文章目录
一些插件,基本上都是在github上搜集来并用过一段时间觉得可以留下来的插件

logger++
比burp更详细的日志,历史记录功能
商店下
Software Vulnerability Scanner
主动式根据 vulners.com 查找 CVE
商店下
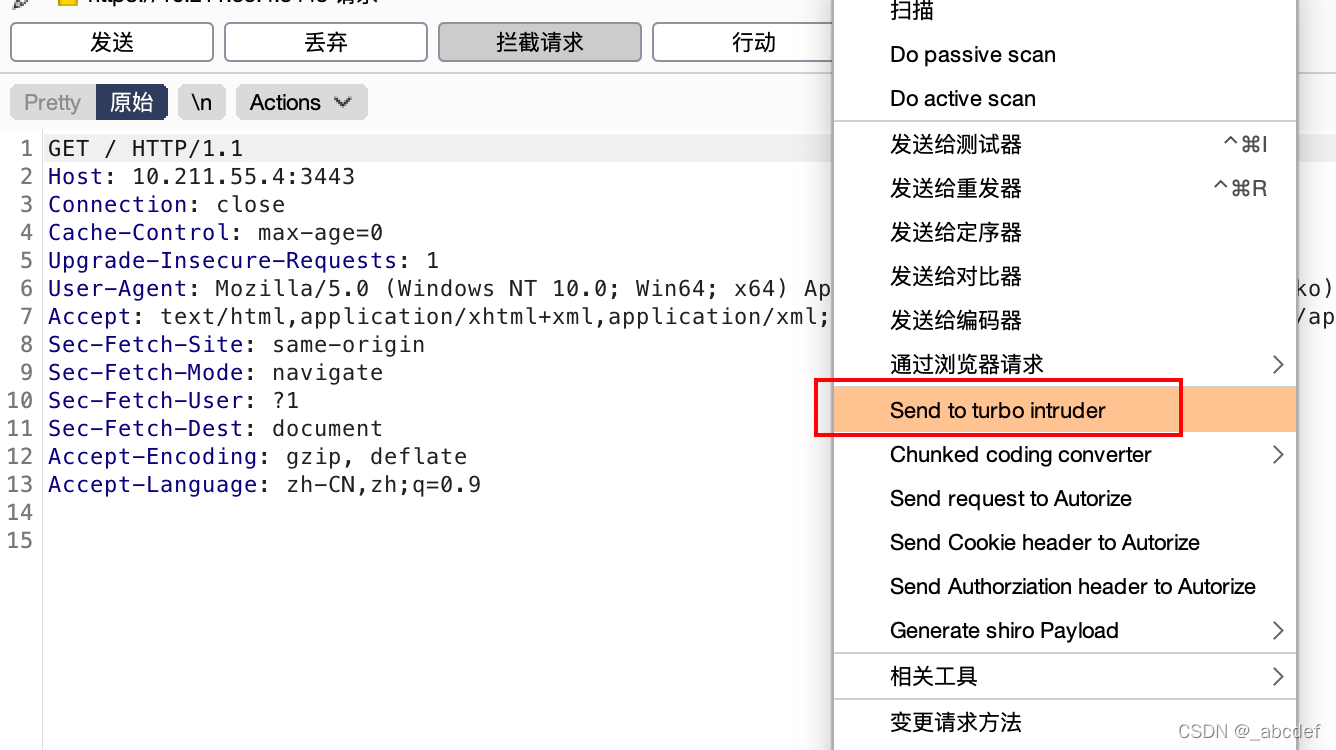
Turbo Intruder
加强版 Intruder ,如果是burpp也可以通过配置多线程,效率跟Turbo不相上下
商店下
自带的各类脚本
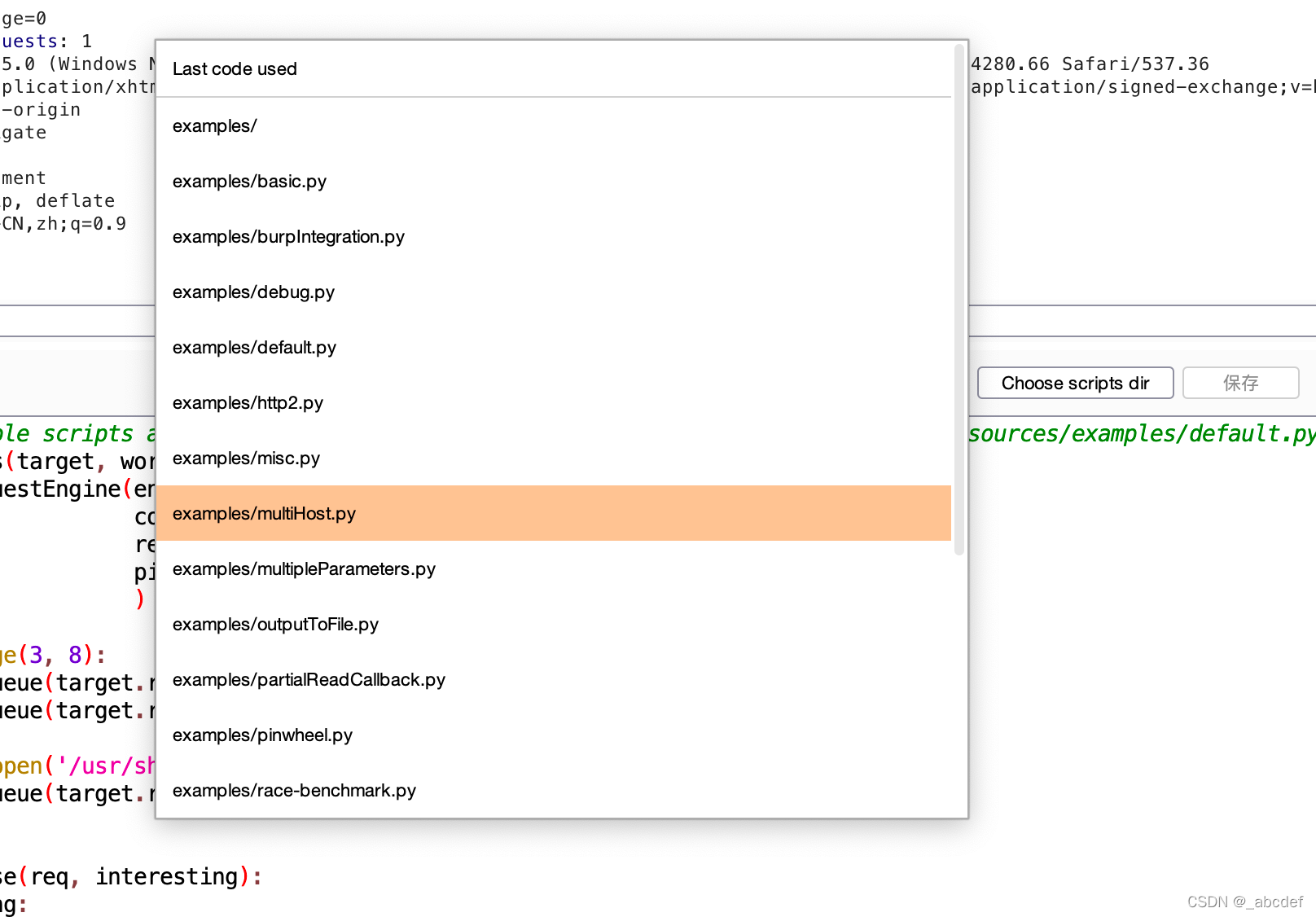
配置好就可以梭了,效率非常高。
reflector
检测xss的
https://github.com/elkokc/reflector
chunked-coding-converter
https://github.com/c0ny1/chunked-coding-converter
分块传输绕waf的,还没用过,感觉大佬写得很牛逼
burp-unauth-checker
检测未授权的
https://github.com/theLSA/burp-unauth-checker
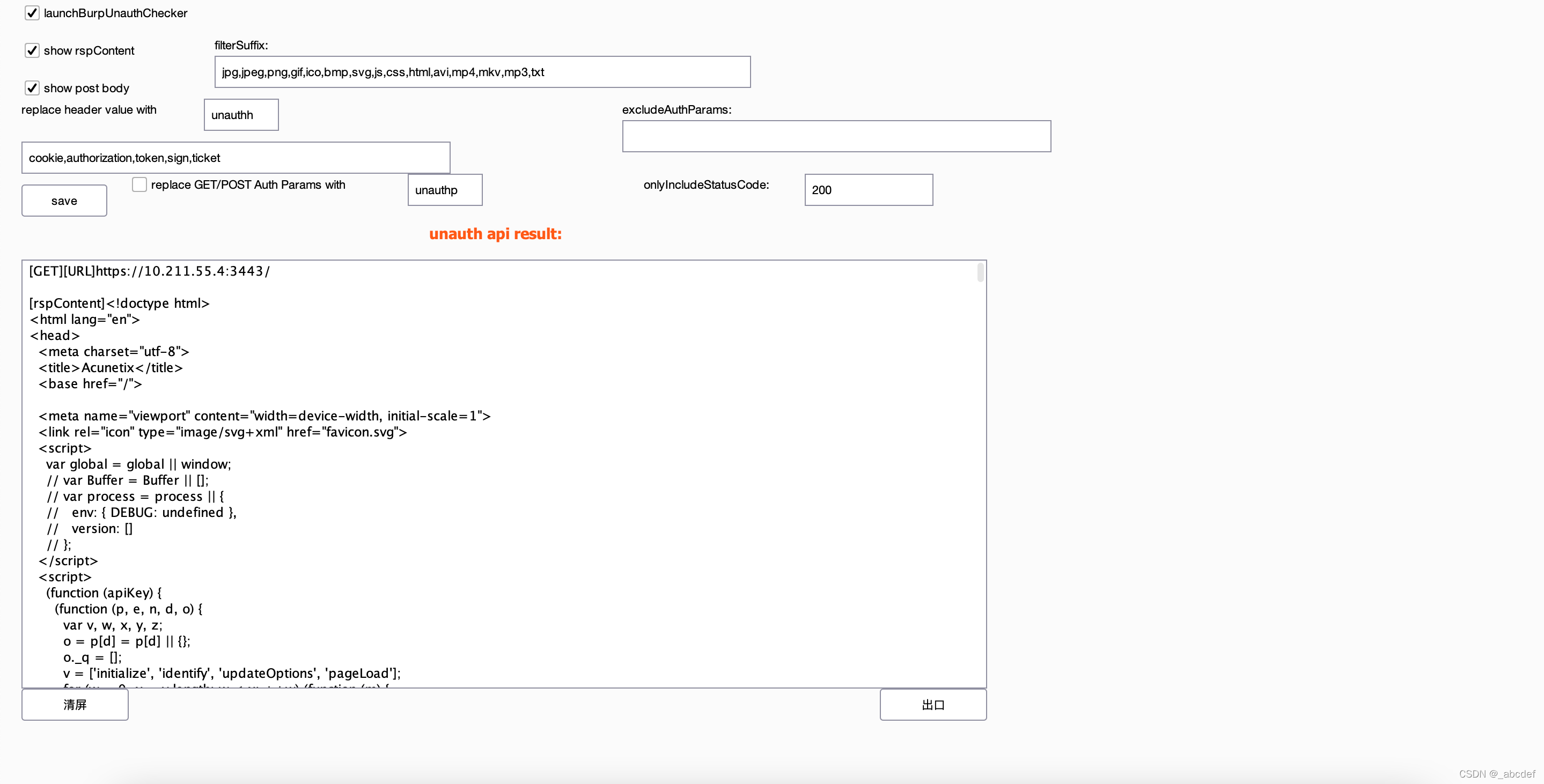
BurpJSLinkFinder
https://github.com/rv0p111/BurpJSLinkFinder
查找js中的一些链接,用于寻找一些接口之类的东西
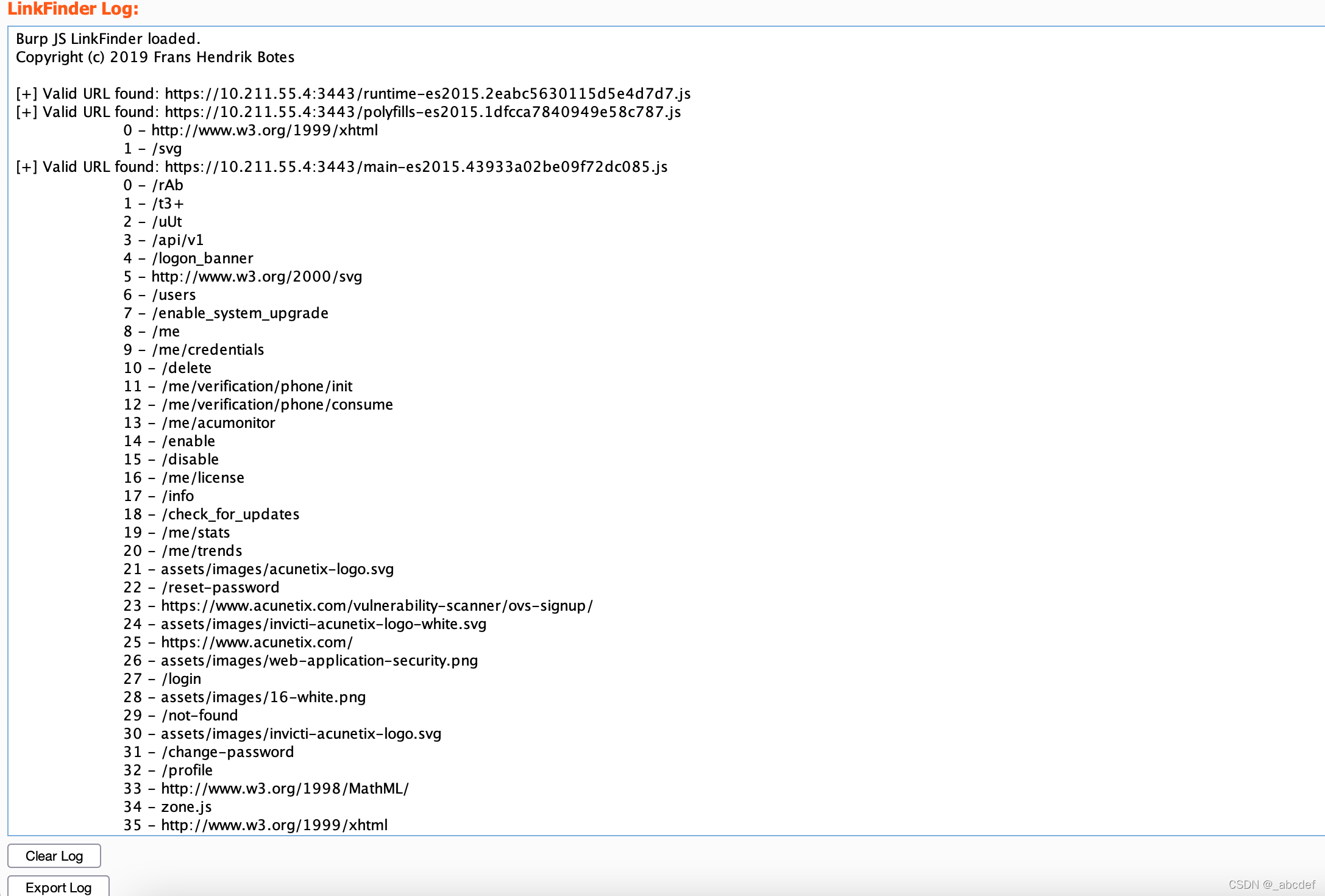
burp-sensitive-param-extractor
越权相关
https://github.com/theLSA/burp-sensitive-param-extractor
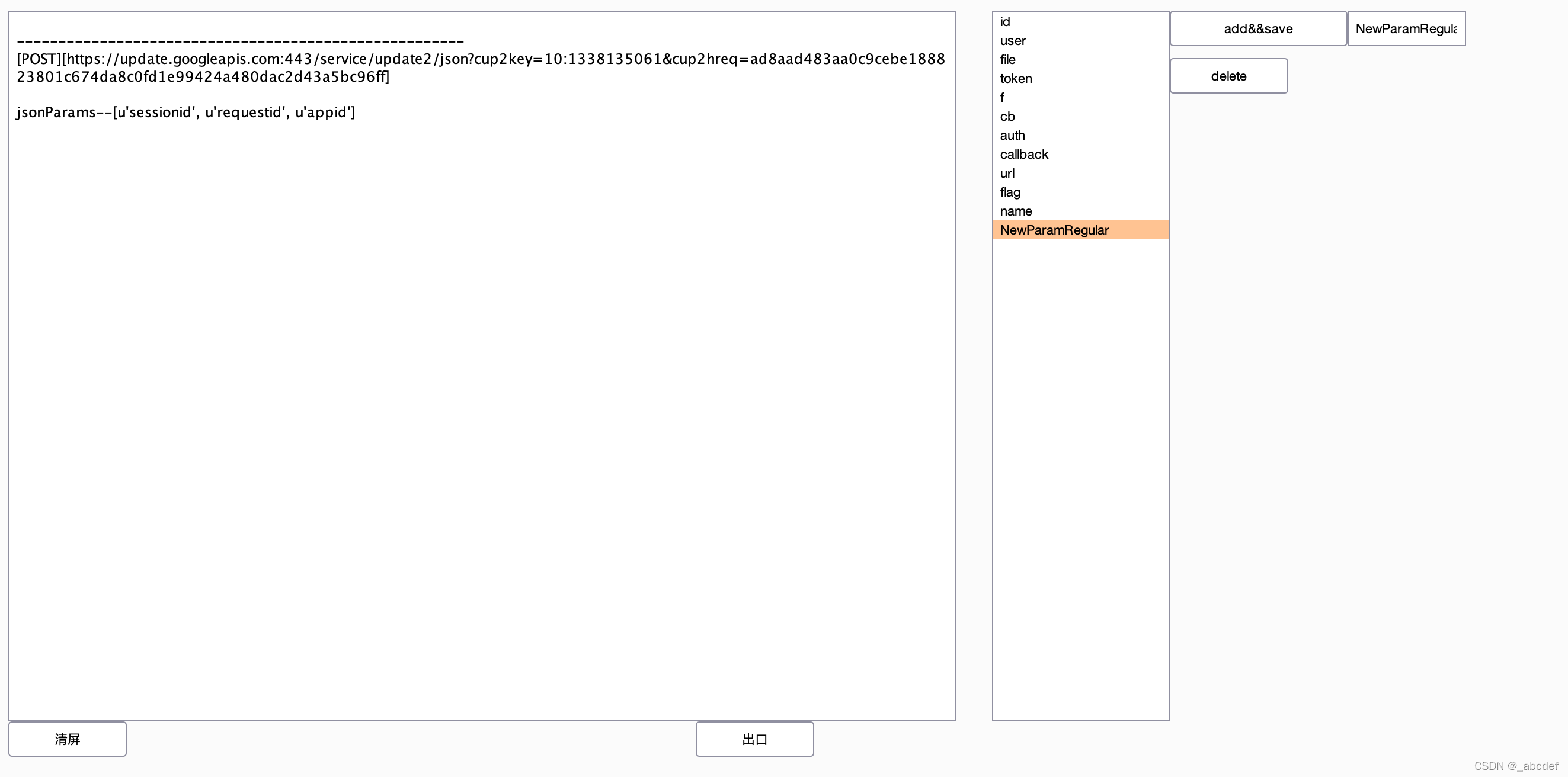
BurpSuite_403Bypasser
通过修改uahead之类的绕过403访问
https://github.com/sting8k/BurpSuite_403Bypasser
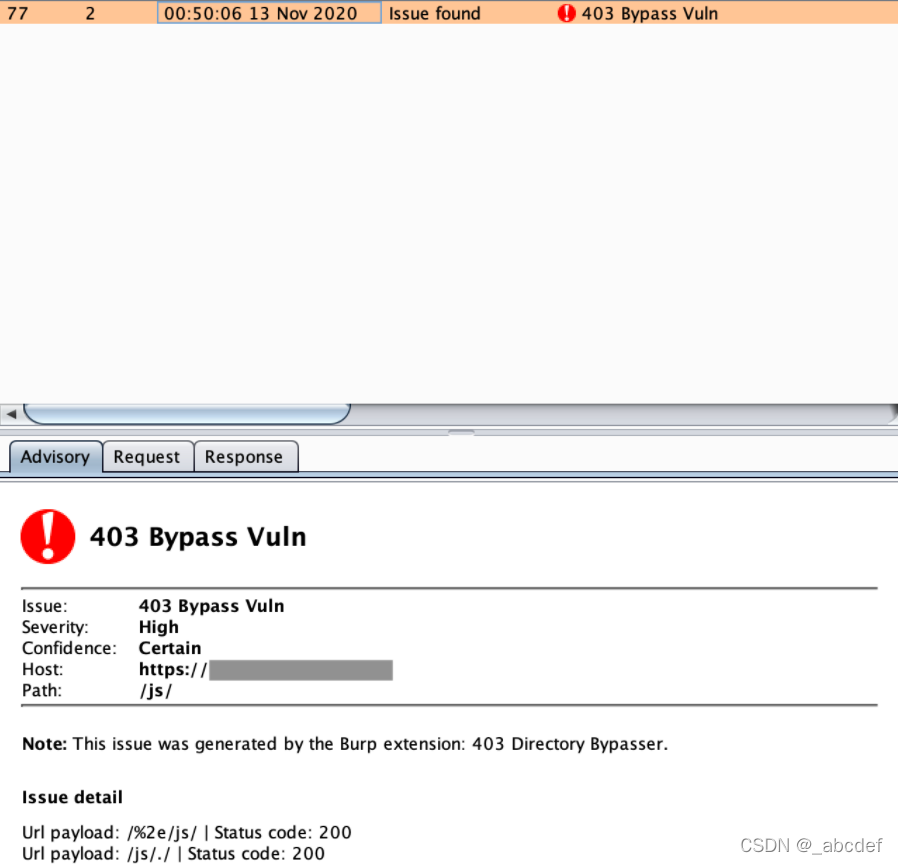
Autozie
越权相关
HaE
正则匹配信息
https://github.com/gh0stkey/HaE
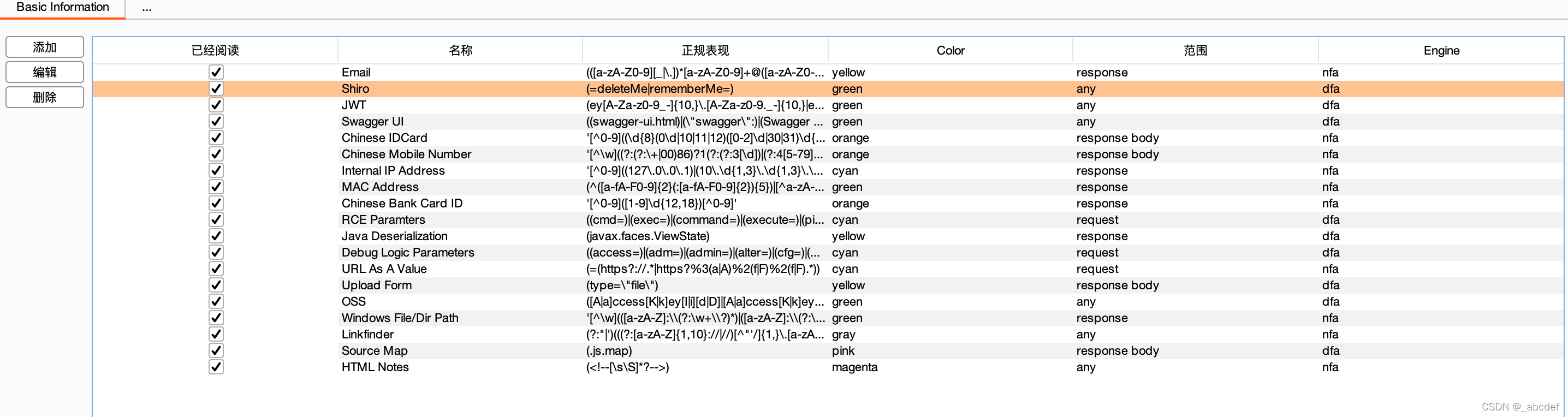
作者写的一些正则匹配
rules:
- rule:
- color: green
engine: dfa
loaded: true
name: Shiro
regex: (=deleteMe|rememberMe=)
scope: any
- color: green
engine: dfa
loaded: true
name: JSON Web Token
regex: (ey[A-Za-z0-9_-]{10,}\.[A-Za-z0-9._-]{10,}|ey[A-Za-z0-9_\/+-]{10,}\.[A-Za-z0-9._\/+-]{10,})
scope: any
- color: green
engine: dfa
loaded: true
name: Swagger UI
regex: ((swagger-ui.html)|(\"swagger\":)|(Swagger UI)|(swaggerUi))
scope: response
type: Fingerprint
- rule:
- color: yellow
engine: nfa
loaded: true
name: Email
regex: (([a-zA-Z0-9][_|\.])*[a-zA-Z0-9]+@([a-zA-Z0-9][-|_|\.])*[a-zA-Z0-9]+\.((?!js|css|jpg|jpeg|png|ico)[a-zA-Z]{2,}))
scope: response
- color: orange
engine: nfa
loaded: true
name: Chinese IDCard
regex: '[^0-9]((\d{8}(0\d|10|11|12)([0-2]\d|30|31)\d{3}$)|(\d{6}(18|19|20)\d{2}(0[1-9]|10|11|12)([0-2]\d|30|31)\d{3}(\d|X|x)))[^0-9]'
scope: response body
- color: orange
engine: nfa
loaded: true
name: Chinese Mobile Number
regex: '[^\w]((?:(?:\+|00)86)?1(?:(?:3[\d])|(?:4[5-79])|(?:5[0-35-9])|(?:6[5-7])|(?:7[0-8])|(?:8[\d])|(?:9[189]))\d{8})[^\w]'
scope: response body
- color: cyan
engine: nfa
loaded: true
name: Internal IP Address
regex: '[^0-9]((127\.0\.0\.1)|(10\.\d{1,3}\.\d{1,3}\.\d{1,3})|(172\.((1[6-9])|(2\d)|(3[01]))\.\d{1,3}\.\d{1,3})|(192\.168\.\d{1,3}\.\d{1,3}))'
scope: response
- color: green
engine: nfa
loaded: true
name: MAC Address
regex: (^([a-fA-F0-9]{2}(:[a-fA-F0-9]{2}){5})|[^a-zA-Z0-9]([a-fA-F0-9]{2}(:[a-fA-F0-9]{2}){5}))
scope: response
- color: orange
engine: nfa
loaded: false
name: Chinese Bank Card ID
regex: '[^0-9]([1-9]\d{12,18})[^0-9]'
scope: response
type: Basic Information
- rule:
- color: cyan
engine: dfa
loaded: true
name: RCE Paramters
regex: ((cmd=)|(exec=)|(command=)|(execute=)|(ping=)|(query=)|(jump=)|(code=)|(reg=)|(do=)|(func=)|(arg=)|(option=)|(load=)|(process=)|(step=)|(read=)|(function=)|(feature=)|(exe=)|(module=)|(payload=)|(run=)|(daemon=)|(upload=)|(dir=)|(download=)|(log=)|(ip=)|(cli=))
scope: request
- color: yellow
engine: dfa
loaded: true
name: Java Deserialization
regex: (javax.faces.ViewState)
scope: response
- color: cyan
engine: dfa
loaded: true
name: Debug Logic Parameters
regex: ((access=)|(adm=)|(admin=)|(alter=)|(cfg=)|(clone=)|(config=)|(create=)|(dbg=)|(debug=)|(delete=)|(disable=)|(edit=)|(enable=)|(exec=)|(execute=)|(grant=)|(load=)|(make=)|(modify=)|(rename=)|(reset=)|(root=)|(shell=)|(test=)|(toggl=))
scope: request
- color: cyan
engine: nfa
loaded: true
name: URL As A Value
regex: (=(https?://.*|https?%3(a|A)%2(f|F)%2(f|F).*))
scope: request
- color: yellow
engine: dfa
loaded: true
name: Upload Form
regex: (type=\"file\")
scope: response body
type: Maybe Vulnerability
- rule:
- color: green
engine: dfa
loaded: true
name: OSS
regex: ([A|a]ccess[K|k]ey[I|i][d|D]|[A|a]ccess[K|k]ey[S|s]ecret)
scope: any
- color: green
engine: nfa
loaded: true
name: Amazon AWS URL
regex: (((([a-zA-Z0-9._-]+\.s3|s3)(\.|\-)+[a-zA-Z0-9._-]+|[a-zA-Z0-9._-]+\.s3|s3)\.amazonaws\.com)|(s3:\/\/[a-zA-Z0-9-\.\_]+)|(s3.console.aws.amazon.com\/s3\/buckets\/[a-zA-Z0-9-\.\_]+)|(amzn\.mws\.[0-9a-f]{8}-[0-9a-f]{4}-[0-9a-f]{4}-[0-9a-f]{4}-[0-9a-f]{12})|(ec2-[0-9-]+.cd-[a-z0-9-]+.compute.amazonaws.com)|(us[_-]?east[_-]?1[_-]?elb[_-]?amazonaws[_-]?com))
scope: any
- color: green
engine: nfa
loaded: true
name: Amazon AWS AccessKey ID
regex: ((aws(.{0,20})?(?-i)['\"][0-9a-zA-Z\/+]{40}['\"])|((A3T[A-Z0-9]|AKIA|AGPA|AIDA|AROA|AIPA|ANPA|ANVA|ASIA)[a-zA-Z0-9]{16}))
scope: any
- color: green
engine: nfa
loaded: true
name: Amazon AWS Region
regex: ((us(-gov)?|ap|ca|cn|eu|sa)-(central|(north|south)?(east|west)?)-\d)
scope: any
- color: yellow
engine: nfa
loaded: true
name: SSH Private Key
regex: ([-]+BEGIN [^\s]+ PRIVATE KEY[-])
scope: response
- color: green
engine: nfa
loaded: true
name: Windows File/Dir Path
regex: '[^\w](([a-zA-Z]:\\(?:\w+\\?)*)|([a-zA-Z]:\\(?:\w+\\)*\w+\.\w+))'
scope: response
type: Sensitive Information
- rule:
- color: gray
engine: nfa
loaded: false
name: Linkfinder
regex: (?:"|')(((?:[a-zA-Z]{1,10}://|//)[^"'/]{1,}\.[a-zA-Z]{2,}[^"']{0,})|((?:/|\.\./|\./)[^"'><,;|*()(%%$^/\\\[\]][^"'><,;|()]{1,})|([a-zA-Z0-9_\-/]{1,}/[a-zA-Z0-9_\-/]{1,}\.(?:[a-zA-Z]{1,4}|action)(?:[\?|#][^"|']{0,}|))|([a-zA-Z0-9_\-/]{1,}/[a-zA-Z0-9_\-/]{3,}(?:[\?|#][^"|']{0,}|))|([a-zA-Z0-9_\-]{1,}\.(?:php|asp|aspx|jsp|json|action|html|js|txt|xml)(?:[\?|#][^"|']{0,}|)))(?:"|')
scope: any
- color: pink
engine: dfa
loaded: true
name: Source Map
regex: (.js.map)
scope: response body
- color: magenta
engine: nfa
loaded: false
name: HTML Notes
regex: (<!--[\s\S]*?-->)
scope: any
type: Other
BurpFastJsonScan
fastjson检测
https://github.com/pmiaowu/BurpFastJsonScan
Shiro Echo Tool
shiro框架检测
http://github.com/potats0
ssrf-king
SSRF 检测
https://github.com/ethicalhackingplayground/ssrf-king

bypasswaf
绕waf
https://github.com/codewatchorg/bypasswaf
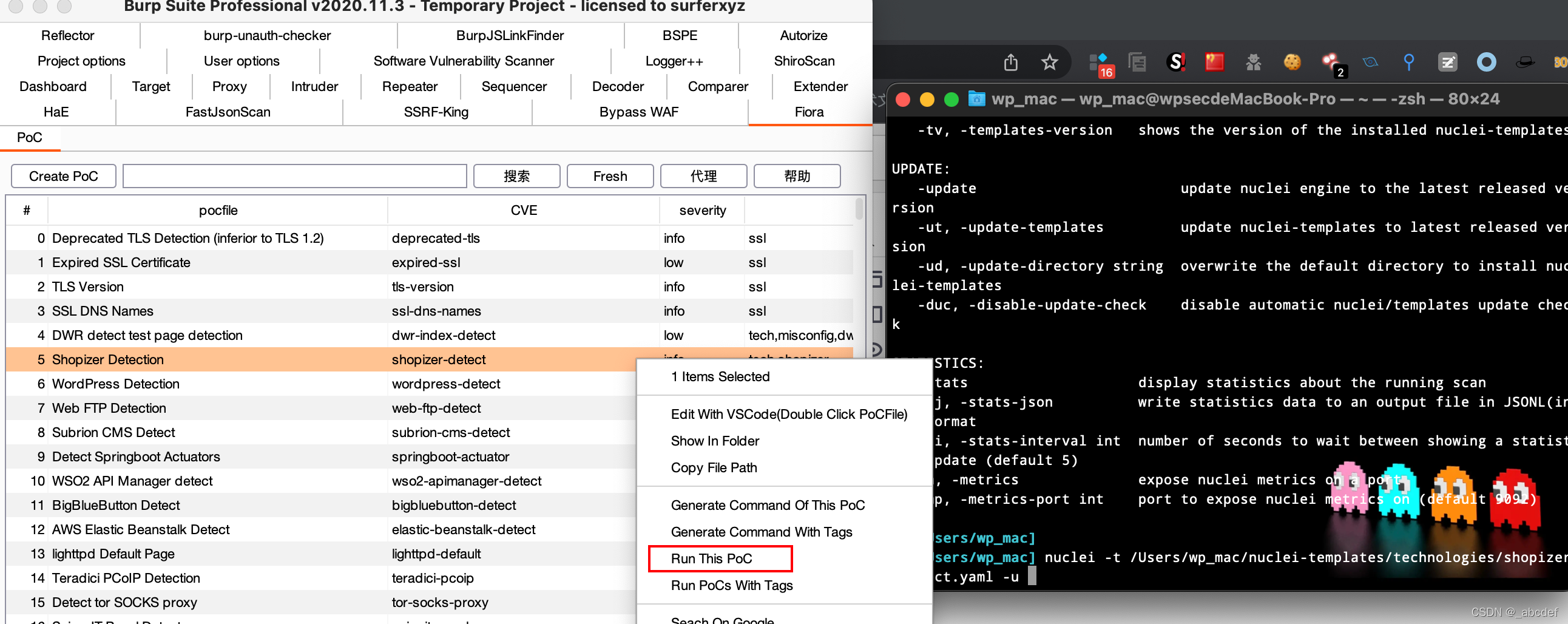
Fiora
https://github.com/bit4woo/Fiora
下载对应版本nuclei,配置环境变量
联动nuclei
在burp 测某poc时候会自动调用nuclei
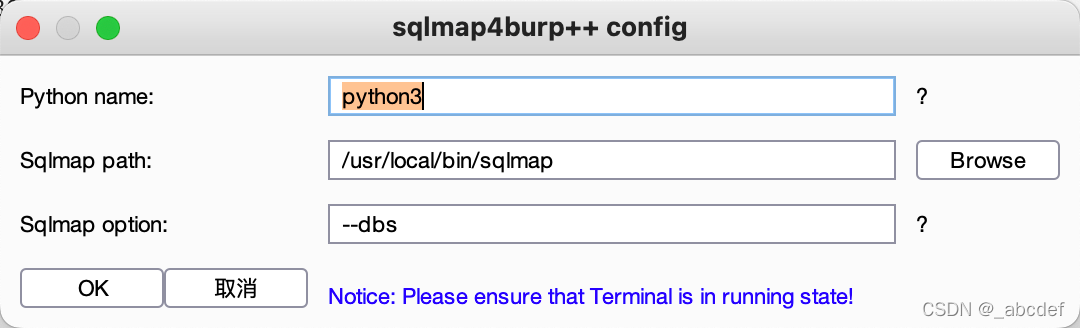
burpsqlmap++
https://github.com/c0ny1/sqlmap4burp-plus-plus
快速测试sqlmap