1. 漏洞描述
TLS 1.0是于1996年发布的老版协议,使用的是弱加密算法和系统。比如SHA-1和MD5,这些算法和系统十分脆弱,存在重大安全漏洞,容易受到降级攻击的严重影响。
| 服务 | 端口 | 漏洞名称 | 修复建议 |
|---|---|---|---|
| nginx | 443 | TLS版本1.0协议检测 | 启用对TLS 1.2或1.3的支持,并禁用对TLS 1.0的支持 |
| nginx | 443 | TLS版本1.1协议检测 | 启用对TLS 1.2或1.3的支持,并禁用对TLS 1.1的支持 |
2. 补充学习
-
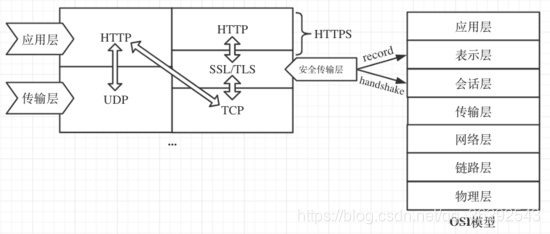
TLS全称为:Transport Layer Security——安全传输层协议,用于在两个通信应用程序之间提供保密性和数据完整性。
-
该协议由两层组成: TLS 记录协议(TLS Record)和 TLS 握手协议(TLS Handshake)。较低的层为 TLS 记录协议,位于某个可靠的传输协议(例如 TCP)上面。
-
TLS 的最大优势就在于:TLS 是独立于应用协议。高层协议可以透明地分布在 TLS 协议上面。
3. 漏洞检测
使用nmap网络安全审计工具(kail中有集成)
检测命令:
nmap --script ssl-enum-ciphers -p 443 ip地址
>nmap --script ssl-enum-ciphers -p 443 192.168.1.100
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-17 17:30 ?D1ú±ê×?ê±??
Nmap scan report for localhost (192.168.1.100)
Host is up (0.0089s latency).
PORT STATE SERVICE
443/tcp open https
| ssl-enum-ciphers:
| TLSv1.0:
| ciphers:
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (ecdh_x25519) - A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 1024) - A
| TLS_RSA_WITH_CAMELLIA_256_CBC_SHA (rsa 1024) - A
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 1024) - A
| TLS_RSA_WITH_CAMELLIA_128_CBC_SHA (rsa 1024) - A
| compressors:
| NULL
| cipher preference: server
| TLSv1.1:
| ciphers:
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (ecdh_x25519) - A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 1024) - A
| TLS_RSA_WITH_CAMELLIA_256_CBC_SHA (rsa 1024) - A
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 1024) - A
| TLS_RSA_WITH_CAMELLIA_128_CBC_SHA (rsa 1024) - A
| compressors:
| NULL
| cipher preference: server
| TLSv1.2:
| ciphers:
| TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_ARIA_256_GCM_SHA384 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_ARIA_128_GCM_SHA256 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_CAMELLIA_256_CBC_SHA384 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_CAMELLIA_128_CBC_SHA256 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (ecdh_x25519) - A
| TLS_RSA_WITH_AES_256_GCM_SHA384 (rsa 1024) - A
| TLS_RSA_WITH_AES_256_CCM_8 (rsa 1024) - A
| TLS_RSA_WITH_AES_256_CCM (rsa 1024) - A
| TLS_RSA_WITH_ARIA_256_GCM_SHA384 (rsa 1024) - A
| TLS_RSA_WITH_AES_128_GCM_SHA256 (rsa 1024) - A
| TLS_RSA_WITH_AES_128_CCM_8 (rsa 1024) - A
| TLS_RSA_WITH_AES_128_CCM (rsa 1024) - A
| TLS_RSA_WITH_ARIA_128_GCM_SHA256 (rsa 1024) - A
| TLS_RSA_WITH_AES_256_CBC_SHA256 (rsa 1024) - A
| TLS_RSA_WITH_CAMELLIA_256_CBC_SHA256 (rsa 1024) - A
| TLS_RSA_WITH_AES_128_CBC_SHA256 (rsa 1024) - A
| TLS_RSA_WITH_CAMELLIA_128_CBC_SHA256 (rsa 1024) - A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 1024) - A
| TLS_RSA_WITH_CAMELLIA_256_CBC_SHA (rsa 1024) - A
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 1024) - A
| TLS_RSA_WITH_CAMELLIA_128_CBC_SHA (rsa 1024) - A
| compressors:
| NULL
| cipher preference: server
|_ least strength: A
Nmap done: 1 IP address (1 host up) scanned in 5.55 seconds
4. 漏洞修复
采用2008年和2017年发布的协议新版本,分为TLS 1.2和TLS 1.3。
# 原始配置
#ssl_protocols TLSv1 TLSv1.1 TLSv1.2 ;
# 修复配置
ssl_protocols TLSv1.2 ;
# HTTPS server
#
server {
listen 443 ssl;
server_name 192.168.1.100;
keepalive_timeout 70;
ssl_certificate cert/mycert.pem;
ssl_certificate_key cert/privatekey.pem;
#ssl_certificate cert/server.crt;
#ssl_certificate_key cert/server_rsa_private.pem.unsecure;
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 5m;
#ssl_protocols TLSv1 TLSv1.1 TLSv1.2 ;
ssl_protocols TLSv1.2 ;
ssl_ciphers HIGH:!aNULL:!MD5;
ssl_prefer_server_ciphers on;
location / {
root html;
index index.html index.htm;
}
# 映射服务器集群
location /test/{
proxy_set_header X-Real-IP $remote_addr;
proxy_pass http://test;
}
location /status{
stub_status on;
}
}
漏洞复测
>nmap --script ssl-enum-ciphers -p 443 192.168.1.100
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-17 17:32 ?D1ú±ê×?ê±??
Nmap scan report for localhost (192.168.1.100)
Host is up (0.011s latency).
PORT STATE SERVICE
443/tcp open https
| ssl-enum-ciphers:
| TLSv1.2:
| ciphers:
| TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_ARIA_256_GCM_SHA384 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_ARIA_128_GCM_SHA256 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_CAMELLIA_256_CBC_SHA384 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_CAMELLIA_128_CBC_SHA256 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (ecdh_x25519) - A
| TLS_RSA_WITH_AES_256_GCM_SHA384 (rsa 1024) - A
| TLS_RSA_WITH_AES_256_CCM_8 (rsa 1024) - A
| TLS_RSA_WITH_AES_256_CCM (rsa 1024) - A
| TLS_RSA_WITH_ARIA_256_GCM_SHA384 (rsa 1024) - A
| TLS_RSA_WITH_AES_128_GCM_SHA256 (rsa 1024) - A
| TLS_RSA_WITH_AES_128_CCM_8 (rsa 1024) - A
| TLS_RSA_WITH_AES_128_CCM (rsa 1024) - A
| TLS_RSA_WITH_ARIA_128_GCM_SHA256 (rsa 1024) - A
| TLS_RSA_WITH_AES_256_CBC_SHA256 (rsa 1024) - A
| TLS_RSA_WITH_CAMELLIA_256_CBC_SHA256 (rsa 1024) - A
| TLS_RSA_WITH_AES_128_CBC_SHA256 (rsa 1024) - A
| TLS_RSA_WITH_CAMELLIA_128_CBC_SHA256 (rsa 1024) - A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 1024) - A
| TLS_RSA_WITH_CAMELLIA_256_CBC_SHA (rsa 1024) - A
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 1024) - A
| TLS_RSA_WITH_CAMELLIA_128_CBC_SHA (rsa 1024) - A
| compressors:
| NULL
| cipher preference: server
|_ least strength: A
Nmap done: 1 IP address (1 host up) scanned in 5.01 seconds
5. 片尾彩蛋
道路注定很漫长,但如果一味地等待,就永远不会到达终点。——白岩松