配置点:
1、内外网接口/IP地址/区域
2、路由及策略路由
3、区域间访问控制策略
4、NAT策略:包括代理上网、端口映射信息
5、IPSec对接方式及对接信息
6、H3C防火墙设备授权许可证;远程登录方式;IPS、防病毒、攻击防范和SYN泛洪攻击等安全防护策略配置
1、内外网接口/IP地址/区域
接口
interface GigabitEthernet1/0/0:192.168.0.1/24? ? ? ? ? ? ? ? //管理口
interface GigabitEthernet1/0/2:192.168.99.2/24? ? ? ? ? ? ? //内网口
interface GigabitEthernet1/0/3:183.124.192.118/30? ? ? ? //外网口
区域
security-zone name Trust
?import interface GigabitEthernet1/0/2
security-zone name Untrust
?import interface GigabitEthernet1/0/3
security-zone name Management
?import interface GigabitEthernet1/0/0
2、路由及策略路由
?ip route-static 0.0.0.0 0 183.124.192.117
?ip route-static 192.168.7.0 24 192.168.99.1
?ip route-static 192.168.0.0 24 192.168.99.1
?ip route-static 192.168.1.0 24 192.168.99.1
?ip route-static 192.168.2.0 22 192.168.99.1
?ip route-static 192.168.3.0 24 192.168.99.1
3、区域间访问控制策略
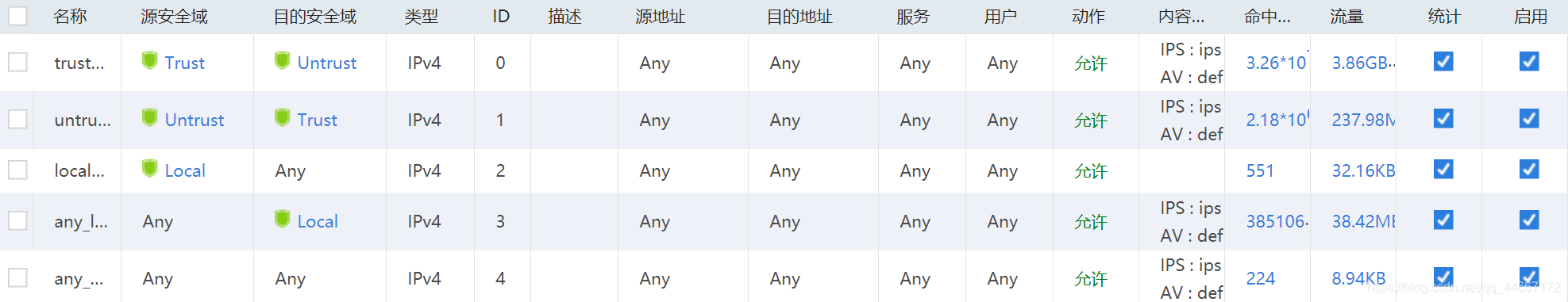
4、NAT策略
代理上网????????????????????????????????????????????????????????????????????????//不对感兴趣流进行NAT转换
acl advanced 3001
?rule 12 deny ip source 192.168.0.0 0.0.0.255 destination 172.20.10.0 0.0.0.255
?rule 20 deny ip source 192.168.0.0 0.0.0.255 destination 10.0.0.50 0
?rule 21 permit ip source 192.168.1.119 0
?rule 22 permit ip source 192.168.2.55 0
?rule 23 permit ip source 192.168.3.28 0
?rule 24 permit ip source 192.168.3.43 0
?rule 27 permit ip source 192.168.0.100 0
?rule 28 permit ip source 192.168.0.32 0
?rule 29 permit ip source 192.168.0.82 0
端口映射
interface GigabitEthernet1/0/3
?nat outbound 3001? ? ? ? ? ? ? ? ? ? ? ????????????????????????????????? //代理上网? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ?
?gateway 183.124.192.117
?nat server protocol tcp global 183.124.192.118?8081 inside 192.168.0.20 80 rule A
?nat server protocol tcp global 183.124.192.118 8082 inside 192.168.1.2 22 rule B
?nat server protocol tcp global 183.124.192.118?18081 inside 192.168.0.20 8080 rule H
?nat server protocol tcp global 183.124.192.118 18082 inside 192.168.0.25 22 rule I
?nat server protocol tcp global 183.124.192.118 18083 inside 192.168.0.24 22 rule J
?nat server protocol tcp global 183.124.192.118 22222 inside 192.168.1.4 22 rule K
?nat server protocol tcp global 183.124.192.118 37778 inside 192.168.7.2 37772 rule L
?nat server protocol tcp global 183.124.192.118 37779 inside 192.168.7.3 37773 rule M
?5、IPSec对接方式及对接信息
IKE提议
ike logging negotiation enable
设备角色(分支/节点),使用一个IPSec策略feita应用于外网端口,设置优先级不同,代表不同的策略。
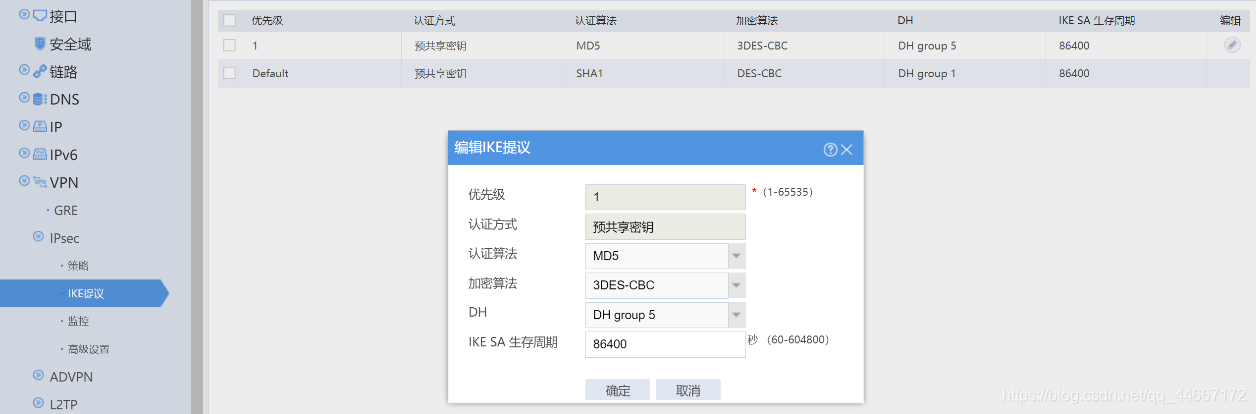
[F1000-AK115] ike proposal 1
[F1000-AK115-ike-proposal-1]authentication-method pre-share? ? ? ? ? ? ? ? //认证方式预共享加密
[F1000-AK115-ike-proposal-1]authentication-algorithm md5? ? ? ? ? ? ? ? ? ? ?//认证算法MD5
[F1000-AK115-ike-proposal-1]encryption-algorithm 3des-cbc? ? ? ? ? ? ? ? ? ? //加密算法3DES
[F1000-AK115-ike-proposal-1]dh group5? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? //DH组5
IPSec策略
对端一:
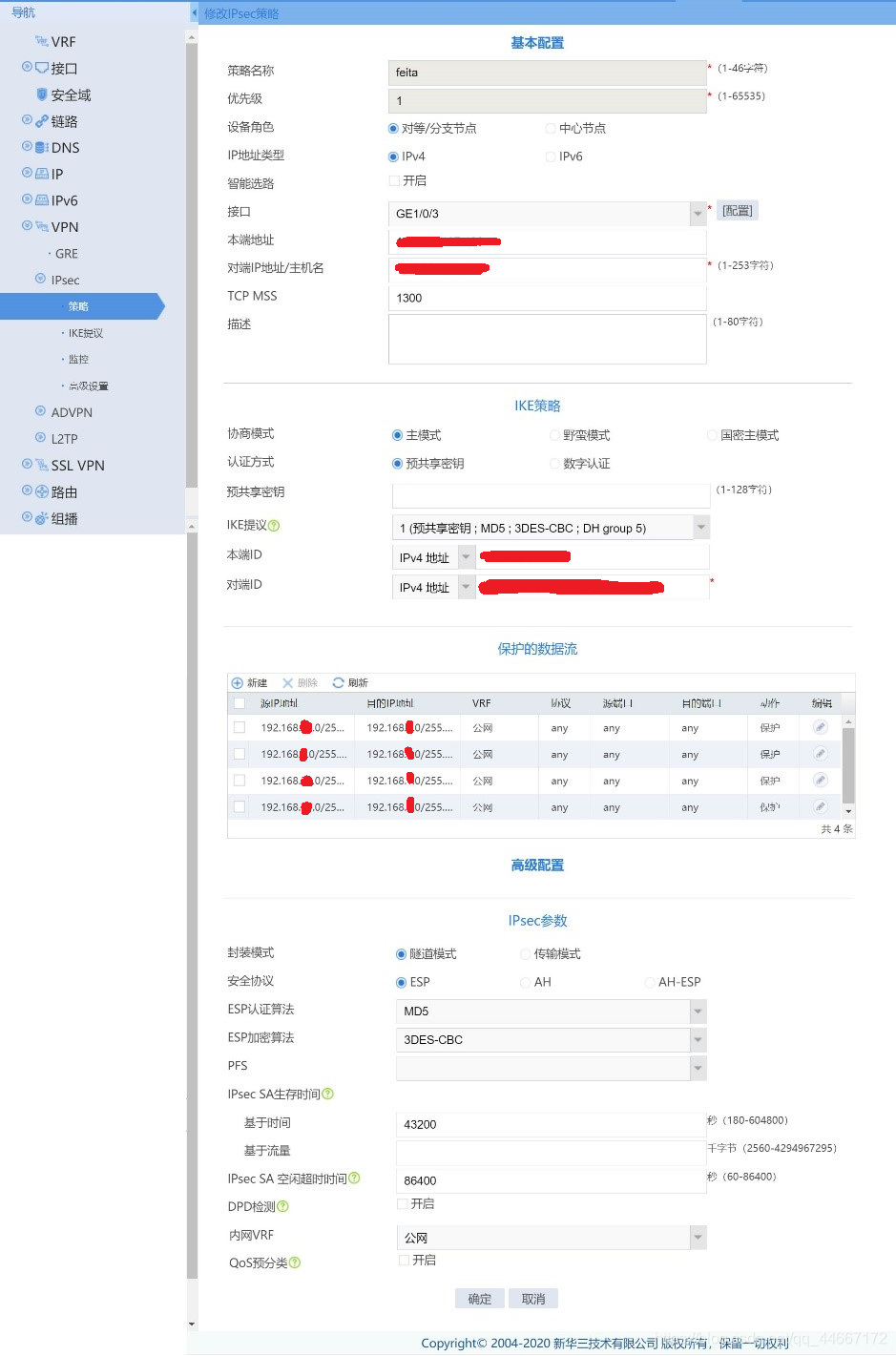
ipsec policy feita 1 isakmp
?transform-set feita_IPv4_1? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ?//转换集(IPSec安全提议)
?exchange-mode main? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ?//交换模式(默认主模式)? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ?security acl name IPsec_feita_IPv4_1? ? ? ? ? ? ? ? ? ?//保护数据流ACL
?local-address 183.124.192.118
?remote-address 122.224.111.102
?ike-profile feita_IPv4_1? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ?//IKE策略
?sa duration time-based 43200? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? //IKE SA生存时间
?sa idle-time 86400? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? //IKE SA空闲超时时间
ipsec transform-set feita_IPv4_1
?encapsulation-mode tunnel? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ?//报文封装模式(默认隧道模式)
?protocol esp? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ?//安全协议(默认esp模式)
?esp encryption-algorithm 3des-cbc?
?esp authentication-algorithm md5?
?acl advanced name IPsec_feita_IPv4_1
?rule 1 permit ip source 192.168.3.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
?rule 2 permit ip source 192.168.7.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
?rule 3 permit ip source 192.168.2.0 0.0.3.255 destination 192.168.1.0 0.0.0.255
?rule 4 permit ip source 192.168.0.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
ike profile feita_IPv4_1
?keychain feita_IPv4_1
?local-identity address 183.124.192.118
?match remote identity address 122.224.111.102 255.255.255.255
?match local address GigabitEthernet1/0/3
?proposal 1
ike keychain feita_IPv4_1
?match local address GigabitEthernet1/0/3
?pre-shared-key address 122.224.111.102 255.255.255.255 key cipher XXX? ? ? //对端预共享密钥
?interface GigabitEthernet1/0/3
?ipsec apply policy feita
对端二:
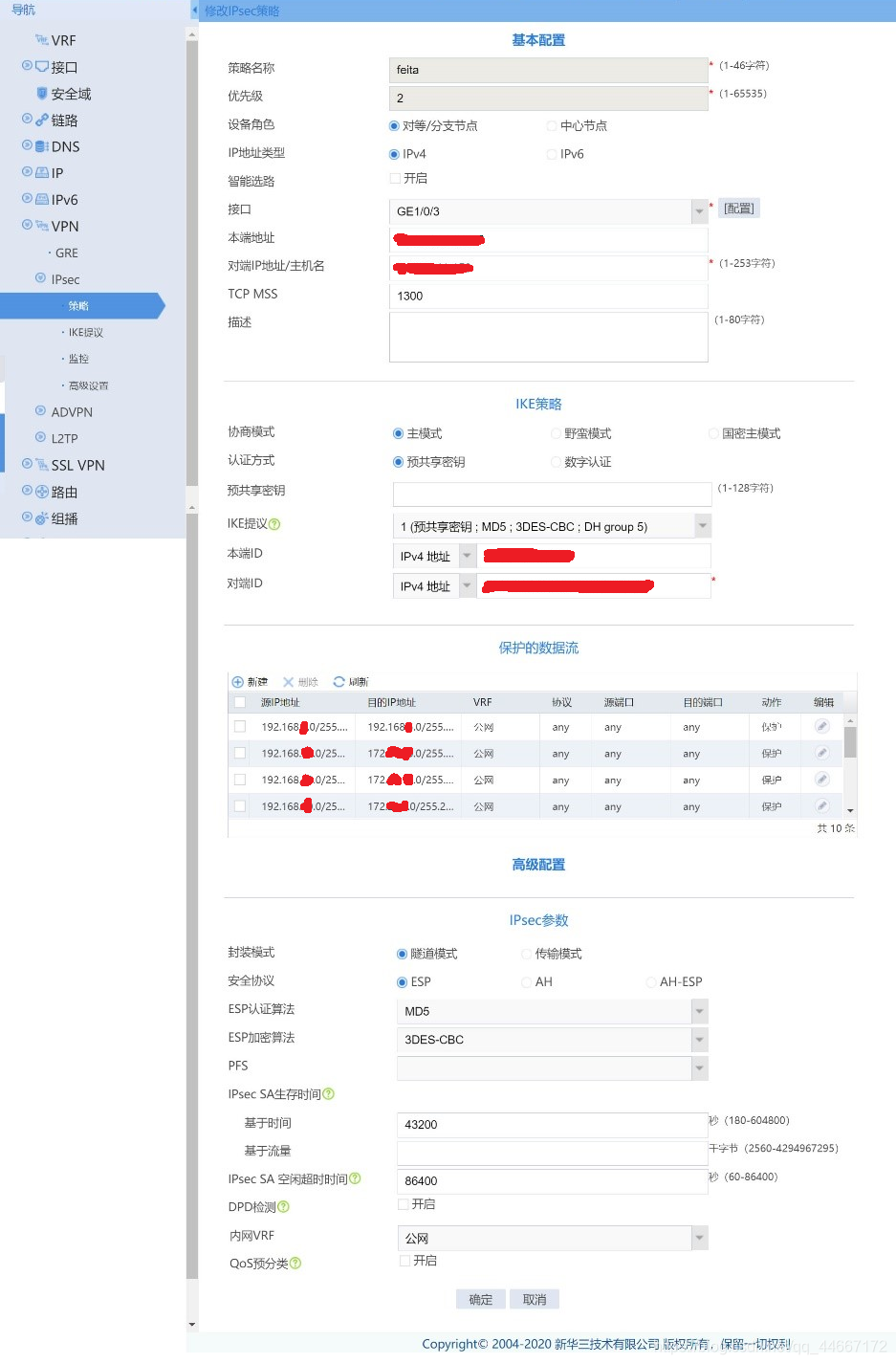
ipsec policy feita 2 isakmp
?transform-set feita_IPv4_2?
?security acl name IPsec_feita_IPv4_2?
?local-address 183.124.192.118
?remote-address 122.224.111.102
?ike-profile feita_IPv4_2
?sa duration time-based 43200
?sa idle-time 86400
ipsec transform-set feita_IPv4_2
?encapsulation-mode tunnel? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ?//报文封装模式(默认隧道模式)
?protocol esp? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ?//安全协议(默认esp模式)
?esp encryption-algorithm 3des-cbc?
?esp authentication-algorithm md5?
?acl advanced name IPsec_feita_IPv4_2
?rule 1 permit ip source 192.168.7.0 0.0.0.255 destination 192.168.5.0 0.0.0.255
?rule 2 permit ip source 192.168.0.0 0.0.0.255 destination 172.0.0.0 0.0.0.255
?rule 3 permit ip source 192.168.0.0 0.0.0.255 destination 172.0.2.0 0.0.0.255
?rule 4 permit ip source 192.168.0.0 0.0.0.255 destination 172.0.4.0 0.0.0.255
?rule 5 permit ip source 192.168.0.0 0.0.0.255 destination 172.0.4.0 0.0.0.255
?rule 6 permit ip source 192.168.0.0 0.0.0.255 destination 172.0.4.0 0.0.0.255
?rule 10 permit ip source 192.168.0.0 0.0.0.255 destination 10.0.0.3?0
ike profile feita_IPv4_2
?keychain feita_IPv4_2
?local-identity address 183.124.192.118
?match remote identity address 122.224.111.102 255.255.255.255
?match local address GigabitEthernet1/0/3
?proposal 1
ike keychain feita_IPv4_2
?match local address GigabitEthernet1/0/3
?pre-shared-key address 122.224.111.102 255.255.255.255 key cipher XXX
?interface GigabitEthernet1/0/3
?ipsec apply policy feita
