Getting Started
Wireshark:A packet sniffer for observing the messages exchanged between executing protocol entities
A packet sniffer captures (“sniffs”) messages being sent/received from/by your computer; it will also typically store and/or display the contents of the various protocol fields in these captured messages. A packet sniffer itself is passive. It observes messages being sent and received by applications and protocols running on your computer, but never sends packets itself.
The packet sniffer is an addition to the usual software in your computer, and consists of two parts.
- The packet capture library receives a copy of every link-layer frame that is sent from or received by your computer over a given interface (link layer).Capturing all link-layer frames gives you all messages sent/received across the monitored link from/by all protocols and applications executing in your computer
- The packet analyzer displays the contents of all fields within a protocol message.
packet sniffer独立于计算机的软件之外,由packet capture获取计算机上的应用发出或收到的frame的拷贝,再由packet analyzer对frame进行分析,显示信息中的字段和内容。
we’ve chosen to show detailed content for the Hypertext Transfer Protocol application message that was found within the TCP segment, that was inside the IPv4 datagram that was inside the Ethernet II (WiFi) frame
Questions:
-
List 3 different protocols that appear in the protocol column in the unfiltered packet-listing window in step 7 above.
-
DHCP
-
HTTP
-
SSDP
-
Socks
-
-
How long did it take from when the HTTP GET message was sent until the HTTP OK reply was received?
304 Not Modified表示访问的内容之前已经访问过了,请求被重定向至缓存中,与200 OK等价
The HTTP
304 Not Modifiedclient redirection response code indicates that there is no need to retransmit the requested resources. It is an implicit redirection to a cached resource. This happens when the request method is safe, like aGETor aHEADrequest, or when the request is conditional and uses aIf-None-Matchor aIf-Modified-Sinceheader. -
What is the Internet address of the gaia.cs.umass.edu (also known as wwwnet.cs.umass.edu)? What is the Internet address of your computer?
HTTP
HTTP请求报文的格式:
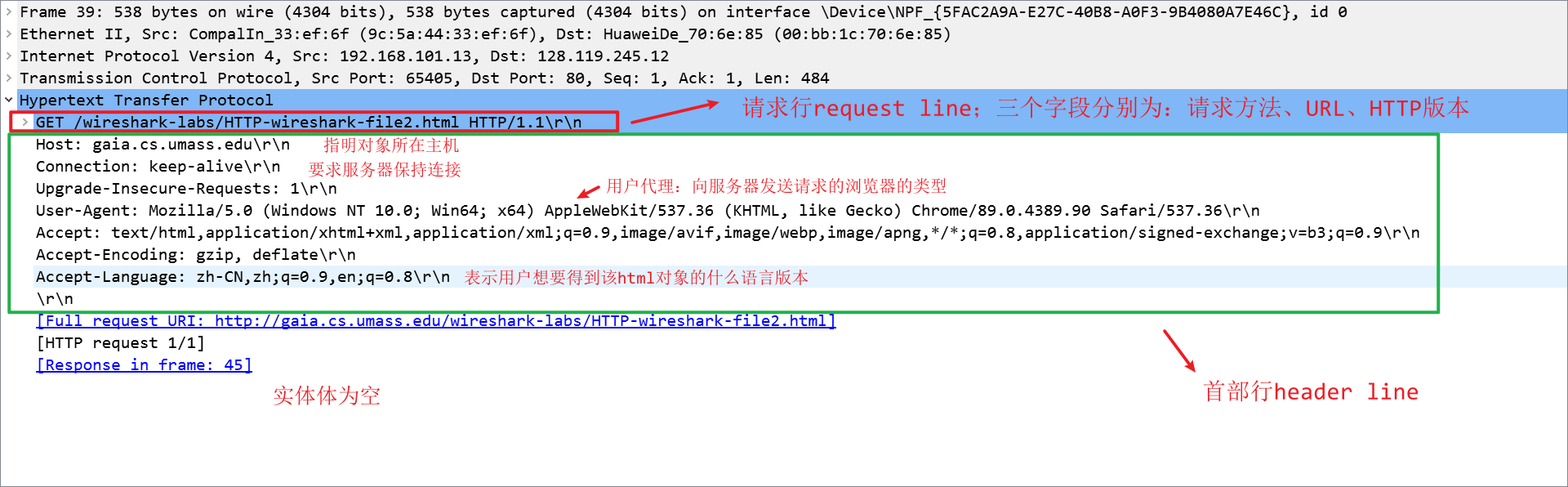
HTTP响应报文的格式:
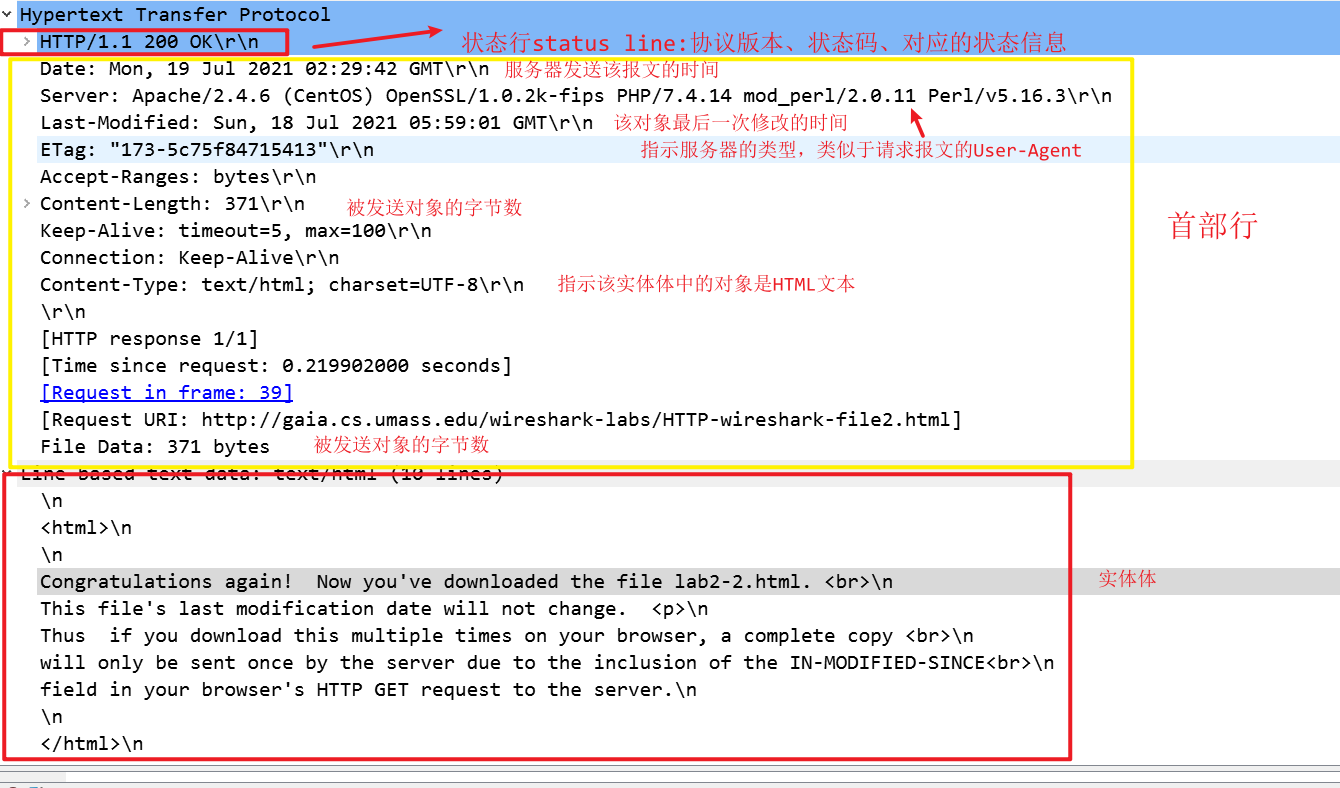
1、 The Basic HTTP GET/response interaction
进入这个网址http://gaia.cs.umass.edu/wireshark-labs/HTTP-wireshark-file1.html,再用wireshark进行抓包,在筛选框中输入http进行筛选,找到本机发送给gaia.cs.umass.edu服务器的GET信息和对方服务器对本机的response信息。
-
Is your browser running HTTP version 1.0 or 1.1? What version of HTTP is the server running?
我的浏览器运行HTTP1.1,对方服务器运行HTTP1.1


-
What languages (if any) does your browser indicate that it can accept to the server?
可接受语言为中文,权重为0.9;英语,权重为0.8

-
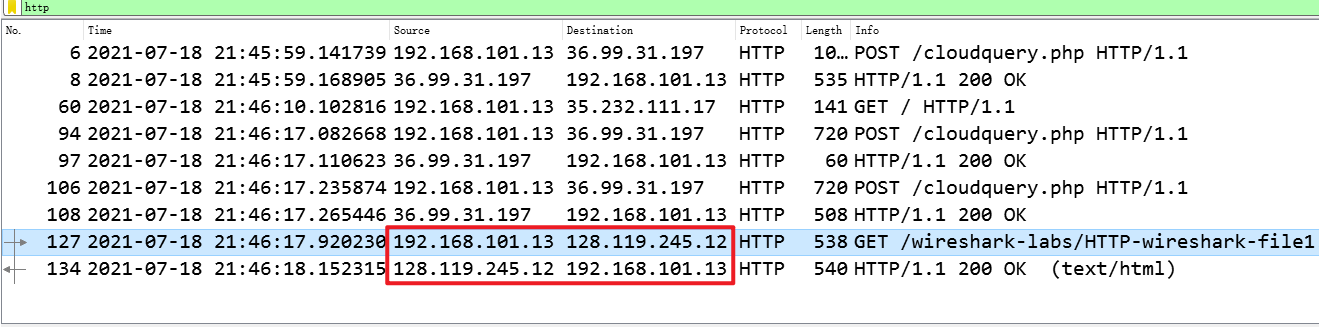
What is the IP address of your computer? Of the gaia.cs.umass.edu server?
我的IP:192.168.101.13,gaia.cs.umass.edu服务器的IP:128.119.245.12
-
What is the status code returned from the server to your browser?
200
-
When was the HTML file that you are retrieving last modified at the server?
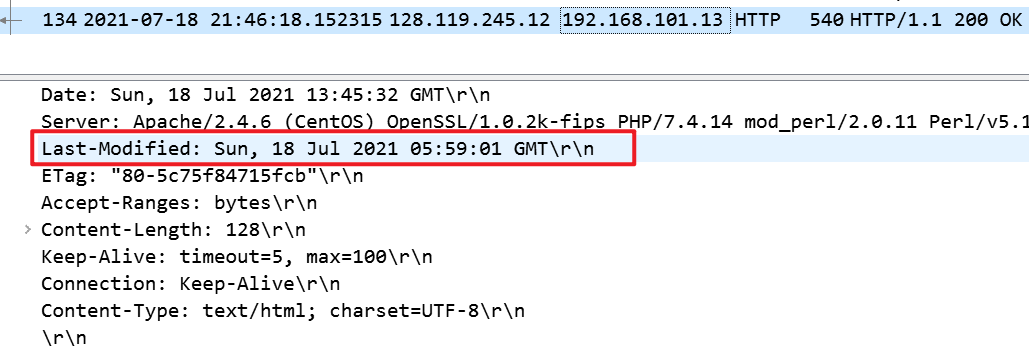
gaia.cs.umass.edu server每分钟都要设置此文件的last-modified时间为当前时间,所以我的浏览器每次都是从服务器下载一个新的副本。 -
How many bytes of content are being returned to your browser?

-
By inspecting the raw data in the packet content window, do you see any headers within the data that are not displayed in the packet-listing window? If so, name one.
2、 The HTTP CONDITIONAL GET/response interaction
大多数Web浏览器使用对象缓存,从而在检索HTTP对象时执行条件GET。执行以下步骤之前,请确保浏览器的缓存为空
启动Wireshark packet sniffer,打开浏览器,进入此网址http://gaia.cs.umass.edu/wireshark-labs/HTTP-wireshark-file2.html,进入后再刷新一次。在筛选框中输入http进行筛选,找到自己的浏览器与服务器的两次交互。如果一个请求报文使用GET方法,并且请求报文中包含一个If-Modified-Since首部行,那么这个报文是一个条件(conditional)请求报文。
一个缓存服务器代表一个请求浏览器向某web服务器发送一个请求报文,web服务器向缓存服务器返回的响应报文中包含一个首部行字段:Last-Modified,表示该对象最后一次修改日期,缓存服务器将对象存在本地,同时转发给请求浏览器。
当缓存服务器第二次收到对同一个对象的请求,此对象还在本地,但是为了检验该对象是否被目标服务器修改,缓存服务器发送一个条件GET请求,包含一个首部行字段If-Modified-Since,等于上一次服务器的响应报文中的Last-Modified字段中的值。该字段告诉服务器仅当指定日期后该对象被修改过,才发送此对象。如果没有被修改,web服务器向缓存器发送一个不包含实体体的,状态行为304 Not Modified的响应报文,包含实体体只会浪费带宽。
以下的缓存都是浏览器本地的缓存,而不是一个单独的缓存服务器。
-
Inspect the contents of the first HTTP GET request from your browser to the server. Do you see an “IF-MODIFIED-SINCE” line in the HTTP GET?
在第一次请求中没有“IF-MODIFIED-SINCE”

-
Inspect the contents of the server response. Did the server explicitly return the contents of the file? How can you tell?
响应的内容:

-
Now inspect the contents of the second HTTP GET request from your browser to the server. Do you see an “IF-MODIFIED-SINCE:” line in the HTTP GET? If so, what information follows the “IF-MODIFIED-SINCE:” header?
我的浏览器第二次向服务器发送的GET请求中有If-Modified-Since字段,第一次没有

第二次发送的If-Modified-Since的时间就是上一次服务器的response的Last-Modified的时间

-
What is the HTTP status code and phrase returned from the server in response to this second HTTP GET? Did the server explicitly return the contents of the file? Explain.
304 Not Modified,没有返回实体体,表示该对象从上次请求过后没有修改过,可以直接使用本地缓存的对象。

3、Retrieving Long Documents
之前是从服务器获取短报文,现在要求从服务器获取长报文。访问http://gaia.cs.umass.edu/wireshark-labs/HTTP-wireshark-file3.html此网页,重启packet capture。
我们可以看到在刚才的一个GET请求后面跟随着好几个TCP报文段。因为这一次的http请求的HTML文件太长了,单个的http响应被TCP分成了好几段。
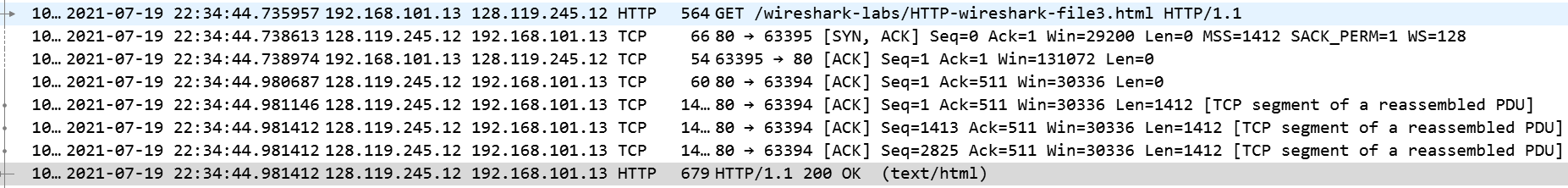
-
. How many HTTP GET request messages did your browser send? Which packet number in the trace contains the GET message for the Bill or Rights?
仅发送了一个GET请求
-
Which packet number in the trace contains the status code and phrase associated with the response to the HTTP GET request?
-
What is the status code and phrase in the response?
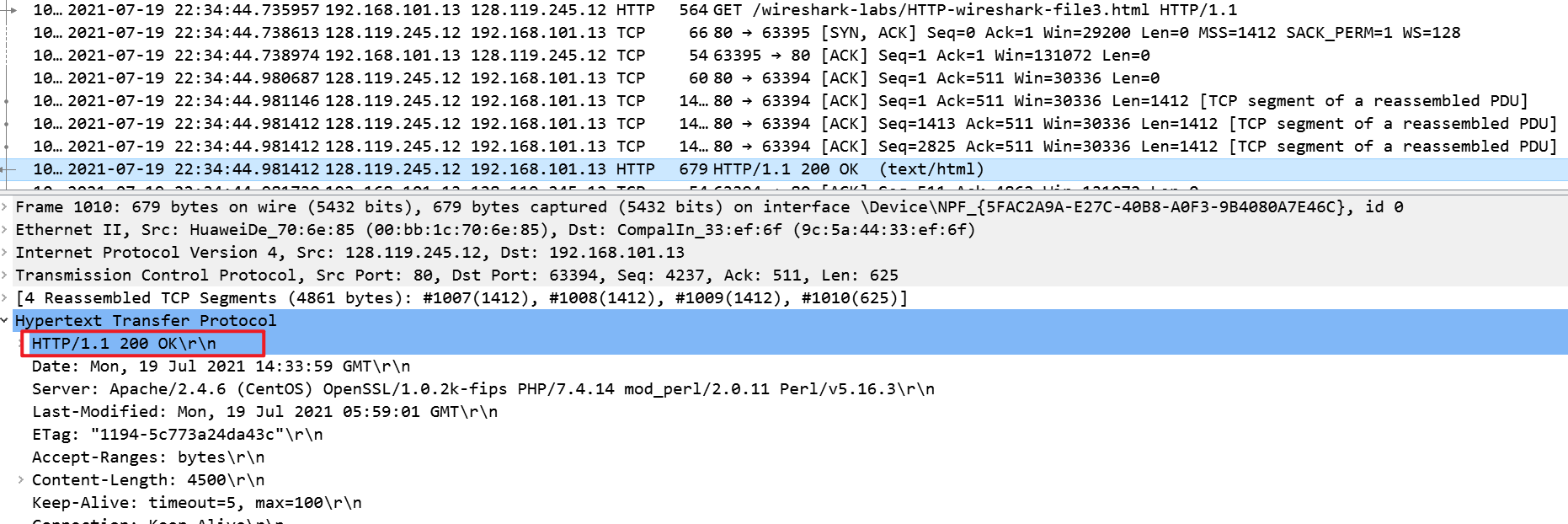
-
How many data-containing TCP segments were needed to carry the single HTTP response and the text of the Bill of Rights?

从最后一个http的响应可以看出,共有4个重新组合的TCP报文段。
4、HTML Documents with Embedded Objects
这一次我们来看看当浏览器请求包含嵌入的、存储在其他服务器的其他对象(比如图片)的文件时,会发生什么。访问http://gaia.cs.umass.edu/wireshark-labs/HTTP-wireshark-file3.html此网页,重启packet capture。在这个网页中有两个图片,图片本身并没有包含在其中,而包含的是图片的URL。我们的浏览器需要从URL指定的服务器获取这两张图片。
-
How many HTTP GET request messages did your browser send? To which Internet addresses were these GET requests sent?
发送了三个http请求,发送到128.119.245.12和178.79.137.164
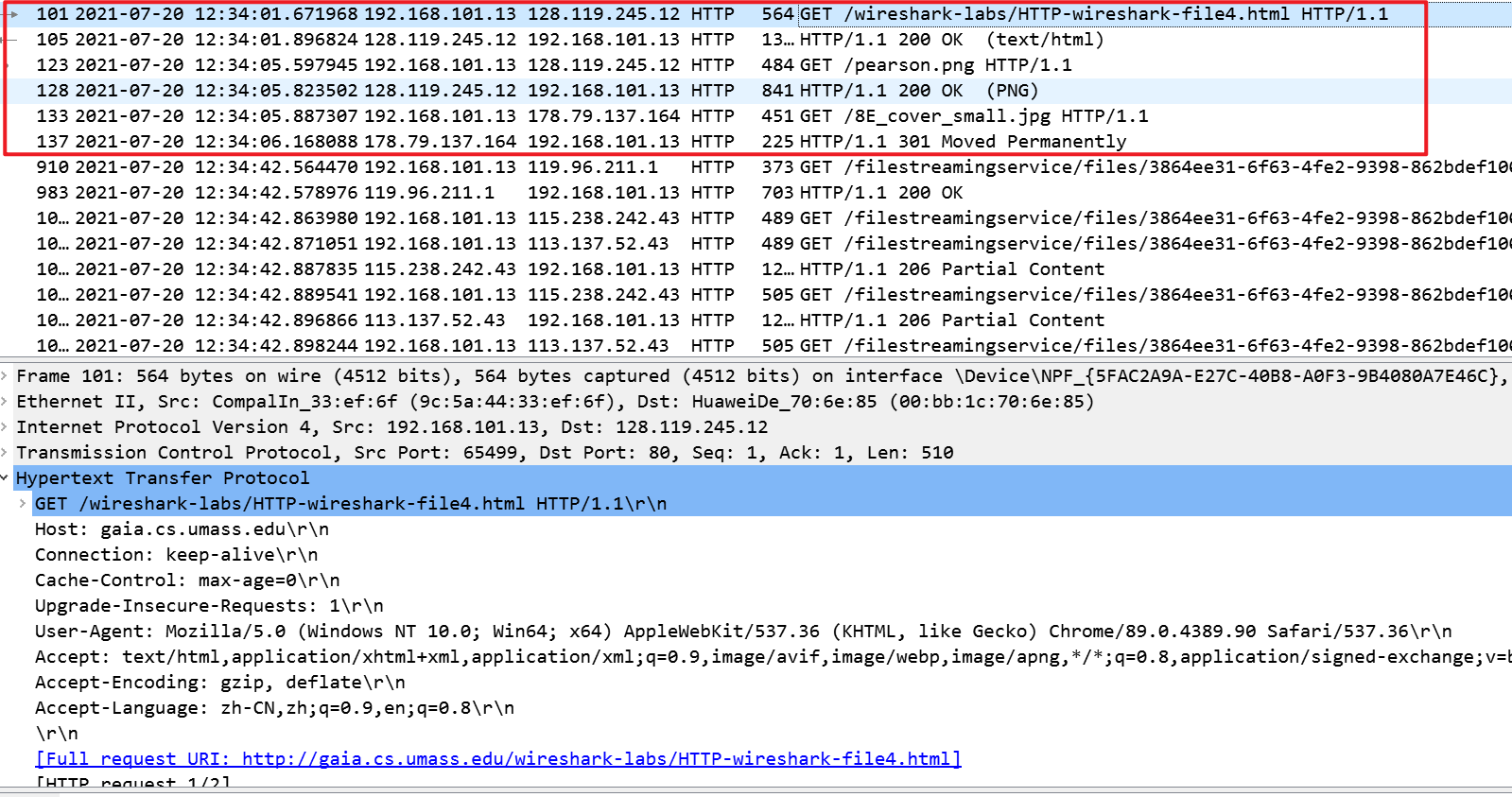
-
Can you tell whether your browser downloaded the two images serially, or whether they were downloaded from the two web sites in parallel? Explain.
这些包是先后发出的,所以它们不是并行下载的,而是顺序下载的。
5、HTTP Authentication
http认证:
现在我们尝试访问受密码保护的网站,并检查网站的HTTP消息交换的序列。URL http://gaia.cs.umass.edu/wireshark-labs/protected_pages/HTTP-wireshark-file5.html 是受密码保护的。用户名是“wireshark-students”,密码是“network”。
清除浏览器缓存,重启packet capture,访问以上网站。
-
What is the server’s response (status code and phrase) in response to the initial HTTP GET message from your browser?
服务器先返回401 Unauthorized,即未授权,要求登录才能访问。
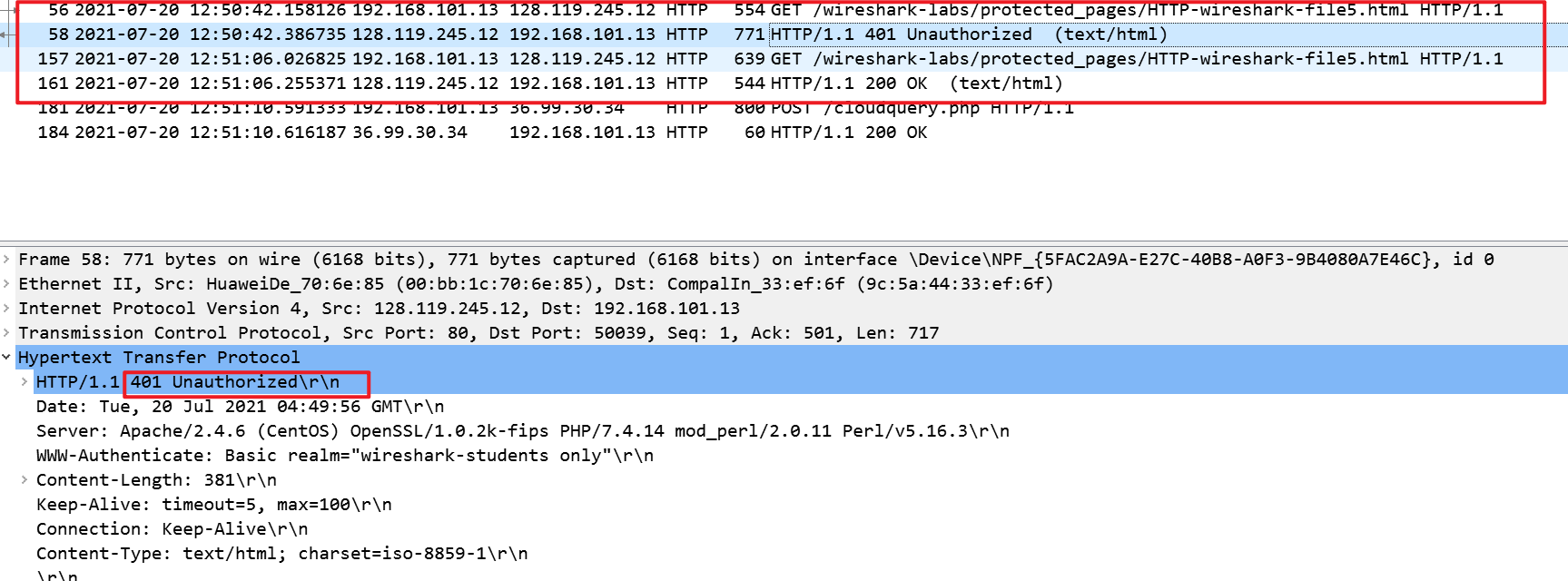
-
When your browser’s sends the HTTP GET message for the second time, what new field is included in the HTTP GET message?
我的浏览器第二次发送的GET请求包含一个Authorization: Basic字段
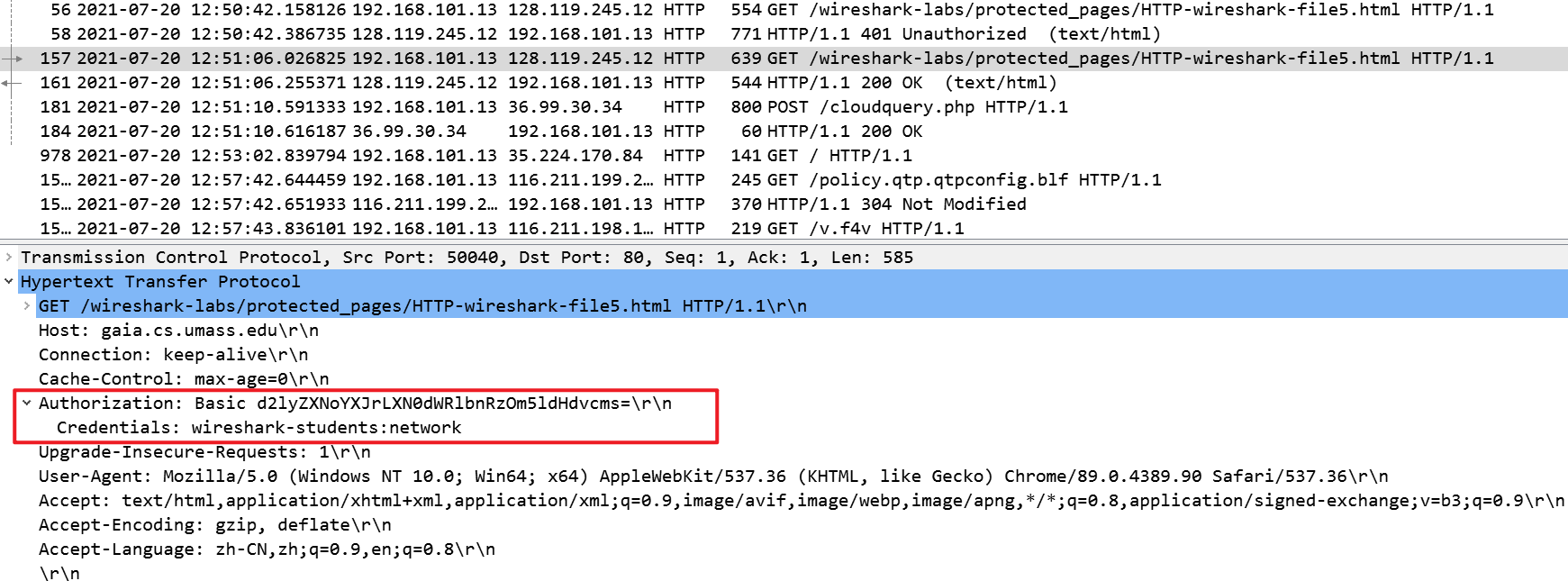
Authorization: Basic后面跟着的一串64位的字符串,就是我们输入的用户名和密码经过base64编码后的结果。这并不是加密,任何人都可以将这些字符串转化为ASCII码,就可以看到我们的密码。在wireshark中自带解码工具,直接转换成了我们刚才输入的用户名和密码。
Base64是一种用64个字符来表示任意二进制数据的方法。
DNS
1、 nslookup
要在Linux/Unix中运行nslookup,只需在命令行中键入nslookup命令即可。要在Windows中运行,打开cmd并在命令行上运行nslookup。nslookup工具允许主机查询任何指定的DNS服务器的DNS记录。DNS服务器可以是根DNS服务器,顶级域DNS服务器,权威DNS服务器或中间DNS服务器。要完成此任务,nslookup将DNS查询发送到指定的DNS服务器,然后接收DNS回复,并显示结果。运行nslookup时,如果没有指定DNS服务器,则nslookup会将查询发送到默认的DNS服务器
-
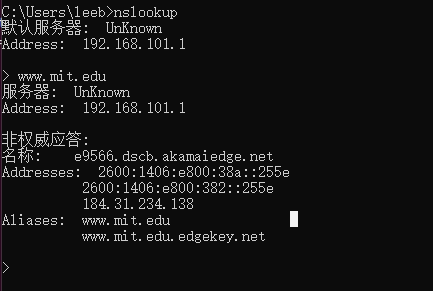
nslookup www.mit.edu这个命令是说,请告诉我主机 www.mit.edu 的IP地址。此命令的响应提供两条信息:
- 提供响应的DNS服务器的名称和IP地址;
- 响应本身,即 www.mit.edu 的主机名、别名、IPv4地址和ipv6地址。
-
nslookup -type=NS mit.edu
我们添加了选项"-type=NS"和域名"mit.edu",让nslookup发送对type-NS记录的请求到默认DNS服务器。也就是要求默认DNS服务器返回mit.edu的权威服务器的名字。当不使用-type选项时,nslookup使用默认值,即查询A类记录。
在上图中,首先显示了提供响应的DNS服务器(这是默认本地DNS服务器)以及八个MIT域名服务器。。然而,nslookup也表明该响应是非权威的,这意味着这个响应来自某个服务器的缓存,而不是来自权威MIT DNS服务器。最后,响应结果还显示了mit权威DNS服务器的IP地址。 (即使nslookup生成的NS类型查询没有明确要求IP地址,本地DNS服务器依然返回了这些信息,然后被nslookup显示出来。)
-
如果是向某主机的权威服务器查询它的IP地址,就不会出现非权威查询的字样

-
用-type=NS方式查不到包含www的域名对应的权威DNS服务器,因为包含www的域名已经是最底层的域名了,不会有子域名存在,也就不会有对应的权威DNS服务器。

-
-
nslookup www.aiit.or.kr bitsy.mit.edu在这个例子中,我们希望将查询请求发送到DNS服务器 bitsy.mit.edu ,而不是默认的DNS服务器(dns-prime.poly.edu)。因此,查询和响应事务直接发生在我们的主机和 bitsy.mit.edu 之间。在这个例子中,DNS服务器 bitsy.mit.edu 提供主机 www.aiit.or.kr 的IP地址,它是高级信息技术研究所(韩国)的Web服务器。
问题:
-
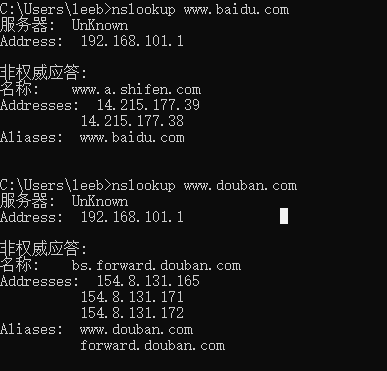
Run nslookup to obtain the IP address of a Web server in Asia. What is the IP address of that server?
-
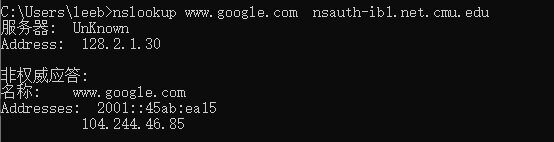
Run nslookup to determine the authoritative DNS servers for a university in Europe.
查看了cmu的权威服务器的名字和cmu的cs专业的权威服务器的名字

-
Run nslookup so that one of the DNS servers obtained in Question 2 is queried for the mail servers for Yahoo! mail. What is its IP address?
返回的响应服务器的IP地址是对的,和上面查找的一致,就是查找的目标服务器有点问题,结果很奇怪。
2、ipconfig
ipconfig可用于显示我们当前的TCP/IP信息,包括IP地址,DNS服务器地址,适配器类型等。例如,您只需进入命令提示符,输入ipconfig /all可以显示所有的主机信息

输入ipconfig /displaydns可以显示主机缓存的最近获得的DNS记录。每个条目显示剩余的生存时间(TTL)(秒)。要清除缓存,输入ipconfig /flushdns清除了所有条目并从hosts文件重新加载条目。

3、Tracing DNS with Wireshark
使用ipconfig清空主机中的DNS缓存,清空浏览器缓存,打开Wireshark,然后在过滤器中输入“ip.addr==your_IP_address“,本机的IP地址使用ipconfig查看。这个过滤器移除所有源地址不是此IP、目标地址也不是此IP的包。启动packet capture,访问https://www.ietf.org此网址。
-
Locate the DNS query and response messages. Are then sent over UDP or TCP?
一共两条DNS记录,一条是本机发送给本地DNS服务器的查询报文,一条是本地DNS服务器返回的报文,通过UDP发送
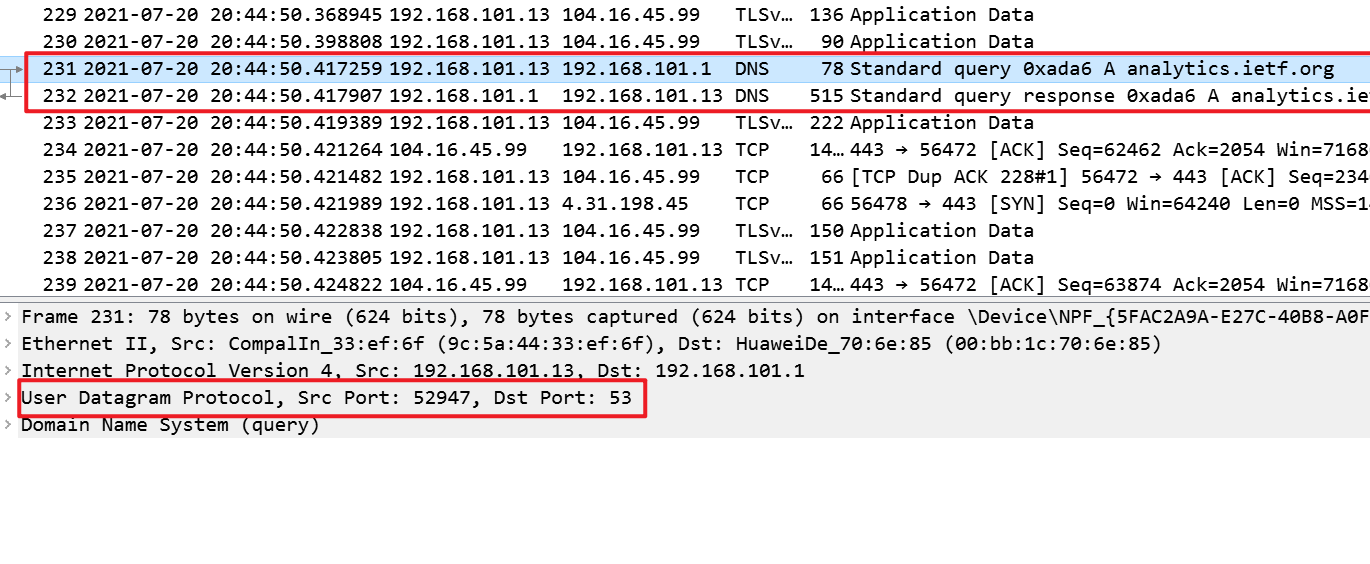
-
What is the destination port for the DNS query message? What is the source port of DNS response message?
DNS查询消息的目标端口和响应消息的源端口都是 53
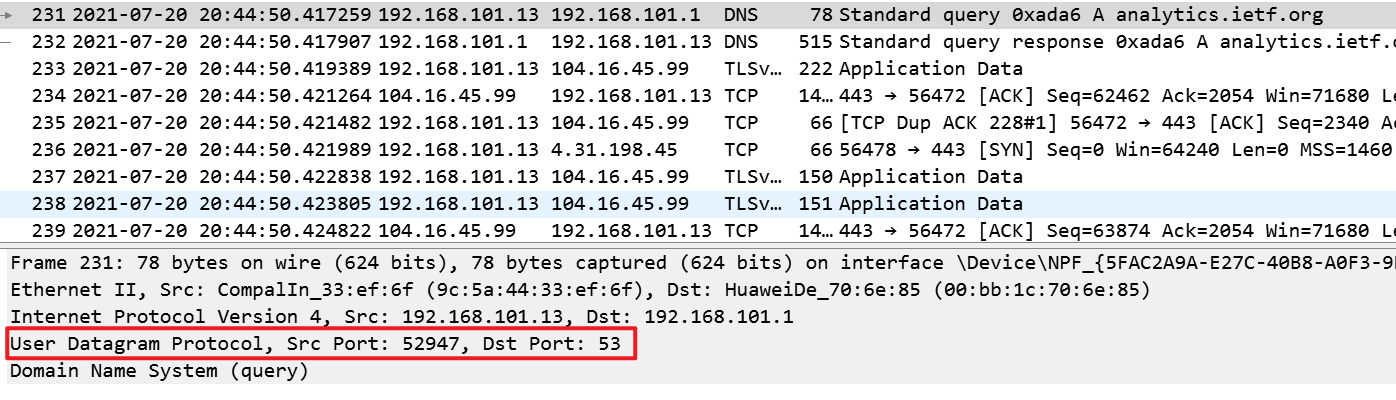
-
To what IP address is the DNS query message sent? Use ipconfig to determine the IP address of your local DNS server. Are these two IP addresses the same?
使用ipconfig得到的本地DNS服务器的IP:

与wireshark抓包得到的IP相同,与nslookup得到的默认DNS服务器的IP地址也相同
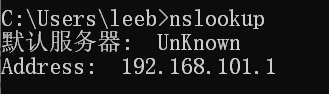
-
Examine the DNS query message. What “Type” of DNS query is it? Does the query message contain any “answers”?
type A,查询消息不包含任何answer

-
Examine the DNS response message. How many “answers” are provided? What do each of these answers contain?
1个answer,包含主机的名字,主机的IP地址,查询的类型

-
Consider the subsequent TCP SYN packet sent by your host. Does the destination IP address of the SYN packet correspond to any of the IP addresses provided in the DNS response message?

-
This web page contains images. Before retrieving each image, does your host issue new DNS queries?
没有
现在我们来使用nslookup,重启packet capture,使用nslookup查询 www.mit.edu。

-
What is the destination port for the DNS query message? What is the source port of DNS response message?
DNS查询消息的目标端口和响应消息的源端口都是 53
-
To what IP address is the DNS query message sent? Is this the IP address of your default local DNS server?
是本地DNS服务器的IP地址
-
Examine the DNS query message. What “Type” of DNS query is it? Does the query message contain any “answers”?
type=A(ipv4查询),type=AAAA(ipv6查询),不包含任何答案

-
Examine the DNS response message. How many “answers” are provided? What do each of these answers contain?
很多answer,包含主机的规范名、ipv4地址和ipv6地址。
现在重启packet capture,输入 nslookup –type=NS mit.edu命令。
-
Examine the DNS query message. What “Type” of DNS query is it? Does the query message contain any “answers”?
A和NS,不包含
-
Examine the DNS response message. What MIT nameservers does the response message provide? Does this response message also provide the IP addresses of the MIT namesevers?
响应信息中包含了NS类型的answer、也包含了A类型的answer和AAAA类型的answer
-
NS类型

-
A类型:

-
AAAA类型:

与命令行显示的内容一致,响应信息中既包括权威域名服务器的名字,也包含权威域名服务器的ipv4地址和ipv6地址。
-