《OpenShift 4.x HOL教程汇总》
本文在 OpenShift 4.9 和 RHACS 3.67.1 环境中进行验证。
DevSecOps Pipeline Demo 是使用以下环境的 CI/CD Pipeline,它使用的是基于 Tekton 驱动的 OpenShift Pipeline 组件驱动运行。而 RHACS 负责对镜像进行安全扫描。
- RHACS
- SonarQube
- Nexus
- JUnit
- Gogs
- Git Webhook
- Gatling
- Zap Proxy
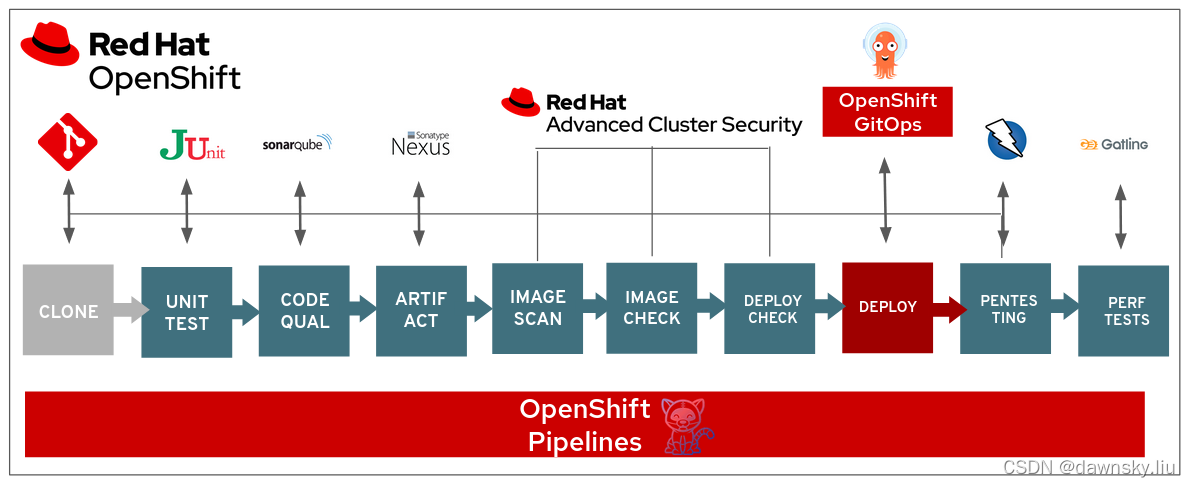
安装 DevSecOps Pipeline 演示环境
- 下载 devsecops demo 应用资源
$ git clone https://github.com/rcarrata/devsecops-demo.git
$ ansible-galaxy collection install community.kubernetes
$ cd devsecops-demo
- 设置 RHACS 的访问密码
$ ACS_PASSWORD=$(oc -n stackrox get secret central-htpasswd -o jsonpath={.data.htpasswd})
$ cat > bootstrap/roles/ocp4-install-acs/templates/acs-password.yml.j2 << EOF
kind: Secret
apiVersion: v1
metadata:
name: acs-password
namespace: stackrox
data:
password: ${ACS_PASSWORD}
type: Opaque
EOF
- 安装 devsecops demo 应用资源
$ ./install.sh
。。。
PLAY RECAP *********************************************************************************************************************************************************
localhost : ok=65 changed=9 unreachable=0 failed=0 skipped=0 rescued=0 ignored=0
- 查看 DevSecOps 相关环境
$ ./status.sh
## GOGS Server - Username/Password: gogs/gogs ##
http://gogs-cicd.apps.cluster-mcz5p.mcz5p.sandbox1644.opentlc.com
## Nexus Server - Username/Password: admin/admin123 ##
https://nexus-cicd.apps.cluster-mcz5p.mcz5p.sandbox1644.opentlc.com
## Sonarqube Server - Username/Password: admin/admin ##
https://sonarqube-cicd.apps.cluster-mcz5p.mcz5p.sandbox1644.opentlc.com
## Reports Server - Username/Password: reports/reports ##
http://reports-repo-cicd.apps.cluster-mcz5p.mcz5p.sandbox1644.opentlc.com
## ACS/Stackrox Server - Username/Password: admin/stackrox ##
https://central-stackrox.apps.cluster-mcz5p.mcz5p.sandbox1644.opentlc.com
## ArgoCD Server - Username/Password: admin/[DEX] ##
https://openshift-gitops-server-openshift-gitops.apps.cluster-mcz5p.mcz5p.sandbox1644.opentlc.com
运行 DevSecOps Pipeline
- 执行命令,运行 DevSecOps Pipeline。
$ ./demo.sh start
# INFO: ## Executing Dev Pipeline... ##
pipelinerun.tekton.dev/petclinic-build-devc9ptn created
# INFO: Check the pipeline in:
https://console-openshift-console.apps.cluster-mcz5p.mcz5p.sandbox1644.opentlc.com/pipelines/ns/cicd/pipeline-runs
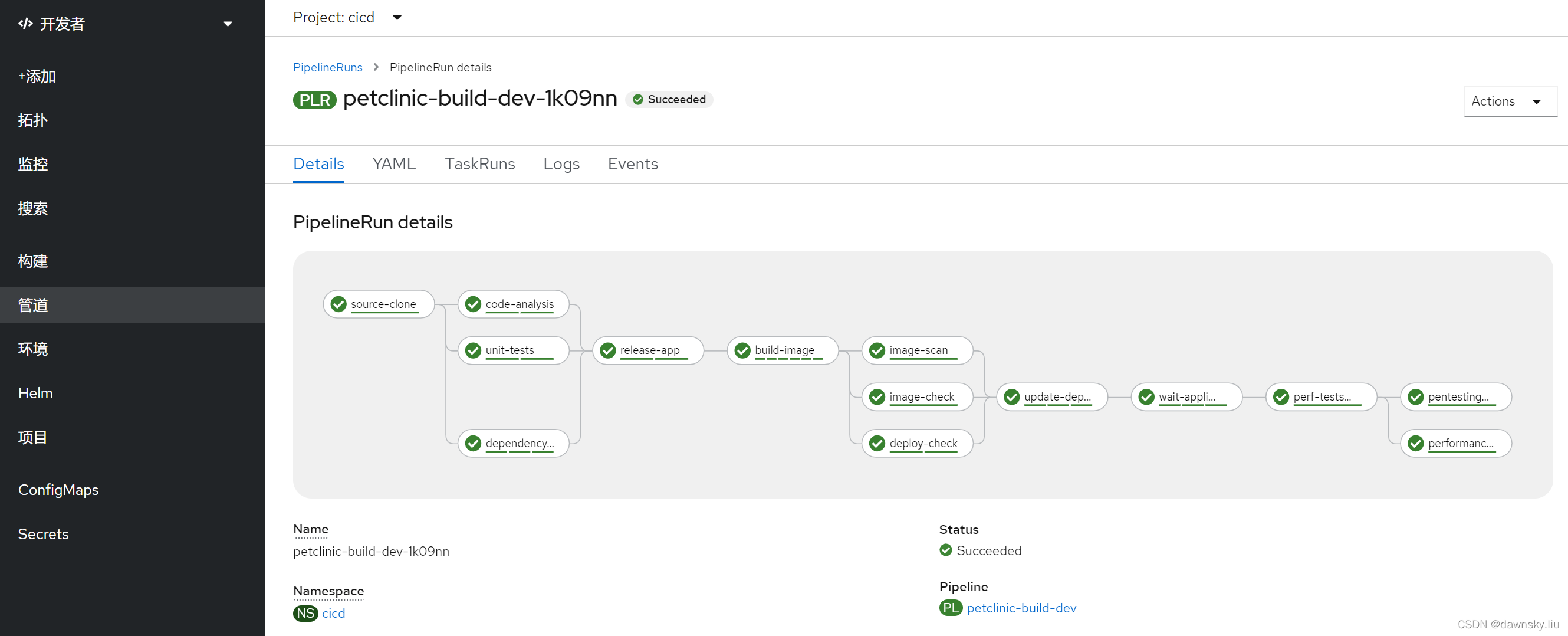
- 查看 Pipeline 运行状态,此时管道运行状态是“失败”。然后进入下图的“日志”。
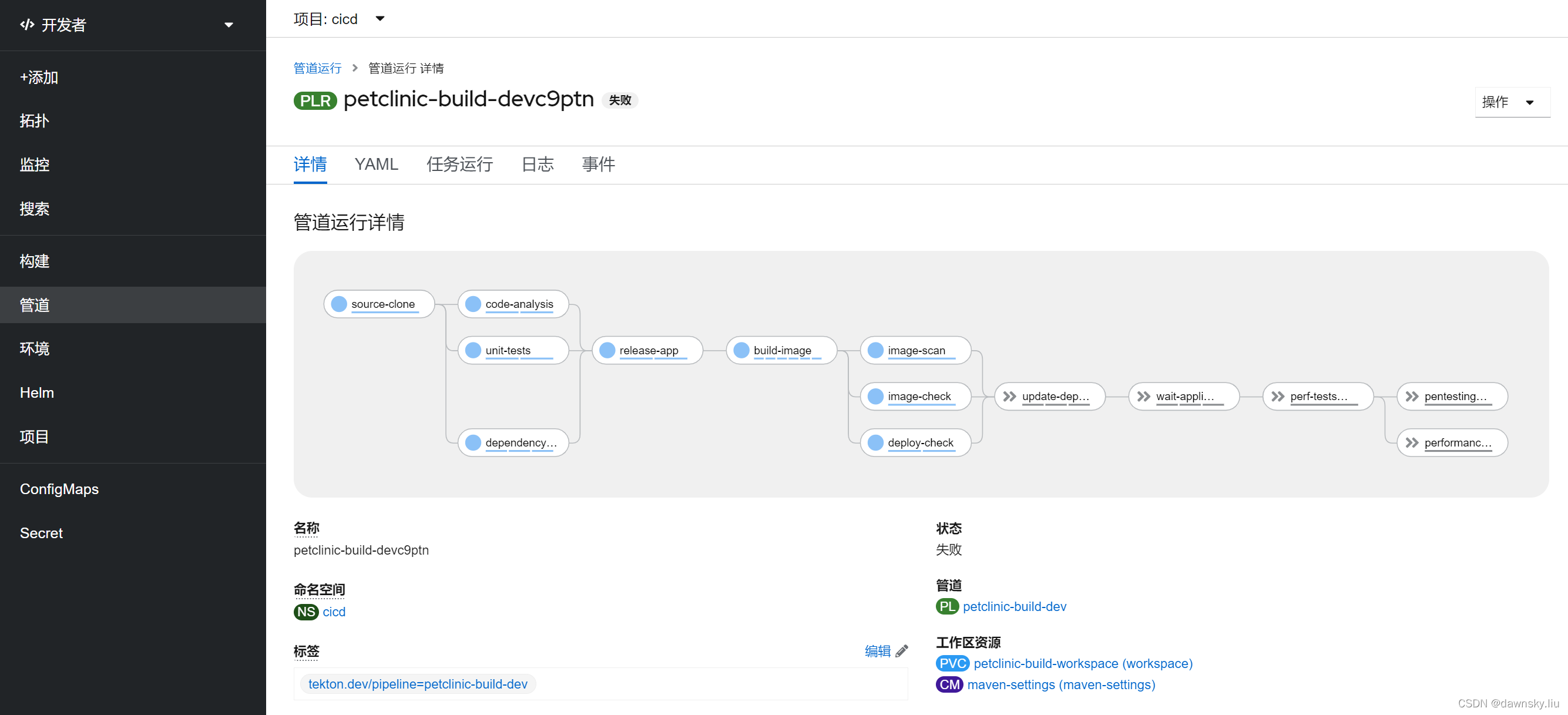
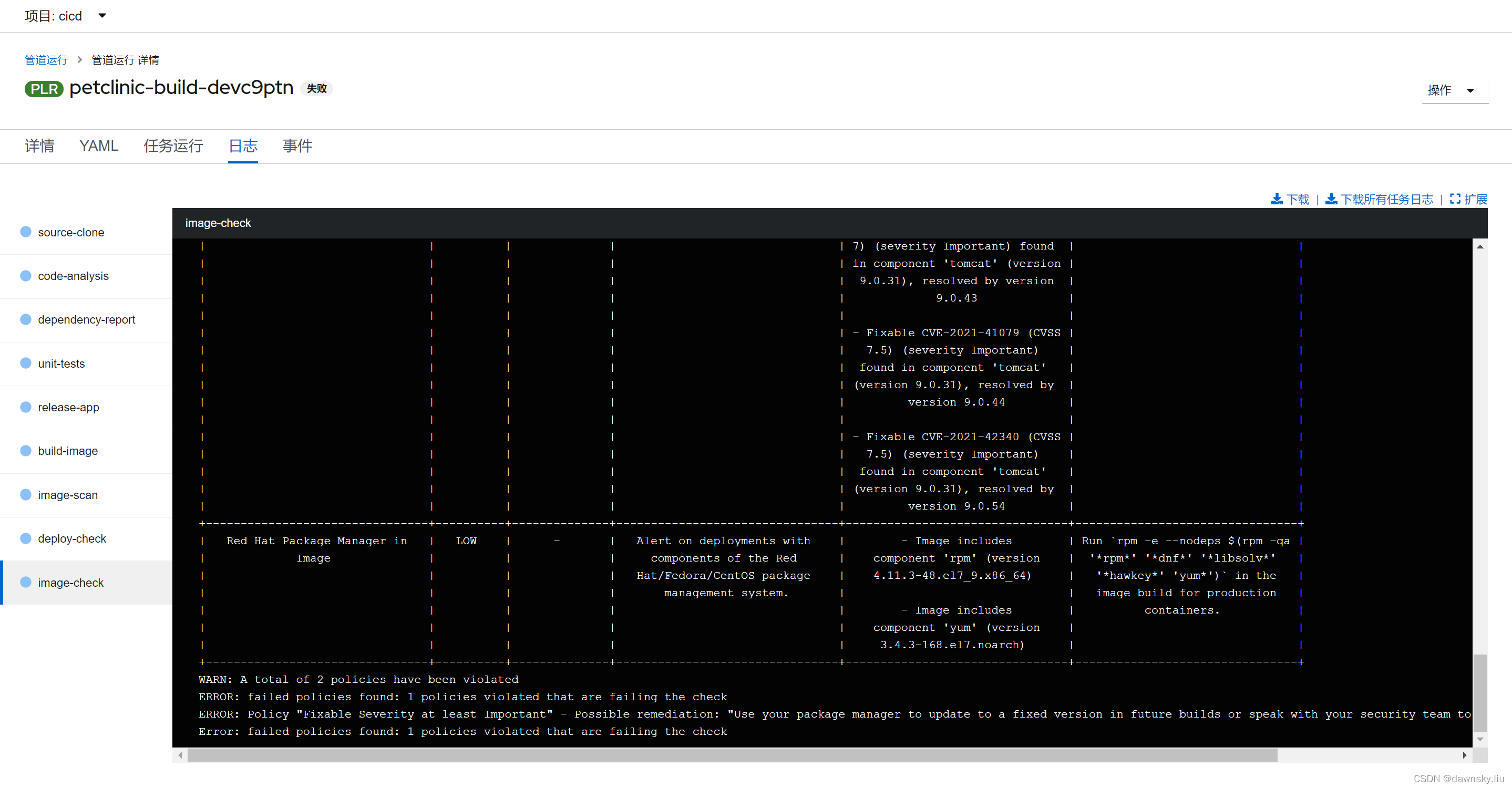
- 可以看到 Pipeline 停在 “image-check”,并提示以下错误:
ERROR: failed policies found: 1 policies violated that are failing the check
ERROR: Policy "Fixable Severity at least Important" - Possible remediation: "Use your package manager to update to a fixed version in future builds or speak with your security team to mitigate the vulnerabilities."
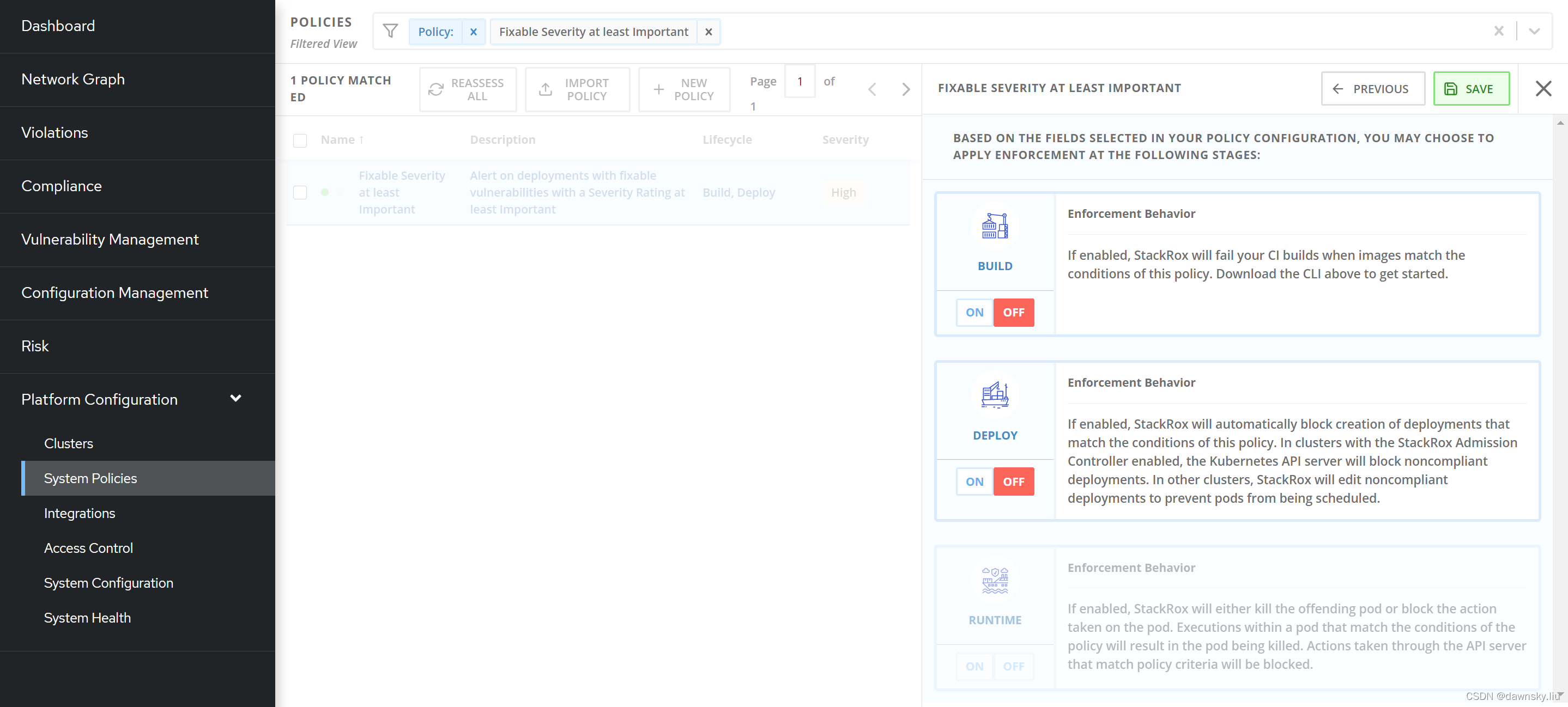
- 在 RHACS 中进入 System Policies,然后查找到 “Fixable Severity at least Important”。选择查找到的策略,然后在右侧窗口点击“Edit”,在下图的步骤中确保 BUILD 和 DEPLOY 都是 OFF 状态,最后点击 SAVE 即可。
- 重新运行 Pipeline,确认这次可以成功运行。
参考
https://github.com/RedHatDemos/SecurityDemos/blob/master/2021Labs/OpenShiftSecurity/documentation/lab4.adoc