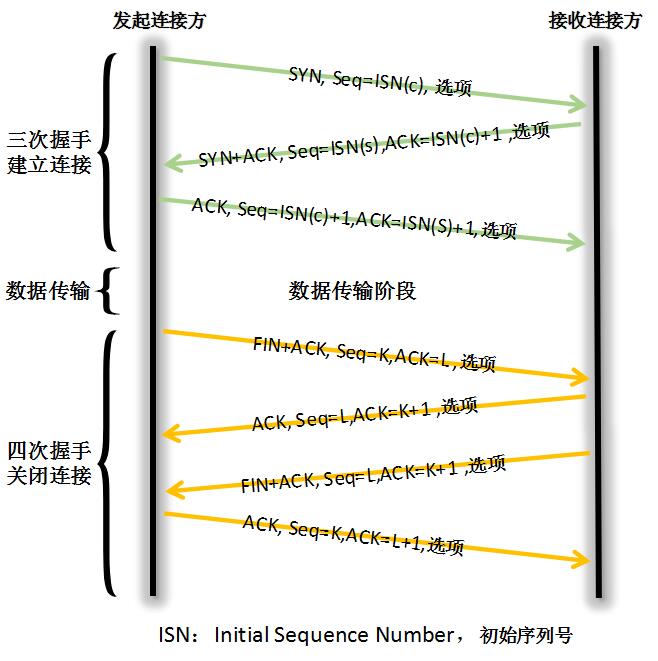
简单的tcpdump抓包说明
安装tcpdump
yum install tcpdump -y
最好设置一下网卡的混杂模式
参考文档
https://blog.csdn.net/weixin_37127253/article/details/84308131
ifconfig eth0 promisc
开启端口监听
#注意iptables放行端口访问
nohup python -m SimpleHTTPServer 88 &
tcpdum监听流量信息
tcpdump -vvv -i ens33 -p tcp port 88
telnet主机查看telnet流量特征
telnet 10.1.1.10 88
连接后不要输入任何信息,查看抓包结果
tcpdump: listening on ens33, link-type EN10MB (Ethernet), capture size 262144 bytes
05:41:28.949213 IP (tos 0x0, ttl 128, id 56061, offset 0, flags [DF], proto TCP (6), length 52)
10.1.1.1.53120 > localhost.localdomain.kerberos: Flags [S], cksum 0x1ec2 (correct), seq 1105931661, win 64240, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
05:41:28.949262 IP (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 52)
localhost.localdomain.kerberos > 10.1.1.1.53120: Flags [S.], cksum 0x1633 (incorrect -> 0x8c23), seq 275712768, ack 1105931662, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
05:41:28.949437 IP (tos 0x0, ttl 128, id 56062, offset 0, flags [DF], proto TCP (6), length 40)
10.1.1.1.53120 > localhost.localdomain.kerberos: Flags [.], cksum 0x2efc (correct), seq 1, ack 1, win 4106, length 0
可以看到如下过程
- 10.1.1.1向服务器发送了syn包,对应标志Flags [S]
- 服务器答复10.1.1.1 syn和ack包,对应标志为Flags [S.]
- 10.1.1.1答复服务器ack包,对应标志为Flags [.]
一次curl访问的完整连接抓包
访问服务器命令
curl 10.1.1.10:88
抓包结果
05:59:40.288219 IP (tos 0x0, ttl 128, id 56124, offset 0, flags [DF], proto TCP (6), length 52)
10.1.1.1.54607 > localhost.localdomain.kerberos: Flags [S], cksum 0x11a4 (correct), seq 1540299512, win 64240, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
05:59:40.288270 IP (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 52)
localhost.localdomain.kerberos > 10.1.1.1.54607: Flags [S.], cksum 0x1633 (incorrect -> 0x626a), seq 1768017576, ack 1540299513, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
05:59:40.288421 IP (tos 0x0, ttl 128, id 56125, offset 0, flags [DF], proto TCP (6), length 40)
10.1.1.1.54607 > localhost.localdomain.kerberos: Flags [.], cksum 0x0543 (correct), seq 1, ack 1, win 4106, length 0
05:59:40.300603 IP (tos 0x0, ttl 128, id 56126, offset 0, flags [DF], proto TCP (6), length 116)
10.1.1.1.54607 > localhost.localdomain.kerberos: Flags [P.], cksum 0xc9b1 (correct), seq 1:77, ack 1, win 4106, length 76
05:59:40.300716 IP (tos 0x0, ttl 64, id 16264, offset 0, flags [DF], proto TCP (6), length 40)
localhost.localdomain.kerberos > 10.1.1.1.54607: Flags [.], cksum 0x1627 (incorrect -> 0x141c), seq 1, ack 77, win 229, length 0
05:59:40.638453 IP (tos 0x0, ttl 64, id 16265, offset 0, flags [DF], proto TCP (6), length 57)
localhost.localdomain.kerberos > 10.1.1.1.54607: Flags [P.], cksum 0x1638 (incorrect -> 0x543e), seq 1:18, ack 77, win 229, length 17
05:59:40.638865 IP (tos 0x0, ttl 64, id 16266, offset 0, flags [DF], proto TCP (6), length 745)
localhost.localdomain.kerberos > 10.1.1.1.54607: Flags [FP.], cksum 0x18e8 (incorrect -> 0x8cc8), seq 18:723, ack 77, win 229, length 705
05:59:40.639007 IP (tos 0x0, ttl 128, id 56128, offset 0, flags [DF], proto TCP (6), length 40)
10.1.1.1.54607 > localhost.localdomain.kerberos: Flags [.], cksum 0x0228 (correct), seq 77, ack 723, win 4103, length 0
05:59:40.640293 IP (tos 0x0, ttl 128, id 56130, offset 0, flags [DF], proto TCP (6), length 40)
10.1.1.1.54607 > localhost.localdomain.kerberos: Flags [.], cksum 0x0227 (correct), seq 77, ack 724, win 4103, length 0
05:59:40.648738 IP (tos 0x0, ttl 128, id 56132, offset 0, flags [DF], proto TCP (6), length 40)
10.1.1.1.54607 > localhost.localdomain.kerberos: Flags [F.], cksum 0x0226 (correct), seq 77, ack 724, win 4103, length 0
05:59:40.648839 IP (tos 0x0, ttl 64, id 29339, offset 0, flags [DF], proto TCP (6), length 40)
localhost.localdomain.kerberos > 10.1.1.1.54607: Flags [.], cksum 0x1148 (correct), seq 724, ack 78, win 229, length 0
可以看到连接断开和数据发送的完整过程
附常用flag标志释义
SYN表示建立连接,
FIN表示关闭连接,
ACK表示响应,
PSH表示有 DATA数据传输,
RST表示连接重置
F : FIN - 结束; 结束会话
S : SYN - 同步; 表示开始会话请求
R : RST - 复位;中断一个连接
P : PUSH - 推送; 数据包立即发送
A : ACK - 应答