android-app-100
题目有Android,下载是.apk文件,打开雷电模拟器,下载apk
用JEB打开,解析a
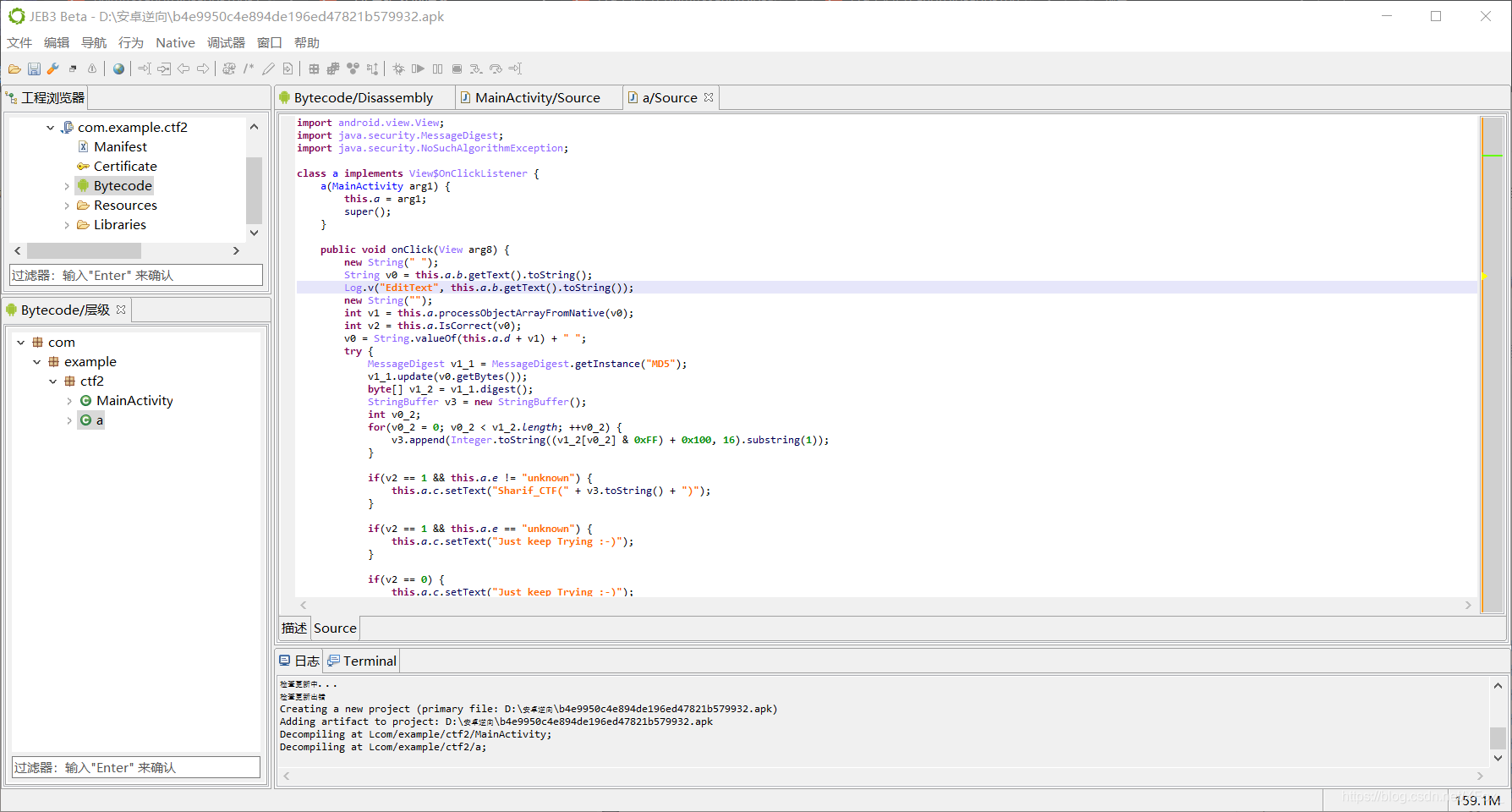
发现主要函数
public void onClick(View arg8) {
new String(" ");
String v0 = this.a.b.getText().toString(); //输入字符
Log.v("EditText", this.a.b.getText().toString());
new String("");
int v1 = this.a.processObjectArrayFromNative(v0);
int v2 = this.a.IsCorrect(v0);//定义函数
v0 = String.valueOf(this.a.d + v1) + " ";
try {
MessageDigest v1_1 = MessageDigest.getInstance("MD5");//MD5加密
v1_1.update(v0.getBytes());
byte[] v1_2 = v1_1.digest();
StringBuffer v3 = new StringBuffer();
int v0_2;
for(v0_2 = 0; v0_2 < v1_2.length; ++v0_2) {
v3.append(Integer.toString((v1_2[v0_2] & 0xFF) + 0x100, 16).substring(1)); //转16进制
}
if(v2 == 1 && this.a.e != "unknown") {
this.a.c.setText("Sharif_CTF(" + v3.toString() + ")");
} //输出16进制,就是flag
if(v2 == 1 && this.a.e == "unknown") {
this.a.c.setText("Just keep Trying :-)");
}
if(v2 == 0) {
this.a.c.setText("Just keep Trying :-)");
}
return;
}
catch(NoSuchAlgorithmException v0_1) {
v0_1.printStackTrace();
return;
分析算法发现最重要的是processObjectArrayFromNative和IsCorrect函数
拖进ida,查看字符串,找到IsCorrect函数
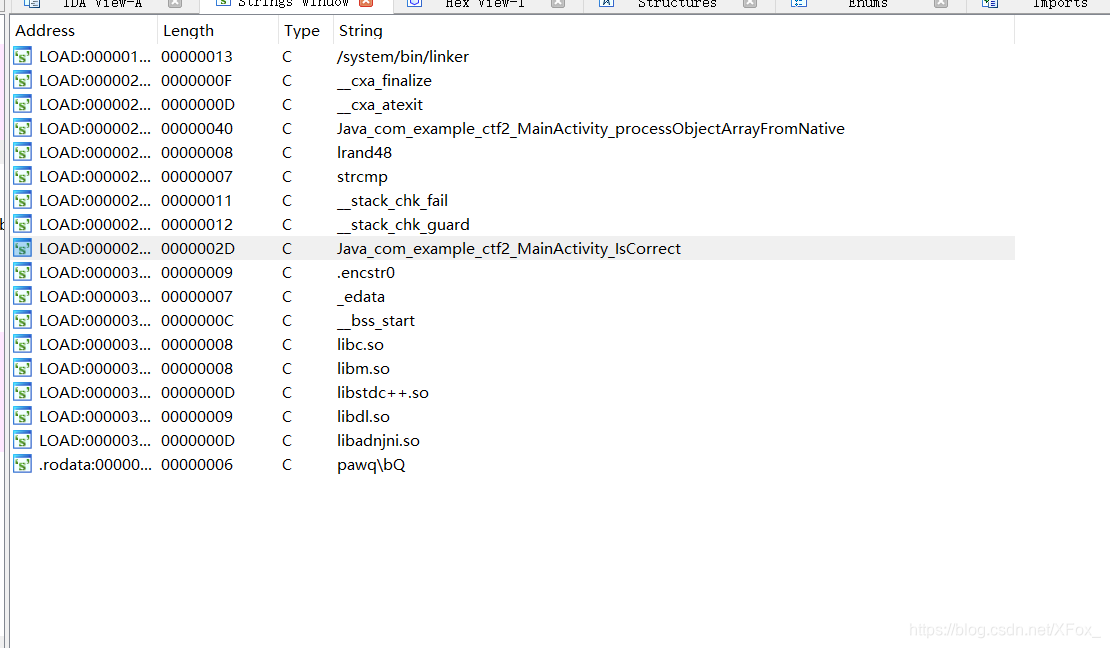
IsCorrect:
v9 = (char *)(*(int (__fastcall **)(int, int, _DWORD))(*(_DWORD *)a1 + 676))(a1, a3, 0);
strcpy(v12, "ef57f3fe3cf603c03890ee588878c0ec");
v4 = 0;
v12[33] = 53;
v10 = j_strcmp(v9, v12);
v5 = 1701458332;
while ( 1 )
{
while ( 1 )
{
while ( 1 )
{
v6 = v5;
v5 = 809244963;
if ( v6 <= 1701458331 )
break;
v5 = -333293478;
if ( v10 )
v5 = -158041539;
}
if ( v6 <= 809244962 )
break;
(*(void (__fastcall **)(int, int, char *))(*(_DWORD *)a1 + 680))(a1, a3, v9);
v11 = v4;
v5 = -326599761;
}
if ( v6 != -158041539 )
{
v4 = 1;
v5 = -158041539;
if ( v6 != -333293478 )
break;
}
}
return v11;
}
processObjectArrayFromNative:
v16 = a3;
v15 = a1;
v3 = -1661035768;
while ( 1 )
{
while ( 1 )
{
while ( 1 )
{
while ( v3 <= -1303766071 )
v3 = 2063008300;
if ( v3 > 441419317 )
break;
v3 = 1800572839;
if ( !v25 )
v3 = 441419318;
}
if ( v3 > 867851767 )
break;
v3 = 1405326207;
}
if ( v3 <= 1405326206 )
break;
if ( v3 == 1405326207 )
{
*v24 = j_lrand48();
(*(void (__fastcall **)(_DWORD, int, int))(*(_DWORD *)*v20 + 680))(*v20, *v21, *v23);
v26 = *v22;
v3 = 867851768;
}
发现都要处理字符串ef57f3fe3cf603c03890ee588878c0ec
在雷电模拟器中输入
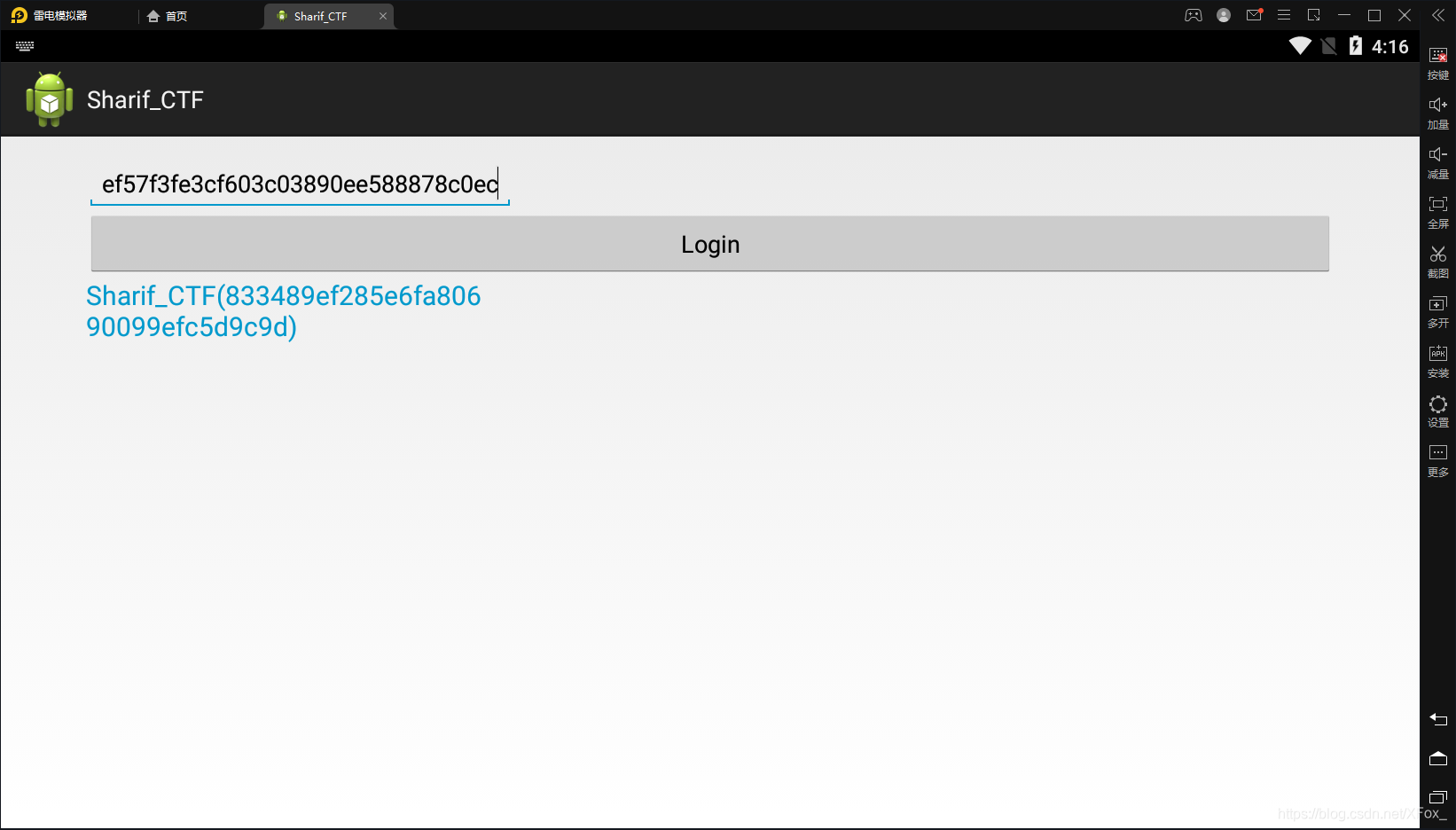
得到flag:Sharif_CTF(833489ef285e6fa80690099efc5d9c9d)