密匹配器对象
private PasswordEncoder passwordEncoder;
//负责获取用户信息信息,自己创建的
private UserDetailsService userDetailsService;
//设置认证端点的配置(/oauth/token),客户端通过这个路径获取JWT令牌
@Override
public void configure(AuthorizationServerEndpointsConfigurer endpoints) throws Exception {
endpoints
//配置认证管理器
.authenticationManager(authenticationManager)
//验证用户的方法获得用户详情
.userDetailsService(userDetailsService)
//要求提交认证使用post请求方式,提高安全性
.allowedTokenEndpointRequestMethods(HttpMethod.POST,HttpMethod.GET)
//要配置令牌的生成,由于令牌生成比较复杂,下面有方法实现
.tokenServices(tokenService());//这个不配置,默认令牌为UUID.randomUUID().toString()
}
//定义令牌生成策略
@Bean
public AuthorizationServerTokenServices tokenService(){
//这个方法的目标就是获得一个令牌生成器
DefaultTokenServices services=new DefaultTokenServices();
//支持令牌刷新策略(令牌有过期时间)
services.setSupportRefreshToken(true);
//设置令牌生成策略(tokenStore在TokenConfig配置了,本次我们应用JWT-定义了一种令牌格式)
services.setTokenStore(tokenStore);
//设置令牌增强(固定用法-令牌Payload部分允许添加扩展数据,例如用户权限信息)
//JWT令牌必须设置,假如普通令牌就不要设置了
TokenEnhancerChain chain=new TokenEnhancerChain();
chain.setTokenEnhancers(
Arrays.asList(jwtAccessTokenConverter));
//令牌增强对象设置到令牌生成
services.setTokenEnhancer(chain);
//设置令牌有效期
services.setAccessTokenValiditySeconds(3600);//1小时
//刷新令牌应用场景:一般在用户登录系统后,令牌快过期时,系统自动帮助用户刷新令牌,提高用户的体验感
services.setRefreshTokenValiditySeconds(3600*72);//3天
//配置客户端详情
//services.setClientDetailsService(clientDetailsService);
return services;
}
//设置客户端详情类似于用户详情,客户端传递到服务端的信息,是哪些信息时,服务端才会颁发令牌
@Override
public void configure(ClientDetailsServiceConfigurer clients) throws Exception {
clients.inMemory()
//客户端id
.withClient("gateway-client")
//客户端秘钥
.secret(passwordEncoder.encode("123456"))
//设置权限
.scopes("all")//all只是个名字而已和写abc效果相同
//允许客户端进行的操作 里面的字符串千万不能写错
.authorizedGrantTypes("password","refresh_token");
}
// 认证成功后的安全约束配置,由oauth2协议提供
// 这里规定了我们通过什么url访问令牌,检查令牌
// 而且这些url不需要认证就可以访问
@Override
public void configure(AuthorizationServerSecurityConfigurer security) throws Exception {
//认证通过后,允许客户端进行哪些操作
security
//公开oauth/token_key端点
.tokenKeyAccess("permitAll()")
//公开oauth/check_token端点
.checkTokenAccess("permitAll()")
//允许提交请求进行认证(申请令牌)
.allowFormAuthenticationForClients();
}
}
第二 安全配置类 WebSecurityConfigurerAdapter
SecurityConfig配置类,添加登录成功或失败的处理逻辑,
package com.jt.auth.config;
import com.fasterxml.jackson.databind.ObjectMapper;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.security.authentication.AuthenticationManager;
import org.springframework.security.config.annotation.web.builders.HttpSecurity;
import org.springframework.security.config.annotation.web.configuration.WebSecurityConfigurerAdapter;
import org.springframework.security.crypto.bcrypt.BCryptPasswordEncoder;
import org.springframework.security.web.authentication.AuthenticationFailureHandler;
import org.springframework.security.web.authentication.AuthenticationSuccessHandler;
import javax.servlet.http.HttpServletResponse;
import java.io.IOException;
import java.io.PrintWriter;
import java.util.HashMap;
import java.util.Map;
@Configuration
public class SecurityConfig extends WebSecurityConfigurerAdapter {
/**初始化密码加密对象*/
@Bean
public BCryptPasswordEncoder passwordEncoder(){
return new BCryptPasswordEncoder();
}
/**配置认证管理器(此对象主要负责对客户端输入的用户信息进行认证),
* 在其它配置类中会用到这个对象*/
@Bean
public AuthenticationManager authenticationManagerBean()
throws Exception {
return super.authenticationManagerBean();
}
/**在这个方法中定义登录规则
* 1)对所有请求放行(当前工程只做认证)
* 2)登录成功信息的返回
* 3)登录失败信息的返回
* */
@Override
protected void configure(HttpSecurity http) throws Exception {
//关闭跨域工具
http.csrf().disable();
//放行所有请求
http.authorizeRequests().anyRequest().permitAll();
//登录成功与失败的处理
http.formLogin()
.successHandler(successHandler())
.failureHandler(failureHandler());
}
@Bean
public AuthenticationSuccessHandler successHandler(){
// return new AuthenticationSuccessHandler() {
// @Override
// public void onAuthenticationSuccess(HttpServletRequest httpServletRequest, HttpServletResponse httpServletResponse, Authentication authentication) throws IOException, ServletException {
//
// }
// }
return (request,response,authentication) ->{
//1.构建map对象,封装响应数据
Map<String,Object> map=new HashMap<>();
map.put("state",200);
map.put("message","login ok");
//2.将map对象写到客户端
writeJsonToClient(response,map);
};
}
@Bean
public AuthenticationFailureHandler failureHandler(){
return (request,response, e)-> {
//1.构建map对象,封装响应数据
Map<String,Object> map=new HashMap<>();
map.put("state",500);
map.put("message","login failure");
//2.将map对象写到客户端
writeJsonToClient(response,map);
};
}
private void writeJsonToClient(HttpServletResponse response,
Object object) throws IOException {
//1.将对象转换为json
//将对象转换为json有3种方案:
//1)Google的Gson-->toJson (需要自己找依赖)
//2)阿里的fastjson-->JSON (spring-cloud-starter-alibaba-sentinel)
//3)Springboot web自带的jackson-->writeValueAsString (spring-boot-starter-web)
//我们这里借助springboot工程中自带的jackson
//jackson中有一个对象类型为ObjectMapper,它内部提供了将对象转换为json的方法
//例如:
String jsonStr=new ObjectMapper().writeValueAsString(object);
//3.将json字符串写到客户端
PrintWriter writer = response.getWriter();
writer.println(jsonStr);
writer.flush();
}
//创建认证管理器对象,授权服务器会用到
@Bean
public AuthenticationManager authenticationManagerBean()
throws Exception {
return super.authenticationManagerBean();
}
}
资源服务
第三 资源服务令牌解析 ResourceServerConfigurerAdapter
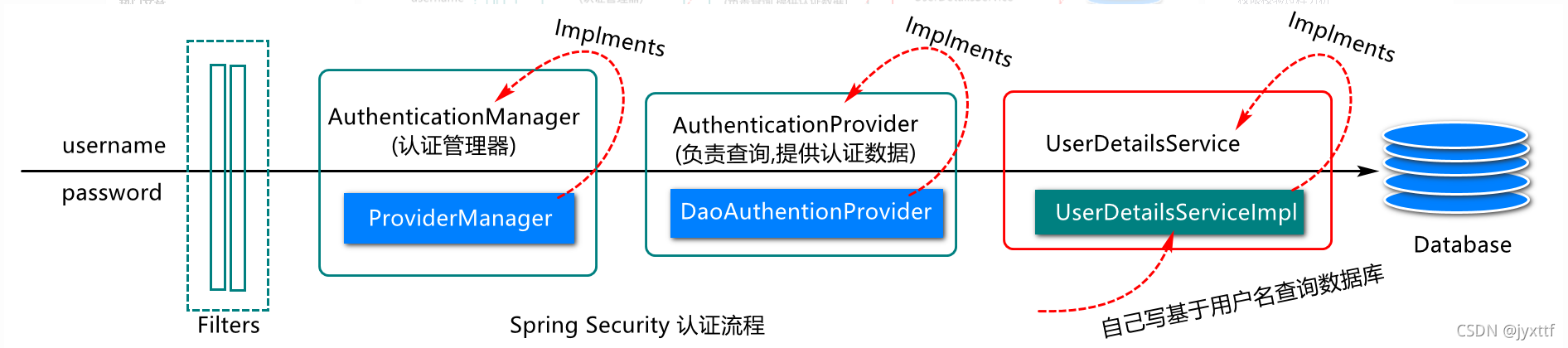
spring security应用中底层会借助UserDetailService对象获取数据库信息,并进行封装,最后返回给认证管理器,完成认证操作
package cn.jjj.resource.config;
import com.fasterxml.jackson.databind.ObjectMapper;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.context.annotation.Configuration;
import org.springframework.security.config.annotation.method.configuration.EnableGlobalMethodSecurity;
import org.springframework.security.config.annotation.web.builders.HttpSecurity;
import org.springframework.security.oauth2.config.annotation.web.configuration.EnableResourceServer;
import org.springframework.security.oauth2.config.annotation.web.configuration.ResourceServerConfigurerAdapter;
import org.springframework.security.oauth2.config.annotation.web.configurers.ResourceServerSecurityConfigurer;
import org.springframework.security.oauth2.provider.token.TokenStore;
import org.springframework.security.web.access.AccessDeniedHandler;
import javax.servlet.http.HttpServletResponse;
import java.io.PrintWriter;
import java.util.HashMap;
import java.util.Map;
@Configuration
@EnableResourceServer
@EnableGlobalMethodSecurity(prePostEnabled = true)
public class ResourceServerConfig extends ResourceServerConfigurerAdapter {
@Autowired
private TokenStore tokenStore;
/**
* token服务配置
*/
@Override
public void configure(ResourceServerSecurityConfigurer resources) throws Exception {
resources.tokenStore(tokenStore);
}
/**
* 路由安全认证配置
*/
@Override
public void configure(HttpSecurity http) throws Exception {
http.csrf().disable();
http.exceptionHandling() //不携带令牌去访问,会提示请先登录(认证)
.accessDeniedHandler(accessDeniedHandler());
http.authorizeRequests().anyRequest().permitAll();
}
//没有权限时执行此处理器方法
public AccessDeniedHandler accessDeniedHandler() {
return (request, response, e) -> {
Map<String, Object> map = new HashMap<>();
map.put("state", HttpServletResponse.SC_FORBIDDEN);//SC_FORBIDDEN的值是403
map.put("message", "没有访问权限,请联系管理员");
//1设置响应数据的编码
response.setCharacterEncoding("utf-8");
//2告诉浏览器响应数据的内容类型以及编码
response.setContentType("application/json;charset=utf-8");
//3获取输出流对象
PrintWriter out=response.getWriter();
//4 输出数据
String result=
new ObjectMapper().writeValueAsString(map);
out.println(result);
out.flush();
};
}
}
第四 权限控制
访问此方法需要具备的权限
@PreAuthorize("hasAuthority('sys:res:create')")
@PostMapping("/upload/")
public String uploadFile(MultipartFile uploadFile) throws IOException {
...
}