前言
随着工作项目的变换,我发现自己使用加密算法的次数原来越多,因为自己记忆力比较差(就是菜),每次都需要翻别人的博客,特设定本文章,用于记录python使用各种加密方式的记录。
md5 算法(hash)
# -*- coding:utf-8 -*-
import hashlib
# 该函数实现对指定字符串取md5值
def getmd5(str):
m = hashlib.md5()
m.update(str.encode("utf-8"))
return m.hexdigest()
# 这里需要注意一个点,那就说如果要对json类型字符串进行hash,需要处理:与值之间的空格,具体参考我的另一篇文章:https://blog.csdn.net/weixin_42380348/article/details/121795572
print(getmd5('abcderg'))
AES加解密(对称)
1、AES有5中加密模式,这里使用使用AES.MODE_CBC,该模式需要指定一个vi,vi指初始化向量,如果不指定初始化向量,每次的加密结果都不一致,解密时也需要使用相同的初始化向量
2、AES加密算法只能以Block模式加密,且Block大小为16Byte,因此加密的明文需要是16的整数倍,如果不足需要padding到16的倍数
3、AES加密的key大小可以为,16、24、32,对应到128bit、192bit、256bit.
注:AES5种加密模式
1.电码本模式(Electronic Codebook Book (ECB)
2.密码分组链接模式(Cipher Block Chaining (CBC))
3.计算器模式(Counter (CTR))
4.密码反馈模式(Cipher FeedBack (CFB))
5.输出反馈模式(Output FeedBack (OFB))
import base64
from Crypto.Cipher import AES
def get_enAes(data):
# 解决加密明文不是16的整数倍问题
pad = lambda s: s + (16 - len(s) % 16) * chr(16 - len(s) % 16)
# 去除加密明文右侧的空白符
data = pad(data.rstrip())
# 这个用作iv,初始化向量
key16 = 'de03a088357803gf'
# 这个是AES加密用到的key
key32 = 'a0ea98d098989loki96709oipd388jgn'
# 统一编码一下
iv = key16.encode('utf-8')
key = key32.encode('utf-8')
data1 = data.encode('utf-8')
# 定义加密模式
model = AES.MODE_CBC
# 创建AES对象
endata = AES.new(key, model, iv)
# 进行加密
endata_res = endata.encrypt(data1)
# 将返回的字节型数据转进行base64编码
res = base64.b64encode(endata_res)
return res.decode()
def get_deAes(data):
# 这个用作iv,初始化向量
key16 = '2f03e088357803f1'
# 这个是AES加密用到的key
key32 = 'a0ea98d540989e5aa96709oipd388bjk'
iv = key16.encode('utf-8')
key = key32.encode('utf-8')
# 定义加密模式
model = AES.MODE_CBC
# 创建AES对象
dedata = AES.new(key, model, iv)
#进行解密
res = dedata.decrypt(base64.b64decode(data))
return res.decode()
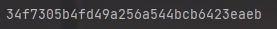
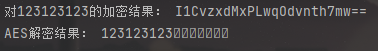
endata = get_enAes('123123123')
print("对123123123的加密结果:",endata)
print("AES解密结果:",get_deAes(endata))
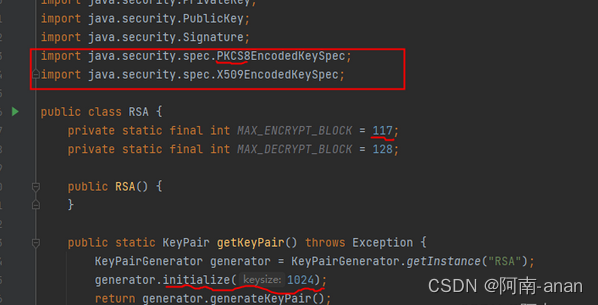
rsa非对称加解(适用于java项目的接口测试)
本次进行rsa加密源于一次针对接口的渗透测试,该接口采用rsa对关键数据进行加密,然后又采用rsa进行签名,整个过程设计两对秘钥,下图是研发给我的java的rsa加密示例(有完整的示例,这里不予展示),我需要根据该示例实现加密和签名并进行渗透测试。
python对应的rsa加密方式及解密示例
# -*- coding:utf-8 -*-
import Crypto
import base64
from Crypto.PublicKey import RSA
# 关键在这里 使用Crypto模块中的pkcs1_v1_5。就是对应pkcs8的格式了
from Crypto.Cipher import PKCS1_v1_5 as Cipher_pkcs1_v1_5
# 前提
# PKCS8EncodedKeySpec
# X509EncodedKeySpec
# 1024
# 签名:md5withrsa
# rsa加密
# 参考https://blog.csdn.net/soulwyb/article/details/111354661
def enRsa(msg,pub_key):
rsakey = RSA.importKey(pub_key)
cipher = Cipher_pkcs1_v1_5.new(rsakey)
encrypt_bytes = cipher.encrypt(msg.encode(encoding='utf-8'))
cipher_text = base64.b64encode(encrypt_bytes)
# return request.quote(cipher_text)
return cipher_text.decode()
# 分段加密函数,调用了下方获取公钥长度的函数
def enRsaLog(msg,pub_key):
length = len(msg)
public_key = RSA.importKey(pub_key)
default_length = int(get_max_length(public_key))
pub_obj = Cipher_pkcs1_v1_5.new(public_key)
# 长度不用分段
if length < default_length:
return base64.b64encode(pub_obj.encrypt(msg.encode(encoding='utf-8')))
# 需要分段
offset = 0
res = []
while length - offset > 0:
if length - offset > default_length:
res.append(pub_obj.encrypt(msg[offset:offset + default_length].encode(encoding='utf-8')))
else:
res.append(pub_obj.encrypt(msg[offset:].encode(encoding='utf-8')))
offset += default_length
byte_data = b''.join(res)
return base64.b64encode(byte_data)
# 获取rsa能够一次能够加密的长度
def get_max_length(rsa_key, encrypt=True):
blocksize = Crypto.Util.number.size(rsa_key.n) / 8 # :param rsa_key: 钥匙.
reserve_size = 11 # 预留位为11
if not encrypt: # 解密时不需要考虑预留位 # :param encrypt: 是否是加密.
reserve_size = 0
maxlength = blocksize - reserve_size
return maxlength
#--=======================================rsa解密==========================================================--
# 分段解密:
def dec_rsa(rsa_msg,pri_key):
msg = base64.b64decode(rsa_msg)
length = len(msg)
private_key = RSA.importKey(pri_key)
max_length = int(get_max_length(private_key, False))
private_obj = Cipher_pkcs1_v1_5.new(private_key)
# 长度不用分段
if length < max_length:
return b''.join(private_obj.decrypt(msg, b'xyz'))
# 需要分段
offset = 0
res = []
while length - offset > 0:
if length - offset > max_length:
res.append(private_obj.decrypt(msg[offset:offset + max_length], b'xyz'))
else:
res.append(private_obj.decrypt(msg[offset:], b'xyz'))
offset += max_length
return res
if __name__ == '__main__':
msg = "12345678909090909090080080845678909090909090080084567890909090909008008456789090909090900800845678909090909090080084567890909090909008008456789090909090900800845678909090909090080084567890909090909008008"
pub_key = """-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDK8ry98taCozOfcmv2KlEOE5EvJXChpsa/N4fa6CBa/HLjz4A3A7aviP6qhhaW1h8kKywSZyjQtplURIb0HkSrZGMTVehTtk641rxtEutioARdN/2q/XoHS6fL+OheVXOs9c7uV3bflWybqtCg5i4FY1CIwvbpVArRcXxo6U2k2wIDAQAB
-----END PUBLIC KEY-----"""
pri_key = """-----BEGIN PRIVATE KEY-----
MIICdgIBADANBgkqhkiG9w0BAQEFAASCAmAwggJcAgEAAoGBAMryvL3y1oKjM59ya/YqUQ4TkS8lcKGmxr83h9roIFr8cuPPgDcDtq+I/qqGFpbWHyQrLBJnKNC2mVREhvQeRKtkYxNV6FO2TrjWvG0S62KgBF03/ar9egdLp8v46F5Vc6z1zu5Xdt+VbJuq0KDmLgVjUIjC9ulUCtFxfGjpTaTbAgMBAAECgYAtNwFX7GdgOY4BwxNMh8cBNNjOwS+jxC1ZYrzQx5CV1NKf8JXnK9uipgne4frcZh4QB9JM01Djlxr4DEBo2OmBRE5ghXkreuHyZsN3EWWalgyO8yksHM/MsCARkfFDmXn1rM5fvrCMHINfXv+jQvgUOVaVVyvdhJDWaOsOPZwcOQJBAOToQgs8GkbnKghwsfxWm5T09870VGnQ44uiwhNYrIpucbTMcrejlaSynHHgD4J1dh9rcSy6MG4No9NxMTi0rt8CQQDi9++20m3/kj7uLFmAbxTuWyOPpGDMgR7Xlp7x6FCGNgF4GQDSXjTmTa4JtJ4tkqrWXoyW1Gf1Uvw/o0LmOZWFAkEA1uI5bXaEbF8BFF9Glk1vTAwSvVKcE6GmmiS175dkkadQUptCbaXBCpUpS7U8mglOU/x2h7hZUla3nfw6arMjHQJATLlXdUvJF13OnCCt2La0MqbobIQ6nKcBUAuAi3Hm1penA3wgRPzHkRqtPGasGee8jF7F067VvZ5h2vlLghvxKQJAaIxu3NMMkdlXXOvcU1P43nlbu86j3CwuN3zBvxdAmVp5eKfeEbd6Gh1eo47QEblqS+W1IbrbKx1Y2sjfX+xhpA==
-----END PRIVATE KEY-----
"""
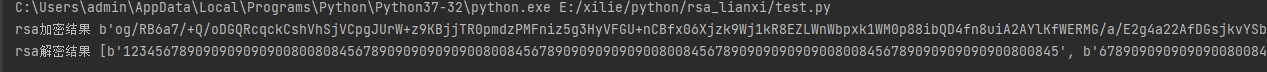
endata = enRsaLog(msg,pub_key)
print("rsa加密结果" , endata)
print("rsa解密结果" , dec_rsa(endata,pri_key))