写在最前
-
Spring 团队正式宣布 Spring Security OAuth 停止维护,该项目将不会再进行任何的迭代;
-
目前 Spring 生态中的 OAuth2 授权服务器是 Spring Authorization Server 已经可以正式生产使用;
-
作为 SpringBoot 3.0 的过渡版本 SpringBoot 2.7.0 过期了大量关于 SpringSecurity 的配置类,如沿用旧版本过期配置无法向上升级;
-
可以阅读【安全篇】Spring Boot 整合 Spring Security 安全框架,学习一下 Spring Security OAuth 认证;
Spring Authorization Server
Demo 地址:mingyue-springboot-sas
Spring Authorization Server (以下简称 SAS)是 Spring 团队最新开发适配 OAuth 协议的授权服务器项目,旨在替代原有的 Spring Security OAuth Server。目前已经发布了 0.3.1 版本,已支持授权码、客户端、刷新、注销等 OAuth 协议。SAS 项目已经迁移至官方正式仓库维护,成为官方的正式子项目。
Spring Boot 整合 SAS
1.添加依赖
<!-- SAS 依赖 -->
<dependency>
<groupId>org.springframework.security</groupId>
<artifactId>spring-security-oauth2-authorization-server</artifactId>
<version>0.3.1</version>
</dependency>
<!-- Springboot Security -->
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-security</artifactId>
</dependency>
2.授权码模式认证
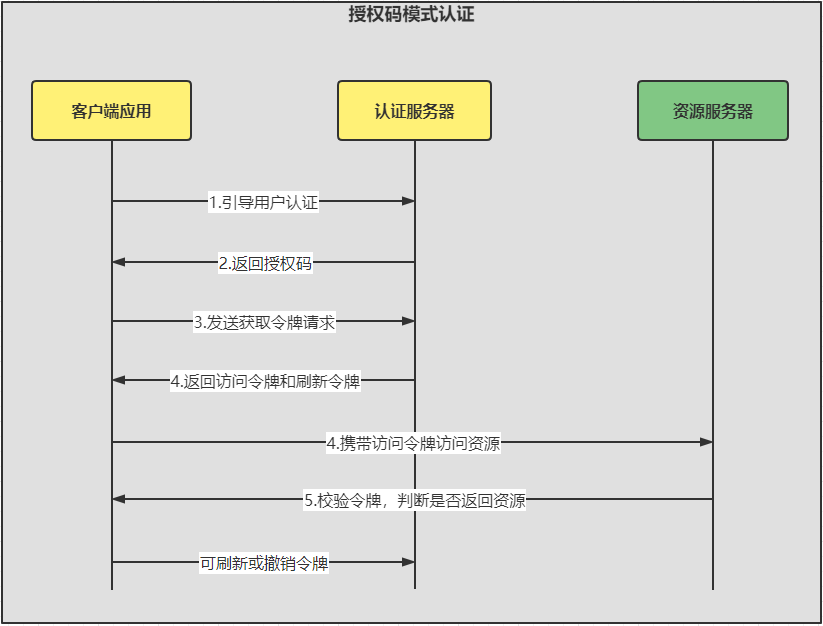
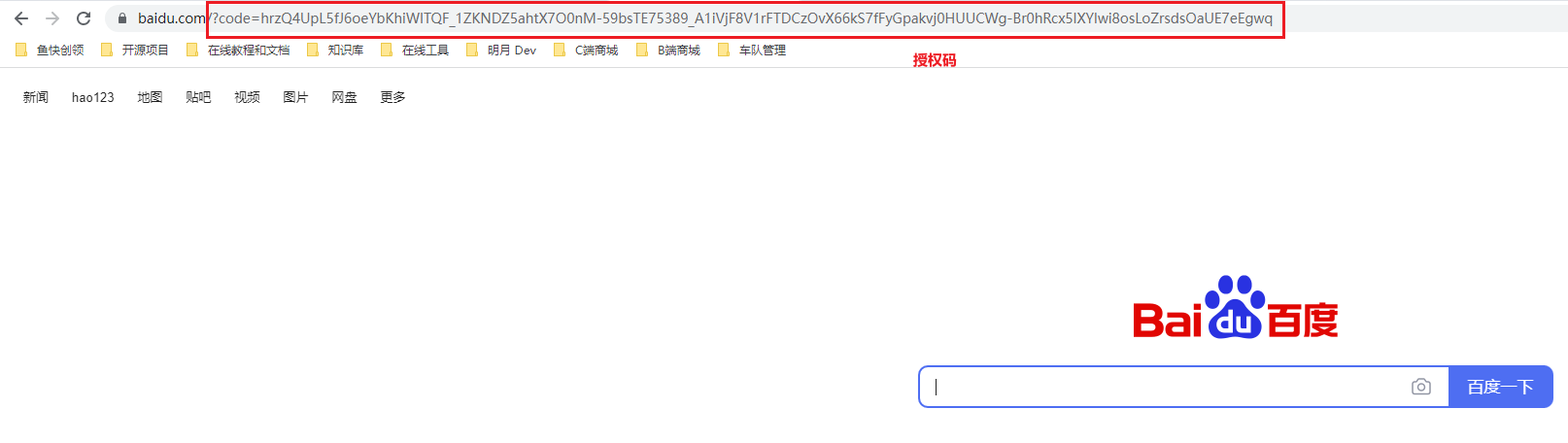
2.1.获取授权码
账号:mingyue
密码:123456
http://localhost:3000/oauth2/authorize?client_id=baidu&client_secret=baidu&response_type=code&redirect_uri=https://www.baidu.com
2.2.获取令牌
curl --location --request POST 'http://localhost:3000/oauth2/token' \
--header 'Authorization: Basic YmFpZHU6YmFpZHU=' \
--header 'Content-Type: application/x-www-form-urlencoded' \
--data-urlencode 'grant_type=authorization_code' \
--data-urlencode 'code=hrzQ4UpL5fJ6oeYbKhiWITQF_1ZKNDZ5ahtX7O0nM-59bsTE75389_A1iVjF8V1rFTDCzOvX66kS7fFyGpakvj0HUUCWg-Br0hRcx5IXYlwi8osLoZrsdsOaUE7eEgwq' \
--data-urlencode 'redirect_uri=https://www.baidu.com'
返回示例:
{
"access_toke n": "cM_htxUi2r7s5YqmZ31fqmWSGroJcnFIxMdfbscP9N0wd8NWx9j3qeH-C6Iej6lxKVRp0QLA3kDQgmKkvrXTGz3bhlqAkoFv8bR-QeqdCuUBks9bVcU9986stEF9k2bs",
"refresh_token": "ZaOys78E8VqESI9wAY5ISD2JWbPhOELnpICeiO6vPcE7bJik7qG-NWI59hXW6uw2lSJjrYzrxzFqohBk0TpA28Mj1_i030JiYniAf9hNWPt5iN0dld6J40y3fKfD_7Uq",
"token_type": "Bearer",
"expires_in": 299
}
2.3.刷新令牌
curl --location --request POST 'http://localhost:3000/oauth2/token' \
--header 'Authorization: Basic YmFpZHU6YmFpZHU=' \
--header 'Content-Type: application/x-www-form-urlencoded' \
--data-urlencode 'grant_type=refresh_token' \
--data-urlencode 'refresh_token=ZaOys78E8VqESI9wAY5ISD2JWbPhOELnpICeiO6vPcE7bJik7qG-NWI59hXW6uw2lSJjrYzrxzFqohBk0TpA28Mj1_i030JiYniAf9hNWPt5iN0dld6J40y3fKfD_7Uq'
返回示例:
{
"access_toke n": "F4ZR5L0BIrfolBh7v65rxvEv1cr5R6URtTftLBO-dYbpwzQQbokUW9TXeWLj3rcYWLHNnBPupIafdPZ8EOEQc50V7bxfXPh-ZmaBTnfBtrjqyVm3GsbLqdG7tY8295Rj",
"refresh_token": "ZaOys78E8VqESI9wAY5ISD2JWbPhOELnpICeiO6vPcE7bJik7qG-NWI59hXW6uw2lSJjrYzrxzFqohBk0TpA28Mj1_i030JiYniAf9hNWPt5iN0dld6J40y3fKfD_7Uq",
"token_type": "Bearer",
"expires_in": 300
}
2.4.撤销令牌
- 通过 access_token
curl --location --request POST 'http://localhost:3000/oauth2/revoke' \
--header 'Authorization: Basic YmFpZHU6YmFpZHU=' \
--header 'Content-Type: application/x-www-form-urlencoded' \
--data-urlencode 'token=F4ZR5L0BIrfolBh7v65rxvEv1cr5R6URtTftLBO-dYbpwzQQbokUW9TXeWLj3rcYWLHNnBPupIafdPZ8EOEQc50V7bxfXPh-ZmaBTnfBtrjqyVm3GsbLqdG7tY8295Rj' \
--data-urlencode 'token_type_hint=access_token'
- 通过 refresh_token
curl --location --request POST 'http://localhost:3000/oauth2/revoke' \
--header 'Authorization: Basic YmFpZHU6YmFpZHU=' \
--header 'Content-Type: application/x-www-form-urlencoded' \
--data-urlencode 'token=ZaOys78E8VqESI9wAY5ISD2JWbPhOELnpICeiO6vPcE7bJik7qG-NWI59hXW6uw2lSJjrYzrxzFqohBk0TpA28Mj1_i030JiYniAf9hNWPt5iN0dld6J40y3fKfD_7Uq' \
--data-urlencode 'token_type_hint=refresh_token'
3.密码模式认证

3.1.密码登录
curl -X GET -F 'username=mingyue' -F 'password=123456' http://localhost:3000/password/login
返回示例:
{
"access_toke n": "FEIWp8cpWPLeZN9UHfpqj2ZwIqJrDd0pZsntYgj92LgOgM_K5gklmM4dVzuLHdxdgzYIDECZIDDbVS_K385L-Y-JOal6OqNmFdTOBgW7h1-w6HXEvH8A1Jmzxjn8N9dA",
"refresh_token": "Jb-LNN1cfdryNLgH5XTc3TFYOMKzaBa2tPJb1gAs7kcpL6mjbimzFyWBD18Y9LeHGEHymtpTgDQNiLg_BZkaVbfP3Umxf1QsSxDZRJ8l6XBmg-_zdogIWsYyyHTSrLr1",
"license": "mingyue",
"token_type": "Bearer",
"expires_in": 300
}
3.2.获取认证信息
curl -X GET -F 'token=FEIWp8cpWPLeZN9UHfpqj2ZwIqJrDd0pZsntYgj92LgOgM_K5gklmM4dVzuLHdxdgzYIDECZIDDbVS_K385L-Y-JOal6OqNmFdTOBgW7h1-w6HXEvH8A1Jmzxjn8N9dA' http://localhost:3000/password/info
返回示例:
{
"id": "653afaf5-764f-4c29-a016-cfa5fa1a7694",
"registeredClientId": "baidu",
"principalName": "mingyue",
"authorizationGrantType": {
"value": "password"
},
"attributes": {},
"refreshToken": {
"token": {
"tokenValue": "Jb-LNN1cfdryNLgH5XTc3TFYOMKzaBa2tPJb1gAs7kcpL6mjbimzFyWBD18Y9LeHGEHymtpTgDQNiLg_BZkaVbfP3Umxf1QsSxDZRJ8l6XBmg-_zdogIWsYyyHTSrLr1",
"issuedAt": "2022-08-01T08:30:46.295Z",
"expiresAt": "2022-08-01T09:30:46.295Z"
},
"metadata": {
"metadata.token.invalidated": false
},
"active": true,
"claims": null,
"expired": false,
"invalidated": false,
"beforeUse": false
},
"accessToken": {
"token": {
"tokenValue": "FEIWp8cpWPLeZN9UHfpqj2ZwIqJrDd0pZsntYgj92LgOgM_K5gklmM4dVzuLHdxdgzYIDECZIDDbVS_K385L-Y-JOal6OqNmFdTOBgW7h1-w6HXEvH8A1Jmzxjn8N9dA",
"issuedAt": "2022-08-01T08:30:46.295Z",
"expiresAt": "2022-08-01T08:35:46.295Z",
"tokenType": {
"value": "Bearer"
},
"scopes": []
},
"metadata": {
"metadata.token.claims": {
"sub": "mingyue",
"aud": [
"baidu"
],
"nbf": "2022-08-01T08:30:46.295Z",
"exp": "2022-08-01T08:35:46.295Z",
"iat": "2022-08-01T08:30:46.295Z",
"jti": "ccae9f3d-8003-4ba3-ae40-89d2f731babc"
},
"metadata.token.invalidated": false
},
"active": false,
"claims": {
"sub": "mingyue",
"aud": [
"baidu"
],
"nbf": "2022-08-01T08:30:46.295Z",
"exp": "2022-08-01T08:35:46.295Z",
"iat": "2022-08-01T08:30:46.295Z",
"jti": "ccae9f3d-8003-4ba3-ae40-89d2f731babc"
},
"expired": true,
"invalidated": false,
"beforeUse": false
}
}